Threat actors of advanced capability seek to compromise network edge devices such as Ivanti systems to establish advanced footholds, from which to perform targeted reconnaissance identifying organizations with data of high value. Three vulnerabilities recently announced in Ivanti systems underscore the importance of layered security for internet-exposed systems. The greatest risk going forward is most likely from ransomware threat actors, who will likely incorporate exploits with ransomware payloads, as well as APT activity that target third parties integral to advanced technology supply chains.
Threat Actors Exploiting The Vulnerabilities Over The Past 21 Days Are a Mix of Moderate to Advanced Cybercriminals And Advanced Persistent Threats
The vulnerabilities are not trivial to exploit and goals are very likely now shifting. From a wider cyberdefense angle, the vulnerabilities are very likely to be further leveraged opportunistically, by threat actors compromising non-specific targets, looking for data of high value and privileged account credentials to compromise.
Zero-day and n-day vulnerabilities in Ivanti security system web components published beginning January 10. [1]
CVE-2023-46805 - authentication-bypass, CVSS score of 8.2
CVE-2024-21887 - command-injection in multiple web components, CVSS score of 9.1
CVE-2024-21888 - privilege escalation to ADMIN, CVSS score of 8.8
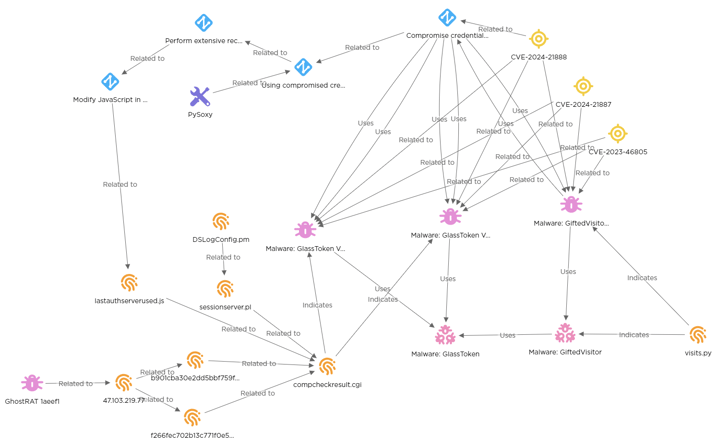
EclecticIQ analysts assess with moderate confidence that further exploitation attempts could be detected based on an exclusive TTP (tactic, technique, procedure), backdooring a legitimate CGI file compcheckresult.cgi. This is a file exploited to produce a webshell for persistent access. The legitimate file used by Ivanti devices was one of the first IOCs detected according to the original Volexity report. [1] Similar files were also previously implicated in a Pulse Secure n-day in 2021. [2] Analyst pivoted from “compcheckresult.cgi” and identified two files that contain positive malicious references and link to further malicious infrastructure:
Figure 1 - A Stix-based threat model of the three earliest Ivanti vulnerabilities
(click on image to open in separate tab).
Pivoting from indicators of compromise specific to the systems targeted produced further open-source intelligence in the form of similar files of the same type and name. Exploring these additional IOCs further produced links to other malicious infrastructure.
Two files:
b901cba30e2dd5bbf759fd8b72b8d2dd2e50e58bcf1a96b3983effcf881fec27
f266fec702b13c771f0e5d6424f449696499809896d9cf8bd1288b0f6ea7e836
share IP address 47[.]103[.]219[.]77 registered in Hangzhou, CN. It is on at least 10 antivirus lists registered as malicious. The domain registration was last modified 28.11.2023. Previously, in 2021 it was observed in a GH0STRAT campaign. [3] GH0STRAT is developed from a tool created by a China-based security team. The files were both uploaded within two weeks of one another at the end of 2023, matching the vulnerability timeline prepublication.
