
As Europe’s leading cyber threat intelligence company, we at EclecticIQ have decided to make use of our resources and provide the community with custom reports on threats connected to the COVID-19 pandemic throughout the duration of the crisis.
This is the seventh report in a weekly series of updates to inform of important developments to COVID-19-themed attacks.
Key Findings
- APTs present a growing threat to strategic information related to COVID-19 treatments and vaccines.
- COVID-19-themed spam attacks are using more realistic lures with limited novelty.
- Past attacks on Healthcare successful in sustaining remote access present continued risk to the same organizations.
- Brute-force attacks and stolen credentials provide growing attack surface and risk to the remote workforce.
- Pandemic propaganda from China targets the European region.
Analysis
APTs Will Target Strategic Healthcare Information Related to the Pandemic.
Reports from the United States signal increasing geopolitical tensions regarding attacks on strategic healthcare information. The report highlights China as a primary culprit although attacks span globally. Treatment and disease-related data will become more valuable to APT groups. Extended lockdowns significantly impact national economies and governments will look for many ways to mitigate impact. Obtaining beneficial data from a foreign government on COVID-19 will provide states with a direct advantage in containing their own crisis.
EclecticIQ analysts have been monitoring infrastructure that could be used in attacks against vaccine participants listed here.
Our analysts have discovered evidence of an attack against at least one major pharmaceutical company. Infrastructure showing recent timestamps is configured in a way that is highly conducive to Spearphishing TTPs. These TTPs are either under development or have already engaged the victim (unnamed for privacy reasons) beyond the Delivery Kill Chain Phase. Spearphishing is the most probable delivery vector for an attack and participating vaccine organizations should be on highest alert for APT activities.
Related attacks conducted thus far include COVID-19 detection and testing organizations. In a recent attack, threat actors breached a CT-scan technology firm in China that had software used to detect COVID-19 pneumonia symptoms. The threat actors offered the stolen files for sale publicly, rather than using the information in a further attack or keeping it to themselves. This strongly implicates an attacker not involved with an APT.
Prior to that report, a ransomware attack compromised Hammersmith Medicines Research and their data was also posted publicly. An APT also previously targeted the WHO, which notes a large general increase in attacks as well.
COVID-19 related phishing attacks develop better TTPs as threat actors spread out and create more novel attacks.
Mass-spam attacks continue to develop novel COVID-19 themes. Outside the new lure material, the attacks rely on the same TTPs as phishing attacks observed near the start of the pandemic (https://blog.eclecticiq.com/covid-19/investigating-phishing-attacks-exploiting-coronavirus-covid-19-themes) and many others.
A recent campaign featured COVID-19-themed attacks attacks spoofing popular shipping carriers including FedEx, UPS, and DHL. Attacks drop the Bsymem Trojan, which enables control of the device and data theft, according to Kaspersky. The attack is well configured with good spoofing TTPs. The grammar, language, and content are all highly accurate. The attack is likely to be more effective than initial attacks observed near the start of the pandemic. Analysts observed evidence of phishing attacks against commercial shipping organizations that used similar delivery and installation mechanisms as this newer campaign. The difference is the recent spoof goes to greater technically length to appear realistic, which indicates greater time and resource investment by the threat actors responsible.
Phishing attacks rapidly adapt to many situations in order to exploit victims and stay ahead of security controls and are very popular for the delivery phase of an attack. Threat intelligence analysis can provide great benefits to phishing mitigation by providing a birds-eye view of similar activity and showing how current activity may be linked. Threat Intelligence highlights changing attack patterns via TTPs (Techniques, Tactics, and Procedures). Comparing TTPs quickly demonstrates how threat actor attacks are changing or adapting to security defenses. Analysis at this level allows organizations to realize weaknesses and common attack vectors more quickly and better focus limited resources.
