Executive Summary
On 21st March 2023, EclecticIQ researchers detected a spearphishing email targeting the healthcare industry in Poland. The spoofed email was designed to appear as legitimately sent from a Polish government entity called the National Health Fund (Narodowy Fundusz Zdrowia - NFZ).
The email contained a malicious Microsoft Excel XLL attachment that can download and execute Vidar Infostealer malware upon user execution. Vidar can collect sensitive information from infected devices and potentially lead to ransomware, which puts the Polish healthcare industry at risk of losing critical data and disruption of systems.
The Vidar command and control (C2) infrastructure has multiple connections to recently observed ransomware attacks from LockBit 2.0 and Djvu. Due to these overlaps, EclecticIQ researchers assess with high confidence that the observed spearphishing attack on a hospital in Poznań, Poland, was carried out by a Ransomware affiliated member or group of individuals.
Vidar is capable of stealing sensitive data from the infected system such as digital crypto wallets, messaging apps, credentials from web browsers and Two-Factor Authentication codes (2FA) from browser extensions like Authy, EOS and GAuth Authenticator. Annex 1 lists browsers and applications targeted by Vidar.
Delivering Malicious XLL Files via Spear Phishing Email
The infection chain starts with an email containing a Microsoft Excel XLL attachment. The email is addressed to szpital@lutycka.pl - the Provincial hospital in Poznań. If the attachment is opened, it will start downloading Vidar infostealer malware along with a decoy Excel sheet from app4j[.]org.
- hxxps[://]app4j[.]org/Date2023[.]zip (Vidar Infostealer)
- hxxps[://]app4j[.]org/Wyciek-NFZ-16-03-2023[.]xlsx (Decoy Excel sheet)
A .XLL file is an Excel add-in file. Excel add-in files are similar to DLL files, except they are built specifically for Excel. They allow users to extend the functionality of Microsoft Excel by adding custom functions and features.
Malware authors used an open-source tool called “Excel-DNA” as one of the common tools for creating malicious XLL files. A XLL file written in .NET language is compiled within a standalone file containing functions that map native exports to the CLR functions, contained in a user-defined assembly DLL embedded in the resource section of the file generated by Excel-DNA. [1]
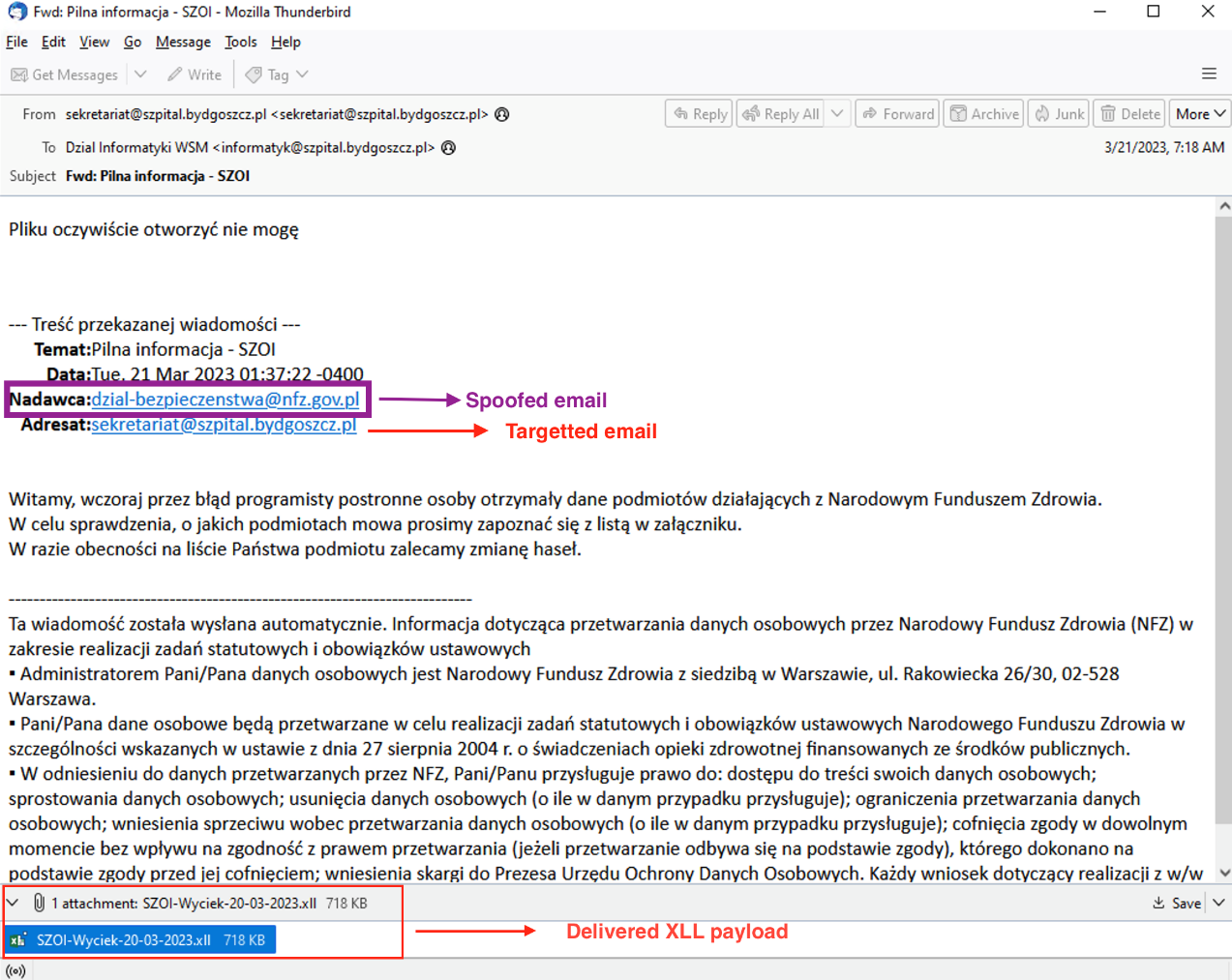
Figure 1 – Spear phishing email and XLL payload [2].