File: b901cba30e2dd5bbf759fd8b72b8d2dd2e50e58bcf1a96b3983effcf881fec27 is contained within a collection of files matching Cobalt Strike signatures from GCTI (Google). The file was first uploaded 26.11.2023 and references the following malicious IP addresses:
91[.]243[.]44[.]63 (BE)
198[.]12[.]81[.]50, 51[.]161[.]42[.]94, 172[.]245[.]191[.]17, 107[.]172[.]73[.]152 (CA)
87[.]236[.]146[.]34 (EE)
185[.]140[.]248[.]17 (FR)
92[.]38[.]135[.]99 (KR)
195[.]123[.]210[.]174 (LV)
185[.]141[.]26[.]236, 45[.]140[.]146[.]34 (MD)
185[.]117[.]75[.]123, 195[.]123[.]220[.]220 (NL)
40[.]125[.]65[.]33 (US)
File: f266fec702b13c771f0e5d6424f449696499809896d9cf8bd1288b0f6ea7e836
was first observed 11.12.2023 and contains strings referencing the following malicious IP addresses:
54[.]39[.]144[.]250 (CA)
194[.]36[.]190[.]41, 185[.]14[.]28[.]10, 45[.]133[.]1[.]53 (NL)
93[.]189[.]43[.]3, 45[.]138[.]157[.]211 (RU)
45[.]10[.]88[.]124 (UA)
131[.]153[.]38[.]125, 66[.]220[.]17[.]157, 66[.]117[.]37[.]7 (USA)
The IVANTI Vulnerability Exploitation is Deployed From a Combination of Compromised Infrastructure
The primary command and control domain identified for the exfiltration of credentials, symantke[.]com was first registered in August 2022. It does not tie to further known open-source intelligence or have any archived snapshots, further implicating it as likely a relatively new domain. The remaining IPs above link to a mix of past commodity malware campaigns, while a minority are relatively new and do not share connections with past open-source intelligence. The use of new and known infrastructure to target and exploit these vulnerabilities provides strong evidence that more common cybercriminals are now participating in less targeted, opportunistic exploitation.
The C2 IP addresses listed in the original report from Volexity all run JQuery (the primary JavaScript library used by most websites) and more than one of these servers is detected as having a vulnerable, outdated version vulnerable to at least one of the following JQuery CVEs: CVE 2020-11023, CVE 2020-11022, CVE 2019-11358.
Advanced Cybercriminals Will Seek to Exploit Remaining Opportunistic Vulnerable Instances
The use of a combination of compromised legitimate and known malicious infrastructure, both old and new supports cyberattack models that align with common cybercriminals operating higher-volume and more opportunistic cyberattacks. These cyberattacks carry higher risk of failure from using previously known malicious domains, which are easily filtered by network gateway security devices.
Rapid mobilization of multiple channels in cyberattacks after vulnerabilities are made public results in new cyberattack delivery channels that may not all be prevented without more layered security design. This upscaling in cyberattack channels carries greatest risk to endpoints on the network that interface with the internet. Layered security design for network edge endpoints includes multifactor authentication for admin accounts tied to those devices, segmentation of the network to create virtual boundaries for connections to data identified having greatest value, and enforcing minimum privileges wherever possible.
Structured Data
Find this and other research in our public TAXII collection for easy use in your security stack: https://cti.eclecticiq.com/taxii/discovery.
Please refer to our support page for guidance on how to access the feeds.
About EclecticIQ Intelligence & Research Team
EclecticIQ is a global provider of threat intelligence, hunting, and response technology and services. Headquartered in Amsterdam, the EclecticIQ Intelligence & Research Team is made up of experts from Europe and the U.S. with decades of experience in cyber security and intelligence in industry and government.
We would love to hear from you. Please send us your feedback by emailing us at research@eclecticiq.com.
You might also be interested in:
DarkGate: Opening Gates for Financially Motivated Threat Actors
EclecticIQ Retrospective: A Look at the Themes & Events That Shaped the 2023 Cyber Landscape
References
[1] Volexity, “Active Exploitation of Two Zero-Day Vulnerabilities in Ivanti Connect Secure VPN,” Volexity. Accessed: Jan. 11, 2024. [Online]. Available: https://www.volexity.com/blog/2024/01/10/active-exploitation-of-two-zero-day-vulnerabilities-in-ivanti-connect-secure-vpn/
[2] “CVE-2021-22893 Pulse Secure VPN Zero-Day,” Deepwatch. Accessed: Feb. 14, 2024. [Online]. Available: https://www.deepwatch.com/labs/pulse-vpn-zero-day-active-exploits/
[3] “Ghost RAT (Malware Family).” Accessed: Feb. 14, 2024. [Online]. Available: https://malpedia.caad.fkie.fraunhofer.de/details/win.ghost_rat