Synopsis
With cyberattacks such a common occurrence, analysts must be able to stay ahead of the curve by investigating files and indicators of compromise quickly and efficiently. The EclecticIQ Intelligence Center is the perfect tool to facilitate investigations like these. This post will describe how EclecticIQ’s Intelligence & Research analysts used Intelligence Center to investigate the potential maliciousness of files leveraging NATO-themed phishing lures, and how they operationalized this intelligence by feeding it into the EclecticIQ Endpoint Response (ER) security tool.
The Need for Targeted Collection: The Benelux Region’s Unique Concerns About Cyber Threats
If past attacks are any indicator of future risk, Belgium, the Netherlands, and Luxembourg (collectively Benelux) region of Europe is an attractive target for cyber threat actors. A review of past cyberattacks targeting Benelux shows that the number of attacks targeting this region has grown in a way that is typical for what one might expect in a relatively connected, business-intense region. (1, 2) It is difficult to know the exact number of cyberattacks since many go unreported, but based on those that are reported, analysts note a few patterns. Most Belgium, Luxembourg, and The Netherlands-focused cyberattacks remain localized; they are severe enough to make news and to be disruptive by reducing or suspending services, but generally, the damage from attacks is contained. Often, individuals or assets in the region may be caught up in wide-reaching software vulnerabilities or supply chain issues, simply because they are part of an international network of users. Judging from news and press, cyberattacks were also typical in that they appear opportunistic with attackers pursuing any vulnerable target they find, regardless of industry; schools and universities, businesses, and government entities have been victimized in recent years. (3, 4, 5, 6, 7, 8, 9)
Defining Initial Collection Requirements: Identify and Sample Benelux-Based Potential Targets
To dig deeper into the Benelux cyber threat landscape, analysts developed a list of possible high-profile targets in those three countries; the list included government and commercial entities, as well as non-government organizations.
Analysts used a VirusTotal Intelligence query to look for phishing lures related to the identified organizations for a time period of a few weeks during late Spring 2022. The query was used in a custom integration that leverages an API to ingest VirusTotal Intelligence search results into Intelligence Center further analysis. The query returned twenty-two files.
Refining Collection Requirements: Using VT and the EclecticIQ Intelligence Center to Search and Ingest Key Data
Analysts parsed data by reviewing each of the twenty-two files to determine which merited further study. Eleven files featured NATO-related phishing lures. Six of these eleven files used one of two Ukraine-themed phishing lures with identical titles:
- “list of nato (sic) generals hiding in the basement of the Azovstal steel plant.docx”
- “Nato's generals who were hiding in the underground bunker of the Azovstal steel factory just surrendered.docx”
Given the high interest around the world in the Russia-Ukraine war, analysts decided to focus the investigation on this cluster of data.
These six data points, along with associated IOCs (URIs, domain names, and IPV4s) were ingested into Intelligence Center via its API for further analysis and enriched to show linkages between the entities. The graphic below shows this data cluster in Intelligence Center —complete with the initial six emails represented as entities around the periphery, and the related hashes and other data represented as observables in the center. Note the enrichment process pulled in associated indicators, three of which were URIs associated indirectly with the start point data.
