Executive Summary
EclecticIQ researchers identified a spearphishing campaign that leverages exploited Zimbra and Roundcube email servers to target government organizations.
Analysts assess with high confidence that the threat actor probably compromised government owned Zimbra and Roundcube email servers and used these to send spearphishing emails to other government entities.
The malicious emails contained Zimbra maintenance phishing lures to deceive recipients and steal email credentials.
The campaign had been underway since as early as January 2023. Most of the analyzed phishing emails target government entities in Ukraine. Analysts also identified lures aimed at government bodies in Spain, Indonesia, and France.
Key Findings
- The actor probably exploited vulnerabilities in the Zimbra and Roundcube webmail portals. The portals are publicly accessible and at the time of reporting are running outdated versions.
- The webmail portals were used to distribute spearphishing emails targeting other government organizations.
- Analysis of email headers indicates that the threat actor successfully circumvented anti-spam filters of targeted government organizations. These findings suggest that the threat actor employed evasive tactics throughout the operation.
- According to “Originating-IP” email header section in the observed emails, the threat actor very likely used VPN services to hide its real identity.
- The threat actor abused legitimate web services like Google Firebase, MailChimp, chilipepper.io, and webflow.io to collect email credentials.
Zimbra Maintenance Phishing Lures & Legitimate Web Services Abused for Credential Collection
Analysts assess with moderate confidence that a threat actor gained access to Zimbra and Roundcube email servers of several organizations and used the systems to send phishing lures mostly to other government organizations.
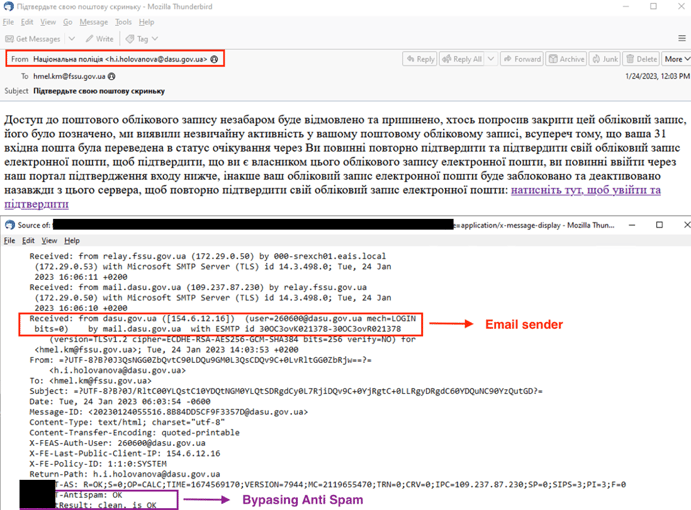
EclecticIQ analysts discovered 12 phishing emails that contained Zimbra lures. The emails were sent from email accounts of various government organizations. Analysis of the email headers revealed that the sender address was not spoofed. Analysts also discovered a commonality among the sender organizations - they either use Zimbra or Roundcube as the email server.
Figure 1 provides a visual representation of the organizations and countries affected by this campaign.
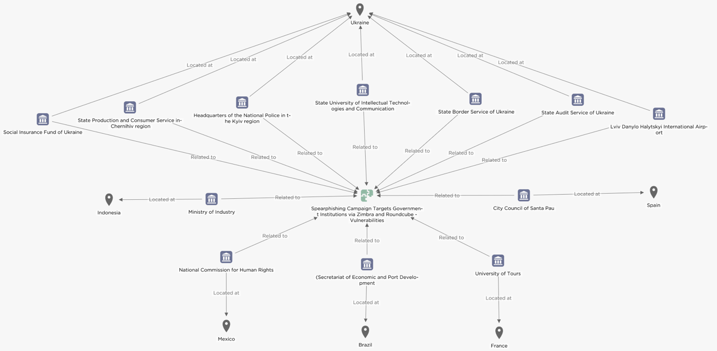
Figure 1 – Visual representation of the organizations and countries affected by this campaign (click image to open in separate tab).
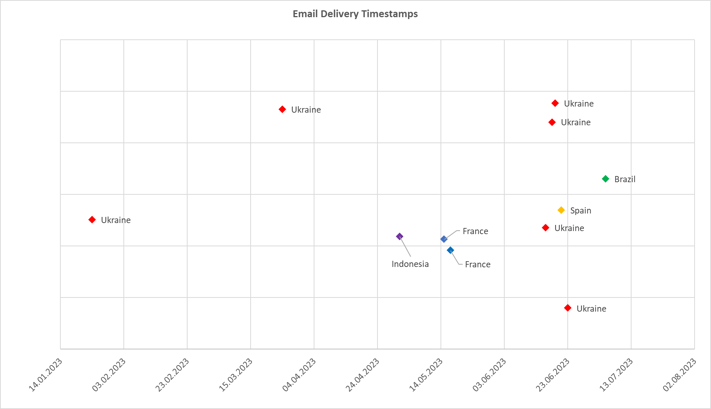
Analysts observed that most of the detected lures were sent to recipients in Ukraine and Indonesia, predominantly in mid-June. The earliest phishing email observed dates from January 2023 (figure 2).
