 As Europe’s leading cyber threat intelligence company, we at EclecticIQ have decided to make use of our resources and provide the community with custom reports on threats connected to the COVID-19 pandemic throughout the duration of the crisis. This is the 17th report in a weekly series of updates to inform of important developments to COVID-19-themed attacks.
As Europe’s leading cyber threat intelligence company, we at EclecticIQ have decided to make use of our resources and provide the community with custom reports on threats connected to the COVID-19 pandemic throughout the duration of the crisis. This is the 17th report in a weekly series of updates to inform of important developments to COVID-19-themed attacks.
Key Findings
- A recently developed ransomware sample with advanced capabilities targeted a preconfigured hospital network.
- Threat actors spoofing contact tracing programs risk subversion of official contact tracing programs.
- Money mule schemes exploiting abundant unemployed or underemployed individuals during the pandemic help drive further illicit activity and larger cybercriminal networks.
Analysis
Ransomware-as-a-Service Continues to Threaten Healthcare
An EKANS ransomware sample dated May 2020 targeted Fresenius Healthcare using brokered access which validates that RaaS remains a risk to healthcare. The variant attempted to validate a Fresenius subdomain and pivot to a domain controller using a preconfigured internal IP address. The malware’s hardcoded internal IP address suggests that the threat actors purchased compromised access to the subdomain from another group or individual on a malware marketplace.
It cannot be ruled out that the EKANS operators purchased network details of Fresenius from someone who previously compromised the network, based on the current growing trend of brokering access to compromised accounts and networks on dark marketplaces. FXMSP, believed to be a single threat actor, specialized in gaining and distributing access to compromised systems all over the world. EKANS was first described by Dragos after the family first emerged in mid-December 2019.
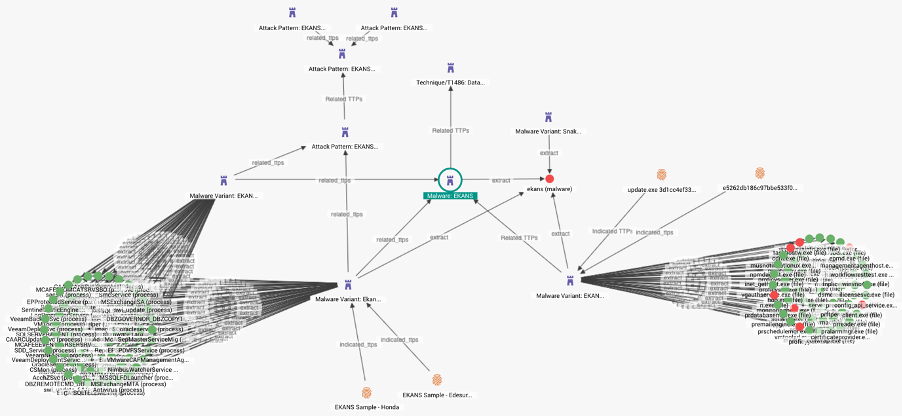 TTP-level analysis of targeting by recent EKANS ransomware variants.
TTP-level analysis of targeting by recent EKANS ransomware variants.
Government Contact Tracing is at Risk of Subversion by Scam Operations
Imposter COVID-19 tracing scams, involving unprompted voice and email solicitations designed to coerce individuals into providing personally identifiable information or money, could undermine official programs. The Financial Crimes Enforcement Network, based in the United States, issued an advisory regarding COVID-19 scams and money-mule activity. Government contact tracing efforts are ongoing in many nations and more people are likely to expose their information in these imposter scam attacks.
Money-mule schemes targeting remote workers and the unemployed incentivize criminal networks and support further operations
Threat actors target people out of work or looking for further work to be complicit or unknowing participants in money-mule schemes. Negative economic trends brought on by the pandemic are causing more people to look for alternative sources of income. Authorities detected many different types of schemes. ‘Work-from-home’ and unemployment insurance fraud represent two schemes directly related to the pandemic. Money mule schemes provide low barriers to entry and help to subsidize criminal networks for further operations. Money mule schemes exploit financial systems and put participants at high risk for detention.
COVID-19 Themed Phishing Attacks Against Enterprise Office365 Accounts Remains a Very High Risk
Recent Office365 attack expressing COVID-19 themed lures have been tied to separate BEC (Business Email Compromise) and APT activities targeted high-level business officials in 62 countries. The attacks are designed to harvest Office365 account credentials for further network penetration. The attacks were first observed by Microsoft in December 2019 and have since increased in quantity. The command and control TTPs spoof actual Microsoft infrastructure. Microsoft worked with law enforcement to take down the command and control networks.