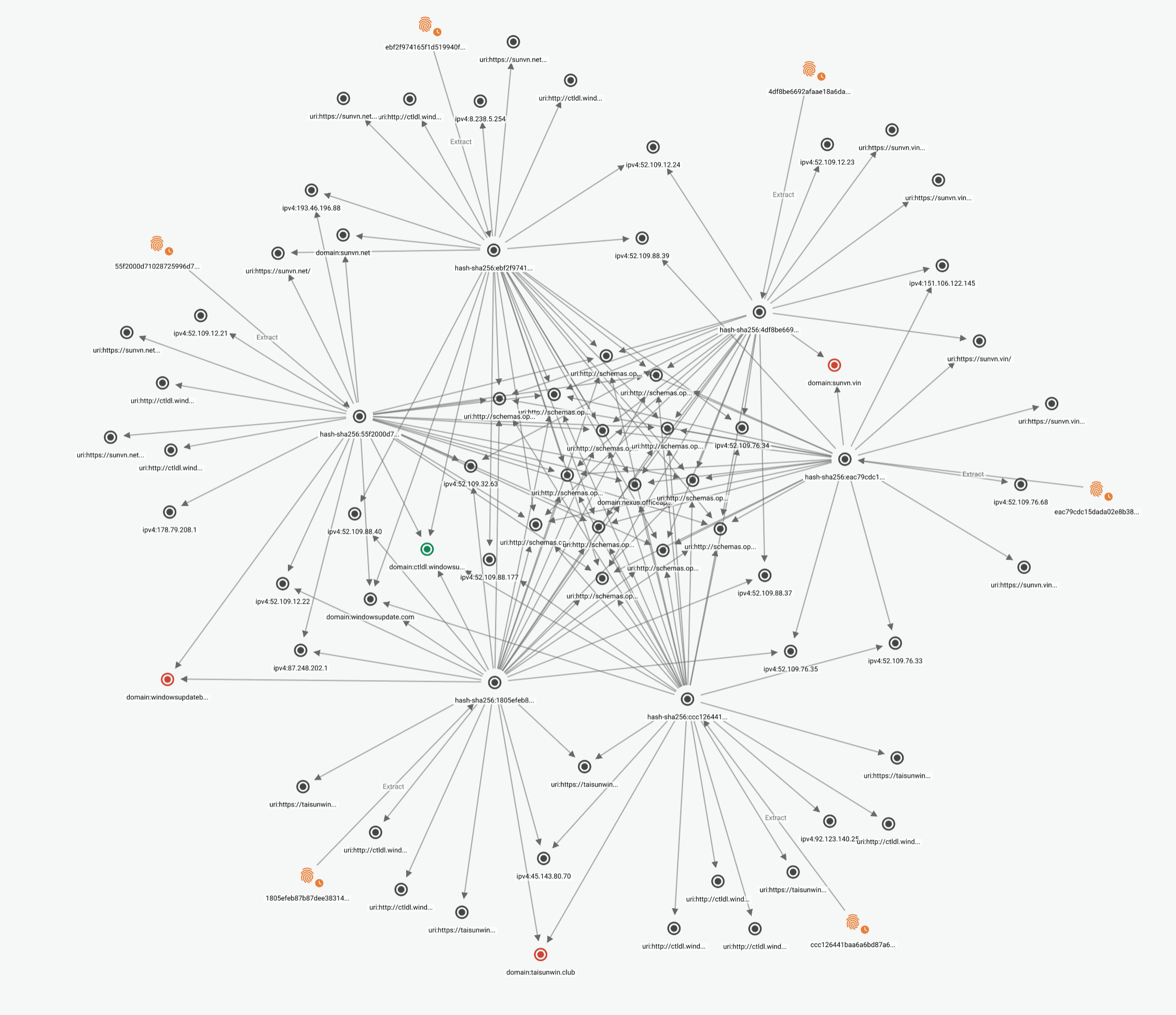 Pic.1: The EclecticIQ Intelligence Center graph displays the six initial start points, related data, and three malicious entities (in red).
Pic.1: The EclecticIQ Intelligence Center graph displays the six initial start points, related data, and three malicious entities (in red).
Processing Data Through Enrichment & Pivoting
Once the data of interest were identified, analysts enriched that data and pivoted to new data. To do this, analysts focused on the three malicious URIs in the graphic above, leveraging search features in the Intelligence Center.
Investigation Into One Malicious Observable Uncover the Use of a Third, Similar Lure
Looking deeper into the data available, one observable, “taisunwin[.]club” led analysts to discover another lure that was similarly themed to the six start point lures, but which did not appear in that data set. Clicking the taisunwin[.]club entity on the graph led to a hash under the heading “original related entities.”
This entity directs readers to a Tweet warning researchers of a malicious document exploiting CVE-2021-40444 entitled “US, Allies Probe Claim of Chemical Agent in Ukraine.docx”. (10) From this, the Intelligence Center immediately leads researchers to another possible malicious document using another Ukraine-focused lure, which can assist analysts in rapidly understanding the breadth of the activity in question. The more related lures which are easily identified, the larger the activity cluster is likely to be.