Figure 2 – Email delivery timestamps and targeted countries.
Figure 3 shows a phishing lure utilizing a fake Zimbra maintenance notification alert. The language within the email is changed for each recipient to align with their spoken language but the phishing lure remains the same.
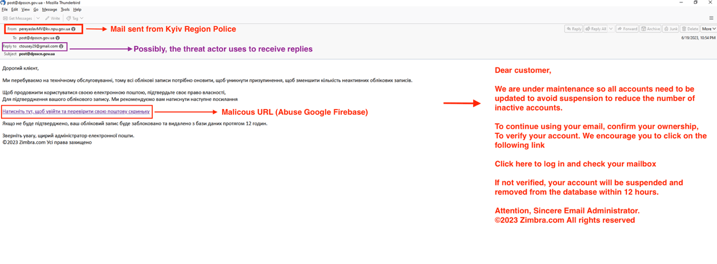
Figure 3 – Zimbra phishing lure in Ukrainian.
In another example (figure 4), the threat actor used the same Zimbra lure in Spanish to target Spanish-speaking victims. The email was sent from an email server of the City Council of Santa Pau, Spain.
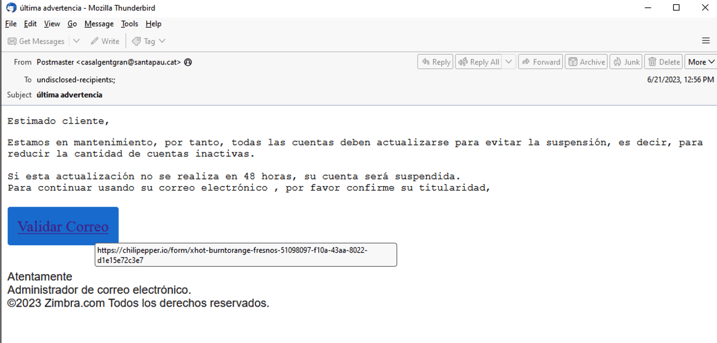
Figure 4 – Zimbra phishing lure in Spanish.
The email headers (figure 5) show that the sender addresses are not spoofed, which means they were sent from legitimate sources of compromised government email servers and bypassing anti-spam filters.
Figure 5 – Email header.
The primary objective of the threat actor is almost certainly to trick victims into clicking on a malicious link embedded in the email body, which redirects to a fake Zimbra email login page (figure 6). The actor used legitimate web services to collect the credentials. Analysts observed the following services:
- Google Firebase
- MailChimp
- Chilipepper.io
- Webflow.io
Figure 6 – Examples of Zimbra Phishing Templates.
The credentials entered on the fraudulent pages are sent to the following compromised WordPress websites for collection:
- pimm-blaj[.]ro
- revistafiscala[.]ro
- sangwishsa[.]com
Email Address in Reply-To Field Suggests Link to Russian Hacking Forum
One of the emails (figure 7) also contains a "reply-to” address - ctousey29[@]gmail.com - that is very likely owned or controlled by the threat actor. If a victim clicks on the reply button, the email client would use this address instead of the legitimate sender addresses.
It is almost certain that the actor used the “reply-to” field to avoid a target’s reply being sent to the sender address, which could have raised suspicion.
The redirect to an external address also indicates that the actor may not have had full control of the Zimbra Email servers. It is plausible that the actor was only able to send emails but did not have access to inboxes.
Analysts observed that a similar email address - ctousey[@]gmail.com - is tied to an account in a Russian speaking hacking forum called Exploit.in. Exploit.in is a popular hacking forum that is widely used by Russian and Eastern European actors. However, as these forums are internationally accessible, it is not definitive proof of the actor's origin or nationality.
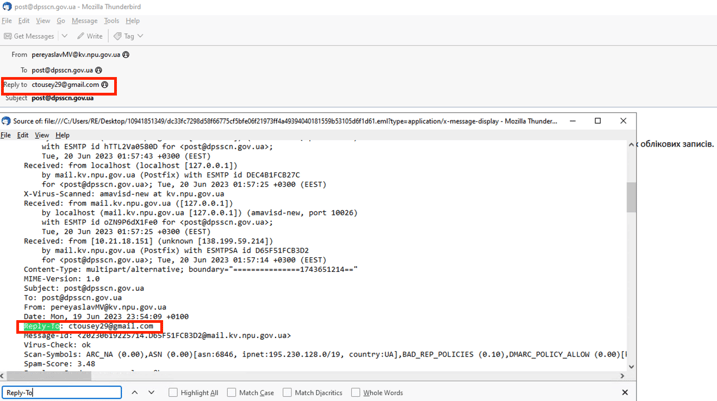
Figure 7 – Spearphishing email from Kyiv police to the
Production and Consumer Service in Chernihiv region.
