Cisco IOS XE Software Web UI Privilege Escalation Vulnerability Exploited in the Wild
On October 16, 2023, Cisco warned of a critical severity (base score 10) privilege escalation vulnerability tracked as CVE-2023-20198 in IOS XE software [1]. Successful exploitation allows an attacker to create an account on the affected device with privilege level 15 access, granting full control of the compromised device and allowing unauthorized activity.
Since there is no workaround or patch available at the time of reporting, threat actors will very likely increasingly use CVE-2023-20198 exploits to obtain initial access from victim networks.
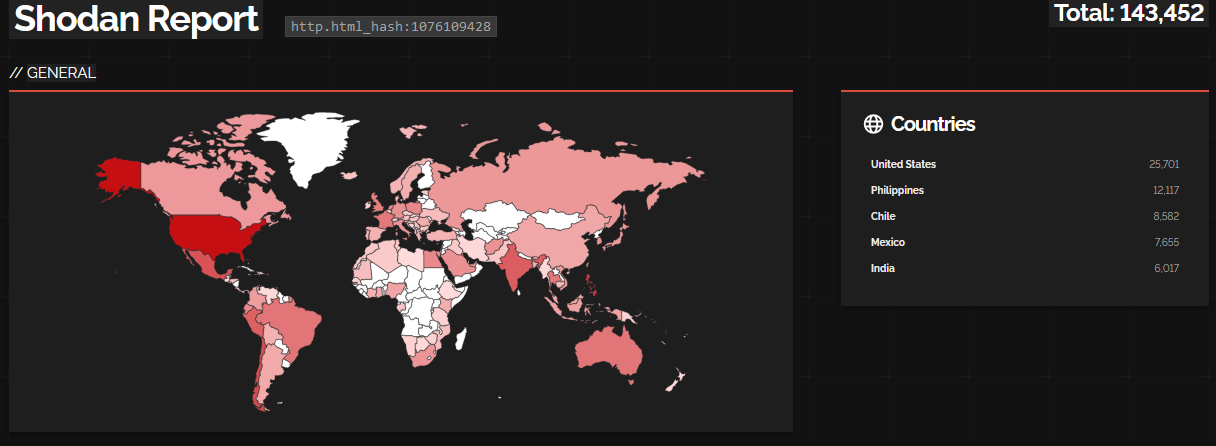
According to OSINT data source from Shodan, there are more than 143,000 publicly exposed Cisco IOS web servers possibly vulnerable to CVE-2023-20198. Sources from Shadowserver [2] suggest that over 32,000 Cisco IOS XE IPs are compromised with implants based on the check published by Cisco [3].
CERT Orange discovered 34.5 thousand Cisco IOS XE IPs devices with malicious implants [4], and released a Python script to check for existence of the malicious implant on a running Cisco IOS XE network device [5].
Figure 1 – OSINT data from Shodan showing publicly exposed
Cisco IOS XE (click on image to open in separate tab).
Sandworm Threat Actor Targeted Ukrainian Telecom Industry
Ukraine's Computer Emergency Response Team (CERT-UA) reported a Russian state APT group known as Sandworm (also referred to as BlackEnergy, UAC-0082, Iron Viking, Voodoo Bear, and TeleBots) has targeted eleven Ukrainian internet and telecom providers since May [6].
The Sandworm threat actors employed various malware, including Poemgate and Poseidon, to steal credentials and control infected devices. Threat actors also used Whitecat - a custom malware - to erase any forensic evidence. The CERT-UA report indicated that the threat actor infiltrated the victims' networks using compromised VPN accounts that lacked multi-factor authentication (MFA) to cause service interruptions.
This attack shows the importance of multi-factor authentication (MFA) for VPN account security. Compromised VPN accounts are used by wide spectrum of threat actors to get initial access from victim network.
Unpatched WS_FTP Servers Exploited for Ransomware Delivery
On September 27, Progress Software released security updates to address a critical WS_FTP Server vulnerability, urging admins to upgrade vulnerable instances [7]. The vulnerability tracked as CVE-2023-40044 is caused by a .NET deserialization vulnerability in the Ad Hoc Transfer Module, enabling unauthenticated attackers to execute commands via HTTP requests remotely [8]. Researchers from Assetnote security who first discovered the WS_FTP bug, released proof-of-concept (PoC) exploit code just days after it was patched, which makes it easier to perform mass exploitation WS_FTP Servers [9].
