Standard Operating Procedures (SOPs) are probably not the very first thing that come to mind when talking about Cyber Threat Intelligence. At EclecticIQ, we understand that SOPs are at the cornerstone for accurate, consistent, timely, and scalable intelligence operations. This blogpost will tell you why.
Why Do You Need Standard Operating Procedures?
A Standard Operating Procedure documents the actions to complete an activity or to respond to a situation. SOPs help our analysts to complete their intelligence operations in the exact same way, so that we can deliver our intelligence products with steady quality and on time.
Consider the following example that highlights the significance of SOPs for intelligence operations.
As shown in the image below, EclecticIQ Fusion Center disseminates all intelligence products using Structured Threat Information Expression (STIX).
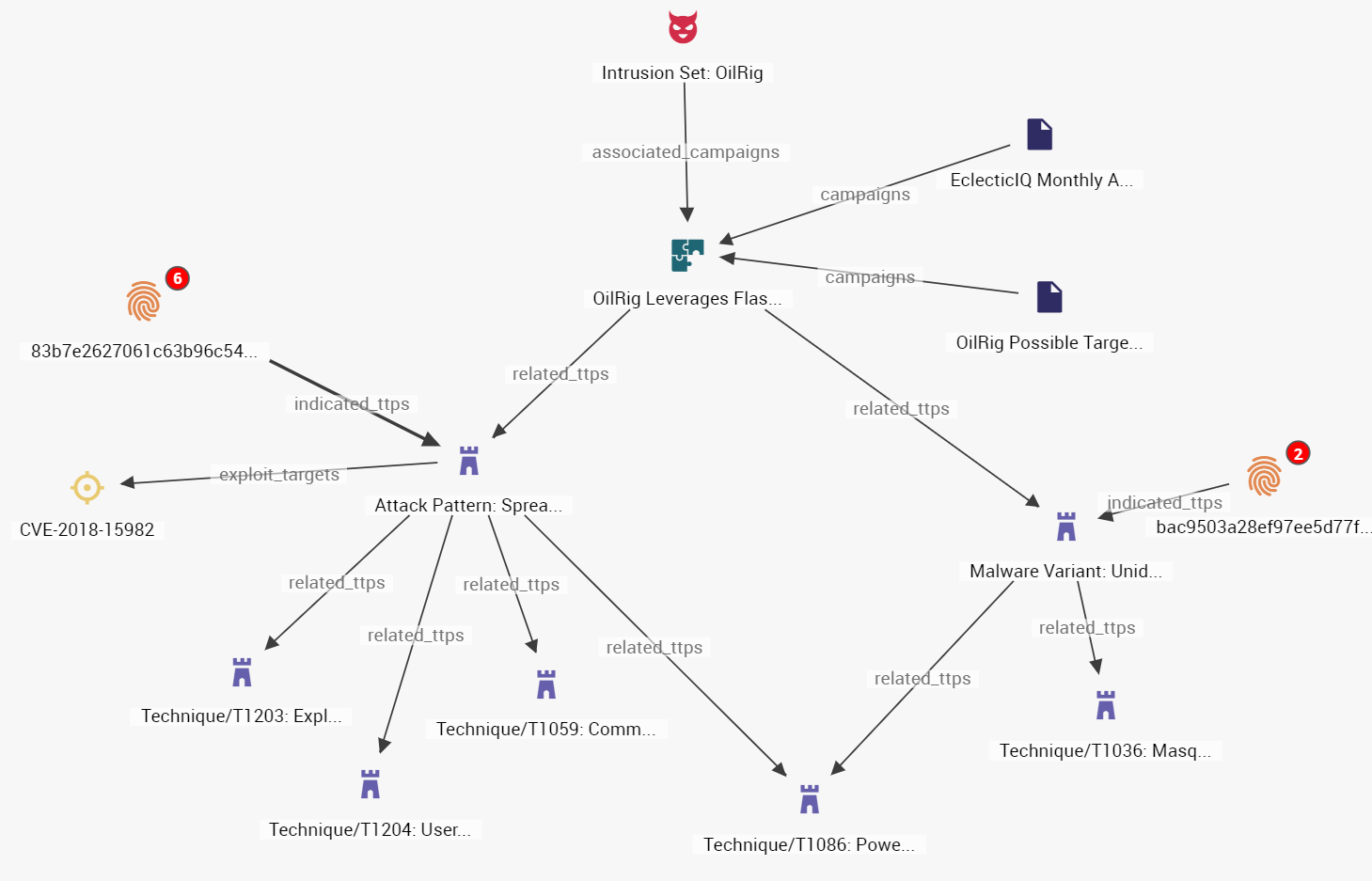
Figure 1 - EclecticIQ Fusion Center Structure Intelligence
However, the STIX model is too flexible. There is far too much room for interpretation and analysts working on the same topic can easily create multiple different interpretations of the same data.
Imagine tasking two analysts to STIXify the exploitation of CVE-2017-11882 served by an RTF attachment? Or to represent code-overlap between malware variants? Or to structure the installation of a Remote Access Trojan that is served from a DDNS domain?
Without some form of guidance, each analyst will likely create their own version/interpretation of the data and the results would be very much different. Also, when analysts attempt to execute a task in many different ways, it will take them longer to complete it. This is unfavorable because intelligence stakeholders rightfully expect that intelligence is delivered on time and presented in a consistent manner.
SOPs Streamline and Improve Workflow
Similarly, SOPs exists for:
- OPSEC (Operations Security) during investigations
- Reviewing tactical report and investigations
- Handling of sensitive information
- Dissemination of intelligence products
...and for other CTI operations.
SOPs ensure that no matter which analyst is working on a case, the creation of an intelligence product is completed in the same way. Hence, our intelligence stakeholders receive their product in a consistent form. Furthermore, an analyst that investigates a case which may have been created weeks, months or even years ago, can easily grasp the meaning of the structure intelligence.
More Time for Analysis? – Automate and Scale
Analysts do not lose valuable time with guess work if they follow an SOP. They do not have to rack their brains to remember how to model a piece of intelligence, leaving more time to focus on the analysis.
Importantly, SOPs point out activities that are constantly being repeated by analysts. In this regard, SOPs can help to streamline CTI activities. They make workflows repeatable, lead to automation of tasks, and eventually scale intelligence operations.
Do Not be Afraid of Change
SOPs are also a great tool to train new employees. Well-documented SOPs will help new joiners to understand how things work. At EclecticIQ, we realize that analysts feel encouraged to question existing workflows if they can refer to a written SOP. This is also beneficial as it allows for evolution of SOPs over time.
An SOP is a living document. We acknowledged that workflows we once deemed adequate, may not be fit for purpose today. Hence, we review our SOPs frequently and change them as needed.
Hopefully, this blog post gave you good glimpse on why a Standard Operation Procedures are effective tools that every intelligence team should have.
Subscribe to our blog for more interesting reads on Cyber Threat Intelligence or check out our resource section for whitepapers, threat analysis reports and more.