Threat Actor Probably Exploited Vulnerable Zimbra and Roundcube Servers to Send Spearphishing Emails
EclecticIQ researchers assess with moderate confidence that a threat actor probably compromised Roundcube and Zimbra email servers of government organizations and leveraged access to send spearphishing emails to other victims. EclecticIQ analysts observed that all sender organizations are using either Zimbra or Roundcube email servers.
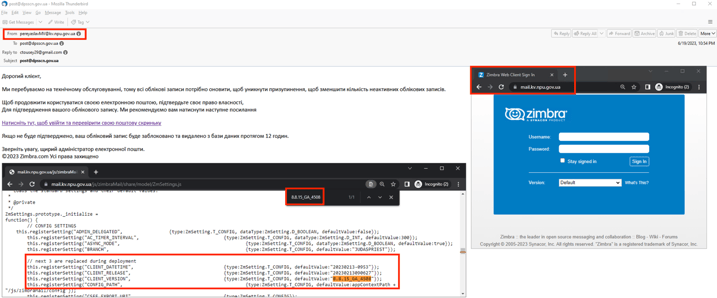
Figure 8 shows the Roundcube email server of the State Audit Service of Ukraine and its version 1.4.1 (mail.dasu.gov.ua). Figure 2 shows an email sent from the State University of Intellectual Technologies and Communication to an unknown recipient. Metadata from email headers and the Roundcube portal show that both are using outdated versions (1.4.10 and 1.4.1). The oldest Long Term Support (LTS) version is 1.4.13. [1]
It is probable that the threat-actor exploited known or unknown vulnerabilities in the Roundcube versions 1.4.10 and 1.4.1, such as CVE-2020-35730 [2], or CVE-2020-12641 [3].
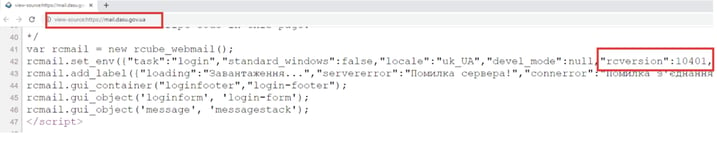
Figure 8 – Version of Roundcube email server.
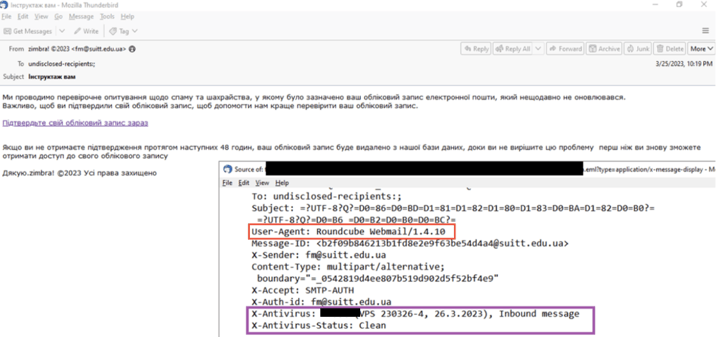
Figure 9 – Email header showing version of Roundcube email server.
Figure 10 shows the Zimbra email server of the “National Police in the Kyiv region” (kv.npu.gov.ua) and an email from the police to the Department of the State Production and Consumer Service in Chernihiv region (dpsscn.gov.ua).
Figure 10 – Sender government organization is a Zimbra webmail portal user.
EclecticIQ analysts observed supported and unsupported versions of Zimbra. It is probable that the actor exploited known or unknown vulnerabilities in Zimbra systems to gain access.
On 13 July 2023, Zimbra urged administrators to implement a workaround for a zero-day vulnerability, that is actively exploited targeting Zimbra Collaboration Suite (ZCS) email servers. The security flaw is a reflected Cross-Site Scripting (XSS) attack. [4]
As part of XSS attacks, threat actors could steal sensitive user information or execute malicious code on vulnerable systems that effects Zimbra Collaboration Suite Version 8.8.15. EclecticIQ analysts observed version 8.8.15 at sender organizations and assess with low confidence that the actor possibly exploited the reported zero-day vulnerability. [5]
| Webmail App |
Version |
Supported |
| Zimbra |
8.8.5_GA_1894 |
No |
| Zimbra |
8.8.15_GA_4484 |
Yes |
| Zimbra |
8.8.15_GA_4508 |
Yes |
| Zimbra |
8.8.15_GA_4468 |
Yes |
Threat Actor Using CyberGhost VPN for Anonymity
EclecticIQ analysts assess with high confidence that the threat actor used VPN service CyberGhost for anonymity. Extracted IP addresses (188[.]241[.]177[.]108 and 154[.]16[.]192[.]141) from the “X-Originating-IP" email header are linked to CyberGhost VPN service.
