By Aleksander W. Jarosz, Fusion Center Analyst
Our Fusion Center analysts are heavy users of EclecticIQ Platform and know the product inside out. Threat Intelligence analyst Aleksander W. Jarosz talked to his Fusion Center colleagues to find out about their favorite platform features.
“The IT community is confronted with incidents of all kinds and nature; new threats appear on a daily basis. Fighting these security incidents individually is almost impossible. Sharing information about threats among the community has become a key element in incident response to stay on top of the attackers. Reliable information resources, providing credible information, are therefore essential to the IT community, or even at broader scale, to intelligence communities or fraud detection groups.”
(Abstract from ‘MISP -The Design and Implementation of a Collaborative Threat Intelligence Sharing Platform’, Cynthia Wagner et al., https://github.com/MISP/MISP)
Threat intelligence practices promise to become a cornerstone of the IT security landscape. Good threat intelligence begins with adopting strong practices and following a strong data model. Analysts need a robust software package to provide a dynamic workspace to enable them to bring together disparate information into an effective structure that yields larger patterns. It is this software that provides the means to express intelligence patterning and allows EclecticIQ to make predictions about the threat landscape.
EclecticIQ Platform allows Fusion Center analysts to rapidly structure and link pieces of intelligence into more coherent data. The TIP combines source feeds that comprise the latest threat intelligence from a plethora of producers and aggregators. The EclecticIQ TIP includes core features that allow analysts to maintain and shape threat intelligence data in a way that adds substantial value. From a Fusion Center point of view, it allows our analysts to connect additional data that reveal larger trends and patterns to clients. In turn, our customers are able to be more reactive and adopt an advanced posture in mitigation and response to the myriad threats they face.
Here are some of the core features of the EclecticIQ TIP that Fusion Center analysts enjoy using to amalgamate intelligence:
> An SDK that allows analysts to customize and extend features of the platform
The backbone of the TIP includes software that allows analysts to drill down to specific entities and build out new features on demand. This adaptability helps analysts evolve with the threat landscape and customize features as threat intelligence becomes more complex.
> Ability to visualize intelligence and relationships between multiple sources, threats and attack patterns
Threat intelligence data is only as good as what you can do with it. Along with the ability to present granular data to clients, the TIP provides a visual web of entities and how they are connected. Clients can use this to walk through the connections (path-walk) between different threats, threat actors and malicious infrastructure. This provides a strong way to visualize the data. Having this visual representation is a powerful tool for uncovering patterns and the larger structure within malicious incidents. This helps analysts understand the complex interrelated nature of the threats faced by clients.
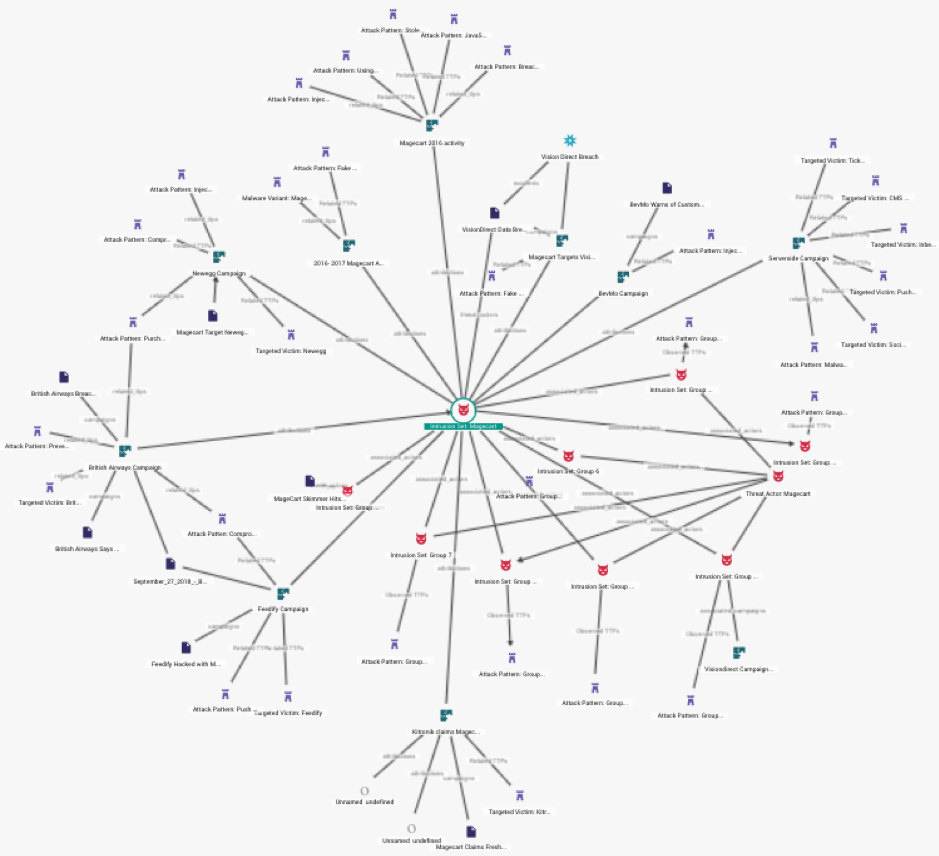
Figure 1. Relationships of activity within Magecart.