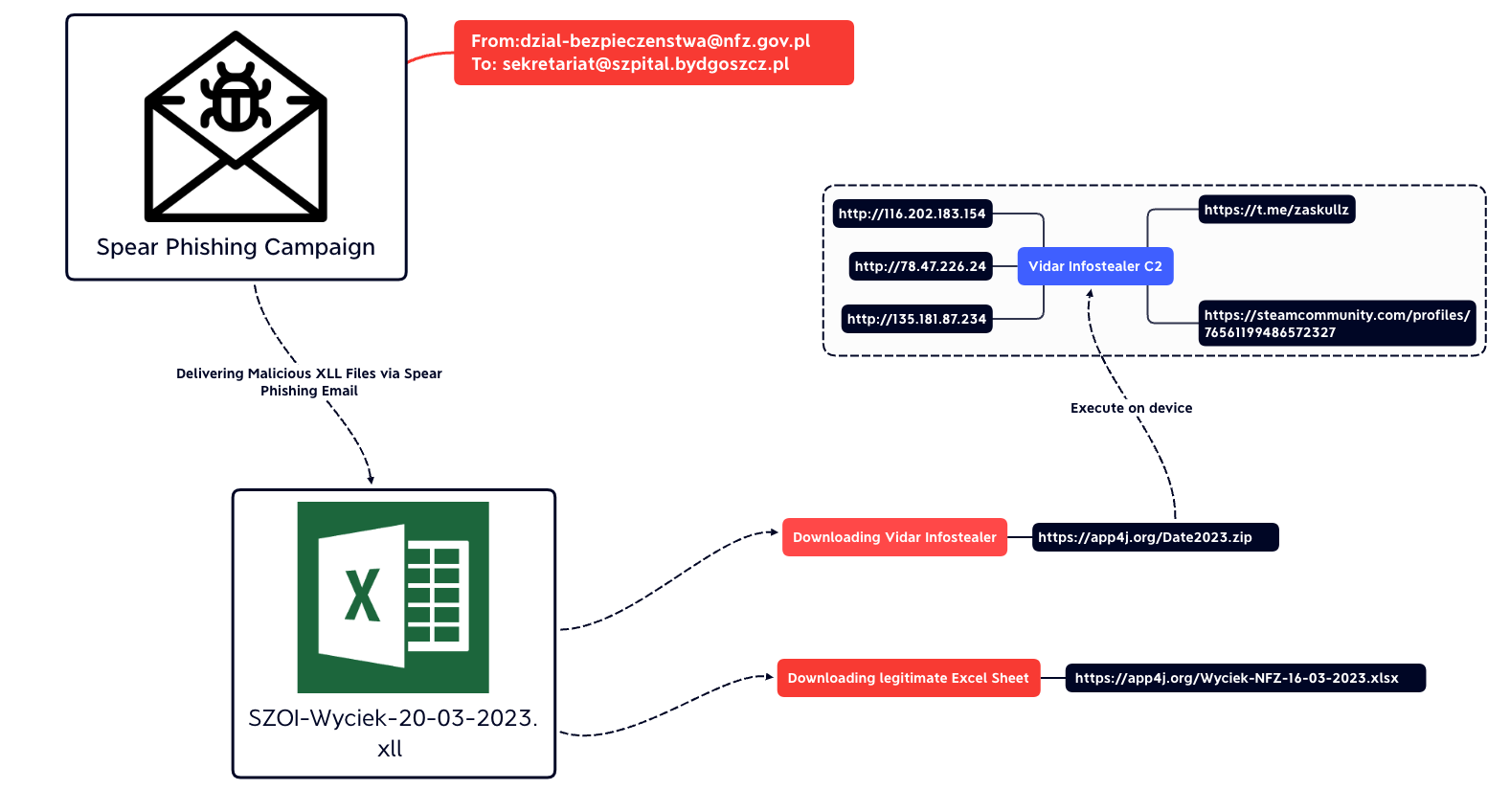
Figure 2 – Details of the malware infection chain.
Weaponization of Excel Add-Ins
EEclecticIQ researchers analyzed the malicious XLL file (SZOI-Wyciek-20-03-2023.xll) and discovered it was generated by Excel-DNA.
The file can execute itself through the AutoOpen function after user interaction. The AutoOpen function downloads two files: A ZIP file (the Vidar infostealer) and a decoy Excel file (XLSX). After downloading, it starts to unzip Vidar and waits for 1.5 seconds before execution. Details are shown in Figure 3.
