Cryptocurrencies will almost certainly continue adoption and further adaptation despite the large 2022 downturn. Growth of the ecosystem and changes underway in 2023 carry important implications for cyberattack risk to both end users and organizations bridging into cryptocurrency throughout the next two years as blockchain-based financial technology further matures. Recent activity and changes to cryptocurrency and decentralized finance (DeFi) have produced stressors on the system. Tracking changes since 2021 and 2022 showcases the trends most likely to continue with regards to cyberattack activity going into 2023 and 2024.
This report analyzes large-scale cybertheft targeting cryptocurrency resulting in at least $1 million in losses. Expanding on data and analysis of cyberattacks from our last related report, which looked at all-time record setting cyberattacks, provides further insights and validation of the cyberattack trends established and growing inside decentralized finance. (2) The primary cyberattack vectors described in our last report retain primacy. Data shows cyberattacks targeting cryptocurrency are now entrenched and present a major stressor to the landscape and are discussed in the figures below.
2022 best estimates pin total cryptocurrency losses at approximately $3.8 billion, increasing from the previous year. (3, 4, 5) The growth in cyberattacks is now taking place for the first time in the context of largescale decreasing market capitalization across almost all cryptocurrencies. 2023 cyberattacks already track at approximately 25% of the total for 2022. (1) The rate of cyberattack growth is not sustainable for future cryptocurrency platforms.
End Users And Organizations Involved in Cryptocurrency Should Expect Increasing Risk Through The Next Two Years
DeFi will continue spreading and adoption will increase. Figure 1 below shows increasing frequency of large-scale cyberattacks and the trend line for major cybertheft highlights losses growing towards unsustainable volumes. It is very likely that smaller scale cybertheft follows a similar trend further compounding overall risk.
Analysis of Cyberattack Activity Strongly Indicates That Risk Will Continue to Grow Unless Security Increases in Key Areas
Data analysis concerning large-scale (greater than $1 million) cyberattacks helps visualize how cyberattacks have become well established despite the large cryptocurrency market downturn that began in earnest in 2022.
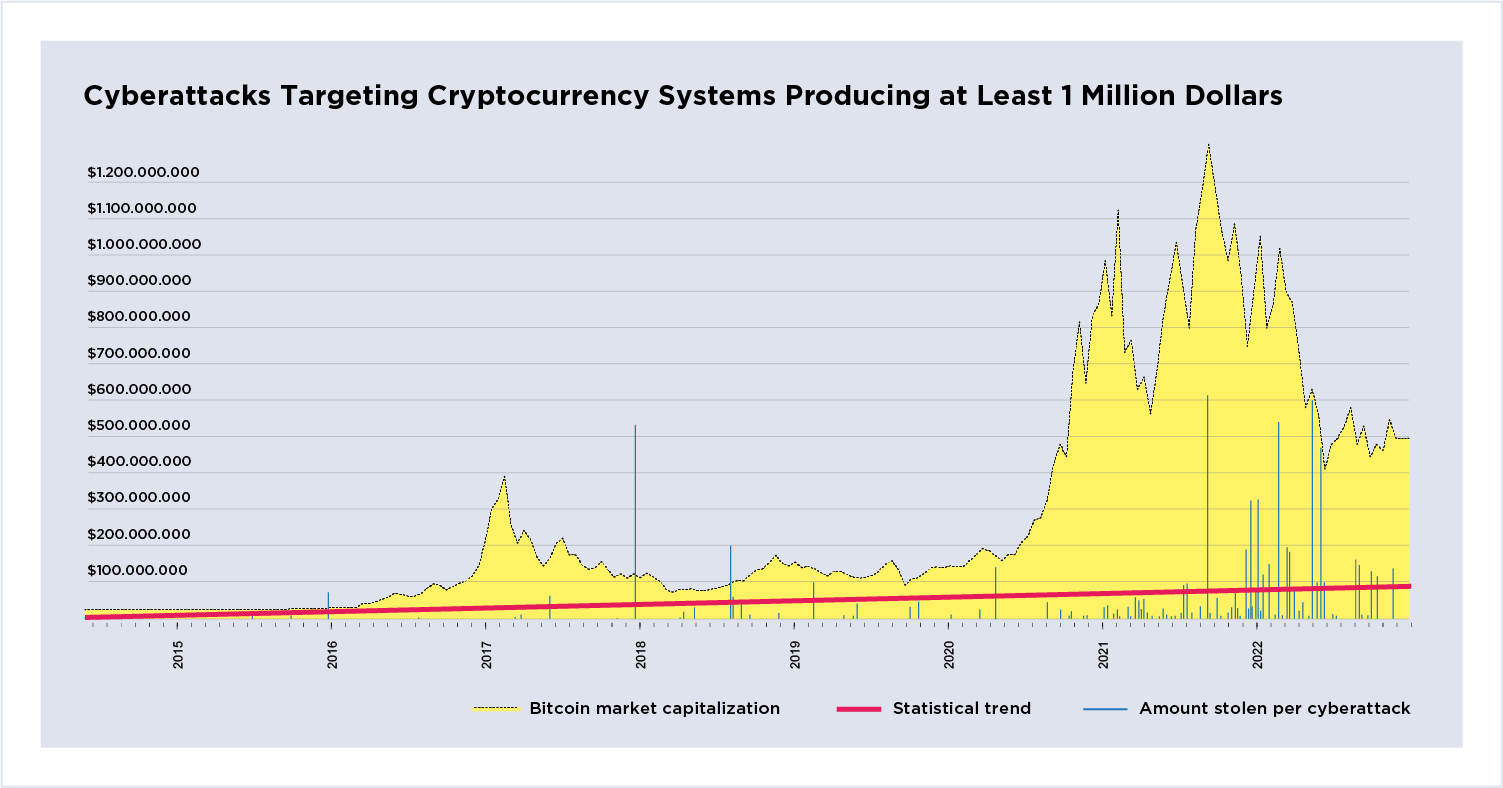
Figure 1: Cyberattacks targeting cryptocurrency
systems producing at least 1 million dollars.