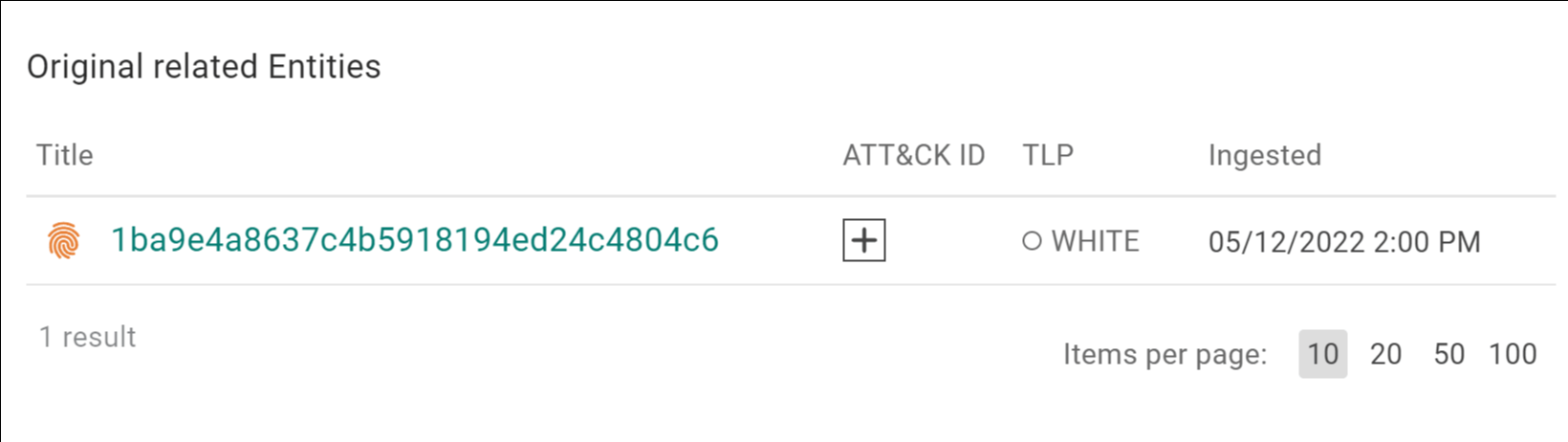 Pic 2: The hash above was identified via the “Original Related Entities” section in the IC and leads analysts to pivot to a warning for malicious documents originally posted to Twitter.
Pic 2: The hash above was identified via the “Original Related Entities” section in the IC and leads analysts to pivot to a warning for malicious documents originally posted to Twitter.
Digging Into a Second Malicious Observable Reveals Possible Connection to a Botnet Server
Another malicious observable identified by Intelligence Center was the URI sunvn[.]vin. Using the graph feature to click on the observable, users immediately see a similarly named URI under the heading “Related Via Extraction.”
