.png?width=859&name=image%20(15).png)
This isn't another Indicators of Compromise (IOC) vs Techniques Tactics Procedures (TTP) argument. We recognize the value of IOCs in detecting and neutralizing threats. But used in isolation they are not capable of detecting all threats.IOCs are an expected product within Cyber Threat Intelligence (CTI). CTI reports that feature a new campaign, malware analysis or an actor assessment will probably include IOCs compiled after the initial analysis. IOCs provide knowledge about known threats and in some cases are the only data points that analysts have at their disposal to help identify a partial narrative. They can indicate where (IPs), how (domains/hosts) and what (hashes) has happened.
But in some cases, the wider narrative can get lost, especially when IOCs are treated as the basis for certain intelligence feeds. IOCs packaged in the form of blacklists are common outputs from intelligence vendors to help organizations detect and mitigate against known threats. However, knowing when something is considered malicious or compromised is not enough. Adversaries cycle through infrastructure quickly and continue to update their operations. This means that using IOCs for detection and prevention is becoming less valuable and, in some cases, not useful at all.
So how do we evolve our detection strategies?
The emphasis on detection rules like YARA is here to stay because rules based on combinations of unique strings, timestamps and even file sizes can be greatly beneficial. But there are some YARA rules that are not beneficial. For example, rules that match only on a specific sample are not much of an improvement over a hash value [1].
Analysts often find themselves using rules to identify a piece of malware, while also trying to identify the entire kill chain and perform a hunt using the diamond model. There needs to be more robust ways to track and identify activity in the future that don't rely solely upon the actor using unchanging malware and infrastructure.
So, IOCs are definitely essential to threat detection and response. But to be most effective they need to be used in an ecosystem of frameworks that enhance what analysts know about certain threats.
These frameworks, standards and libraries already exist – STIX, MITRE ATT&CK, the kill chain, the diamond model. Analysts are already using them and other tools to adopt a more patterned approach to getting context on an adversary and their TTPs.
Consider the images below. They show three unrelated campaigns that occurred in a three-month window targeting companies within the defense industry. Analysts studied the attacks and tried to identify any similarities between the three campaigns.
Analysts did identify four TTPs shared across all three campaigns. In other words: in a three-month time period, analysts were able to identify a small pattern of adversarial behavior targeting a certain sector.
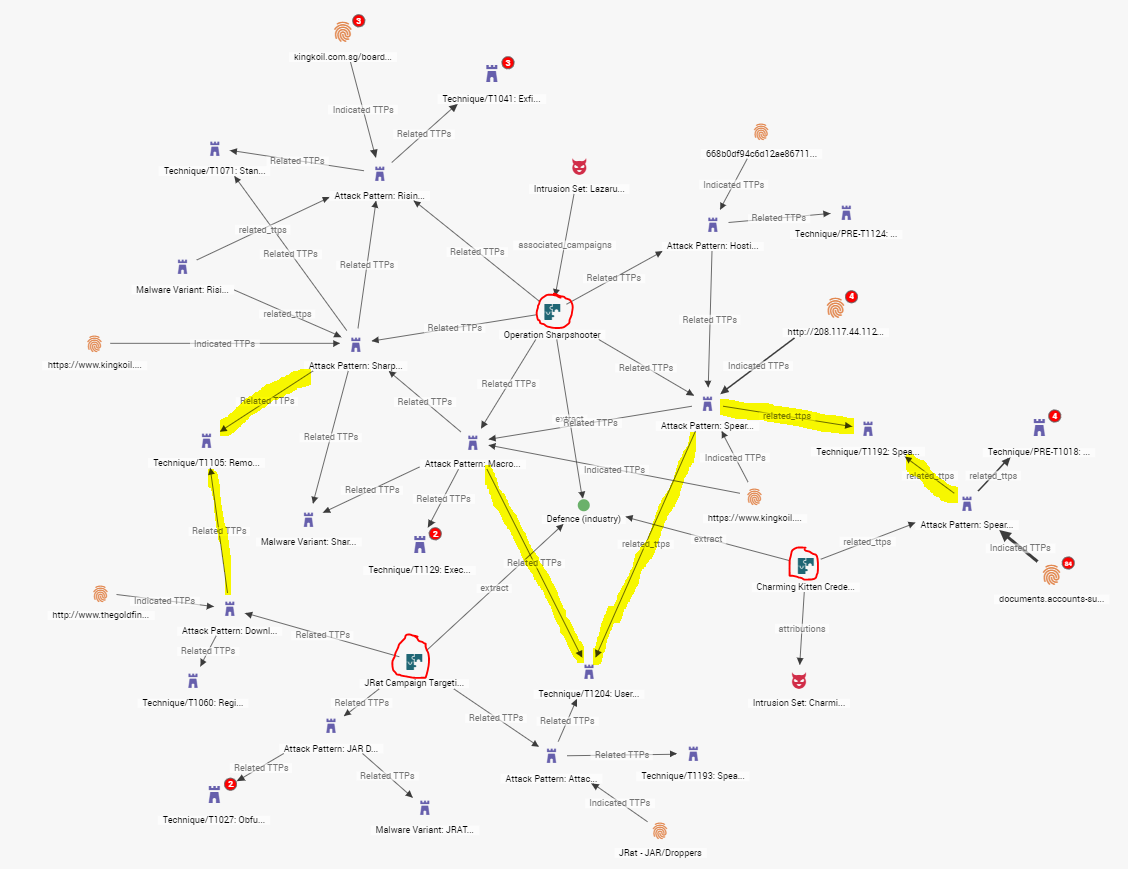
Figure 1: Three unrelated campaigns targeting the defense industry.