The plot shows cyberattacks resulting in at least $1 million in asset theft by date, overlayed with total Bitcoin market capitalization. The red line is the statistical trend. Large cyberattacks are now trending towards $100 million. Peak market capitalization occurs between March and April and a second between October and November of 2021. The rising trend line and falling market capitalization indicate increasing pressures on the system that could create further instability within decentralized financial systems. Not shown in the figure are the 2011/2014 hacks of the MT Gox Bitcoin exchange.
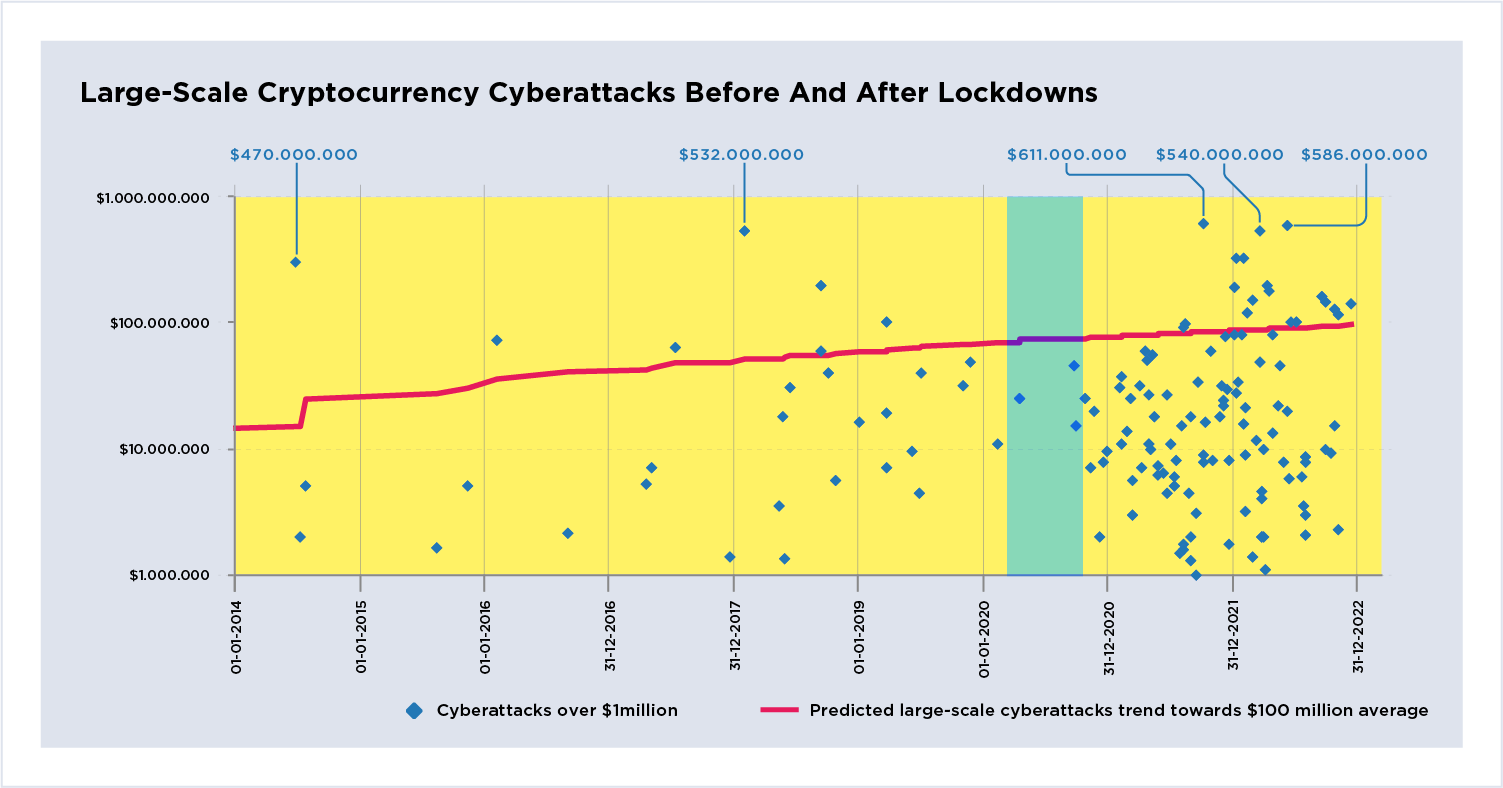
Figure 2: Large-scale cryptocurrency cyberattacks
before and after lockdowns.
The same datapoints from Figure 1 plotted on a logarithmic scale to show clustering. The red line remains the same trend line. This perspective highlights a denser cluster of cyberattacks occurring post-pandemic from mid-2020 onwards mostly focused between $5-$60 million. The blue semi-transparent vertical bar marks the approximate wave of initial global lockdowns between approximately spring and summer. Cyberattacks are becoming more concentrated against DeFi systems. The graph shows threat actors have well-established cyberattack activity against cryptocurrency platforms.