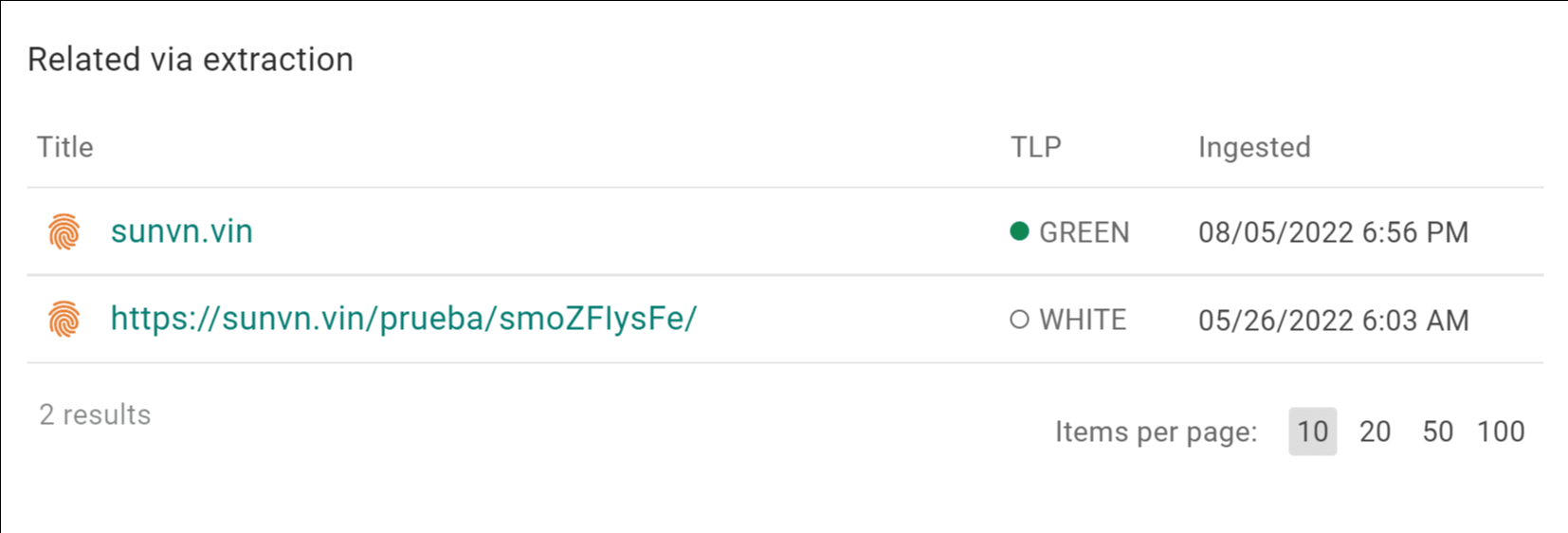 Pic 3: The “Related Via Extraction” section of the Intelligence Center directs analysts to a URI which was not identified in the initial data pull but merits further study.
Pic 3: The “Related Via Extraction” section of the Intelligence Center directs analysts to a URI which was not identified in the initial data pull but merits further study.
Selecting the second URI from the list brings up that as its own entity. Intelligence Center has already ingested data that characterize this entity as a “URL that is used for botnet command & control.” In addition, the Tags applied to the entity automatically by the Intelligence Center are ‘botnet_cc’, individual source tags, and tags related to malware families thought to have used that server. This provides the analyst with a starting point for completing the initial characterization of the threat, giving researchers the ability to move quickly beyond the data available in the initial tranche of results to instead discover the infrastructure underlying the initial sample data.
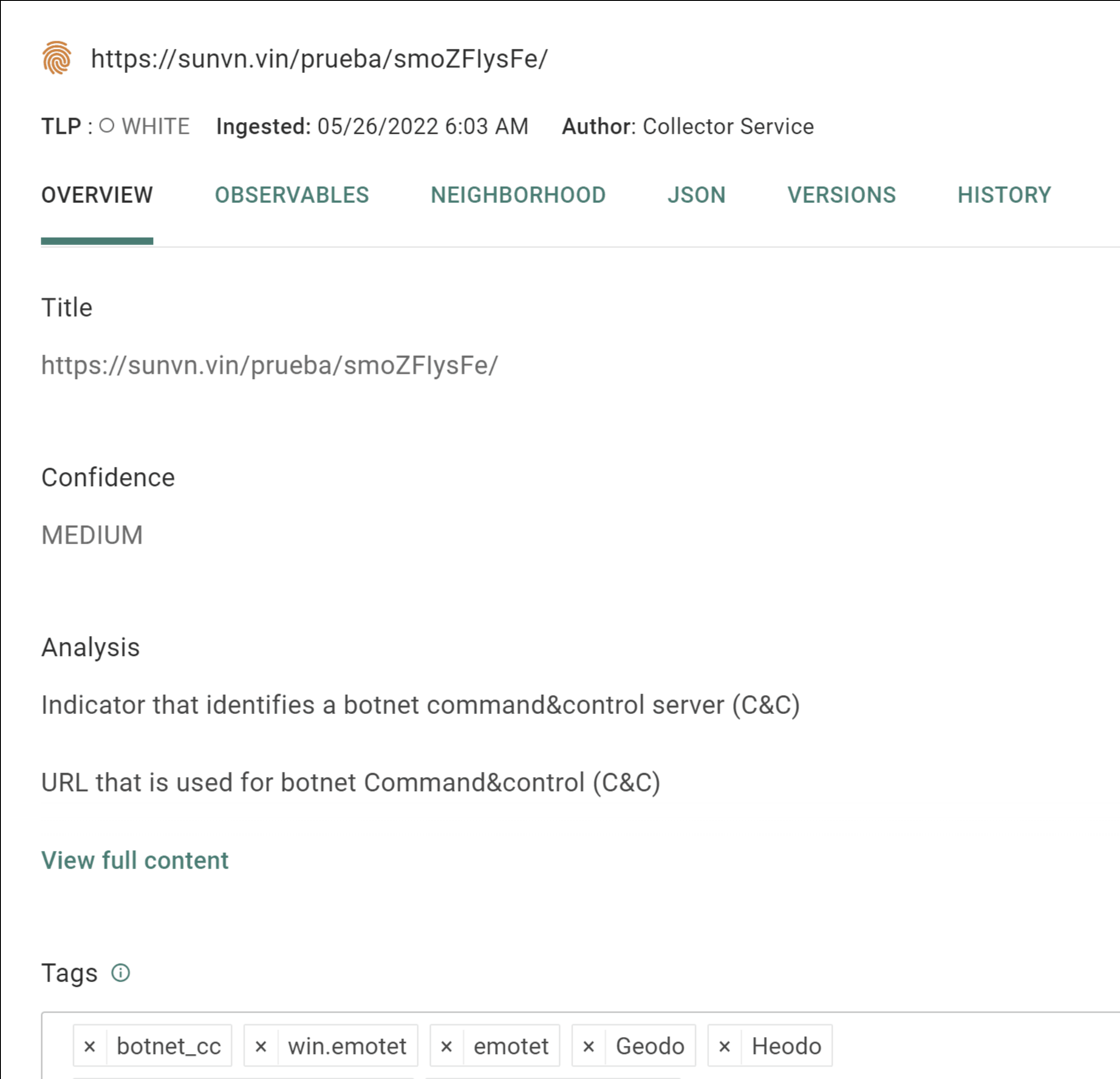 Pic 4: Clicking on the related URI entity brings up its details, including a tag indicating possible relation to a Botnet C2 server.
Pic 4: Clicking on the related URI entity brings up its details, including a tag indicating possible relation to a Botnet C2 server.
An Examination of the Third Malicious URI Indicates a Connection to Known Malware
The third of three malicious URIs that Intelligence Center identified through its enrichment process is windowsupdatebg.s.llnwi[.]net. This URI, when queried in Intelligence Center, greatly illustrates the value of Intelligence Center in the fourteen related malicious hashes it returns in the query. Every one of the fourteen results on the list provides insight through either tags or analysis indicating ties to malicious activity. (A list of the nine hashes in question can be found in the Appendix.) Nine of the fourteen hashes were unique, and the remaining five hashes were duplicates of four results; some hashes are returned multiple times because the Intelligence Center contains entities for the indicator from more than one source. This cluster of results illustrates the value of the Intelligence Center because it returns results that are easy to navigate and can help analysts quickly develop an understanding of the potential threat, all the while enabling more in-depth pivoting where necessary. For example:
- One indicator led to a French-language message urging caution against malicious documents, and others provided general labels such as “downloader”, “exploit”, or “trojan.”
- Other indicators were either tagged with or contained text that pointed users toward specific malware. In this case, Emotet, Geodo, Heodo, and Abracadabra were the most prevalent; they appeared in the descriptions of five of the nine unique hashes in the list.