In below image EclecticIQ analysts have created a partial analysis of recent COVID-19-themed phishing attacks. Structured threat intelligence quickly highlights TTPs across different phases of the Kill Chain and shows where security efforts should be focused. 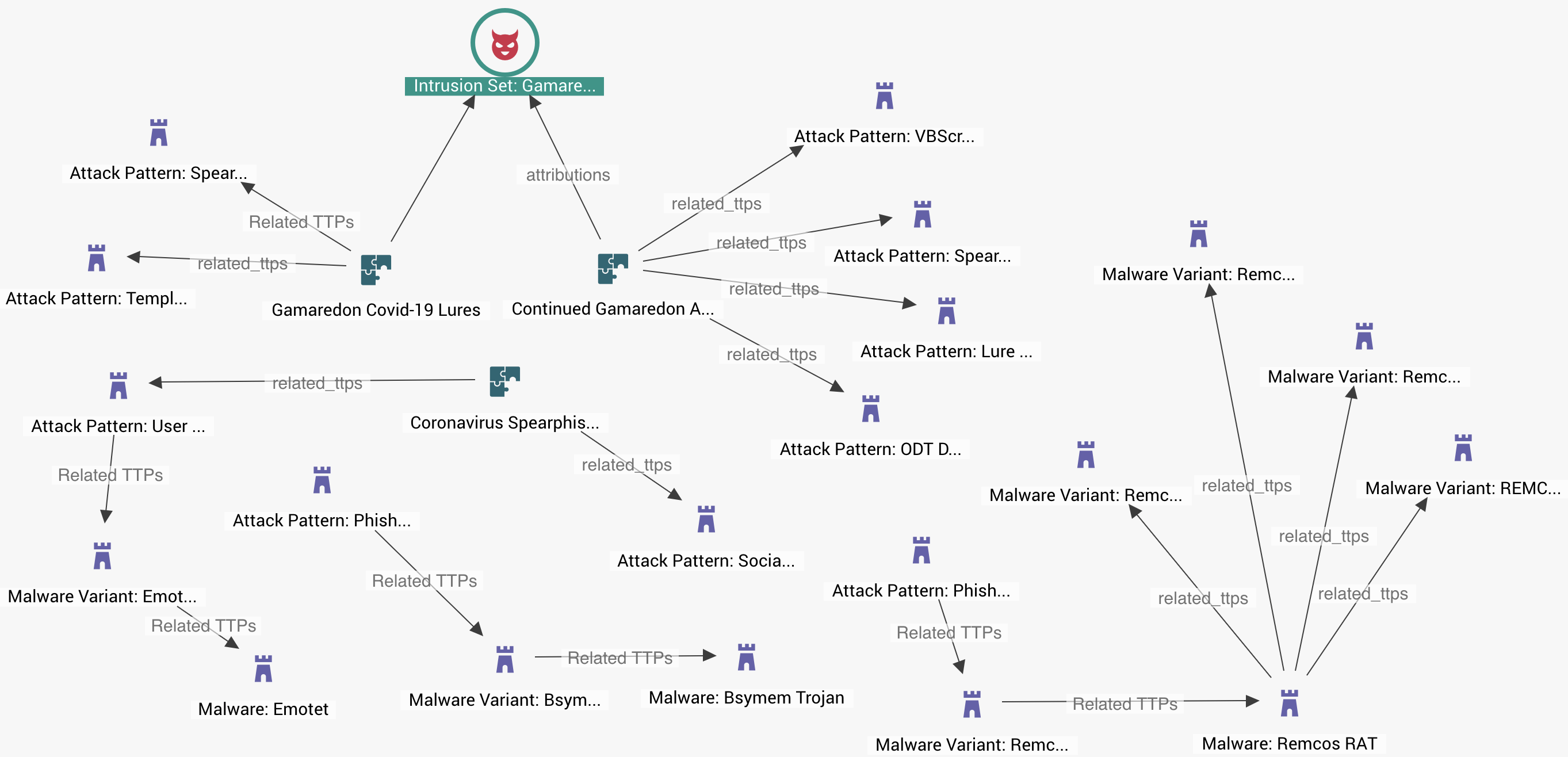
A report from TrendMicro states that Gamaredon, an APT group thought to have links to Russia, has participated in COVID-19 phishing, and EclecticIQ analysts expect that more attacks are likely. Intelligence on Gamaredon can help direct efforts to detect APT activity. Other attack patterns featured in the analysis deploy commodity Trojans that are available on the Dark Web. They all leverage spam and social engineering. This knowledge may assist security efforts at the perimeter to help mitigate risk from other attacks that exploit COVID-19 themes. Threat Intelligence greatly saves time and resources and provides a clear path to risk mitigation. Tracking TTPs allows intelligence analysts to identify how attack patterns are changing and who is participating. This approach is more useful and efficient than mitigation via blacklisting where increasing volume and diversification of phishing attacks can outpace an organization’s ability to collect and apply IOCs (Indicators of Compromise).
