 As Europe’s leading cyber threat intelligence company, we at EclecticIQ have decided to make use of our resources and provide the community with custom reports on threats connected to the COVID-19 pandemic throughout the duration of the crisis.
As Europe’s leading cyber threat intelligence company, we at EclecticIQ have decided to make use of our resources and provide the community with custom reports on threats connected to the COVID-19 pandemic throughout the duration of the crisis.
This is the eleventh report in a weekly series of updates to inform of important developments to COVID-19-themed attacks.
Key Findings
- Remote access is trending to become the greatest risk to healthcare.
- Healthcare misinformation is widely established online, taking many forms.
- New attack patterns and design failures drive privacy risk from ‘contact-tracing’ app exploitation.
Analysis
Risk to Healthcare Shifts Focuses on Cyberattacks That Establish General Remote Access.
A spike in healthcare information leaks could possibly combine with an increasing trend in malware tailored for remote access, to further amplify risk to the healthcare industry. It is possible that ransomware risk will decrease following further announcement in support for the healthcare industry. The joint action, signed by many States, serves to signal further deterrence against cyber-attacks that impact hospital system operations. The most recent notice comes on the heels of law enforcement actions against a healthcare attack in Romania provided in the update from last week.
Recorded Future has analysed data related to healthcare information leaks and noted a statistically significant increase in leak activity since the start of 2020, compared to averages across similar timelines
More people are visiting hospitals. More patients generate more data at risk in attacks that leak healthcare data. APT (advanced persistent threats) activity aimed at treatment technologies could possibly be aided by data in the leaks. It is probable that sensitive information in the leaked data will be used and weaponised for further attacks on healthcare companies, such as to support more advanced malware.
EclecticIQ analysts first reported increasing risks from remote access attacks developing against the healthcare industry in our May 5th update . Patterns of TTPs (Tactics, Techniques, and Procedures) in the weeks since provide consolidating evidence that successful attacks on healthcare have been utilizing RAT (Remote Access Trojan/Tools) TTPs to open networks to further attacks. Some of these attacks result in ransomware, however RDP and other remote access could still open healthcare organizations to a range of other attacks. EclecticIQ analysts typically see further attacks use malware that can directly monetize the remote access advantage in the form of bots or trojans that comprise either, A) Info-stealers that harvest account or personal information that can be sold on the Darkweb, or B) banking trojans and cryptojacking bots that immediately generate income and are mostly automated.
Concurrently and in addition to increased leaked healthcare data, threat actors are tracking and selling higher volumes of RDP access from previously compromised organizations. One prominent family includes Sarwent malware. The malware is tailored to provide remote access command line interface on the internal network and can create new user accounts. Sentinal One offers a recent deep dive into this malware. RDP connections offer access to internal networks with high privileges.
There has not been widespread reporting of RDP attacks on healthcare companies, but according to this year’s RSA conference, “The healthcare industry has significantly more exposed attack surfaces than any other industry surveyed, according to Censys’s research findings of cloud risks and cloud maturity by industry”. Healthcare should remain on high alert and IT should perform a full DFIR (digital forensics and incident response) on any system that is found to be compromised to be sure any remote access holes are closed.
Healthcare misinformation online enables more COVID-19 themed TTPs.
Widespread healthcare misinformation is in robust circulation online. The misleading information covers many facets of the pandemic, relating to treatments, consumer goods, and disease data, among other things. It is unclear what may be motivating much of the activity. A primary consequence of increased inaccurate information circulation is that it creates an environment of confusion, which enables threat actors to use TTPs that exploit confusion, in a fog-of-war effect, to take advantage of victims and official resources and references. It is almost certain that inaccurate information online is boosting the effectiveness of recycled TTPs by exploiting increased confusion over information and resources that relate to the pandemic.
New Tactics, Techniques and Procedures (TTPs)
A new GuLoader infection campaign began to rise in March 2020 and continues strong into May 2020. The initial campaign leveraged a graphically-detailed email with very vague titles and wording like “My Health.exe”, spoofing the World Health Organization and COVID-19 health updates in an attempt to garner more victims. GuLoader is a type of trojan-downloader, that enables access via C2 (command and control infrastructure) to deploy further malware. This is a prime example of threat actors continuing to recycle TTPs with minor iterations to the overall Attack Pattern. It is also another good example of the types of malware, like Sarwent, threat actors are using to establish further penetration into a victimized network.
MalwareBytes has detailed a new version of the Zeus Bot that is making new rounds featuring COVID-19 themed spam. The original Zeus family was well designed and this malware variant is as well. It includes multiple points of obfuscation throughout its kill-chain to remain hidden from defenses. Most prominently, it features encrypted C2 communications and it steals financial data and account information from browsers and encrypts the data within the system, while at rest. The delivery vector, spam, does not employ any particular notable TTPs. The malware works against all operating systems.
COVID-19 Tracing Apps: Scams and Failures
Most of the apps discussed, including the large effort by Google and Apple rely on Bluetooth for data generation. A recent analysis of specific Bluetooth implementation for tracing apps has highlighted some important holes that allow threat actors to perform so called “Bluetooth Impersonation AttackS” (BIAS) that result in complete ID spoofing and thus data contamination.
Threat intelligence is especially useful in this case where there are many technologies and different risk. BIAS attacks involve a collection of exploits that can be carried out in different ways to the same affect, in all mobile platforms. Organizations can use threat intelligence as outlined in the graphical model below to establish initial attack models and track threats against different infrastructure.
