MSI Breach Leaks Intel BootGuard & OEM Image Signing Keys
In early April 2023, the Money Message ransomware gang attacked computer hardware producer company MSI, claiming to have stolen 1.5TB of data during the attack, including private keys used to sign firmware images and the keys for the Intel BootGuard firmware-verification technology on devices made by several different manufacturers and the attackers behind the intrusion began posting data stolen from MSI after the company decided not to pay the ransom demands.
Figure 1: Leaked MSI source code on Money Message data leak site.
BootGuard is an Intel technology that is responsible for protecting the firmware image and preventing any unauthorized modification of it. So, if an attacker is able to get low-level access to a target device and install a custom, malicious firmware image signed with a leaked key, the attacker could also bypass the BootGuard protection. The leaked keys affect MSI products with Intel’s Tiger Lake, Alder Lake, and Raptor Lake core processors. The BootGuard keys are generated by each individual manufacturer [1].
U.S. Says It Dismantled Russia’s “Most Sophisticated” Malware Network
The United States and its allies have dismantled a major cyberespionage system that it said Russia’s intelligence service had used for years to spy on computers around the world, the Justice Department announced on May 09, 2023 [2].
In a separate report [3], the Cybersecurity and Infrastructure Security Agency (CISA) portrayed the system, known as the “Snake” malware network, as “the most sophisticated cyberespionage tool” in the Federal Security Service’s (FSB) arsenal, which it has used to cyber espionage against sensitive targets, including government networks, research facilities and journalists.
The CISA report said Snake was designed in a way that allowed its operators to easily incorporate new or upgraded components, and worked on computers running the Windows, Macintosh and Linux operating systems.
One of the most significant features of Snake malware is highly evasive command and control mechanisms. According to CISA, Snake’s custom communications protocols (HTTP or TCP) employ encryption and fragmentation for confidentiality and are designed to hamper detection and collection efforts. Snake’s kernel module, along with a thoughtfully designed mechanism for distinguishing Snake traffic from legitimate client traffic, allows the implant to function as a server in the Snake P2P network without opening any new ports, greatly complicating detection efforts.
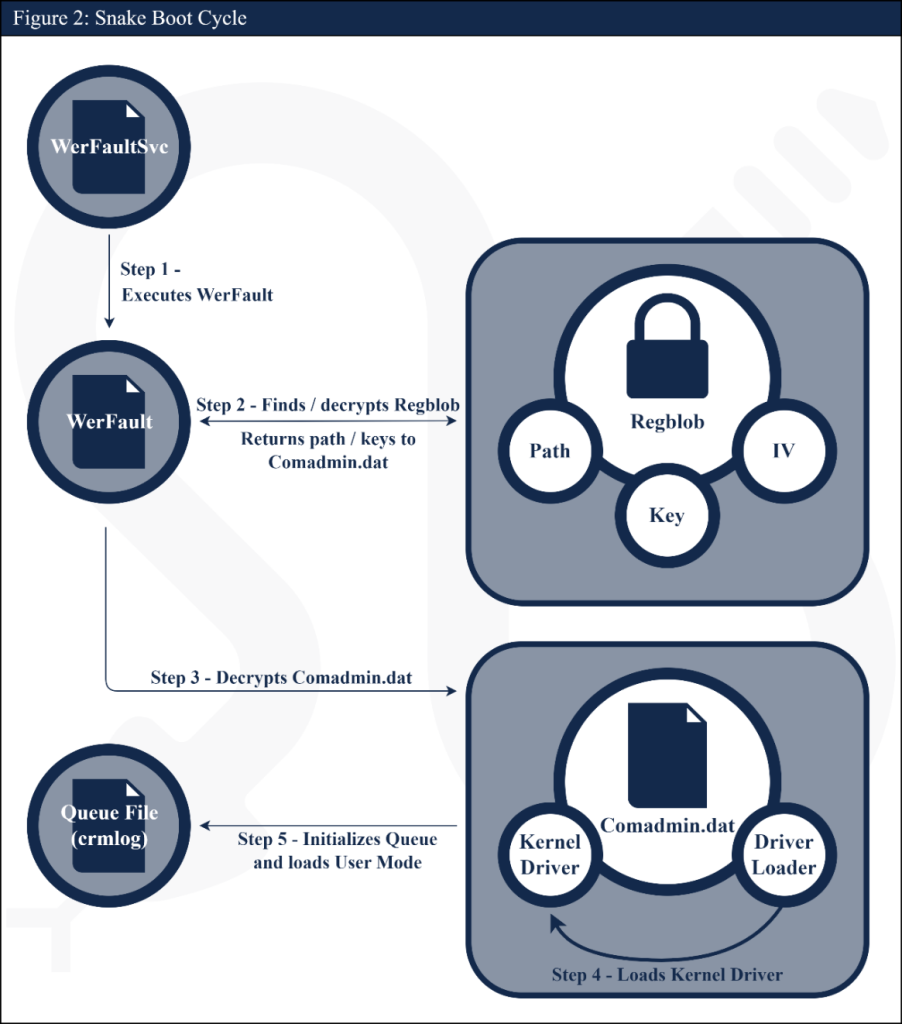
Figure 2: Persistence mechanism of Snake malware.