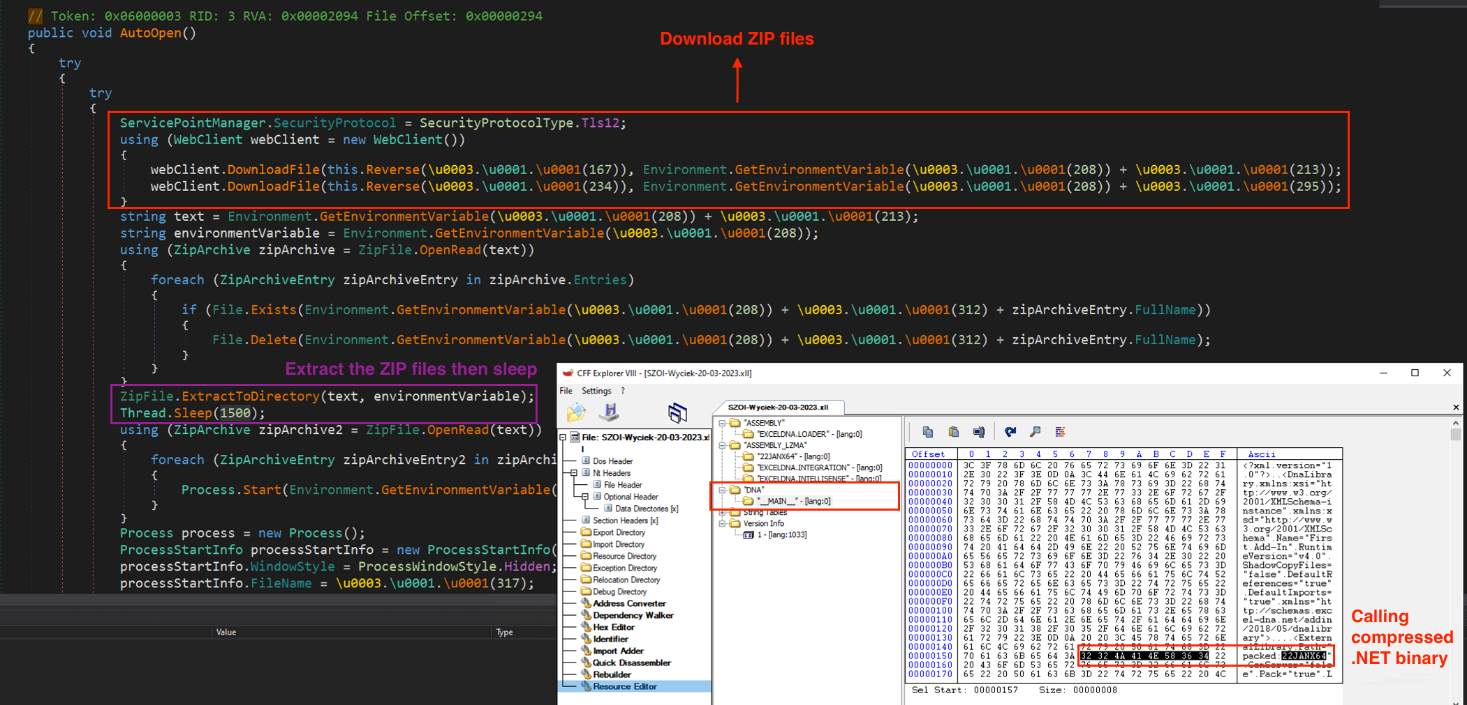
Figure 3 – The resource section of SZOI-Wyciek-20-03-2023.xll
and AutoOpen function inside the XLL file.
The downloaded decoy XLSX file contains data about hospitals in Poland:
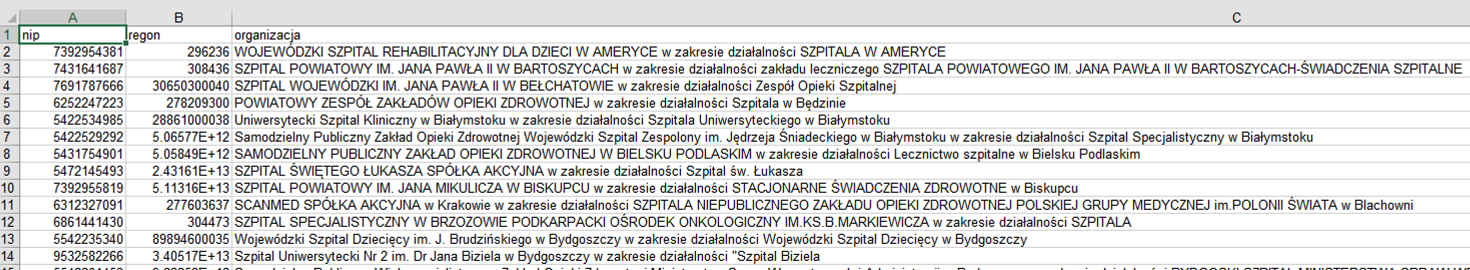
Figure 4 – Content of decoy XLSX file.
The downloaded ZIP files are saved in the C:\Windows\temp\ folder:
- Date2023.exe: Unzipped Vidar infostealer.
- FileTest.zip: Zipped version of Vidar.
- Excel.xlsx: Decoy Excel file.
After successful infection, the child process of Excel.exe contains Date2023.exe (Vidar). The description section of the Vidar infostealer is named "Avira Security." The threat actor likely chose this description to avoid unwanted attention from the user or to evade detection, although this technique is not effective against modern AV/EDR vendors.

Figure 5 – Process tree shows the spawned Vidar
as DATE2023.exe inside Excel.
Capabilities of Vidar Infostealer
Vidar is a malware designed to steal sensitive information from infected systems. It is known for its ability to evade detection and analysis using various techniques.
One of the primary evasion techniques used by Vidar is packing and XOR encryption routines. These conceal its malicious code and prevent detection by security solutions. The malware also uses anti-debugging and anti-emulation techniques, making it difficult to analyze it in a sandbox environment.
Figure 6 shows the packed version of Vidar, which will start unpacking itself after loading the encrypted section from data section of the Vidar executable (RSRC / RT_RCDATA) by calling the LoadResource() Windows API.
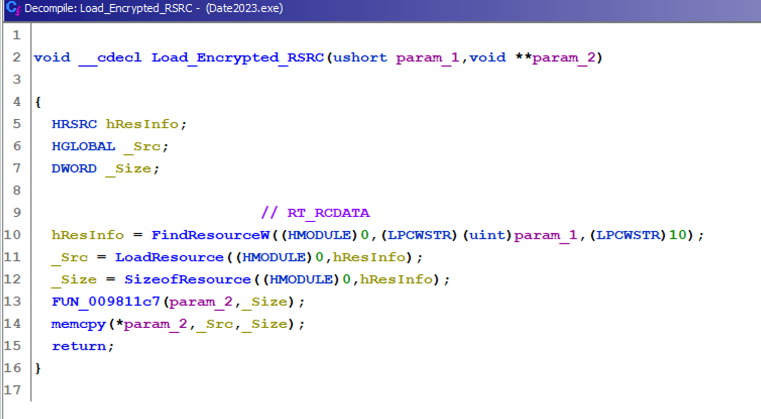
Figure 6 – Loading encrypted data from RSRC.
The XOR decryption routine uses the first 24 bytes of the string from data section (RSRC / RT_RCDATA) "ANu$_Joe_B1den@798576564" as an XOR key to decrypt the final payload from RSRC. EclecticIQ researchers detected more Vidar samples that are using the same XOR key, and that are likely related to the same campaign. The malware hashes are available in our public STIX collection.