A Breakdown of Cyberattacks Relative to Bitcoin’s All-Time 2021 Peak Highlights How Threat Actors Adapt Tactics And Techniques to a Growing Financial Vertical
| 2014-2021 (seven years) |
2021-2023 (three years) |
Last half of 2022 (six months) |
|
| Cyberattacks valued over $1 million | 43 | 97 | 22 |
| Average cost in millions | 37 | 52 | 75 |
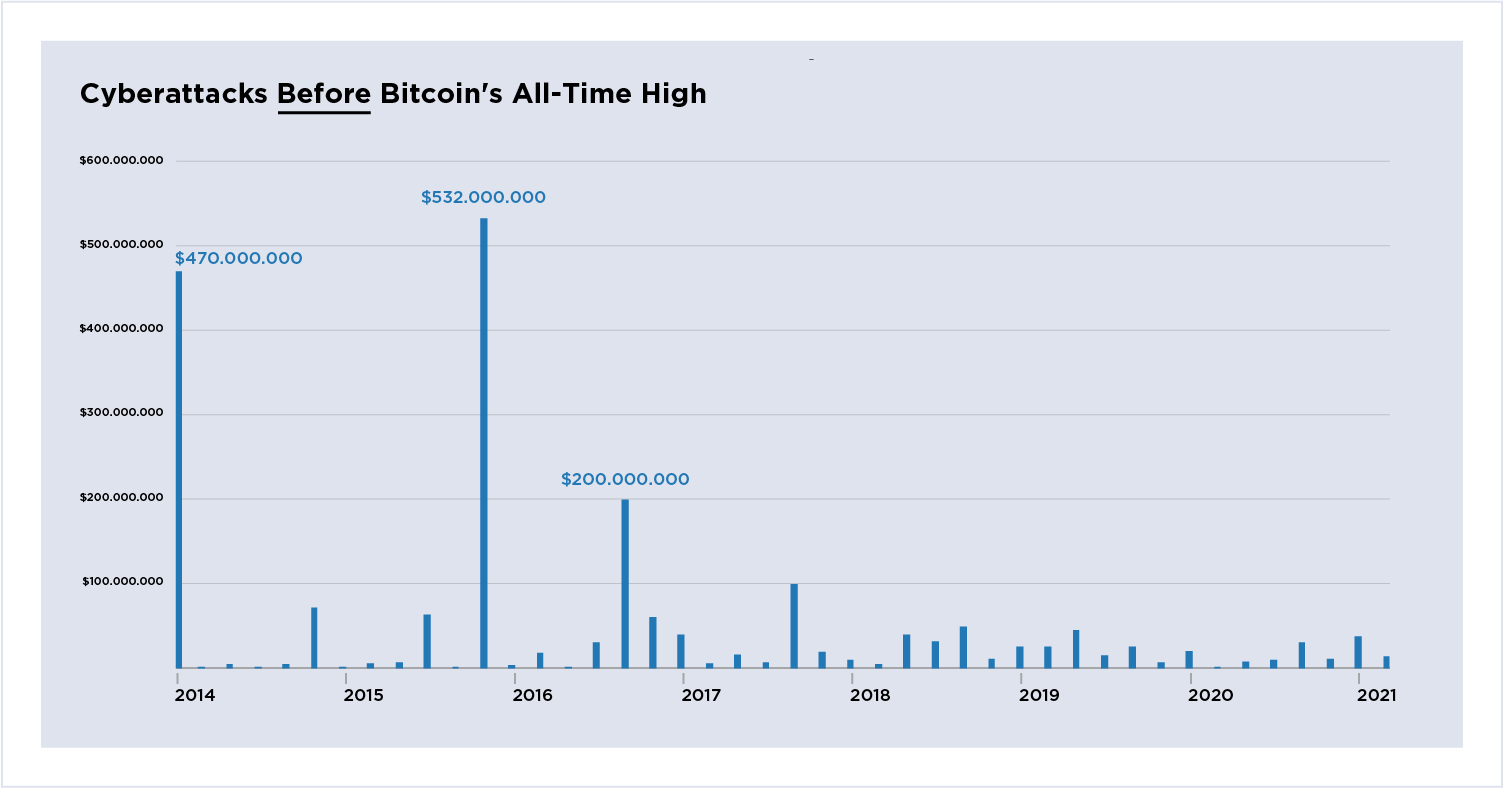
Figure 3: Cyberattacks before Bitcoin's all-time high, 2014-2021.