According to CISA, Snake registers itself as a service to maintain persistence on an infected system. Typically, this service is named “WerFaultSvc,” which was used to blend in with the legitimate Windows service WerSvc. On boot, this service will execute Snake’s WerFault.exe, which Snake developers chose to hide among the numerous valid Windows “WerFault.exe” files in the %windows%\WinSxS\ directory. Executing WerFault.exe will start the process of decrypting Snake’s components and loading them into memory.
Iranian state-backed Threat Actor Muddywater Exploiting (CVE-2023-27350) Vulnerable PaperCut Servers
According to Microsoft [4] , Iranian state-backed hackers have joined the ongoing cyber-attacks by targeting vulnerable PaperCut MF/NG print management servers. The PaperCut vulnerability exploited in these attacks and tracked as CVE-2023-27350 is a pre-authentication critical remote code execution bug in PaperCut MF or NG versions 8.0 or later.
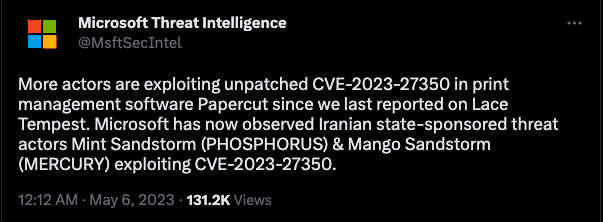
Figure 3 – Publication from Twitter account of Microsoft Threat Intelligence.
After the successful exploitation of CVE-2023-27350, Muddywater threat group also known as Mango Sandstorm by Microsoft and linked to Iran’s Ministry of Intelligence and Security (MOIS), started to execute malicious code inside the infected host to get C2 connection.
According to the vendor’s advisory [6], CVE-2023-27350 affects PaperCut MF or NG 8.0 and later across all platforms. This includes the following versions:
8.0.0 to 19.2.7 (inclusive)
20.0.0 to 20.1.6 (inclusive)
21.0.0 to 21.2.10 (inclusive)
22.0.0 to 22.0.8 (inclusive)
In the meantime, more threat actors begin to use this vulnerability in their attacks, EclecticIQ analysts suggest that organizations are strongly urged to prioritize applying the updates provided by PaperCut to reduce their attack surface.
Structured Data
Find the Analyst Prompt and earlier editions in our public TAXII collection for easy use in your security stack: TAXII v1 Discovery services.
Please refer to our support page for guidance on how to access the feeds.
About EclecticIQ Intelligence and Research
EclecticIQ is a global provider of threat intelligence, hunting and response technology and services. Headquartered in Amsterdam, the EclecticIQ Intelligence and Research team is made up of experts from Europe and the U.S. with decades of experience in cyber security and intelligence in industry and government.
We would love to hear from you. Please send us your feedback by emailing us at research@eclecticiq.com or fill in the EclecticIQ Audience Interest Survey to drive our research toward your priority area.
You might also be interested in:
Polish Healthcare Industry Targeted by Vidar Infostealer Likely Linked to Djvu Ransomware
3CX Incident Attributed to North Korea; New LockBit MacOS Sample
Exposed Web Panel Reveals Gamaredon Group's Automated Spear Phishing Campaigns
Appendix
[1] BINARLY🔬 [@binarly_io], “🔥The bxt_dbg_priv_key.pem, which is the Intel OEM Platform Key (Orange Unlock) obtained from an MSI leak, has been detected on devices from HP, Lenovo, AOPEN, CompuLab, and Star Labs. 🔬Stay tuned for more updates as the investigation continues. https://github.com/binarly-io/SupplyChainAttacks/blob/main/MSI/IntelOemKeyImpactedDevices.md https://t.co/YBXxr1V0zj,” Twitter, May 09, 2023. https://twitter.com/binarly_io/status/1655758951273885696 (accessed May 10, 2023).
[2] “Eastern District of New York | Justice Department Announces Court-Authorized Disruption of the Snake Malware Network Controlled by Russia’s Federal Security Service | United States Department of Justice,” May 09, 2023. https://www.justice.gov/usao-edny/pr/justice-department-announces-court-authorized-disruption-snake-malware-network (accessed May 10, 2023).
[3] “Hunting Russian Intelligence ‘Snake’ Malware | CISA,” May 09, 2023. https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-129a (accessed May 10, 2023).
[4] Microsoft Threat Intelligence [@MsftSecIntel], “More actors are exploiting unpatched CVE-2023-27350 in print management software Papercut since we last reported on Lace Tempest. Microsoft has now observed Iranian state-sponsored threat actors Mint Sandstorm (PHOSPHORUS) & Mango Sandstorm (MERCURY) exploiting CVE-2023-27350.,” Twitter, May 05, 2023. https://twitter.com/MsftSecIntel/status/1654610012457648129 (accessed May 10, 2023).