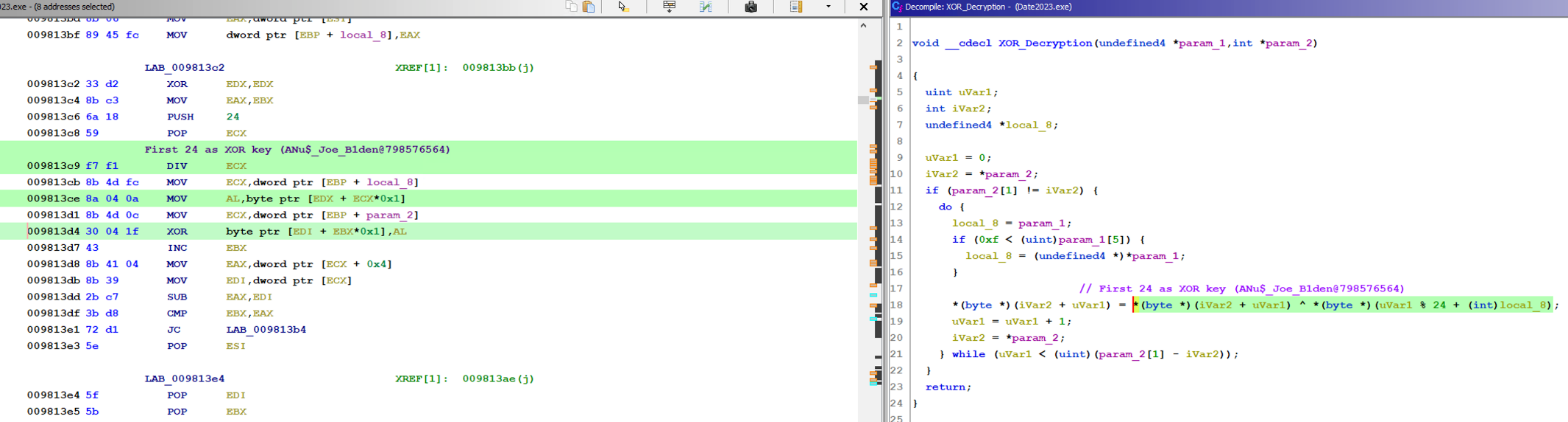
Figure 7 – XOR decryption routine used for unpacking
process during the execution of Vidar.
Figure 8 shows the content of the encrypted final payload from RSRC. After the 24-byte XOR key has been removed from the data, it is ready to be decrypted during the execution time of Vidar. This technique is used to evade detection by decrypting the malware only at execution time.
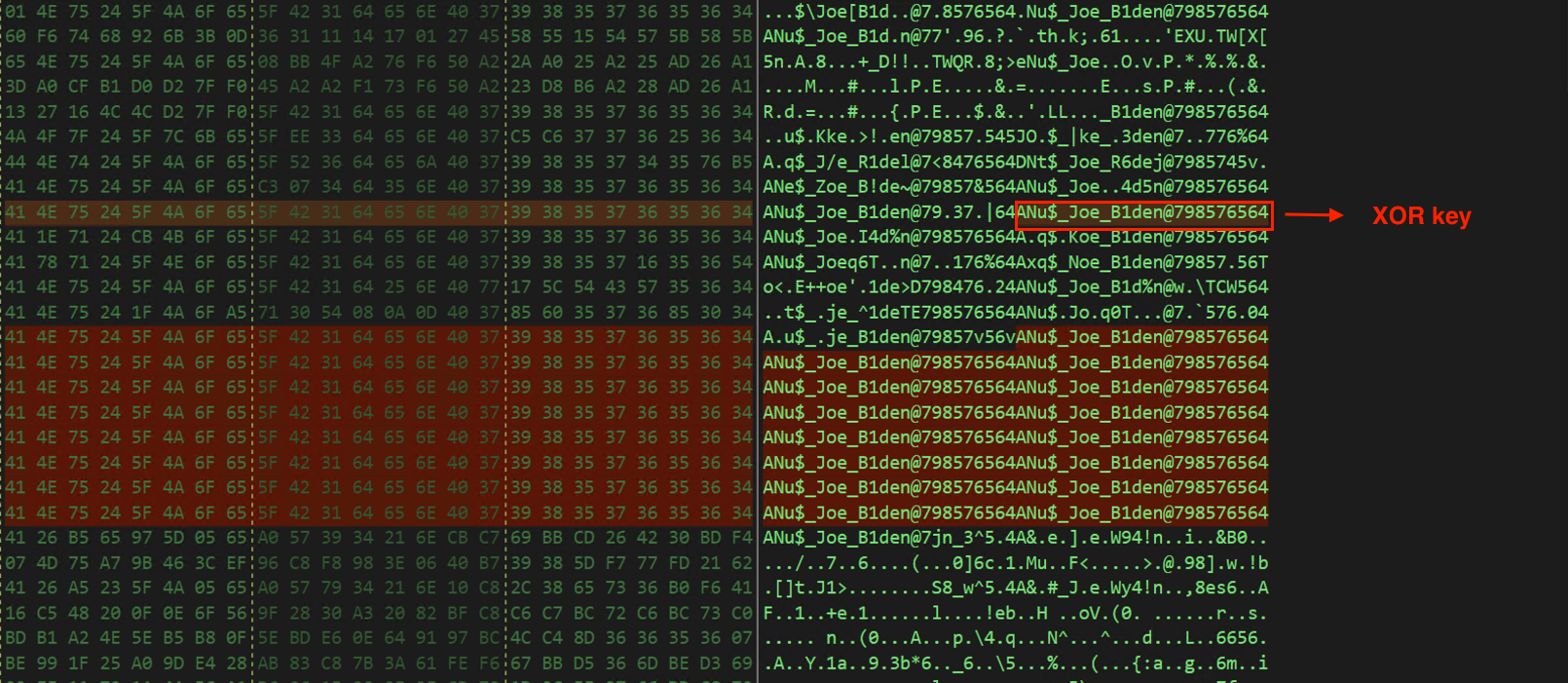
Figure 8 – XOR key inside encrypted RSRC data.
