
Despite the ever-increasing focus on the state of industrial cybersecurity, accurate and timely threat intelligence for industrial control systems (ICS) remains hard to come by. Worse still, the burgeoning interest around incidents caused by novel capabilities like TRITON can often give way to hyperbolic commentary from outlets far removed from the reality of the situation. To combat this, EclecticIQ Fusion Center has teamed up with Dragos to bolster our Critical Infrastructure offering.
Why is ICS Threat Intelligence Different?
The operational technology (OT) environment is a distant relative of the enterprise IT environment. Although many cybersecurity best practices are applicable to both, an ICS-focussed adversary’s background, intent and leveraged TTPs are so radically different that we must tailor our own approach.
Coverage
As an Intelligence Requirement, the scope of ‘threats to critical infrastructure’ can be difficult to define. For our Critical Infrastructure bundle we have adopted three distinct categories previously defined by Dragos:
- Direct ICS Impact: actors and capabilities seeking to directly impact ICS operations. Examples: Stuxnet, Industroyer, TRITON.
- Interested Adversaries: actors with demonstrated interest in ICS and operational networks but have not demonstrated destructive or disruptive intent. Examples: Dragonfly, OilRig, Thrip.
- Indirect Impact: threats not tailored to disrupt industrial processes, but which can impact operations. Examples: Shamoon, Stonedrill, WannaCry.
Funnily enough, Dragos’ categories directly map to those we initially established when first designing the scope of product, jokingly naming them ‘Big Dogs’, ‘Sneaky Lurkers’ and ‘Tick Tick Boom’.
Integrating with our knowledge base
Like many vendors, Dragos track actors and capabilities according to their own nomenclature. We integrate this nomenclature with all reported actor and malware aliases into a single STIX entity, meaning the actor is searchable in our Platform according to whichever alias an analyst favours – Chrysene is searchable by OilRig, APT34 and HelixKitten, just as TRISIS is searchable by HATMAN and TRITON.
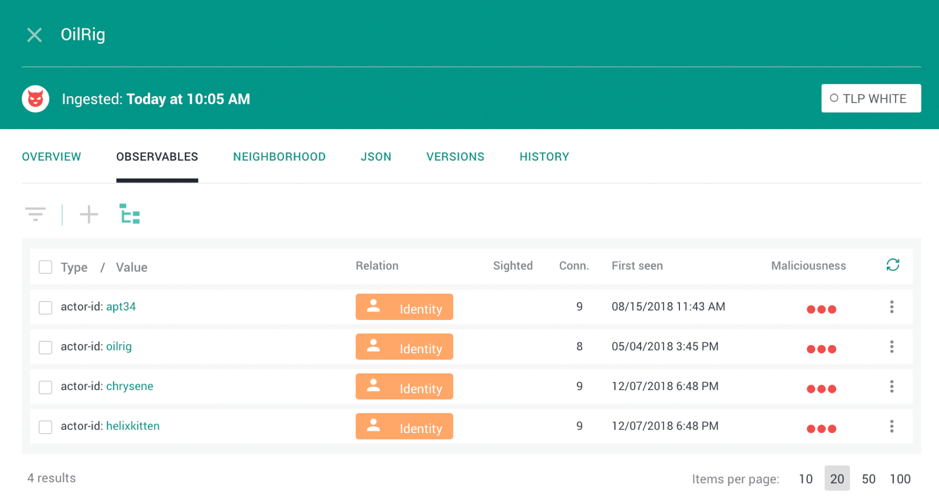
This is not total aggregation. There are cases in which aliases can be completely standardised – for example, in TRITON’s case. However, by adding actor aliases to the entity’s metadata we are not necessarily saying that APT34 is OilRig. Threat actors are groups of real people who may move between different organisations, taking their knowledge and tools with them, so the idea that we can track them as distinct entities without any confusing overlap is unrealistic. The objective is simply to store overlapping intrusion sets in such a way that analysts can easily understand the points of intersection and divergence as report by each vendor.
TTP-driven Approach
Dragos’ approach to CTI is closely-aligned with ours in the respect that it is heavily TTP-driven. Tracking actors according to their attack patterns and the behaviour of their malware enables analysts to defend proactively, rather than based on static values related to an attack that has already occurred. By maintaining and developing a knowledge base of actors’ TTPs of long periods of time, from campaign to campaign, we can assess which attack patterns they favour and how to proactively mitigate them.