> The ability to perform an investigation and report entirely within the platform
Analysts can fuse and create data within the platform. Fusion Center analysts create data through their own investigations into security incidents, attack patterns, malware behavior and more. New entities or information added to existing entities provide extra value to our clients. Proprietary intelligence gained through investigations enhances client knowledge around cyber threats and improves their security posture. The TIP is highly integrated and allows analysts to perform investigations and threat hunting by pivoting between multiple sources and enrichments (like WHOIS data, results from VirusTotal, GeoIP data, etc.). Analysts can then use the results from these to further enrich the intelligence and provide clients with an extra edge. Staying within the TIP to create, write and edit a threat intelligence report is a time saver and allows analysts to focus on the quality of the data.
> Dynamic datasets and filters based on nuanced, granular search queries
This feature allows analysts to isolate specific data and filter out the noise. This is crucial as threat intelligence evolves within an increasingly complex structure. It is important to pinpoint the relevant intelligence. Fusion Center analysts like this feature because it allows EclecticIQ Fusion Center to produce more accurate intelligence and filter out false positives. This provides clients with more accurate information on topic-specific areas that they can successfully action.
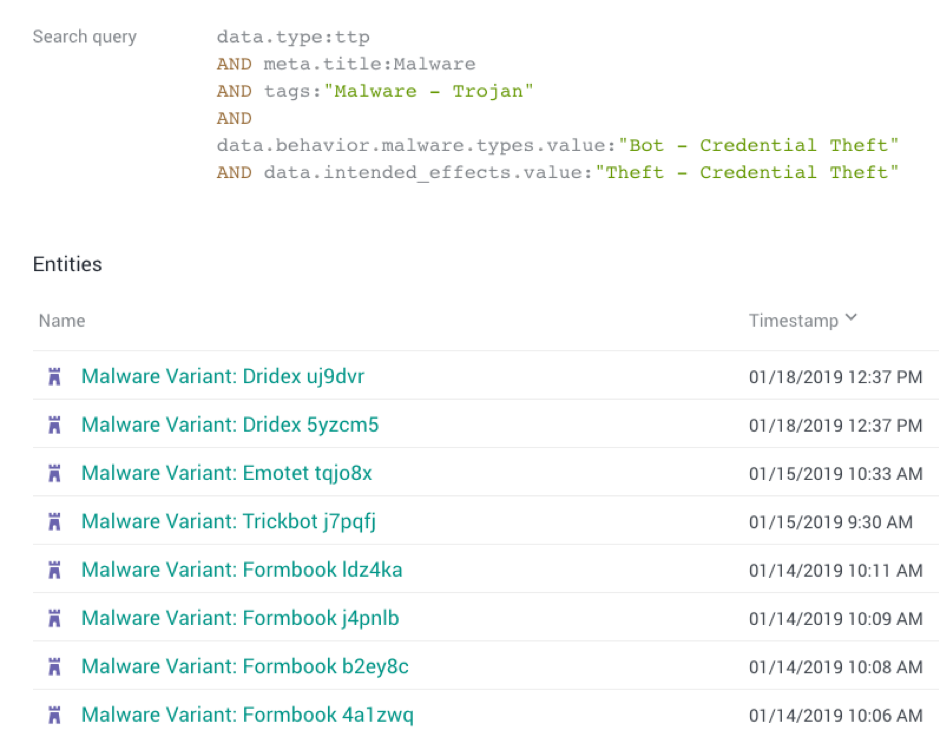
Figure 2. Drilling down to specific banking trojans delivered within the last month.
> Relationships are automatically enriched further with additional source data
The ability to automatically add relevant data to new and existing entities is instrumental in adding value to intelligence. This feature allows Fusion Center analysts to pivot off a single specific indicator or entity to discover larger connected infrastructure used by threat actors and malware. The automation is valuable because it enables Fusion Center analysts to focus on the quality of the intelligence.
The above is just a snapshot of the many features that EclecticIQ Platform holds. Yet, as is the case with any software, there are certain features that individual users find more useful. Our mission is to provide an analyst-centric Threat Intelligence platform, so our product development team is interested in receiving feedback like the above from own analysts.
If you are an analyst using our platform, or any kind of TIP, reach out and let us know what your favorite day-to-day features are.
We hope you enjoyed this post. Subscribe to our blog for more interesting reads on Cyber Threat Intelligence or check out our resource section for whitepapers, threat analysis reports and more.