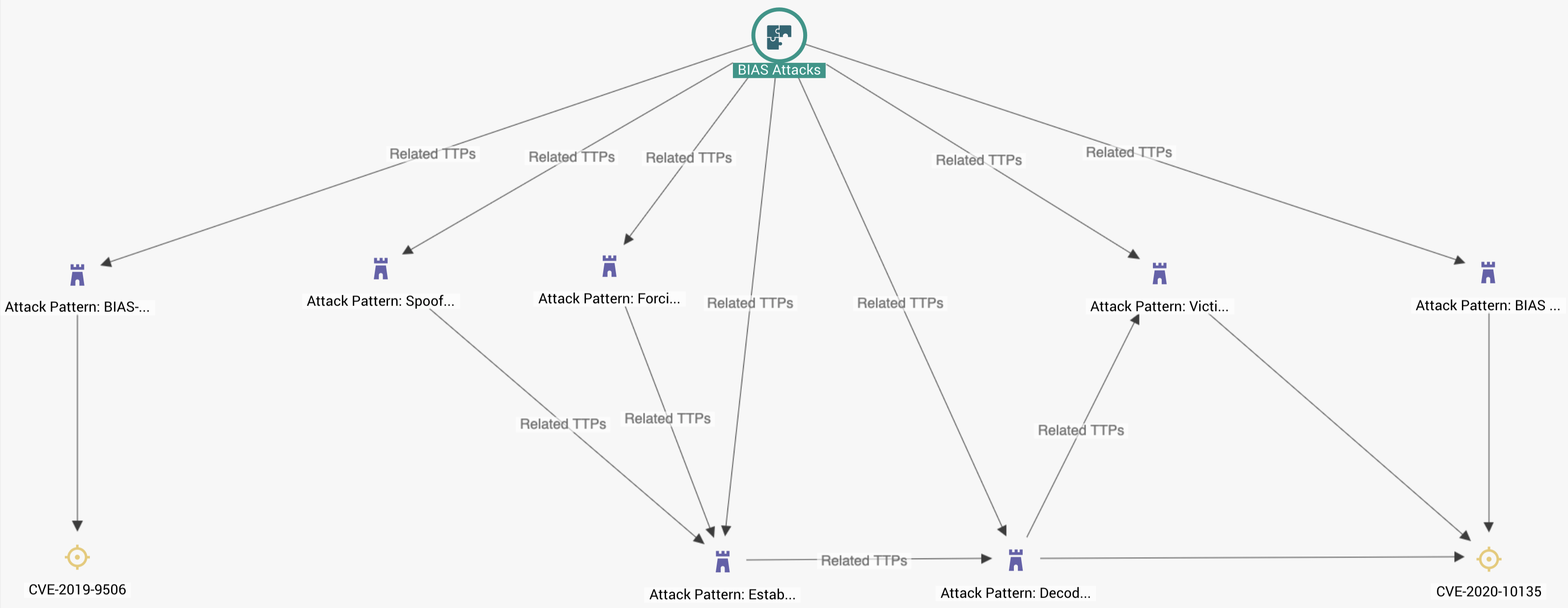
BIAS attacks against bluetooth technology used for tracing apps
Model can be combined with further intelligence representing specific weaknesses or risks to gain more context into active attacks, tracking how they evolve, and manage remediation efforts in the form of released patches or developing proprietary security defenses. Currently there is no official patch for BIAS attacks.
Near the end of April 2020, many States began to announce tracking technology efforts to help contain the pandemic. At this time we alerted to increased exploitation of the apps and data from threat actors and poor security. EclecticIQ analysts continue to observe many reported issues over different developing technologies. Two of the biggest delivery vectors for these types of attacks continue to include social engineering for redirection to external infrastructure for the purpose of credential compromise and sideloading of malicious apps. As more countries offer competing technologies, they expand the attack surface for threat actors. EclecticIQ analysts expect attack patterns against mobile COVID-19 tracking apps to continue and expand.
In our update last week, EclecticIQ Analysts highlighted risk from BEC groups taking advantage of infrastructure providing work benefits. Analysts are now observing this activity moving into the hands of more disparate, individual threat actors. Krebs has reported a large increase of different TTPs being used to exploit unemployment benefits in the US. This is a good example of how threat actors flock to new opportunities. New benefit systems provide new opportunities for fraudulent financial gain by phishing individuals with fewer security controls as comparted to BEC TTPs, which attack more robust enterprise-type networks. The newer attacks are objectively easier to carry out.
Italy has developed a tracking app named “Immuni” and it was recently being spoofed by a malicious app spreading a new family of ransomware dubbed “F-Unicorn”. The operators still use phishing for delivery and redirecting victims to the malicious app.
Analysis shows the threat actors send the password for encryption over clear-text and its possible to intercept the password with network traffic logs and restore the file system. This is one example of how threat actors can attack and spoof official apps.
App failures also carry a similar level of risk as attacks because bad configurations can expose the same data. A recent analysis of the “COVIDSafe” App touted by Australia has demonstrated multiple important privacy issues. The report highlights re-identification false-positives, increased location tracking compromise exposure, and general lack of transparency into who has access to the data. The report recommends adopting the Apple/Google API noting that there is no plan for any remediation of Australia’s proprietary technology.
Further COVID-19 themed activity trends were detailed in a report by Secure List. The report provides cumulative data showing that brute-force attacks against database servers is up significantly since March 2020 and continues to trend upward compared to similar timelines. The report also highlights attack patterns against ‘remote entertainment’ involving redirection to malicious websites claiming to be involved in the same. Threat actors will often seek out environments that attract more victims than normal. Remote entertainment during the pandemic provides fertile ground, but these attacks typically limit threat actors to individuals. Companies will usually have a combination of technology policies and security controls that prevent these same attacks from being effective because they block the web-based attacks in most cases.