“The X-Originating-IP" email header field is a standard for identifying the originating IP address of a client connecting to a mail service's HTTP frontend. When clients (threat actor) connect directly to a mail server, its address is already known to the server, but web frontends act as a proxy which internally connects to the mail server. This header can therefore serve to identify the original sender address despite the frontend.
Figure 11 showing two examples of email headers observed in this campaign contains “X-Originating-IP":
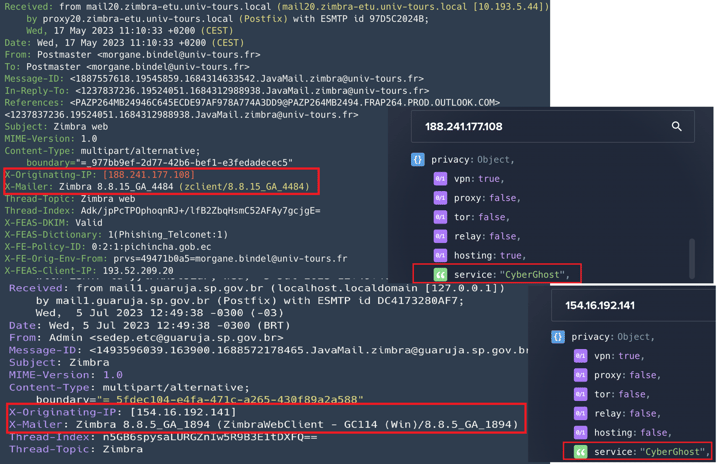
Figure 11 – Email Headers showing victim Zimbra
version and IP address of threat actor.
Mitigation and Prevention
According to Zimbra, mitigating the vulnerability against in the wild exploitation of Zimbra webmail version 8.8.15 requires admins to go through the following steps:
1. Take a backup of the file /opt/zimbra/jetty/webapps/zimbra/m/momoveto
2. Edit this file and go to line number 40
3. Update the parameter value to <input name="st" type="hidden" value="${fn:escapeXml(param.st)}"/>
4. Before the update, the line appeared as <input name="st" type="hidden" value="${param.st}"/>
The inclusion of the escapeXml() function will sanitize the user-input data by escaping special characters used in XML markup to prevent XSS flaws.
- Patch Management: Ensure all software and systems, including Zimbra and Roundcube, are patched and updated to the latest versions. This is critical to close off known vulnerabilities.
- Two-Factor Authentication (2FA): Implementing 2FA on all email and web services can greatly reduce the risk of credential theft. Even if an attacker is able to obtain a user's password, they will also need to bypass this additional layer of security.
About EclecticIQ Intelligence & Research Team
EclecticIQ is a global provider of threat intelligence, hunting, and response technology and services. Headquartered in Amsterdam, the EclecticIQ Intelligence & Research Team is made up of experts from Europe and the U.S. with decades of experience in cyber security and intelligence in industry and government.
We would love to hear from you. Please send us your feedback by emailing us at research@eclecticiq.com.
You might also be interested in:
8Base Ransomware Surge; SmugX Targeting European Governments; Russian-Linked DDoS Warning
Chinese Threat Actor Used Modified Cobalt Strike Variant to Attack Taiwanese Critical Infrastructure
Introducing EclecticIQ Intelligence Center 3.0
References
[1] “Roundcube Webmail Downloads.” https://roundcube.net/download/ (accessed Jul. 14, 2023).
[2] “NVD - CVE-2020-35730.” https://nvd.nist.gov/vuln/detail/CVE-2020-35730 (accessed Jul. 10, 2023).
[3] “NVD - CVE-2020-12641.” https://nvd.nist.gov/vuln/detail/CVE-2020-12641 (accessed Jul. 10, 2023).
[4] Maddie Stone [@maddiestone], .“@_clem1 discovered this being used in-the-wild in a targeted attack. Thank you to @Zimbra for publishing this advisory and mitigation advice! If you run Zimbra Collaboration Suite, please go manually apply the fix! #itw0days,” Twitter, Jul. 13, 2023. https://twitter.com/maddiestone/status/1679542322772721664 (accessed Jul. 14, 2023).
[5] K. Tan, “Security Update for Zimbra Collaboration Suite Version 8.8.15,” Zimbra : Blog, Jul. 13, 2023. https://blog.zimbra.com/2023/07/security-update-for-zimbra-collaboration-suite-version-8-8-15/ (accessed Jul. 14, 2023).