A defense posture that focuses on Indicators of Compromise (IOCs) represents a reactionary approach to security. IOCs include past items or events, also known as artifacts. They fail to extend our defenses into the future (we discussed this already in the post Why IOCs are not enough). This approach shortens the amount of time to action consumable intelligence and allows attackers to retool and re-attack quickly in what is considered a ‘weaponization delta’. Shifting from IOCs to techniques, tactics, and procedures (TTPs) matures an organization’s defense posture by providing easily digestible context around specific details observed. TTPs illustrate the broader attack picture and how it connects to other stages of an attack or campaign. Organizations can break out of a purely reactive posture that is limited to single attack instances and single malware variants.
TTPs highlight relationships between multiple IOCs. TTPs provide more connections to other IOCs via the STIX data model. IOCs sit at the bottom of this stack and inherently lack the same connectivity. IOCs are still valuable, but focusing on TTPs allows for the association and grouping of multiple IOCs to gain further insight into attacks. Lastly, a focus on TTPs helps to funnel resources in more effective places (TTP chokepoints) that offer heavier impact in disrupting key infrastructure used by threat actors. This approach may hold a number of cascading effects.
TTP-based cyber threat intelligence (CTI) lengthens the weaponization delta (time between attacks). Maintaining comprehension and situational awareness of the TTPs in play versus IOCs enables organizations to effectively disrupt the attack infrastructure. TTPs can be modeled against the Cyber Kill Chain to gain deeper understanding of how an attack progresses. This level of defense forces threat actors to retool and recreate command and control (C2) infrastructure, expending additional time and resources.
The STIX Taxonomy
TTPs representing particular attack infrastructure are very likely being used by more than one threat actor for additional actions on objectives. Threat actors tend to execute in repetitive ways using approaches that are known to be successful. A TTP approach to structured intelligence assists in obstructing other attacks and malicious payloads relying on the same TTPs. Threat actors tend to take actions in repetitive ways creating distinct patterning of certain attacks. This in-turn creates a variety of chokepoints centered on TTPs; areas where resources can be effectively staged to stave off multiple threats simultaneously. This can impact and reduce future risk.
TTP-based CTI shifts more risk to the attacker. If the attacker must adopt new TTPs, a higher level of uncertainty is introduced. TTPs unfamiliar to the threat actor will likely not be as robust and may contain errors, since they are not well-tested. New infrastructure may contain holes that expose their activity and/or identity. The threat actors must adopt new approaches. New approaches carry more risk because there is more uncertainty in novel attack vectors.
A focus on TTPs allows for better threat monitoring. Security teams can focus on an entire family of payloads that may be delivered by a particular attack pattern (TTP). If organizations understand the infrastructure threat actors use to accomplish their actions on objectives or install malware, then dynamic defense mechanisms can be deployed to monitor these behaviors. TTPs present a wider, common intelligence picture and help organizations react at a strategic and operational level.
Several models and frameworks mentioned below may help organizations shift to TTP detection:
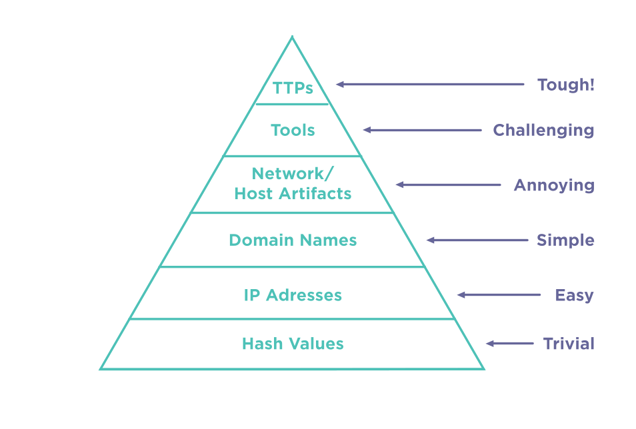
- The Pyramid of Pain is a useful to measure the maturity of an organization’s defense posture. The goal is to move up the pyramid so that, as an organization, you react to TTPs rather than other more traditional artifacts of an attack.
