
Key Findings
- Canada, the United States, and the United Kingdom issue a joint alert to APT activity targeting coronavirus research in their countries.
- Ransomware attacks on hospitals in regions struggling to contain infection rates carry the highest risk to human health.
- Threat actors exploiting government sponsored COVID relief programs obscure legitimate channels and contribute to the further decline of vulnerable populations.
- Increased use of remote banking drives increased risk of wire fraud to the Financial industry, particularly in Australia.
- Schools reopening with increased reliance on remote connections face high-risk from ransomware, especially in the US.
APT Groups linked to Russian Intelligence Pursue Data on Vaccines and Undermine Coronavirus Research.
APT-29 (Cozy Bear) is very likely behind 2020 cyberattacks targeting coronavirus research and vaccine development in organizations belonging to Canada, the United States, and the United Kingdom. First reports of APT activity possibly linked to Russian Intelligence services included Gamaredon in April 2020. Both groups specialize in deploying an array of customized malware post-compromise to persist inside the network and remain hidden. They are known to use a variety of encrypted exfiltration techniques. Cyberattacks on research organizations expend valuable resources risk destroying important medical data. The joint advisory was released by The United Kingdom’s National Cyber Security Centre (NCSC) and Canada’s Communications Security Establishment (CSE).
Hospitals Unable To Control Infection Rates Carry The Highest Risk Of Disruption From Cyberattacks.
Infection rate spikes put increased stress on healthcare resources and make operations more vulnerable to disruption from malware. The Baton Rouge Clinic, AMC, LA, US suffered from a ransomware attack that is reported to have impacted phone, email, lab, and radiology services. An investigation is ongoing.
The attack in Louisiana follows a period of near record-level infections across the State. In our update posted June 30, 2020 EclecticIQ Analysts highlighted particular risk from cyber-attacks to healthcare facilities in regions struggling to contain the pandemic.
Malicious Activity Exploiting State Issued COVID-19 Services is Likely to Disrupt Official Channels of Communication.
Government programs providing covid-19 services are at high risk of exploitation by cybercriminals for financial gain. Brazil is being targeted by threat actors exploiting government portals to financial relief programs. Threat actors use email, SMS messages, and WhatsApp to deliver malicious URLs or apps spoofing legitimate government portals. The attacks can further defraud people in vulnerable situations during the pandemic by disrupting the finite resources of supportive government programs.
Attacks on government relief programs are an attractive target because threat actors can target a large audience with minimal infrastructure and phishing TTPs that are more simplistic to execute.
Other State governments with increasing infections will increase use of similar programs to support stressed working populations in those States. In April 2020, threat actors exploited a US-based stimulus program providing financial relief from the effects of the pandemic. Our last weekly update highlighted risk from threat actors spoofing COVID-19 government contact tracing programs.
Actors Seeking Financial Gain Via Wire Fraud Are Most Likely To Increase Risk To The Financial Industry By Exploiting Vulnerabilities And Data Sharing.
The pandemic has shifted more people to remote working, which is increasing the use of remote banking services. The increased technology demand has induced banks to expand their infrastructure to support customers in the form of more VPN systems and external client-facing applications. The increased infrastructure (attack surface) inevitably leads to increased vulnerability risk.
The Australian banking sector will experience a higher risk relative to the global Financial industry due to the State’s concurrent implementation of consumer data right (CDR), “which enables consumers to securely direct their banking data to access bespoke financial products and services” on a variety of transactions and accounts starting November 1, 2020. Increased data sharing will provide threat actors with more opportunity to capture sensitive financial data as data proliferates through more systems; a side-effect of increased data-sharing.
Schools Will Face Higher Risk From Ransomware When Classrooms Resume With Expanded Online-Only Offerings.
The pandemic will force many school districts to rely more on online remote connections as they reopen, increasing the likelihood of ransomware attacks on school operations. The FBI reports that attacks have increased during the pandemic and “hacking and ransomware attacks are becoming more common in municipalities, businesses and school systems.” The FBI has warned school districts to prepare for ransomware attacks when classes resume. 2020 incidents to schools in the US are listed on this map, in red.
Redevelopment of Popular Malware Loaders Increases Risk To Many Industries From Common High-Volume Phishing Attacks That Lead To Ransomware. 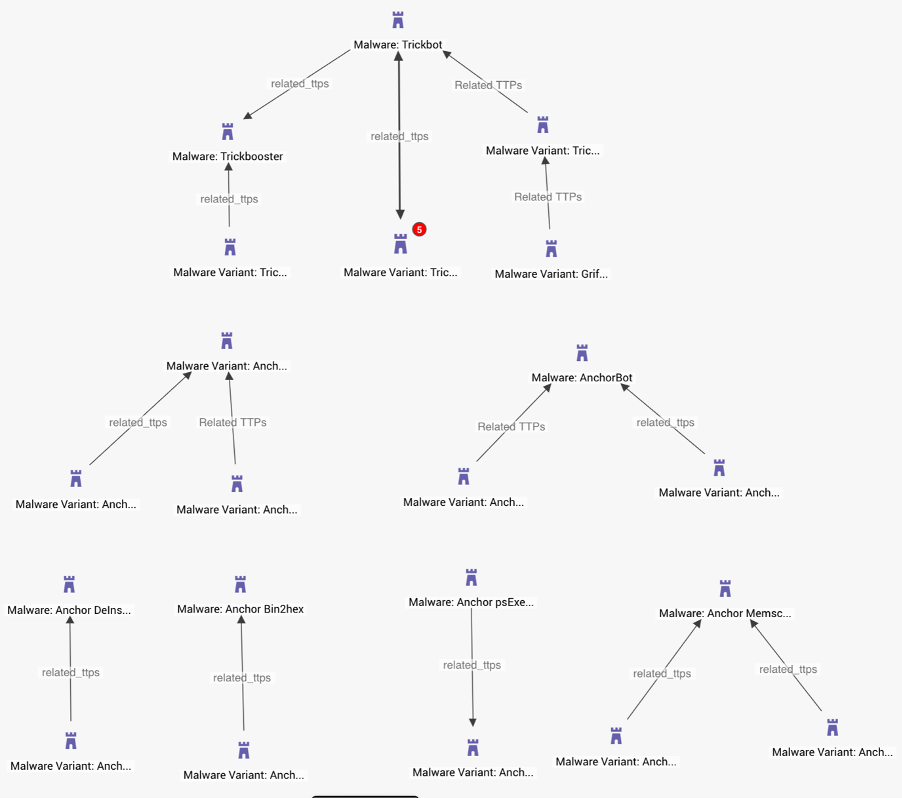
Threat intelligence demonstrating some of the major branches to the Trickbot malware family prior to Bazar, based on TTP modeling.
The Trickbot-anchor loader has been redeveloped into a new family of malware called Bazar that lives in memory and uses blockchain-DNS for its command and control infrastructure. Trickbot has historically supported attacks against Financial and Education verticals, among others. It is highly likely that Bazar will also be used to threaten these same industries. At least one Bazar loader has targeted an education institution, spoofing a University of the West Indies email address. The malware has also been observed in attacks exploiting COVID-19, specifically employee payroll reports and customer complaints.