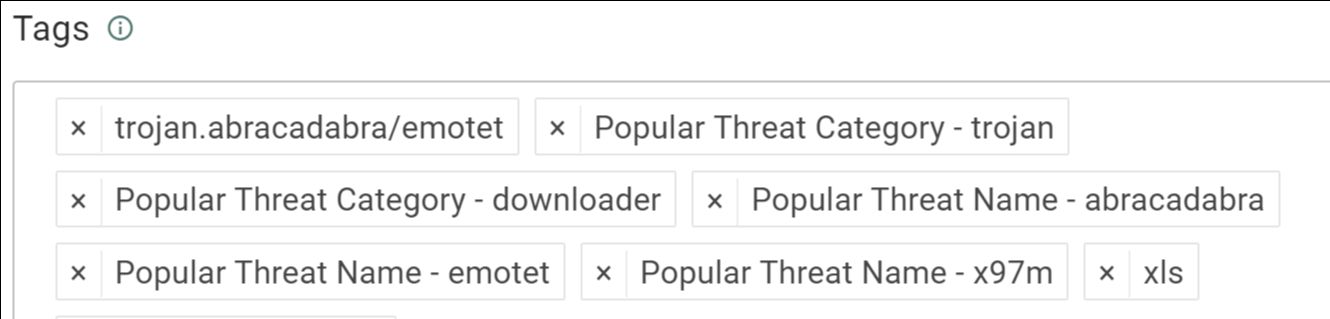 Pic 5: A list of tags seen in one of the hashes associated with domain: windowsupdatebg.s.llnwi[.]net, one of the three malicious URIs associated with the NATO-themed phishing lures.
Pic 5: A list of tags seen in one of the hashes associated with domain: windowsupdatebg.s.llnwi[.]net, one of the three malicious URIs associated with the NATO-themed phishing lures.
Here again, Intelligence Center provides an intuitive way for analysts to get the most out of their investigation. A natural pivot is for analysts to then investigate Emotet, and the quickest way to do that is to check out the Emotet malware overview, which appears in Intelligence Center as a malware TTP object. The malware overview is easily located using the “Search and Browse” function. Along with the written overview, Intelligence Center includes the Emotet knowledge pack which contains a workspace and data sets that automatically pull in various types of indicators, reports, detection signatures, and threat actors associated with the malware, its variants, and aliases.
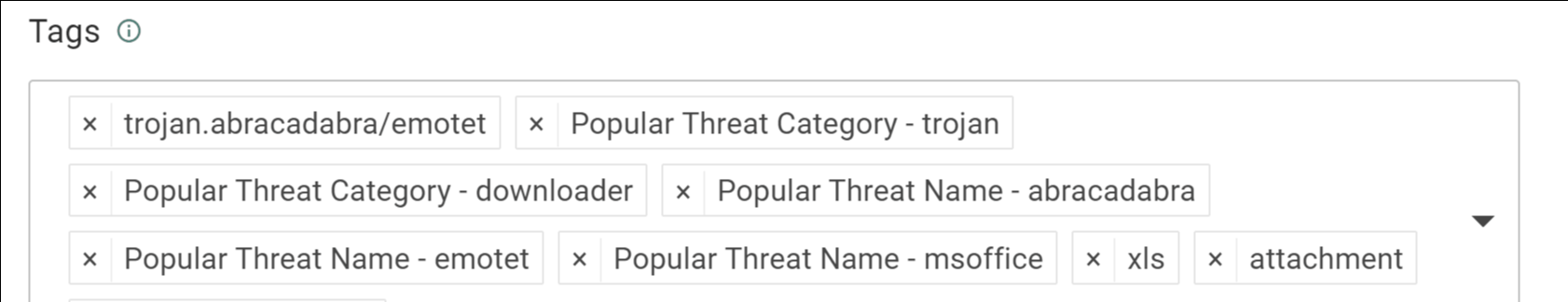 Pic 6: The tags automatically applied to the indicator in the Intelligence Center give analysts a quick way to identify potential malicious activity, and provide direction for follow-up investigation
Pic 6: The tags automatically applied to the indicator in the Intelligence Center give analysts a quick way to identify potential malicious activity, and provide direction for follow-up investigation