In this case the campaigns were all conducted by disparate threat actors, differing in motivation and location. Imagine if an analyst could determine that all three campaigns were conducted by actors operating in the same region. That could be the basis of an interesting report that would aid hunt and incident response (IR) teams.
The TTPs that were shared across all campaigns are MITRE ATT&CK TTPs that analysts use to define what occurs in a given attack pattern. In STIX 2.0, an attack pattern [2] is a type of TTP that describes ways and behaviors in which adversaries attempt to compromise a target. Being able to attach MITRE TTP objects to attack patterns gives analysts additional granularity to better understand how something is being done (i.e. compromise third-party or closed-source vulnerability, obtain/re-use payloads, remote file copy). As shown above, it also lets analysts discover possible overlaps and trends over the lifecycle of a campaign.
An analyst can use this TTP coverage in a number of ways. If the above graph represented Chinese threat-actor activity, analysts could track how particular regional adversaries are evolving over time. We could identify how TTPs are changing within the delivery phases of an operation or how an actor is changing lateral-movement skills across several campaigns. Using the diamond model approach, analyst teams could use the knowledge gained from the above example about regional adversaries and their overlapping TTPs as a starting point for additional investigations.
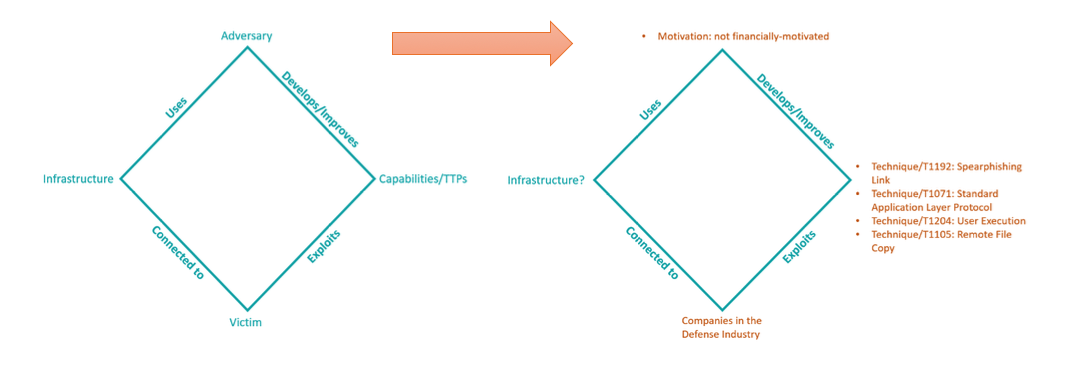 Figure 2: Diamond Model approach
Figure 2: Diamond Model approach
In the below image, if we were to remove the ‘sea of purple’ TTPs and expand the IOCs seen in the three campaigns, we get something that resembles a constellation: groupings of IOCs clustered around the activity they were seen in. The graph is fairly unremarkable as is and would require a lot of enrichment and analyst tooling to create more context.
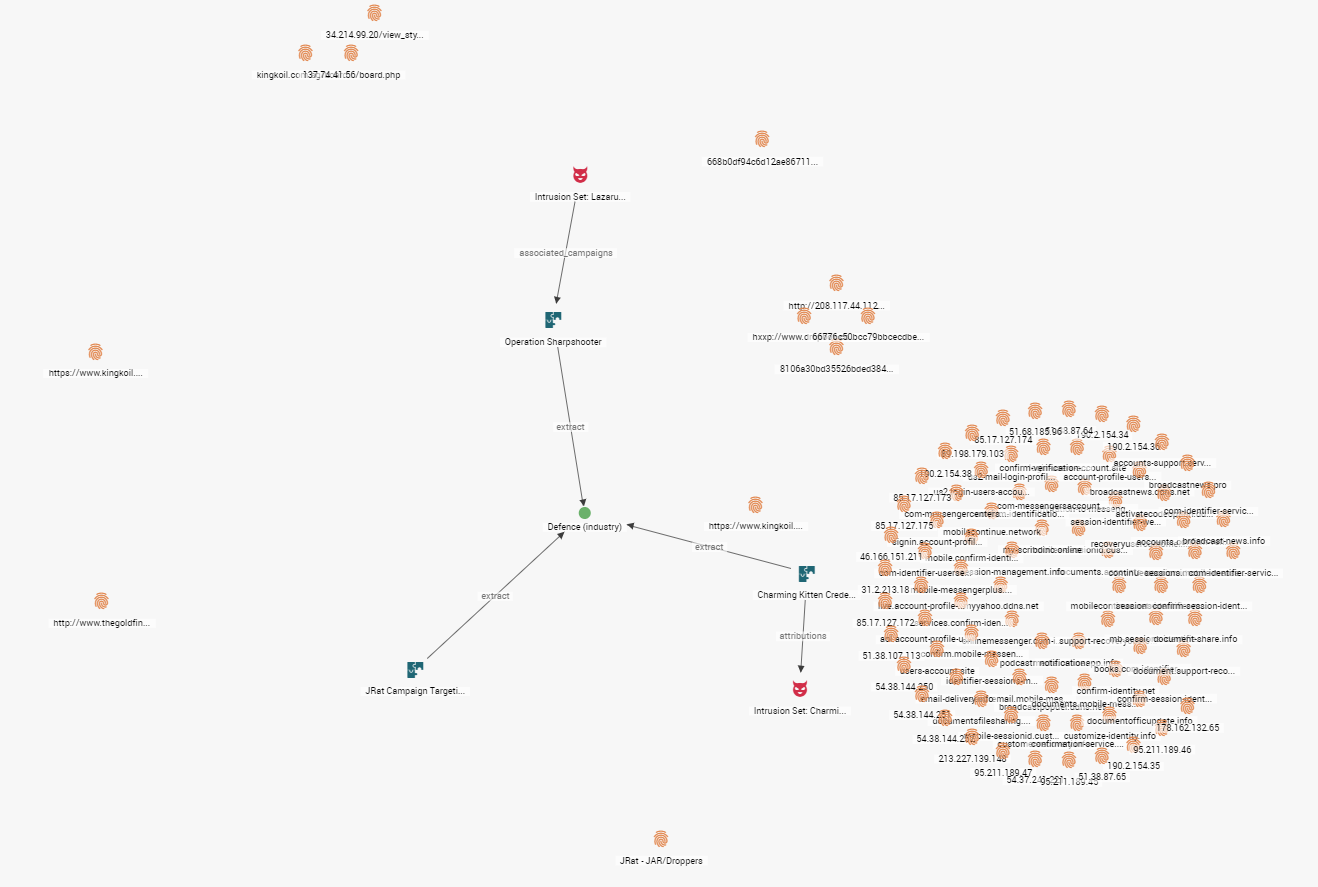
Figure 3: Removing the "sea of purple" TTPs