After the decryption process, it will allocate the unpacked version using the VirtualAlloc() Windows API.
Figure 9 shows the disassembled Vidar infostealer containing three different functions to load final payload (decrypted RSRC) into memory region:
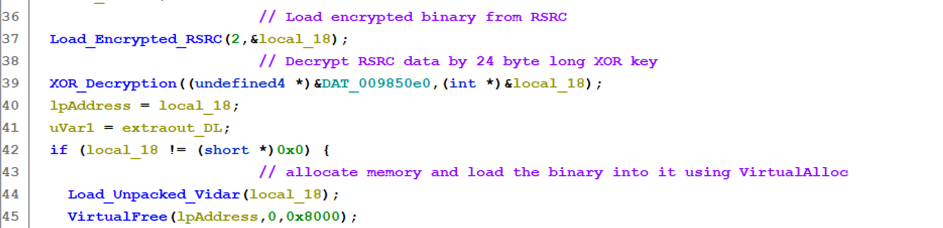
Figure 9 – XOR decryption and final payload loader function.
EclecticIQ researchers used the 24-byte long XOR key to unpack Vidar. Figure 10 shows the unpacking process by a python script used for XOR decryption:
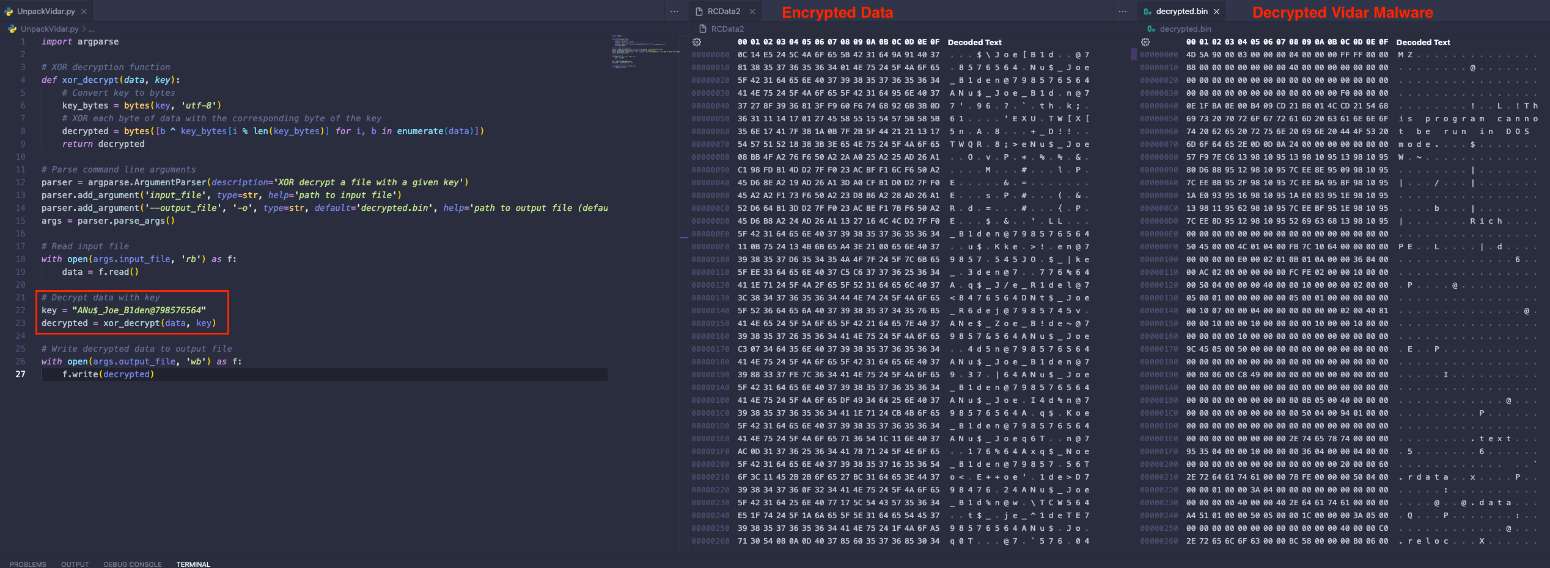
Figure 10 – Encrypted RSRC data is a final Vidar binary after manual decryption.
Data Exfiltration Over C2 Telegram Channel
Stolen victim data is exfiltrated to multiple C2 servers controlled by the threat actor. Upon the execution of Vidar, it starts sending GET requests to legitimate web servers like Telegram and Steam to get up to date C2 IP addresses like in figure 11.
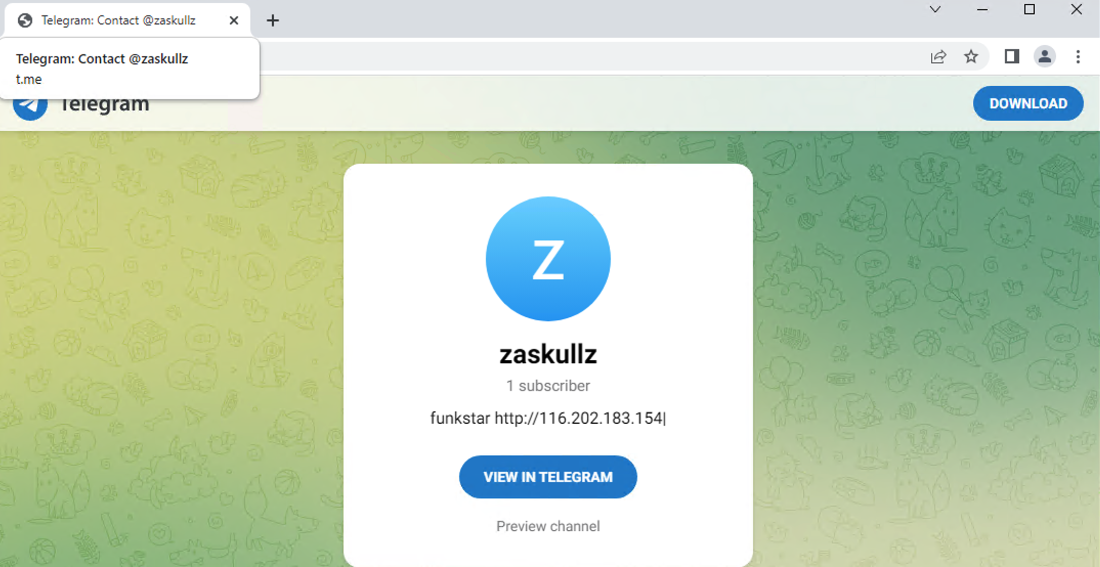
Figure 11 – Vidar C2 Telegram channel.