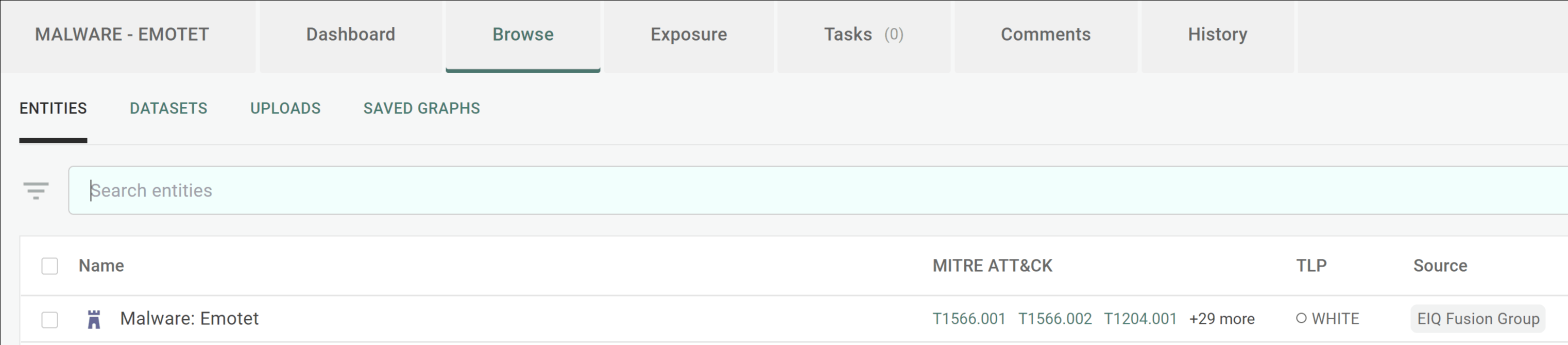 Pic 7: The Emotet Malware TTP as part of the Emotet workspace in the Intelligence Center.
Pic 7: The Emotet Malware TTP as part of the Emotet workspace in the Intelligence Center.
Operationalizing the Indicators for Threat Hunting Using EclecticIQ Endpoint Response
Most EDR tools are capable of ingesting indicators from external feeds, but as the number of indicators increases with time, the EDR tools have problems managing signatures: threat hunting becomes akin to signature matching, which does not scale very well. The EclecticIQ ER solution solves this problem by providing analysts with the ability to not only upload the indicators of compromise from a tool like the Intelligence Center, owing to its Osquery-based engine with EclecticIQ extension, it also arms the SOC analysts with an easy-to-use SQL language to hunt for such indicators at scale.
In the current study, the analyst concludes the investigation by extracting the different file hash indicators (sha2 as well as md5) as the indicators of concern associated with the given campaign.
EclecticIQ ER's agent running on each host collects the properties associated with a file activity and ER's "Live Query" interface can be used to hunt for these indicators across the endpoint devices running the agents using simple SQL-styled syntax.
