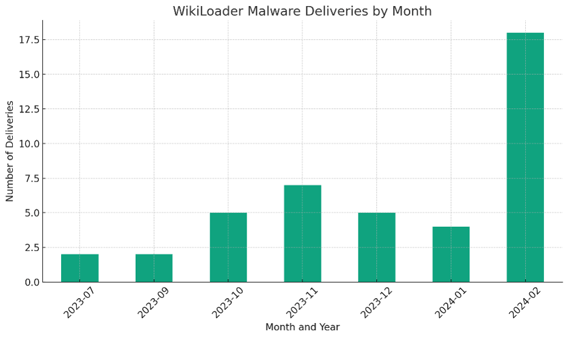
EclecticIQ analysts identified an increase in the delivery of WikiLoader in February 2024 [1]. This trend highlights the necessity for organizations and individuals to enhance their cybersecurity measures against WikiLoader.
Figure 1 - Analytical data from MalwareBazaar showing WikiLoader uploads
(click on image to open in separate tab).
WikiLoader [2] was first identified in 2022 as a downloader designed to deploy additional payloads on victims' devices, including malware like banking trojan Ursnif [3] (AKA Gozi, Gozi-ISFB, Dreambot, Papras, and snifula). Researchers from Proofpoint [4] have linked WikiLoader to two threat actor groups, TA544 and TA551, which are financially motivated and have historically targeted corporations in Europe and Japan with Ursnif. WikiLoader is described as Malware-as-a-Service (MaaS), which is available for rent by cybercriminals on a selective basis.
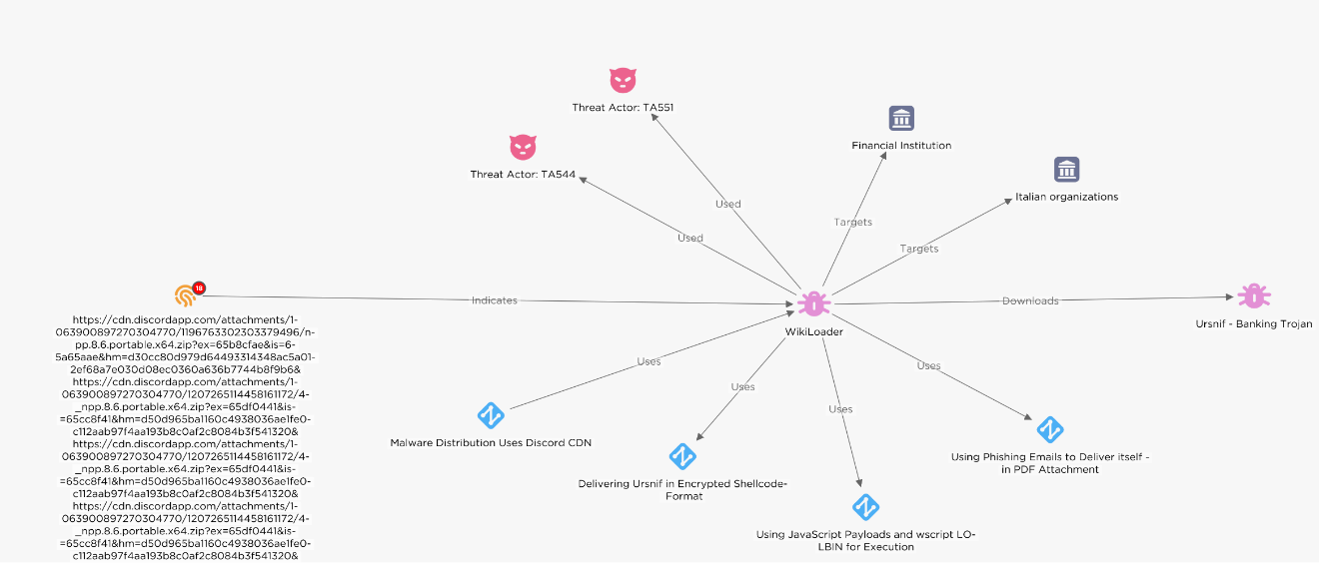
Figure 2 – WikiLoader overview from
EclecticIQ's Intelligence Center.