EclecticIQ analysts assess with moderate confidence that the existence of a proof-of-concept will enable threat actors to perform exploitation more easily. It is almost certain that threat actors will attempt to exploit the vulnerability to obtain a foothold into an organization's networks.
According to Sophos X-Ops incident responders, threat actors self-described as the Reichsadler Cybercrime Group performed mass exploitation of CVE-2023-40044 to deploy Lockbit 3.0 ransomware [10]. After the initial access, the threat actors attempted to escalate privileges using the open-source GodPotato tool, which allows privilege escalation to 'NT AUTHORITY\SYSTEM' across Windows client (Windows 8 to Windows 11) and server (Windows Server 2012 to Windows Server 2022) platforms [11].
Structured Data
Find the Analyst Prompt and earlier editions in our public TAXII collection for easy use in your security stack: https://cti.eclecticiq.com/taxii/discovery.
Please refer to our support page for guidance on how to access the feeds.
About EclecticIQ Intelligence and Research
EclecticIQ is a global provider of threat intelligence, hunting and response technology and services. Headquartered in Amsterdam, the EclecticIQ Intelligence and Research team is made up of experts from Europe and the U.S. with decades of experience in cyber security and intelligence in industry and government.
We would love to hear from you. Please send us your feedback by emailing us at research@eclecticiq.com or fill in the EclecticIQ Audience Interest Survey to drive our research toward your priority area.
You might also be interested in:
Chinese State-Sponsored Cyber Espionage Activity Targeting Semiconductor Industry in East Asia
Ransomware and DDoS Feature in The Apex of Crime-as-a-Service Report
Decrypting Key Group Ransomware: Emerging Financially Motivated Cyber Crime Gang
Appendix
[1] “NVD - CVE-2023-20198.” Accessed: Oct. 17, 2023. [Online]. Available: https://nvd.nist.gov/vuln/detail/CVE-2023-20198
[2] Shadowserver [@Shadowserver], “Cisco CVE-2023-20198 exploitation activity: We see over 32.8K Cisco IOS XE IPs compromised with implants based on the check published by Cisco in https://blog.talosintelligence.com/active-exploitation-of-cisco-ios-xe-software/ IP data on implants shared out daily in: https://shadowserver.org/what-we-do/network-reporting/compromised-website-report/ tagged ‘device-implant’. https://t.co/iJUNHAOTje,” Twitter. Accessed: Oct. 18, 2023. [Online]. Available: https://twitter.com/Shadowserver/status/1714483336876355873
[3] “Active exploitation of Cisco IOS XE Software Web Management User Interface vulnerability,” Cisco Talos Blog. Accessed: Oct. 18, 2023. [Online]. Available: https://blog.talosintelligence.com/active-exploitation-of-cisco-ios-xe-software/
[4] “CERT Orange Cyberdefense on X,” X (formerly Twitter). Accessed: Oct. 20, 2023. [Online]. Available: https://twitter.com/CERTCyberdef/status/1714567941184749609
[5] C. O. CyberDefense, “CVE-2023-20198.” Oct. 20, 2023. Accessed: Oct. 20, 2023. [Online]. Available: https://github.com/cert-orangecyberdefense/Cisco_CVE-2023-20198
[6] “CERT-UA,” cert.gov.ua. Accessed: Oct. 18, 2023. [Online]. Available: https://cert.gov.ua/
[7] “WS_FTP Server Critical Vulnerability - (September 2023) - Progress Community.” Accessed: Oct. 18, 2023. [Online]. Available: https://community.progress.com/s/article/WS-FTP-Server-Critical-Vulnerability-September-2023
[8] “CVE-2023-40044,” AttackerKB. Accessed: Oct. 18, 2023. [Online]. Available: https://attackerkb.com/topics/bn32f9sNax/cve-2023-40044
[9] “RCE in Progress WS_FTP Ad Hoc via IIS HTTP Modules (CVE-2023-40044).” Accessed: Oct. 19, 2023. [Online]. Available: https://www.assetnote.io/resources/research/rce-in-progress-ws-ftp-ad-hoc-via-iis-http-modules-cve-2023-40044
[10] S. (@SophosXOps@infosec. exchange) X-Ops, “The ransomware actors didn’t wait long to abuse the recently reported vulnerability in WS_FTP Server software. Even though Progress Software…,” Mastodon. Accessed: Oct. 18, 2023. [Online]. Available: https://infosec.exchange/@SophosXOps/111222943608438109
[11] beichen, “GodPotato.” Oct. 18, 2023. Accessed: Oct. 18, 2023. [Online]. Available: https://github.com/BeichenDream/GodPotato