Large scale cyberattacks prior to Bitcoin's all time price peak of over $66000. The two significant outliers include MT Gox and Bitfinex. A majority of cyberattacks remain below $100 million and are relatively evenly spaced. The data shows a steady application of cyberattacks that do not grow in size and frequency -exhibiting a level of stability in terms of risk and losses.
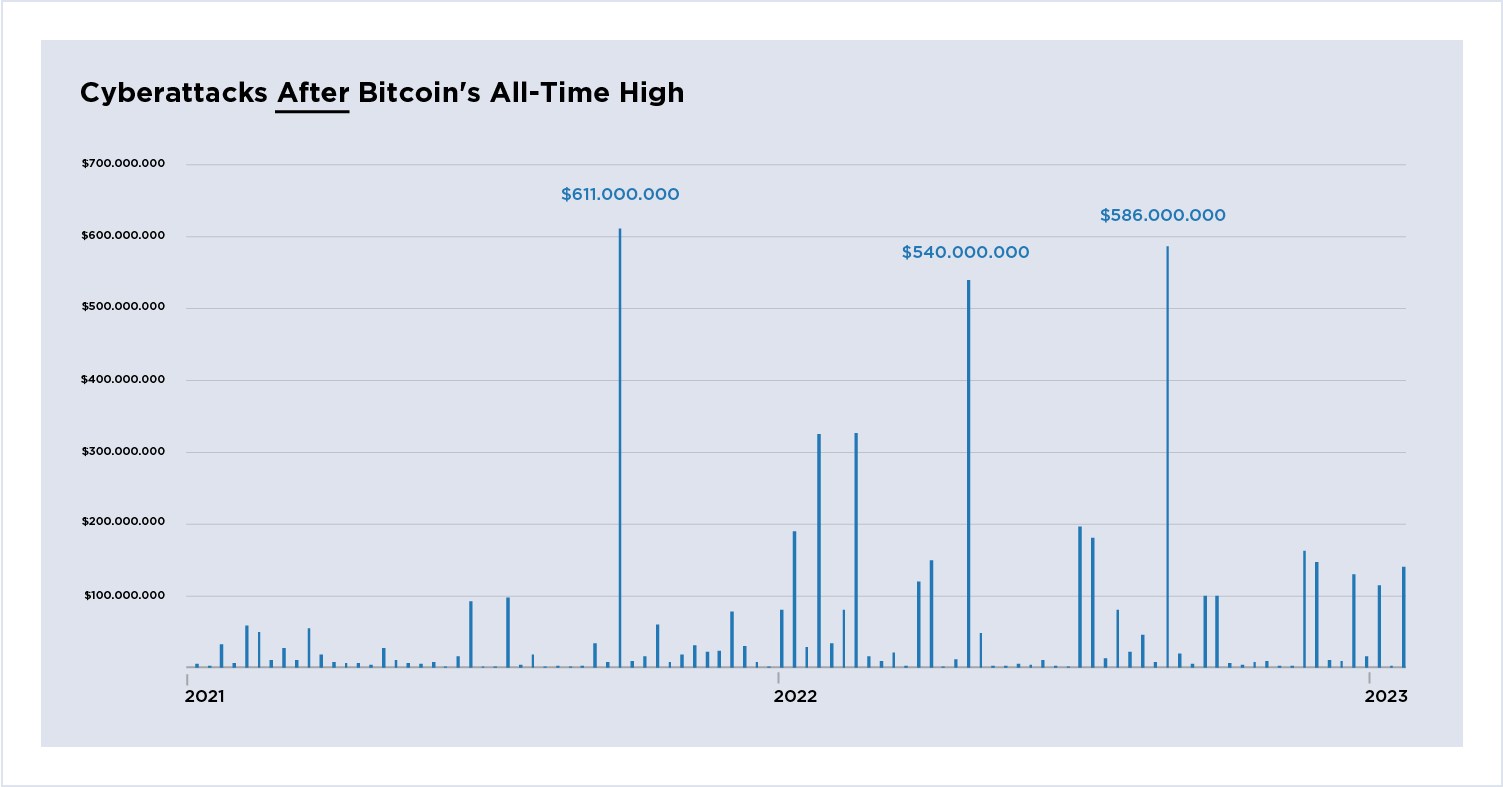
Figure 4: Cyberattacks after Bitcoin's all-time high, 2021-2023.