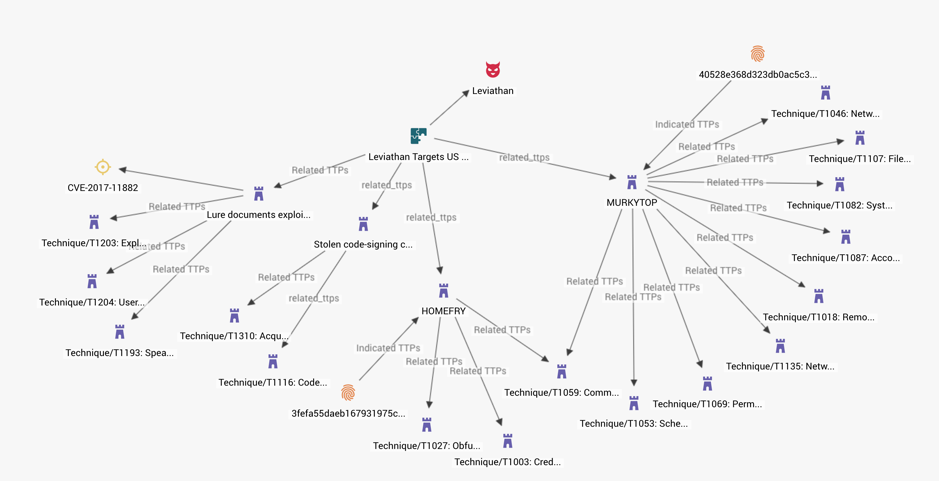
Selected snapshot of Leviathan campaign reported by FireEye demonstrates TTP-driven approach
All our TTPs are mapped to relevant MITRE ATT&CK techniques. As well as providing strategic view of a TTP’s functionality and intent, this allows users to build dynamic datasets based on combinations of high-level attack patterns and other contextual information. A basic example shows a dataset that isolates malware and tools with T1113: Screen Capture that have observed targeting organisations within the energy telecommunications or utilities sectors:
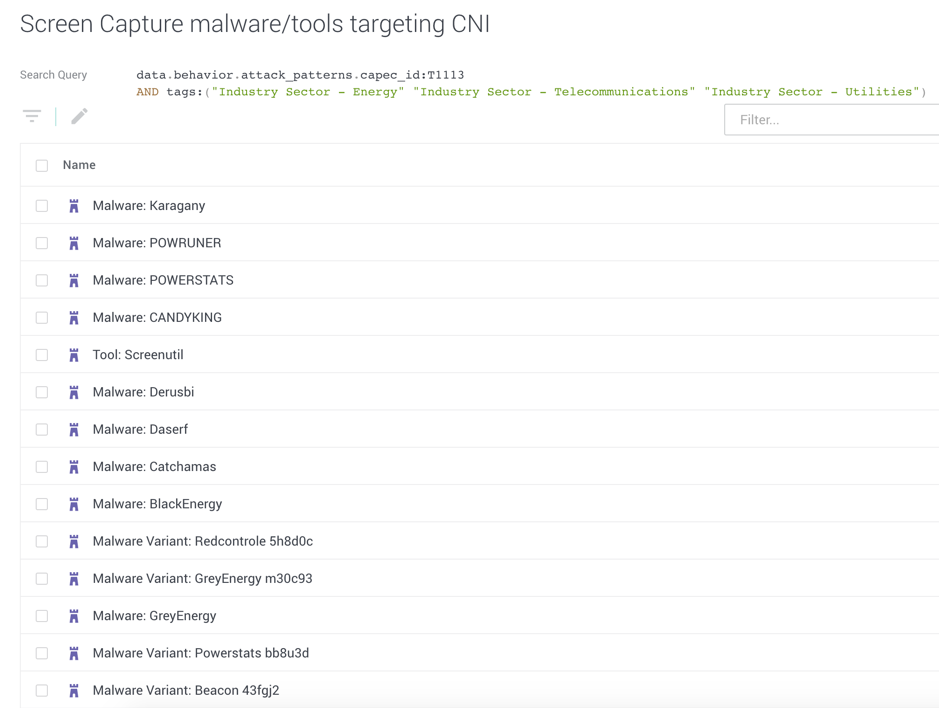
By mapping TTPs to high-level categories like Defense Evasion and Persistence we can also track over time which specific tactics are most commonly observed for each tactic in order to prioritise mitigations.
Conclusion
Threat Intelligence for industrial control systems is different. The intents and TTPs observed in campaigns of adversaries targeting require:
- Clear definition of an organisation’s intelligence requirements against the backdrop of the threat landscape;
- Aggregating known actors and capabilities in order to minimise the noise created by conflicting nomenclatures;
- A TTP-driven approach
See our Critical Infrastructure data sheet for more details.
We hope you enjoyed this post. Subscribe to our blog for more interesting reads on Cyber Threat Intelligence or check out our resource section for whitepapers, threat analysis reports and more.