Below is a list of C2 servers observed after the infection:
- hxxp[://]135[.]181[.]87[.]234
- hxxps[://]steamcommunity[.]com/profiles/76561199486572327
- hxxp[://]78[.]47[.]226[.]24
- hxxps[://]t[.]me/zaskullz
- hxxp[://]116[.]202[.]183[.]154
C2 connections made by a generic User Agent like below:
- Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36 Edg/107.0.1418.26/8mqLqMuL-37
Possible Ransomware Attack on the Polish Healthcare Industry
The Polish healthcare industry has become a frequent target of ransomware attacks in recent years. These attacks have caused significant disruptions to healthcare services, potentially jeopardizing the health and well-being of patients across the country. [3]
EclecticIQ researchers identified a connection between the Vidar C2 addresses in this campaign and a Djvu Ransomware sample - 0f9677642599cf23aafe225ee2dbe403f305dc5801298b83ba19f6b939a8f914. [4]
The Vidar C2 address was previously (2023-03-20) used by Djvu ransomware operators to collect sensitive information from victim devices before initiating the ransomware encryption. In this way, threat actors can use the stolen data as a pivot point to increase the effectiveness of the ransomware attack.
Analysts also identified a ZIP folder written in Korean that contains a LockBit 2.0 ransomware sample (9916a835c20ea3eb75657f34eeb0fa152e72b374954bea087445d7e383e68455) [5] alongside a Vidar Infostealer. Both are in executable file format, and the Vidar sample is connecting to the same C2 address - 116[.]202[.]183[.]154.
Figure 12 shows the pivoted ZIP folder from hxxp[://]116[.]202[.]183[.]154 (one of the Vidar C2 servers).
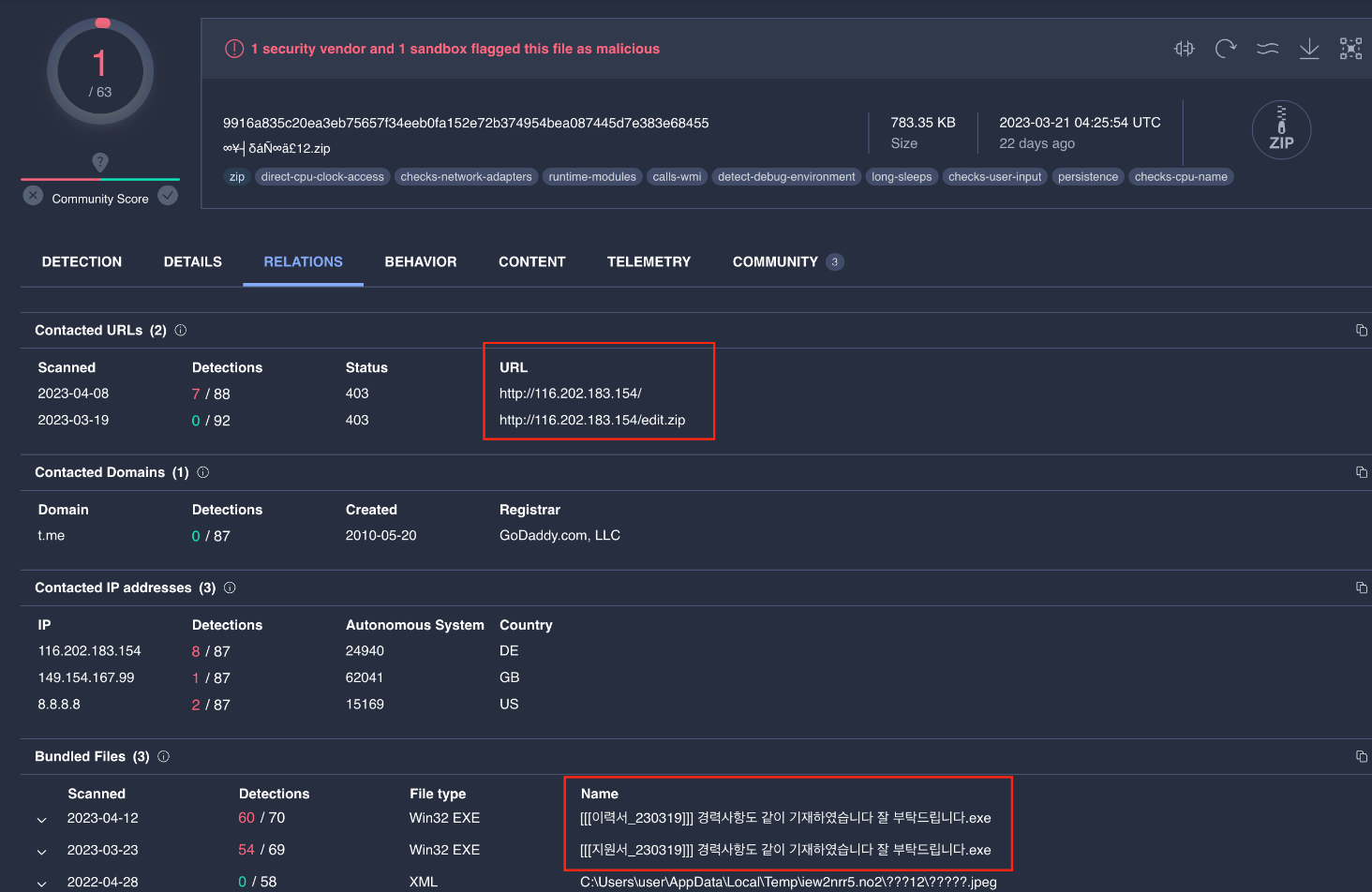
Figure 12 – LockBit 2.0 Ransomware and Vidar infostealer
inside a delivered ZIP folder.