Large scale cyberattacks after Bitcoin's all-time price peak. Three significant outliers include Poly Networks, Ronin Bridge, and BNB Bridge. Figure 4 compared to Figure 3 shows growing rates of cyberattacks, which become more chaotic; increasing in both frequency and amount stolen. The graph is demonstrative of a system with decreasing stability in terms of risk and losses.
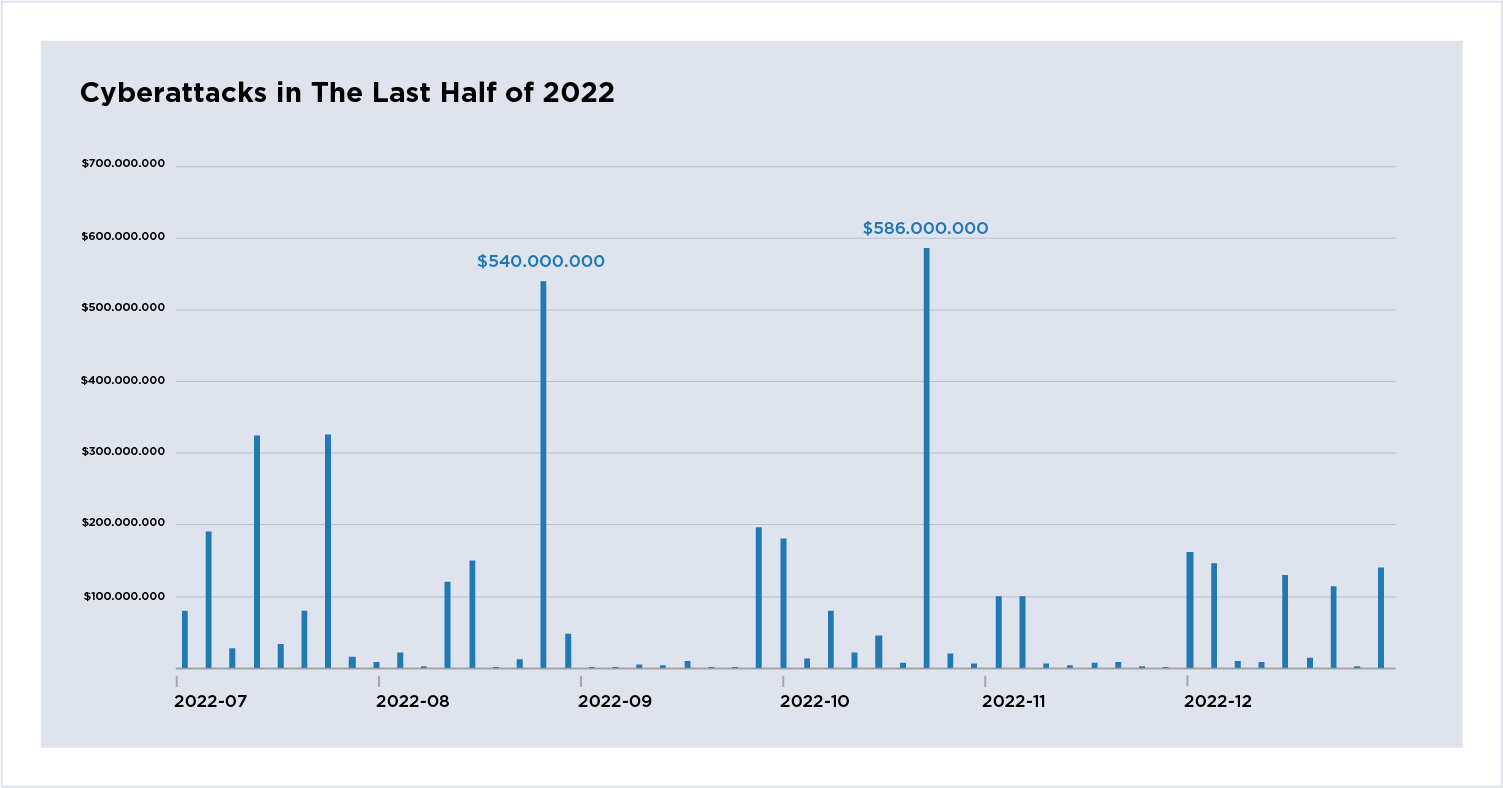
Figure 5: Cyberattacks in the last half of 2022.