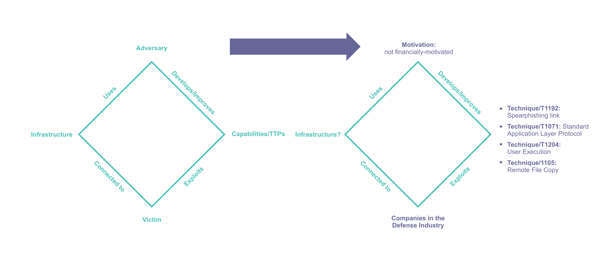
- The Diamond Model illustrates TTPs and allows for their comparison. This is applicable for understanding changes to attack patterns and differentiating between attack patterns used by various threat actors. Understanding these changes through diamond modeling provides a more effective, tailored response.
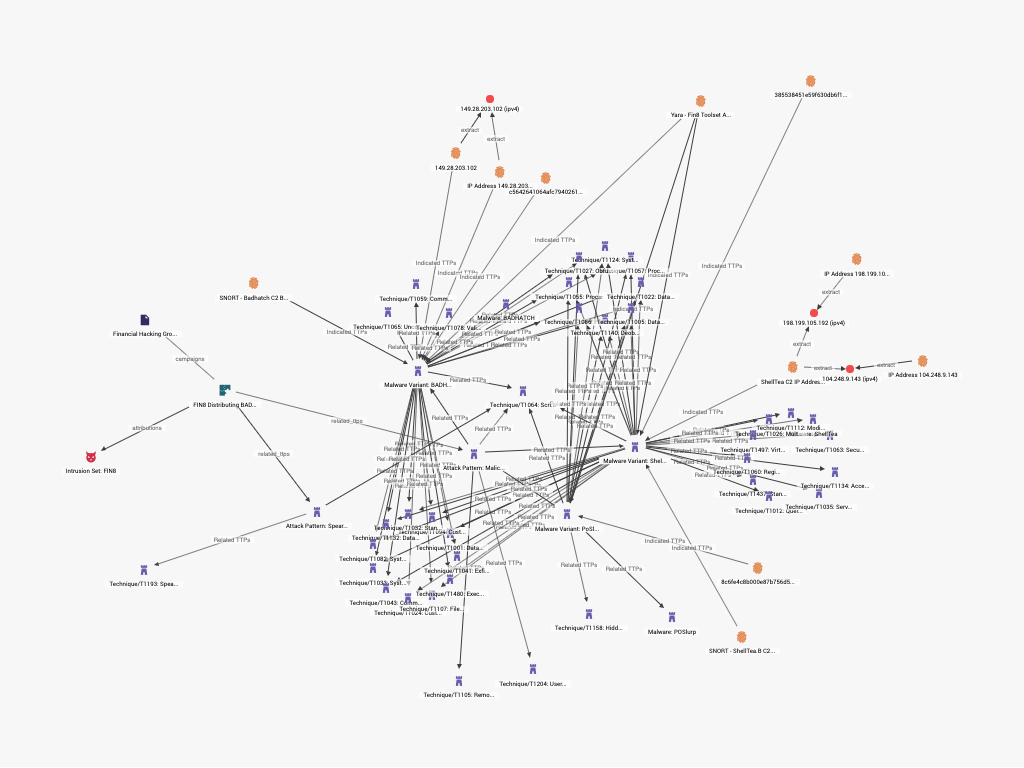
- Structured Threat Intelligence provides powerful analysis and visualization of TTPs. Curated Structured Intelligence allows an organization to access troves of data collected through various threat intelligence agencies. Structured Intelligence provides context to TTPs by linking them to their other aspects of an attack encompassing IOCs, but also extends relationships to related attack patterns and threat actors behind the attacks.