Figure 13 shows the overlaps between C2 servers of Vidar infostealer used in malware delivery campaign against Polish healthcare entities on 21st March 2023 and Ransomware samples in the wild using Vidar.
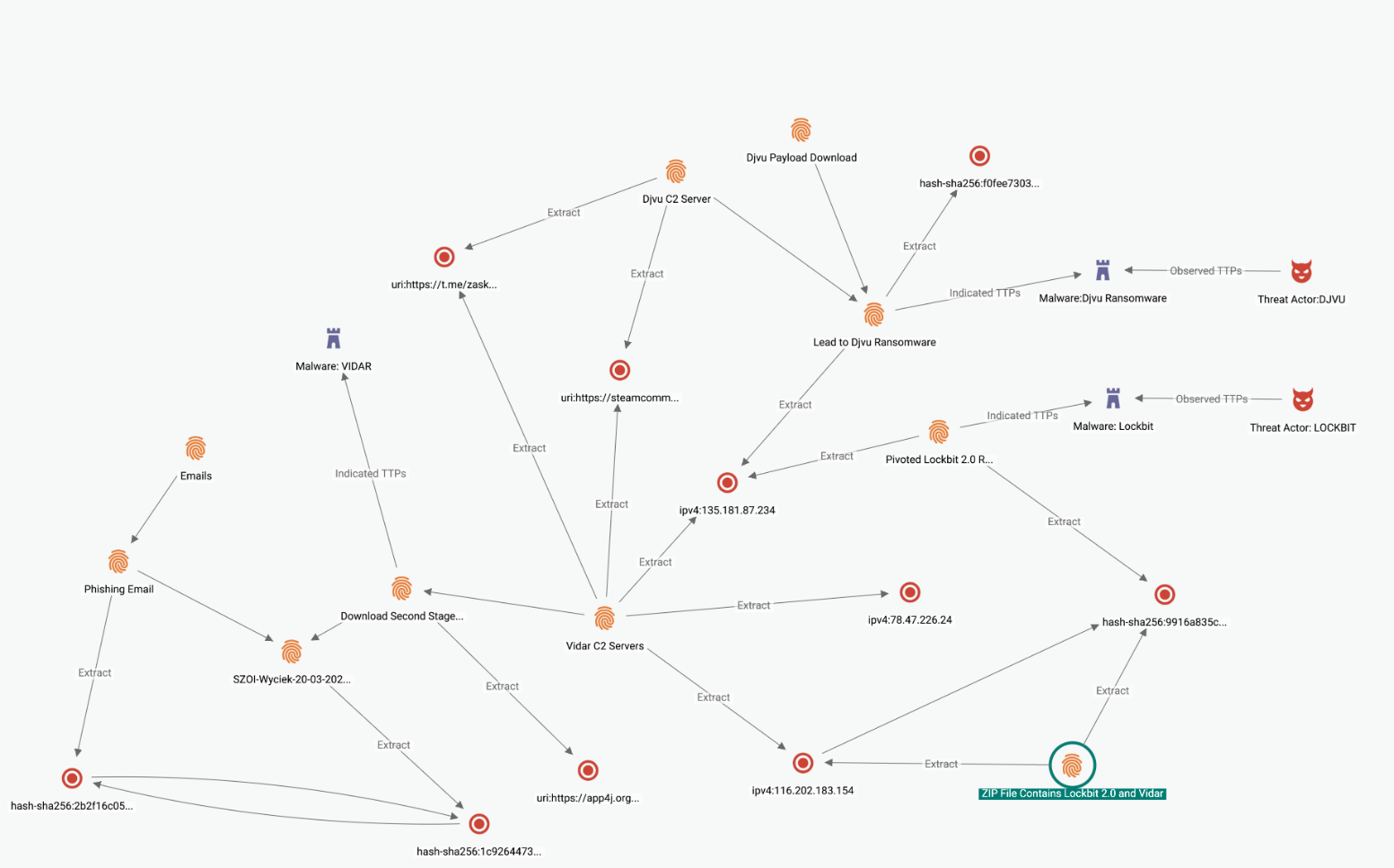
Figure 13 – Overlaps graph on EclecticIQ threat intelligence
platform Intelligence Center.
Outlook
- EclecticIQ analysts assess with high confidence that the Polish healthcare industry will continue to face ransomware attacks in the near future. The healthcare sector has been a prime target for cybercriminals due to the sensitive nature of patient data and the potential for financial gain through ransom payments.
- Threat actors very likely used Vidar infostealer before launching a ransomware attack. By stealing sensitive information, this can increase the potential pay-out from a ransomware attack by threatening to leak the stolen data if the victim does not pay the ransom. Additionally, Vidar infostealer may be used to gather information about a victim's system and network, which can be used to increase the effectiveness of the ransomware attack.
- Various Ransomware groups like GrandCrab, LockBit and Djvu used Vidar stealer in the process for distributing the ransomware as a second stage payload. It is important to note that the usage of Vidar infostealer before a ransomware attack is a significant threat to organizations and individuals alike. By stealing sensitive information, cybercriminals can cause significant damage to victims' reputations, finances, and privacy. Furthermore, the potential loss of critical data can disrupt operations and lead to financial and legal repercussions. EclecticIQ researchers assess with high confidence that double extortion tactics very likely will increase amongst Ransomware groups. [6], [7].
Recommendations
1. Implement Email Authentication: Spear phishing attacks rely on fraudulent emails that appear to be from a trusted source. Implementing email authentication mechanisms such as Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC) can help prevent email spoofing and ensure that emails are originating from a trusted source.