Large scale cyberattacks in the last six months of 2022. The two significant outliers are again Ronin and BNB Bridges. Cyberattacks over the six-month period become increasingly erratic with more cyberattacks resulting in growing losses. The graph provides evidence that current trends are very likely to continue in the short term (two years).
The Primary Tactics And Techniques Used in Large Cyberattacks Involve Two Patterns With Distinct Solutions.
Smart Contract Code Running DeFi Systems Must be Subject to Accredited Transparent Review to Minimize Exploitation
Cryptocurrency systems are not sufficiently ensuring the integrity and capability of their infrastructure. Exploitation of misconfigurations for price manipulation is the most significant attack pattern. (6, 7) https://bishopfox.com/blog/decentralized-finance-blockchain-battleground Exploitation in these cases occurs through misconfigurations in code that almost always involves smart contracts. The FBI raised a warning of Flash-loan cyberattacks stemming from weaknesses in DeFi smart contracts in August 2022 (8) and the largest hack to date, Poly Networks, involved smart contract exploitation.
Another exploitation path takes advantage of pricing errors that almost always involve flash loans to achieve an unintended price discrepancy that benefits the threat actor’s transaction. The top 10 flash loan attacks together produced over half a billion dollars. (9) Flash loan attacks can also be controlled through 3rd party code review and testing to produce unintended outcomes. Testing should be conducted in a manner that is transparent to end-users, recognizable, and meets minimal standards and accreditation.
Signing Keys Must be Stored Offline For Maximum Security And Core Validation Systems Should Leverage Multi-Sign Technology in a Manner That is Transparent to End Users
Compromise of signing keys is the second primary pattern analyzed. With cryptocurrency, signing keys control access to wallets where assets are tracked. Keys to wallets must be stored offline or air-gapped to maximize security. With cyberattacks of this category, it is most common to target individual end-user's wallets through phishing and malicious Dapp downloads. It is also possible to accomplish key exposure by compromising systems within platforms that store signing keys -as was the case in the MT GOX hack, which remains an outlier to this day. EclecticIQ analysts note that 3rd party key exposure also remains prominent here, stemming from lack of controls and management for interoperating 3rd parties -as was the case with Axie Networks role in the Ronin Bridge cyberattack.
High-Risk Targets Must Segregate Assets (Vaults Aad Hot Wallets) And Security Controls to Limit The Effect of a Widespread Compromise Worst-Case Scenario
Threat actors seek to compromise signing keys within core privileged systems that underly the decentralized finance network’s operation. These attacks are more often more impactful because the privileged keys for core systems are typically designed to access greater asset resources. The Ronin Bridge hack remains a central example in the risks of weak implementation of core validation systems. and the Kukoin cyberattack attributed to North Korea is another good example (10). Open-source systems with bug bounty programs could provide further layers of testing and security. DeFi systems with higher interconnectivity to other DeFi entities where assets are concentrated, like Bridges, will remain the highest risk targets for largescale cyberattack.