The infection process typically begins with a phishing email that contains a PDF attachment. This PDF contains a malicious link, when clicked by the victim, initiates the download of a compressed JavaScript file. This file then downloads the final payload. To avoid detection by anti-malware scanners, the malware employs evasion tactics such as obfuscation and the use of indirect system calls.
As WikiLoader operates as a Malware-as-a-Service (MaaS), the specific nature of the final payload can vary. Observed trends indicate that it is often banking malware like Ursnif or other information-stealing malware aimed at financial exploitation.
Mitigation & Detection Opportunities
WikiLoader is mostly delivered via macro-enabled documents, PDFs containing URLs leading to a JavaScript payload, and OneNote attachments with embedded executables. EclecticIQ analysts suggest below mitigation and detection opportunities against in-the-wild WikiLoader attacks.
- Delivery of WikiLoader via macro enabled office documents can be detected by “Suspicious Microsoft Office Child Process [5]” sigma rule.
- Monitor or block execution of wscript.exe Living-Off-the-Land binary (LOLBIN) via application whitelisting.
-
- Sigma rule “Script Interpreter Execution From Suspicious Folder [6]” can be used to detect this activity.
- Implement system wide two-factor authentication (2FA) and block credential savings in endpoint browsers trough group polices.
- Automatically disable macros for all employees.
- Prevent the execution of external files embedded within OneNote documents.
- Ensure JavaScript files are set to open by default in a text editor or similar application.
MITRE ATT&CK
- T1566.001: Phishing: Spearphishing Attachment
- T1566.002: Phishing: Spearphishing Link
- T1204.002: User Execution: Malicious File
- T1105: Ingress Tool Transfer
- T1027: Obfuscated Files or Information
- T1059.007: Command and Scripting Interpreter: JavaScript
- T1562.001: Impair Defenses: Disable or Modify Tools
- T1071.001: Application Layer Protocol: Web Protocols
- T1027.002: Obfuscated Files or Information: Software Packing
Structured Data
Find this and other research in our public TAXII collection for easy use in your security stack: https://cti.eclecticiq.com/taxii/discovery.
Please refer to our support page for guidance on how to access the feeds.
About EclecticIQ Intelligence & Research Team
EclecticIQ is a global provider of threat intelligence, hunting, and response technology and services. Headquartered in Amsterdam, the EclecticIQ Intelligence & Research Team is made up of experts from Europe and the U.S. with decades of experience in cyber security and intelligence in industry and government.
We would love to hear from you. Please send us your feedback by emailing us at research@eclecticiq.com.
You might also be interested in
10 Steps to Building a Comprehensive CTI Practice
DarkGate: Opening Gates for Financially Motivated Threat Actors
References
[1] “MalwareBazaar | Browse malware samples.” Accessed: Feb. 28, 2024. [Online]. Available: https://bazaar.abuse.ch/browse.php?search=tag%3AWikiLoader
[2] “WikiLoader (Malware Family).” Accessed: Feb. 26, 2024. [Online]. Available: https://malpedia.caad.fkie.fraunhofer.de/details/win.wikiloader
[3] “What Is Ursnif Malware?” Accessed: Feb. 26, 2024. [Online]. Available: https://www.blackberry.com/us/en/solutions/endpoint-security/ransomware-protection/ursnif
[4] “Out of the Sandbox: WikiLoader Digs Sophisticated Evasion | Proofpoint US,” Proofpoint. Accessed: Feb. 26, 2024. [Online]. Available: https://www.proofpoint.com/us/blog/threat-insight/out-sandbox-wikiloader-digs-sophisticated-evasion
[5] “sigma/rules/windows/process_creation/proc_creation_win_office_susp_child_processes.yml at 6b8cd1f0f1d222dcffa95394b4cbcec2a05137a0 · SigmaHQ/sigma,” GitHub. Accessed: Feb. 28, 2024. [Online]. Available: https://github.com/SigmaHQ/sigma/blob/6b8cd1f0f1d222dcffa95394b4cbcec2a05137a0/rules/windows/process_creation/proc_creation_win_office_susp_child_processes.yml
[6] “sigma/rules/windows/process_creation/proc_creation_win_susp_script_exec_from_env_folder.yml at master · SigmaHQ/sigma,” GitHub. Accessed: Feb. 28, 2024. [Online]. Available: https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/proc_creation_win_susp_script_exec_from_env_folder.yml