By Diego Sappa, Senior Solution Architect
 Automation is essential to security. Especially in a modern threat landscape, where Security Operation Centers (SOCs) are overloaded with thousands of alerts every day. At the moment, without automation it’s simply not possible to minimize false alerts and not miss out on anything important.
Automation is essential to security. Especially in a modern threat landscape, where Security Operation Centers (SOCs) are overloaded with thousands of alerts every day. At the moment, without automation it’s simply not possible to minimize false alerts and not miss out on anything important.
But while automation is a powerful tool in the fight against adversaries, increasingly it is not enough. Security teams suffer from an overload of false positives and swivel-chair analysis from trying to make sense of the relentless flow and variety of data.
Today, there is more telemetry to analyze, ever-growing IT environments and more technology to manage. The result is a larger attack surface. Given the amount of security resources is not growing at the same scale, the need for automation is very clear.
Meanwhile, adversaries are making use of automation tools themselves and becoming ever more creative – and more familiar with the responses of the security teams they target.
Sophisticated and determined human hackers with automated tools must be met with human defenders with automation-based defense. Automation alone is not enough. Sorry, AI.
The problem with automation
SOCs and Security Information and Event Management (SIEM) solutions have long been a mainstay of enterprise security. But the landscape is changing and growing more complex daily.
This is a consequence of a steady increase in online channels. The spread of enterprise BYOD programs, increased use of mobile devices, and the rapid proliferation of the Internet of Things have led to a wider attack surface and new opportunities for adversaries and criminals.
The result has been an overload of incidents, both in volume and variety, that the traditional SOC/SIEM set-up has struggled to contain or process. SIEM dashboards are lighting up with unnecessary alerts. This wastes security analysts’ time, leaving it more difficult to identify the real threats.
To deal with this, SOCs must either raise their alarm thresholds to respond to the most obvious hacks, or spend more and more time chasing false alarms.
So: too many false negatives or too many false positives. Neither is acceptable for enterprise security operations.
Automation has long been the promised answer to this problem – automation supported by machine learning or some other form of Artificial Intelligence (AI). Yet sophisticated and determined hackers can use the blind spots of automation systems against them. And defending against cyber threats is a difficult proposition for AI. Often, AI tools need to operate with too sparse a dataset. Or there’s too much uncertainty: too many out-of-the-box attack methods exist to provide a comprehensive defense against attackers.
In addition, there’s often a necessary bias to how AI learns from datasets. And knowing how that bias is applied in cyber defenses can aid adversaries and be used as a weapon against enterprises.
Automation is a powerful tool, but it is not the panacea for modern security postures. Smart attackers need to be met by smart human defenders aided by automation.
Plugging the gap
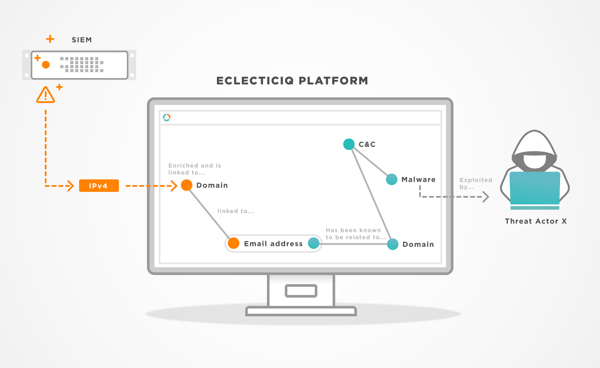
SOCs need to be supplemented by a separate organizational function dedicated to long-term planning and strategy for cybersecurity. That’s the role of a threat intelligence practice, a team of human threat analysts supported by well-monitored automation, and a Threat Intelligence Platform (often abbreviated as TIP).
A TIP lets organizations focus on specific threats and indicators based on security cases and topics. In addition, a TIP’s automation capabilities can be used to reduce actual investigation time spent by SOC teams and to add context to an alarm.
Crucially, it allows human security analysts to proactively – rather than reactively – improve defenses. For that, you need analysts who know your organization inside-out and can uncover hidden threats that may seem like minor blips in the SIEM. As a result, the SIEM can be ‘tuned’ following the analyst’s proactive investigation outcomes.
To do this, analysts need to draw upon experience and creativity. Automation supports them and augments their research and allows them to create both short- and long-term strategies for keeping the organization secure.
For example, automated responses can block an IP address exhibiting suspicious activity, but a threat analyst can do much more. Working with a TIP, the analysts can add context and identify who’s behind a suspicious activity, which tactics, techniques and procedures (TTPs) are potentially being used, and whether any open campaigns are planned. As a result, the analysts can recommend multiple courses of actions for the SOC to follow, significantly expanding its scope as well as providing advisories for security teams.
Threat Intelligence Platforms are increasingly being viewed as an integral part of automated responses. Gartner, for instance, sees a TIP as one of three pillars that make up SOAR (Security Orchestration, Automation and Response) technologies, in which the human element plays a crucial part. Gartner states that a combination of human and machine power for performing incident analysis and triage can help to define, prioritize and drive standardized incident response activities.
These are analytical tasks the SOC was never designed to perform. The best way to evolve an ‘intelligent SOC’ is to give it the backing of automation-powered threat intelligence from human analysts.
By way of an analogy, an effective boxer needs to outmuscle and outthink an opponent. The SOC gives our boxer the strength needed to pack a punch, but the TIP provides the brains.
Understanding how your opponent moves, his strong points and his weaknesses makes you – the SOC ‘boxer’ – much more effective. And more likely to dodge blows and land the winning punch.
Learn more about Threat Intelligence Platforms and how they can augment a SOC in our white paper.
We hope you enjoyed this post. Subscribe to our blog for more interesting reads on Cyber Threat Intelligence or check out our resource section for whitepapers, threat analysis reports and more.