Changes to The DeFi Landscape, Together With Increasingly Erratic Large-Scale Cyberattacks And The 2022 Collapse of Cryptocurrency Organizations (Crypto-Winter) Will Lead to Opportunities For Centralization
Cryptocurrency is very likely to consolidate after the current market downturn. Many decentralized finance companies will not survive, while others become stronger and more likely to increase market share. (11) Centralization will benefit those DeFi organizations currently more mature, that have greater resources to bridge into a more regulated landscape. Centralization in the short term is likely to create disproportionate risk to end users participating in relatively less or more mature cryptocurrency organizations. In the interim threat actors are likely to shift tactics to target less or more centralized cryptocurrency organizations depending on the strength and efficacy of developing regulation and security practices creating stronger vs. weaker targets. National regulations that become adopted will differ from state to state. Differences in centralized regulation are likely to create a widely uneven global cyberattack landscape. Cyberattack effects on central bank digital currencies are not yet clear because implementations remain very restricted.
Further Government Regulation Could Minimize Cyberattack Effects by Reducing Competition
Central governments are likely to exercise varying degrees of control of the cryptocurrency market through regulation and standardization in order to implement central bank digital currencies (CBDCs) alongside current cryptocurrencies. Many recent events demonstrate that more aggressive regulation is already underway. (12, 13, 14) CBDCs issued alongside "unofficial" cryptocurrencies could be granted a greater level of interoperability - and thus practicality and utility for end-users - to increase market share. A power dynamic could be created from this division of status and allowed to play out more passively and slowly behind the scenes, with the effect of CBDCs squeezing out current forms of cryptocurrency.
The Cryptocurrency Market Downturn And Recent Government Regulatory Signaling Will Likely Create an Environment Ripe For Further Increasing Cyberattacks Under a Variety of Threat Actors.
As new financial technology for cryptocurrency and centralized digital currency consolidates, developers and defenders are likely to remain at a disadvantage in the short term. While they adapt to a changing ecosystem, further regulation, and increasing network surface, threat actors are very likely to home in on the effective cyberattack vectors demonstrated above with great success. Strong working knowledge provides threat actors with a relative advantage currently.
The analysis of cybertheft against cryptocurrencies resulting in at least one million dollars stolen further reinforces the main cyberattack patterns highlighted in our last report. (2) Data shows threat actors have strong participation across the cryptocurrency landscape. Recent attacks are evidence rates will not abate in the short term. It is prudent to transfer mitigations outlined here to future versions of financial technology systems that will increasingly depend on cryptocurrency applications so that everyone involved can continue to iterate and enhance security practices surrounding this evolving financial landscape.
About EclecticIQ Intelligence and Research
EclecticIQ is a global provider of threat intelligence, hunting and response technology and services. Headquartered in Amsterdam, the EclecticIQ Intelligence and Research team is made up of experts from Europe and the U.S. with decades of experience in cybersecurity and intelligence in industry and government.
We would love to hear from you. Please send us your feedback by emailing us at research@eclecticiq.com or fill in the EclecticIQ Audience Interest Survey to drive our research toward your priority area.
You might also be interested in:
Polish Healthcare Industry Targeted by Vidar Infostealer Likely Linked to Djvu Ransomware
3CX Incident Attributed to North Korea; New LockBit MacOS Sample
Exposed Web Panel Reveals Gamaredon Group's Automated Spear Phishing Campaigns
Appendix
-
https://www.comparitech.com/crypto/biggest-cryptocurrency-heists/
-
https://www.pymnts.com/cryptocurrency/2023/crypto-hackers-stole-billions-last-year-targeting-defi/
-
https://blog.chainalysis.com/reports/2022-biggest-year-ever-for-crypto-hacking/
-
https://bishopfox.com/blog/decentralized-finance-blockchain-battleground
-
https://www.comparitech.com/crypto/biggest-cryptocurrency-heists/
-
https://hub.elliptic.co/analysis/top-five-defi-crime-trends-of-2022/
-
https://www.justice.gov/opa/press-release/file/1470186/download/