- Threat hunting can benefit significantly from TTP analysis, as it provides focused direction. For organizations lacking a fully mature hunting practice, TTP targets for hunting activity helps to focus hunting resources. TTPs sit near the middle of the STIX hierarchy, providing links to entities above (campaigns, reports, and threat actors) and below (IOCs, observables), so they provide solid points from which to pivot during hunting exercises. Combining a hunting practice with Structured Intelligence enables companies to discover the TTPs and Attack Patterns that most impact them, adapt more quickly to changing TTPs, and to discover new threats based on other TTPs.
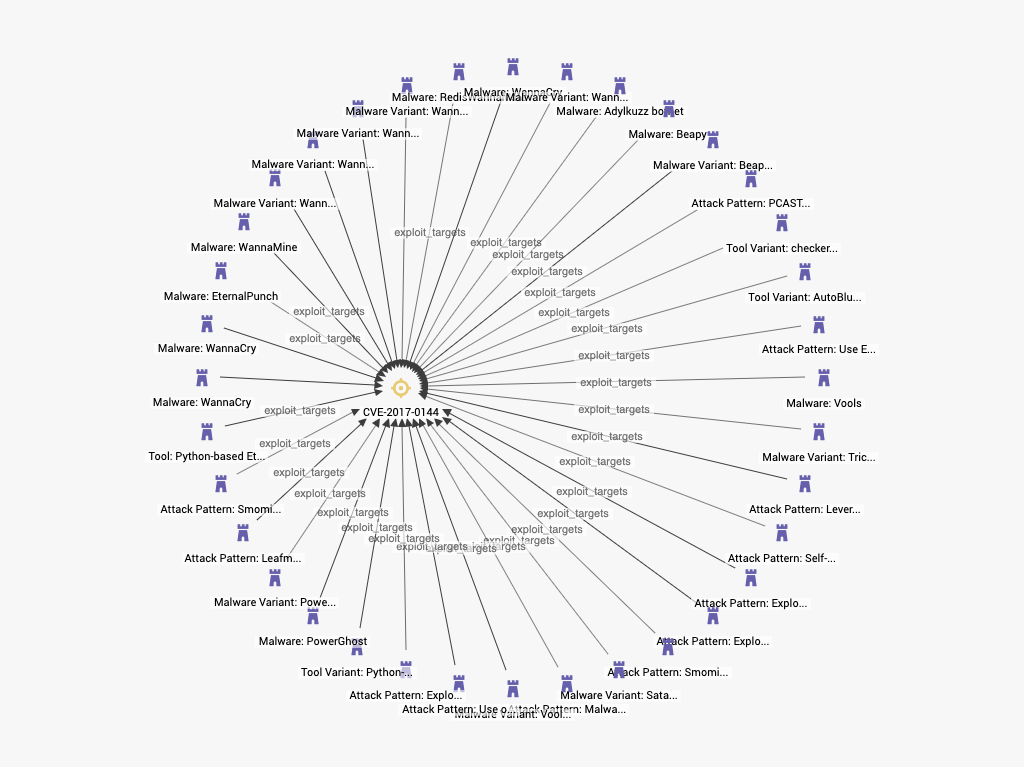
Malware that has all relied on the Eternal Blue vulnerability (CVE-2017-0144) to install
A reactionary posture based largely on IOCs is insufficient to manage risks associated with current cyber-attacks. Structured threat intelligence can offer improvements to the security posture of an organization by employing a defense based around TTPs (Techniques, Tactics, and Procedures) that represent Attack Patterns. Structured Intelligence combined with a Threat Hunting practice can further demonstrate the more important and relevant TTPs on which to focus. TTPs provide better actionable intelligence that include more context around individual and groups of IOCs and give organizations better understanding of threat actor actions against their network. This approach can help companies mature a more effective defense.
