
In today's digital age, the importance of Cyber Threat Intelligence (CTI) cannot be overstated. For organizations at the helm of critical infrastructure, large enterprises, and central governments, a robust CTI practice is not just an option — it's a necessity.
We have put together a detailed roadmap for building a comprehensive CTI practice that shields your digital assets and ensures your organization's resilience against cyber threats.
Step 1 - Make room on the organizational chart
Although CTI is adjacent to and related to IT security, your practice should be a distinct competency. It should have responsibility for clearly defined processes, with appropriate support in terms of staffing and technology. Also, it must work with several other existing organizational functions, including security operations, incident operations, IR, fraud operations, and risk management. A key success factor is establishing the lines of reporting, communication, and responsibility well before setting up the practice.
Step 2 - Lock down IT capacity
While your CTI practice may not need to maintain an IT development team, it requires IT resources, including architecting, planning and implementing standard CTI processes and procedures, such as acquiring CTI feeds. Additionally, it needs ready access to a balanced, cross-functional team responsible for rolling out any changes or security improvements to line-of-business systems.
Step 3 - Build a well-balanced core team
Your CTI practice should include staff with the following experience and skill sets:
- Intelligence specialties including source data collection, threat analysis, indicator and malware analysis, threat intelligence management, incident response, threat hunting, and TIP operations.
- Formal intelligence training or similar training in critical thinking.
- Project management with cross-cultural or cross- organizational experience.
- Change management.
- Risk management.
- Practical IT security implementation and operations, e.g. systems engineering and
security engineering. - Hands-on experience in one or more key subject areas, including vulnerabilities, malware, cyber threats, fraud, and policy analysis.
Step 4 - Follow a CTI lifecycle model
The most successful CTI teams implement a disciplined CTI lifecycle model. Typically, this model covers four phases:
- Planning and Direction. During this phase, the CTI team works with the rest of the organization to establish primary intelligence requirements (PIRs). PIRs direct the CTI team throughout the lifecycle and set up the guardrails that bind the scope of the CTI
program. - Collection and Processing. Successful collection and processing involve ingesting, normalizing, and prioritizing millions of indicators, observables, and reports.
- Analysis and Production. Analysis and production are the activities on which CTI analysts spend most of their time. During this phase, analysts focus on threat actor TTPs to identify active threats to the organization. The CTI team compiles this knowledge into human- and machine-readable reports.
- Dissemination. As the last lifecycle step, reports provide a window into CTI operations for the rest of the organization.
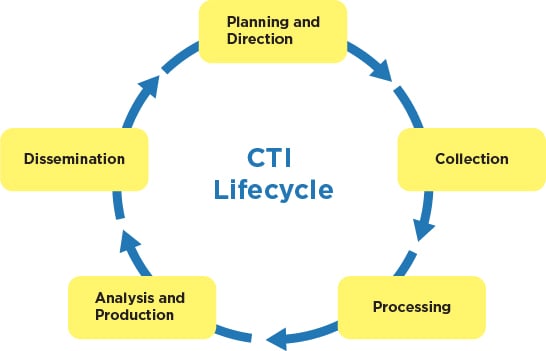
Figure 1 - The CTI lifecycle.
Step 5 - Step Manage the proper collection of CTI feeds
CTI feeds, especially commercially available feeds, often require considerable subscription fees and technology investments. Ensure that your CTI practice can measure the value of new CTI feeds to your stakeholders. Only ramp up your CTI feed investments when you clearly understand their impact.
Step 6 - Bootstrap with a technology stack
New technologies have emerged to support common challenges with implementing or improving the capabilities of a CTI practice, and these tools, such as advanced Threat Intelligence Platforms (TIPs), can provide a fast and easy way to deploy a core set of workflows and processes. Ensure that the workflow functionality of your planned technology platform meets the complete business requirements of your CTI practice.
Step 7 - Deliver a stakeholder-focused CTI solution
Creating business value from CTI relies on a nuanced understanding of the information needs of the key stakeholders in the organization. Even with the support of a CTI practice, it ultimately falls upon these stakeholders to execute a successful strategy to deter, defeat, and prevent cyberattacks. To make a positive impact on the business, the CTI team must understand the questions that stakeholders need answered, and how and at what cadence they prefer to consume intelligence.
Step 8 - Achieve stakeholder buy-in
For a CTI practice to succeed, stakeholders must be comfortable with a shared vision and a long-term plan for ongoing security. Ensure stakeholders understand how much you want to accomplish, at what pace, in what steps, and with what business constraints. Deliver on promises with measurable results.
Step 9 - Provide specific support to stakeholder groups
Your CTI practice must provide comprehensive support to multiple business functions, both inside and outside of IT:
- SOCs require structured indicators and warning signals associated with key threats in machine-readable formats such as CSV and STIX, or vendor-specific formats.
- Vulnerability management teams require written intelligence on emerging, high-impact vulnerabilities and known exploitation vectors to IT systems.
- IR and operations teams require ad hoc, customized intelligence related to TTPs, associated campaigns, actor intents and attributions, and forensic data on points of compromise.
- Business stakeholders require regular updates on critical threats to their areas of responsibility, with assessments of potential impacts on business operations.
- IT architects require up-to-date communications on critical threats to IT security to ensure alignment between the configuration of IT infrastructure and new cyber threats.
- Executives and decision makers require periodic high-level reports on exposures and critical threats the organization faces.
Step 10 - Implement a CTI maturity program
The last step to setting up your CTI practice is implementing processes and practices that improve stakeholders’ ability to defeat present attacks, deter ongoing actions, and prevent future attacks.
Building a CTI practice is a complex undertaking that takes considerable time and money. To justify this investment, you must determine if you are getting the best outcome from your CTI analyst team, if their intelligence is actionable, and if you are satisfying your stakeholders. You need highly mature processes in order to draw these conclusions.
Conclusion
By following these steps, organizations can establish a high-performing CTI practice. This not only enhances cybersecurity resilience but also aligns with business objectives, providing a strategic advantage in the face of cyber threats. For a deeper dive into each of these steps and to leverage the full insights from our experts, download the EclecticIQ white paper “A Stakeholder-centric Approach to Building a High-performing CTI Practice”.
Building a CTI practice is a strategic investment in your organization's cybersecurity posture. By following these steps, you can create a resilient, intelligence-driven defense mechanism that not only counters current threats but is also prepared for the challenges of tomorrow.