Another pain point for teams that focus on IOCs for investigative workflows is that threat intelligence can start to look like a big data problem. We discussed blacklists earlier in this post as a common output for intelligence producers. But an emphasis on having atomic indicators, which point to adversary activity, would create for more effective feeds for analysts.
By using TTP structures like the one above, analysts can help qualify those atomic indicators easily for a more refined high-confidence blacklist.
Open standards like MITRE ATT&CK are being integrated more by the intelligence community to make it easier for CTI analysts and producers of intelligence to identify techniques and stages in an adversary’s campaign.
Hybrid Analysis is just one of the many platforms that is incorporating MITRE ATT&CK. Pairing a malware sample with MITRE TTPs allows an analyst to do the following:
- Identify in more granular ways how an indicator may be linking a set of TTPs
- See how tactics progress along the kill chain
- See how a certain adversary’s tactics evolve across malware campaigns
- Identify when adversary TTPs change to aid in confidence rating when performing attribution
The following is an example of a sample in Hybrid Analysis that maps to MITRE ATT&CK[3]:
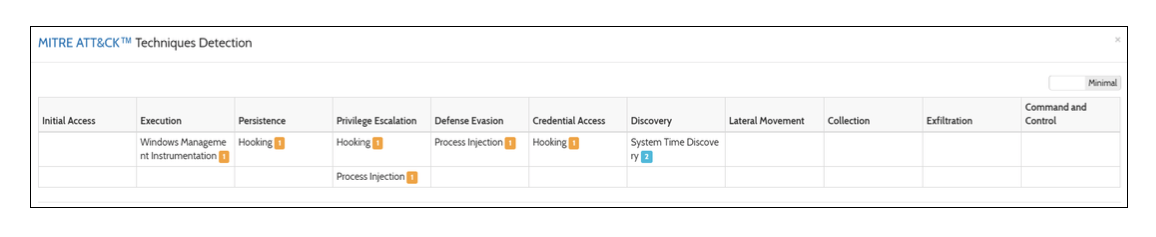
Figure 4: Hybrid Analysis using MITRE ATT&CK
The examples above are meant to show the benefits of relying on TTPs to identify new trends, activities and patterns.
There is no doubt that IOCs have their place in cybersecurity. But they are usually relevant only for short periods of time and limited to detecting existing threats. To fully comprehend the threat landscape, we have to go beyond the IOC with the help of TTPs to understand how an adversary behaves and operates.
If you are interested in more examples or applications, please reach out to us at EclecticIQ and start a conversation.
[1] How to Write Simple but Sound Yara Rules
[2] STIX Version 2.0 - Part 2: STIX objects
[3] Hybrid Analysis - Free Automated Malware Analysis Service
