October is Cybersecurity Awareness Month, and this week’s theme is “Cybersecurity First.” Putting cybersecurity first could mean so many different things to different people and organizations. In this article we explore what it means to us at EclecticIQ.
So, what does it mean to put cybersecurity first?
Let’s start by acknowledging that—unless cybersecurity is your business—it’s probably not *the* most important activity on your plate. Rather, you just want cybersecurity to enable your business to run smoothly and safely. For most organizations (and people) it’s really a matter of understanding your risk tolerance and taking a risk-based approach—by identifying and focusing on various cyber risk components—to decrease your risk to an acceptable level.
Of course, you must be clear-eyed about your risk tolerance. Is your attack surface expanding (e.g., WFH or new cloud-based instances)? Are you considering the ever-evolving threat landscape (e.g., the emergence of Ransomware-as-a-Service, Killware, Terabit DDoS attacks, etc.)? Can you really absorb the impact of a cyberattack (e.g., shutting down revenue-generating operations or resorting to Post-It notes to communicate)? If you miscalculate the dangers or the consequences, then your risk mitigation efforts are likely to fall short when tested by cyber attackers.
So, the better question is probably something like “How can we better prioritize cybersecurity?” Now that is something we can all work toward, and on that topic we have some ideas to share.
First, grow a culture of cyber awareness and cyber involvement. At all levels and across all departments, cybersecurity considerations should be factored into decision making. Executives and leaders need to include input from their cybersecurity team when making business decisions. Technical experts who design products should focus not only on the sleekest, fastest design, but also on making a device that can be easily secured. Workers at all levels should feel comfortable and responsible to contact their IT department if they click on a phishing link—seeking help should be a first reaction, not a dreaded last resort.
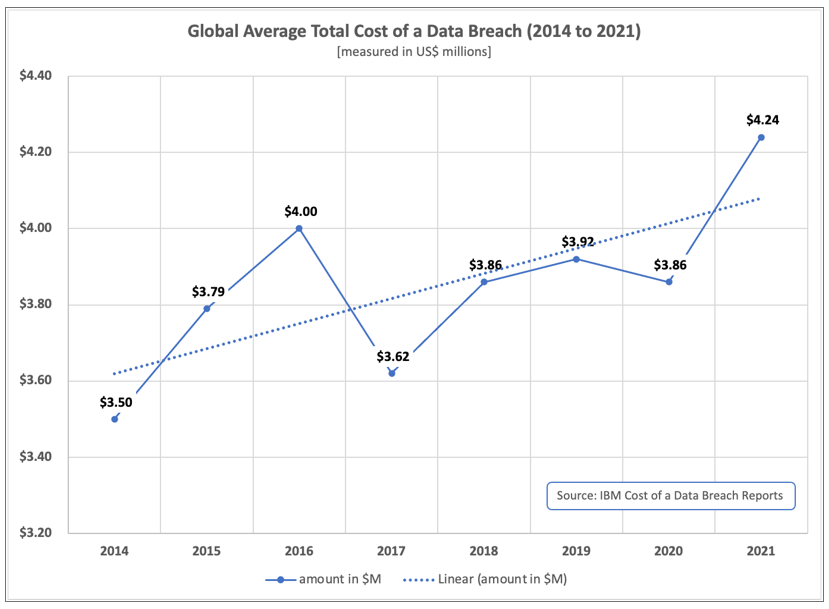
In a different vein, instead of quantifying how much it would cost to be cyber secure, consider the costs associated with not being cyber secure. For instance, the latest IBM Cost of a Data Breach report shows a steady rise in the average costs being borne by organizations victimized by successful attacks (see chart below). Of course, these costs vary by organization size, industry, attack type & magnitude, geography and more—but they are significant.
In addition to the hard costs associated with a successful cyberattack, there are the hard-to-quantify costs—such as the value of intellectual property, the impact on worker productivity & morale, the loss of customer trust, or the hit on your stock price—which are probably much more impactful than the cost of developing a cyber-secure environment.
Finally, strike a balance between improving security posture now while simultaneously making efforts to build a stronger security process in the long-term. A great security program should not make the user’s life more difficult—in fact it should be mostly transparent to the user. Unfortunately, most security programs just are not there yet. Their users may have to adjust to cumbersome procedures or slower processes right now in the name of implementing better security solutions for the future. Communicate the need, communicate the solution.
Obviously, there’s a lot more involved in crafting and implementing an adequate cybersecurity program for your needs. But the bottom line is—if you take a clear-eyed view of your risk tolerance, understand where your cyber risks exist, and chip away at those risks until they’re aligned—then we’re sure you’ll find the right prioritization for your cybersecurity program.
Before you go, check out our posts for the other three weeks of cybersecurity awareness month. Last week we explored careers in cybersecurity, the week prior we discussed what it means to ‘phight the phish’, and we began the month with a look at what it is to be cyber smart. Enjoy!
