EIQ Intelligence Center Data: Emotet Gains Momentum in Recent Months
EclecticIQ Researchers identified continued growth of the Emotet botnet’s activity based on reported botnet command and control (C2) nodes and unique payloads observed from November 2021 through April 2022.
Figure 1 below illustrates new botnet C2 nodes discovered daily and indicates Emotet operators appear to be adding new botnet nodes daily, with growth accelerating in March and April. The increase in C2 nodes likely indicates the continued growth of the botnet. It is also likely that with more nodes the botnet will become more stable, meaning takedown efforts will be difficult and require significant cooperation between law enforcement and private organizations.
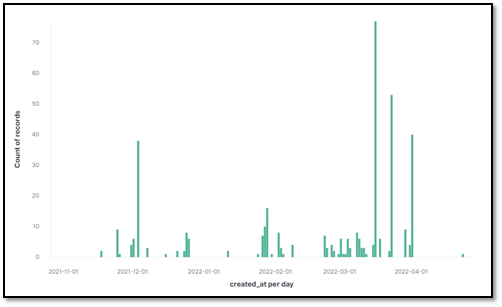
Figure 1 Emotet bots reported per day
Figure 2 illustrates that Emotet operators regularly compile new payloads to be delivered via phishing. The number of payloads observed in the given timeframe, at times more than 1,000 unique payloads in a 24-hour period, likely indicates an automated method for compiling payloads. Changing payloads can make it more difficult for network defenders to identify infections and respond quickly.
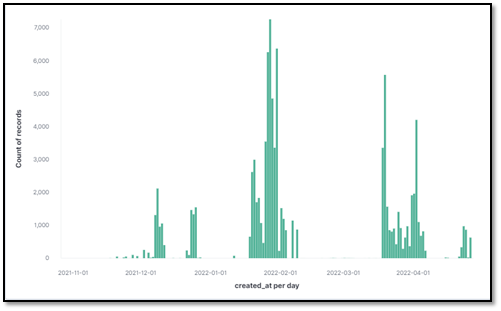
Figure 2 Emotet payloads reported per day
EclecticIQ Researchers assess it is likely the increasing number of C2 nodes combined with regularity of newly observed payloads that Emotet will continue to re-establish and stabilize its operations after past takedowns, while expanding the botnet’s reach and sophistication to avoid future take down attempts. Organizations should consider Emotet a growing threat especially with its previous associations with Colbalt Strike Beacons and ransomware operations.
New and Noteworthy: Ransomware Operators may Target Agriculture Organizations during Critical Operating Periods
The Federal Bureau of Investigation (FBI) issued a warning to the US Food and Agriculture sectors during planting and harvesting seasons that ransomware actors may be more likely to attack during critical planting and harvesting seasons [1]. Attacks during these periods would likely cause significant disruptions to operations, causing financial losses, and possibly disrupt the food supply chain. The FBI notes that ransomware operators may perceive these critical periods as factors that will increase the willingness to pay the ransom quickly to avoid significant disruptions.
It is likely that ransomware operators have also targeted other industries during critical periods and holidays to apply pressure to pay ransoms. The Covid-19 pandemic caused significant stress on the shipping and logistics sectors. Some ransomware operators utilized this pretext to apply additional pressure to victims to pay ransoms and recover quickly [2]. CISA released two alerts between August and November 2021 for organizations to “stay vigilant” of ransomware attacks during the holiday periods [3] [4].
EclecticIQ Researchers assess it is likely ransomware operators will utilize critical operating periods and holidays to target organizations on an increasing basis. It is important that businesses in all industries anticipate these days and prepare accordingly. This may include extra security awareness training to all employees for potential phishing lures, reviewing vulnerabilities and patch managements, and ensuring disaster recovery plans have been tested recently.
Exploit Tools and Targets: Zero-days Exploited in 2021 more than Double
According to Mandiant zero-day exploitation more than doubled in 2021 over the year prior [5]. Research found that state sponsored espionage groups primary based out of China were the most likely to utilize zero-day exploits in cyber-attacks. Financially motivated actors including ransomware groups account for about one-third of the observed exploits. Mandiant suggests that with the continued growth of the of the exploit market zero-day exploitation will continue to increase in coming years.
The increasing threat of zero-day exploitation poses a risk across most industries and sectors. However, EclecticIQ Researchers assess these exploits are most likely to be used when targeting governments, software supply chains, critical infrastructure, or large financial institutions. These organizations are more likely to have mature security practices that make using a zero-day more necessary and the kind of payoffs that are lucrative enough for the threat actor to utilize it.
It is important that organizations adopt a layered secured approach, adhere to best practices, and quickly patch vulnerabilities as quickly as possible. These measures can limit the impact from zero-day exploits.
You might also be interested in:
Microsoft Under Pressure from Zero Day Vulnerabilities and SolarWinds Targeting
Issue #05: Russo-Ukrainian Cyberattacks, and Updates on Lapsus$ and Conti Ransomware Operations
References:
- https://www.ic3.gov/Media/News/2022/220420-2.pdf.
- https://www.nbcnews.com/tech/security/ransomware-hackers-hit-us-supply-chain-experts-warn-rcna1718.
- https://www.cisa.gov/uscert/ncas/current-activity/2021/11/22/reminder-critical-infrastructure-stay-vigilant-against-threats.
- https://www.cisa.gov/uscert/ncas/alerts/aa21-243a.
- https://www.mandiant.com/resources/zero-days-exploited-2021.
Structured Data
Find the Analyst Prompt and earlier editions in our public TAXII collection for easy use in your security stack.
TAXII v1 Discovery services: https://cti.eclecticiq.com/taxii/discovery
You may also download the content as eiq_json, stix1_2, stix2_1.
Please refer to our support page for guidance on how to access the feeds.
About EclecticIQ Threat Research
EclecticIQ is a global provider of threat intelligence, hunting and response technology and services. Headquartered in Amsterdam, the EclecticIQ Threat Research team is made up of experts from Europe and the U.S. with decades of experience in cyber security and intelligence in industry and government.
We would love to hear from you. Please send us your feedback by emailing us at research@eclecticiq.com or fill in the EclecticIQ Audience Interest Survey to drive our research towards your priority area.