 What a year it’s been!
What a year it’s been!
When it became clear in February 2020 that the world was facing a major pandemic, we at EclecticIQ knew adversaries would put their malicious tactics, techniques, and procedures (TTPs) into high gear to exploit organizations as they shifted their focus from security to the health crisis.
As a global threat intelligence organization that uses EclecticIQ Platform, a leading threat intelligence platform (TIP), we launched a campaign to deliver targeted, prioritized, and actionable threat intelligence reports on our closely followed COVID-19 Threat Intelligence blog.
Teaching People to Fish
To stretch the biblical proverb, if you give a person a piece of threat intelligence they may identify one threat. But if you teach a person how to conduct a threat intelligence campaign, they’ll develop their own intelligence and even get ahead of threats. Continually!
Thus, we decided to document in a whitepaper the tradecraft used by our threat intelligence team. The goal was to provide practical guidance, best practice recommendations, and beneficial insights to any cyber threat intelligence (CTI) organization conducting a threat investigation of any size and scope.
In this whitepaper, we cover some of our most important practices. Here are four examples.
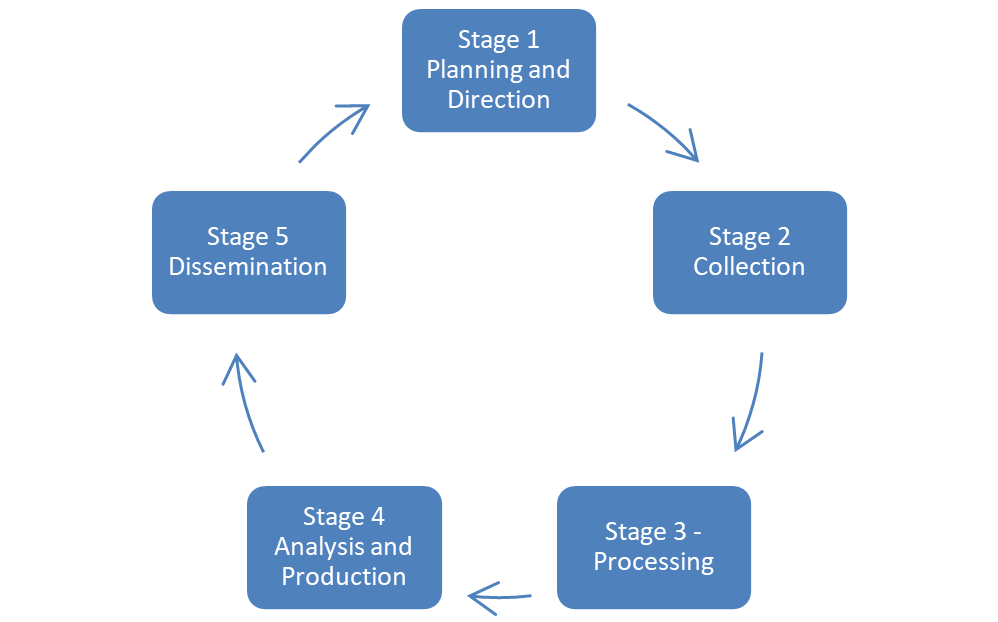
Starting with the CTI Lifecycle
EclecticIQ’s threat intelligence team leverages EclecticIQ Platform to execute a standard CTI lifecycle, as illustrated below. We emphasize the importance of following the full lifecycle because most organizations take shortcuts due to being short-staffed and under continual pressure to produce results.
In the whitepaper, we highlight both the desire to cut corners and its downsides.
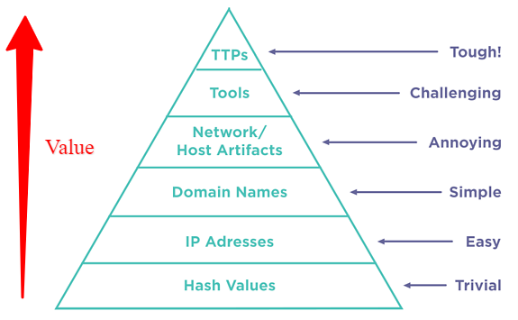
Climbing the Pyramid of Pain
Moving through the lifecycle is like taking a trip, and one of the arduous treks on that journey is climbing the Pyramid of Pain. As we illustrate in the whitepaper, the best way a resource-strapped CTI operation can conduct a successful campaign is to innovate and institute triage of IOCs to optimize staff skills. This triage, which distills millions of indicators per week down to a few TTPs, is essential to climbing the pyramid because it allows the CTI team to prioritize analysis and response.
You’ll read about our success in detecting an APT group that targeted a vaccine organization and its research infrastructure in the whitepaper.
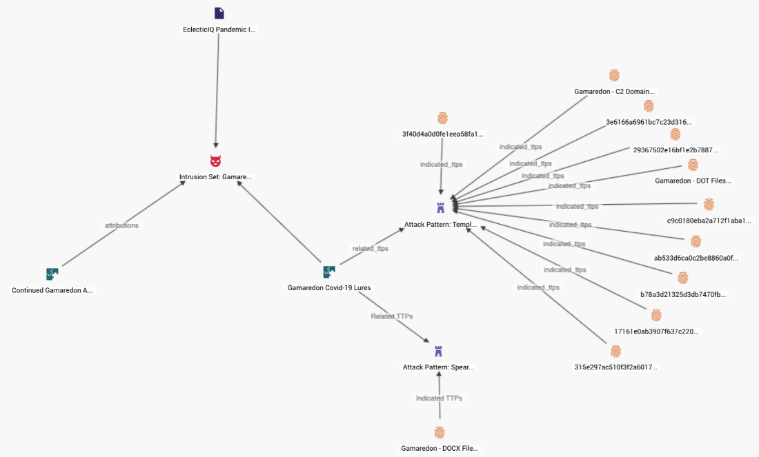
Leveraging the TIP to Illuminate Trends
Central to any helpful analysis is illuminating trends. Trend spotting requires a TIP like EclecticIQ Platform, which allows a CTI operation to quickly track and establish critical relationships between the data.
The whitepaper discusses how trends help prioritize the investigation and supply salient points for reports. For example, we were concerned that work-from-home (WFH) put workers at greater risk of falling for phishing attacks due to a more relaxed attitude and fewer security controls. Indeed, we saw multiple phishing lures exploiting “Covid-19” attributed to Gamaredon, a Russian APT group.
Looking in the Rearview Mirror
An indispensable aspect of any threat intelligence campaign is the historical context provided by the TIP and the ability to query stored intelligence about different use cases. After all, most threat actors follow established patterns. In the paper, we discuss how the TIP can correlate current and past entities. Indeed, we found examples where high-profile threat actors pivoted to vaccines as an opportune target using their established TTPs.
Ten Recommendations to Move Forward
Our purpose for publishing this whitepaper is to provide actionable and prescriptive guidance, based on our experience, which can benefit organizations looking to implement and run a successful threat intelligence campaign. We invite you to download the whitepaper to learn more about the above best practices and take away 10 valuable recommendations from our world-class threat intelligence team.