2. Use Anti-Phishing Filters: Anti-phishing filters can identify and block suspicious emails, including those containing phishing links or malicious attachments. These filters can be integrated into email clients or gateway appliances to detect and block such emails.
3. Provide Security Awareness Training: Train your employees to be vigilant and recognize the signs of a phishing email. This can include training on how to identify phishing links, spoofed email addresses, and suspicious attachments.
4. Implement Least Privilege Access: Limit the access privileges of employees to only those resources that are necessary for them to perform their job functions. This can help prevent attackers from gaining access to sensitive data or systems through compromised credentials.
5. Regularly Backup Data: Regularly backing up critical data can help mitigate the impact of a successful ransomware attack. This way, even if an attacker manages to encrypt your data, you can restore it from a backup rather than paying the ransom. Ensure that backups are stored securely and not directly accessible from your network.
6. Use strong passwords and two-factor authentication: Strong passwords and two-factor authentication can prevent unauthorized access to your accounts, even if an infostealer manages to steal your login credentials.
MITRE ATT&CK
|
TTP ID |
Techniques |
|
T1566 |
Spearphishing Attachment |
|
T1204 |
User Execution: Malicious File |
|
T1027 |
Obfuscated Files or Information: Software Packing |
|
T1071 |
Application Layer Protocol: Web Protocols |
|
T1104 |
Multi-Stage Channels |
|
T1137.006 |
Office Application Startup: Add-ins |
|
T1555 |
Credentials from Password Stores |
|
T1539 |
Steal Web Session Cookie |
|
T1552 |
Unsecured Credentials |
|
T1087 |
Account Discovery |
|
T1518 |
Software Discovery |
|
T1057 |
Process Discovery |
|
T1614.001 |
System Location Discovery: System Language Discovery |
|
T1041 |
Exfiltration Over C2 Channel |
|
T1497 |
Virtualization/Sandbox Evasion |
|
T1027.009 |
Obfuscated Files or Information: Embedded Payloads |
|
T1105 |
Ingress Tool Transfer |
Annex 1 – Vidar capabilities
Targeted web browsers
|
Web browser |
|
Google Chrome |
|
Chromium |
|
Amigo |
|
Torch |
|
Vivaldi |
|
Comodo Dragon |
|
EpicPrivacyBrowser |
|
CocCoc |
|
Brave |
|
Cent Browser |
|
7Star |
|
Chedot Browser |
|
Microsoft Edge |
|
360 Browser |
|
QQBrowser |
|
CryptoTab |
|
Opera Stable |
|
Opera GX Stable |
|
Mozilla Firefox |
|
Pale Moon |
|
Epic Privacy Browser |
Targeted browser extensions
|
TronLink |
Targeted desktop software
|
Software Name |
|
Telegram Desktop |
|
Thunderbird |
|
Discord |
|
WinSCP |
|
Steam |
|
FileZilla |
|
Bitcoin Core |
|
Bitcoin Core Old |
|
Dogecoin |
|
Raven Core |
|
Daedalus Mainnet |
|
Blockstream Green |
|
Wasabi Wallet |
|
Ethereum |
|
Electrum |
|
ElectrumLTC |
|
Exodus |
|
Electron Cash |
|
MultiDoge |
|
Jaxx Desktop (old) |
|
Jaxx Desktop |
|
Atomic |
|
Binance |
|
Coinomi |
About EclecticIQ Intelligence & Research Team
EclecticIQ is a global provider of threat intelligence, hunting, and response technology and services. Headquartered in Amsterdam, the EclecticIQ Intelligence & Research Team is made up of experts from Europe and the U.S. with decades of experience in cyber security and intelligence in industry and government.
We would love to hear from you. Please send us your feedback by emailing us at research@eclecticiq.com.
You might also be interested in:
3CX Incident Attributed to North Korea; New LockBit MacOS Sample
Exposed Web Panel Reveals Gamaredon Group's Automated Spear Phishing Campaigns
Dark Pink APT Group Strikes Government Entities in South Asian Countries
References
[1] “Threat Spotlight: XLLing in Excel - threat actors using malicious add-ins,” Cisco Talos Blog, Dec. 20, 2022. https://blog.talosintelligence.com/xlling-in-excel-malicious-add-ins/ (accessed Apr. 25, 2023).
[2] “VirusTotal - File - 2b2f16c0535f90f325e46946ee695e830296e5eb18032db7233921bea65fb599.” https://www.virustotal.com/gui/file/2b2f16c0535f90f325e46946ee695e830296e5eb18032db7233921bea65fb599 (accessed Apr. 25, 2023).
[3] S. Christensen, “Increasingly frequent attacks by hackers on hospitals also in Poland also in Poland,” Business news from Poland, Mar. 01, 2022. https://news.bizinpoland.com/index.php/2022/03/01/increasingly-frequent-attacks-by-hackers-on-hospitals/ (accessed Apr. 25, 2023).
[4] “VirusTotal - File - 0f9677642599cf23aafe225ee2dbe403f305dc5801298b83ba19f6b939a8f914.” https://www.virustotal.com/gui/file/0f9677642599cf23aafe225ee2dbe403f305dc5801298b83ba19f6b939a8f914 (accessed Apr. 25, 2023).
[5] “VirusTotal - File - 9916a835c20ea3eb75657f34eeb0fa152e72b374954bea087445d7e383e68455.” https://www.virustotal.com/gui/file/9916a835c20ea3eb75657f34eeb0fa152e72b374954bea087445d7e383e68455 (accessed Apr. 25, 2023).
[6] “GandCrab Operators Use Vidar Infostealer as a Forerunner,” BleepingComputer. https://www.bleepingcomputer.com/news/security/gandcrab-operators-use-vidar-infostealer-as-a-forerunner/ (accessed Apr. 25, 2023).
[7] Sanseo, “How Infostealer Threat Actors Make a Profit,” ASEC BLOG, Jan. 03, 2023. https://asec.ahnlab.com/en/45150/ (accessed Apr. 25, 2023).