Past attacks sustain continued risk to the healthcare industry.
In our last weekly report, we highlighted further threats from Ransomware to healthcare as well as how remote access, established through previous attacks, is being used now in new attacks, many of which express COVID-19 themes. Microsoft recently featured a report that shows “Multiple ransomware groups that have been accumulating access and maintaining persistence on target networks for several months activated dozens of ransomware deployments”. This threat will continue to be significant as threat actors continue to evolve new phishing efforts that capitalize on COVID-19 panic and anxieties and as hospital resources are stressed by the pandemic.
Recommended mitigation stresses the importance of having frequent, air-gapped backup copies of critical information and practicing disaster recovery drills to maximize business continuity, which is crucial for hospitals at this time. A decent overview of disaster recovery planning for ransomware can be found here.
Threats escalate to the remote workforce.
Research from Zscaler shows an 85% increase in phishing attacks targeting remote enterprise. This indicates activity is shifting to new targets, rather than lulling. In a testament to evolving phishing TTPs during the pandemic that target remote workers, threat actors are initiating Zoom meetings as spoofed HR personas. The attack sends an invite via email to a Zoom meeting. The link to the meeting takes the victim to a well-spoofed Zoom page that asks for email credentials. The combination of incorporating another channel outside email for communication, along with the HR persona, marks this campaign as better developed and is likely to be more effective than earlier attacks. Trends from earlier examples show attacks are improving with volume to be much more convincing than inaugural attacks that used Zoom bombing, for example.
Stolen credentials combine with remote-work vulnerabilities to significantly increase risk of attacks to remote workers globally.
Brute force attacks against RDP (Microsoft Remote Desktop Protocol) are increasing markedly month-on-month now. Specific capabilities are being bolted-on to popular and successful commodity malware like Trickbot, which also participated in some of the highest volume attacks of the pandemic. RDP is essential for many remote work configurations. The current remote workforce is much larger than normal presenting threat actors with a larger attack surface to exploit. RDP exploitation is likely to be aided by poor network configurations of remote workers, who’s businesses were not well prepared for the influx of remote work and thus have weaker security controls.
Stolen Zoom credentials continue to rain down on forums where they are shared for further attacks. Recent research has shown even more Zoom accounts are being offered on illicit forums. The newer data comes after half a million accounts were previously compromised. These exposed accounts directly aid brute forcing attempts above. The more accounts, the more likely a threat actor will be able to brute force a set of credentials. Password length is the single most important factor to consider in brute-force mitigation. Longer passwords, even if they lack ‘complexity’, quickly become prohibitively time-expensive to crack.
Geopolitical Disinformation Targets Europe.
Previously, we alerted to reporting of possible opportunistic and strategic targeting of the European region by China for geopolitical gain leveraging the pandemic. The United States have confronted disinformation efforts by China. However, a report released by the Guardian reports that EU members may have caved to Chinese influence over false narratives surrounding their handling of pandemic response.
The Dutch government is leading a further investigation into the allegations which were initiated in this report. If found to be true, this development would signal China’s growing power to shape global discussions and disseminate propaganda.