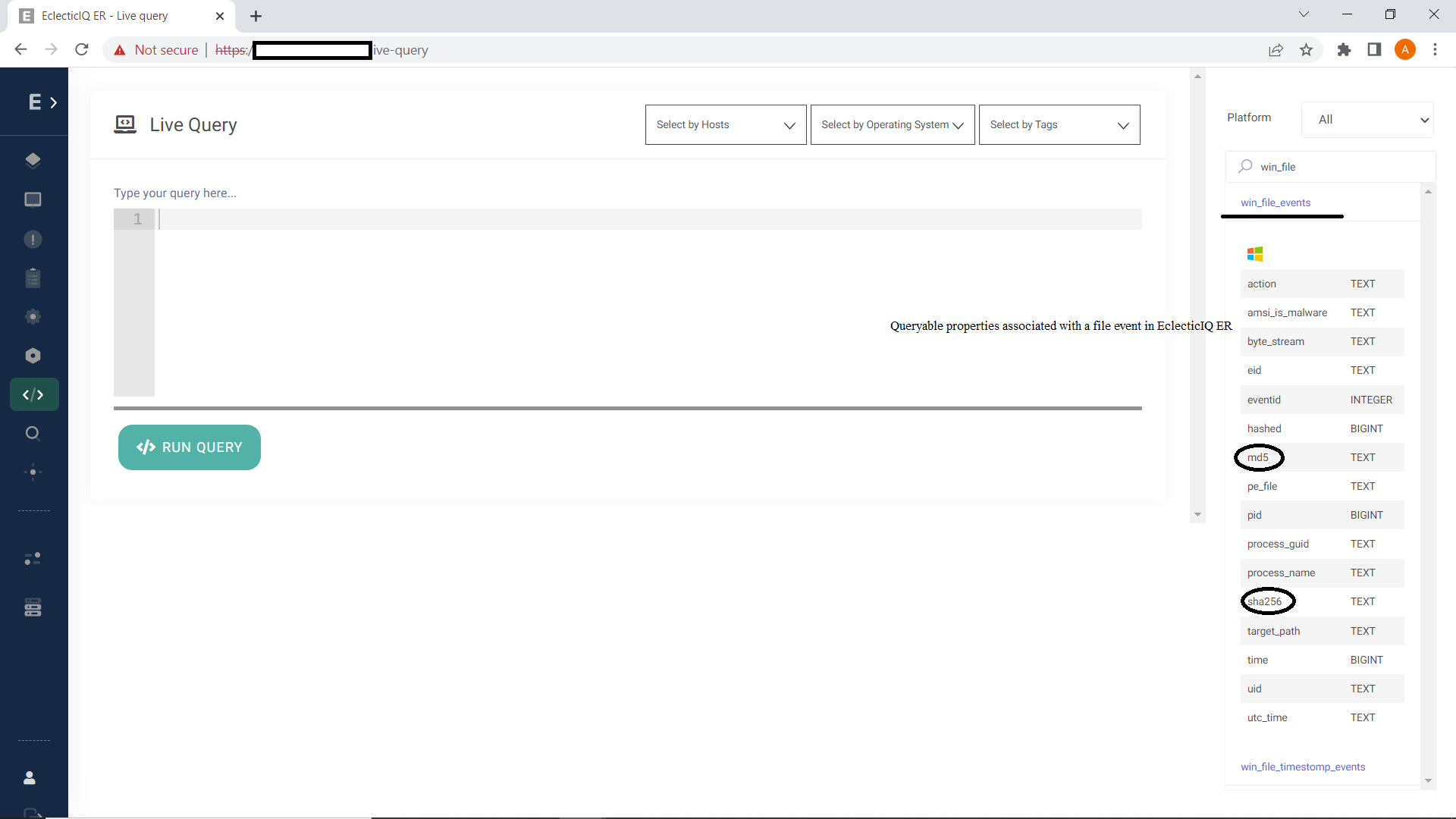 Pic 8: EclecticIQ ER’s Live Query Interface
Pic 8: EclecticIQ ER’s Live Query Interface
In order to hunt for the above-mentioned file hashes, the following query can be imported in the ER's management interface.
select * from win_file_events where (sha256 in
('27c933377f35879466d252b1cc2fc3a1474445faa0ea54c5bbbc16e62884abdc',
'a5926d0f35e5622a41776d75488f6e29f76261e61c124359327169a6674539e1',
'9a1c120455b2f9c6b0590ee0715876f9c37c52bd519c6b57594240c91ba2a40b',
'dbb86b8c7b41e9dd7b66d970b08e4949e94b90977d2cb432760cff269dd24098',
'3025d6dc44ce763b4f6a8b129bd98fafa69841477ad584eee7b74fc5e6cda83c',
'a23c30235bd7f138b6b681b4b285365503d50e10c7cf6a4ebc9a82186439563a',
'55f2000d71028725996d7edc2c847e103e3bbb8eea3da9220e396e2199d2d2c4',
'1805efeb87b87dee38314c8c4e6b6b00f5d0c5e5d750bda26ed7e7f58a4bd4d4'
) or md5='6346968714483ec737c6142b320ac98d');
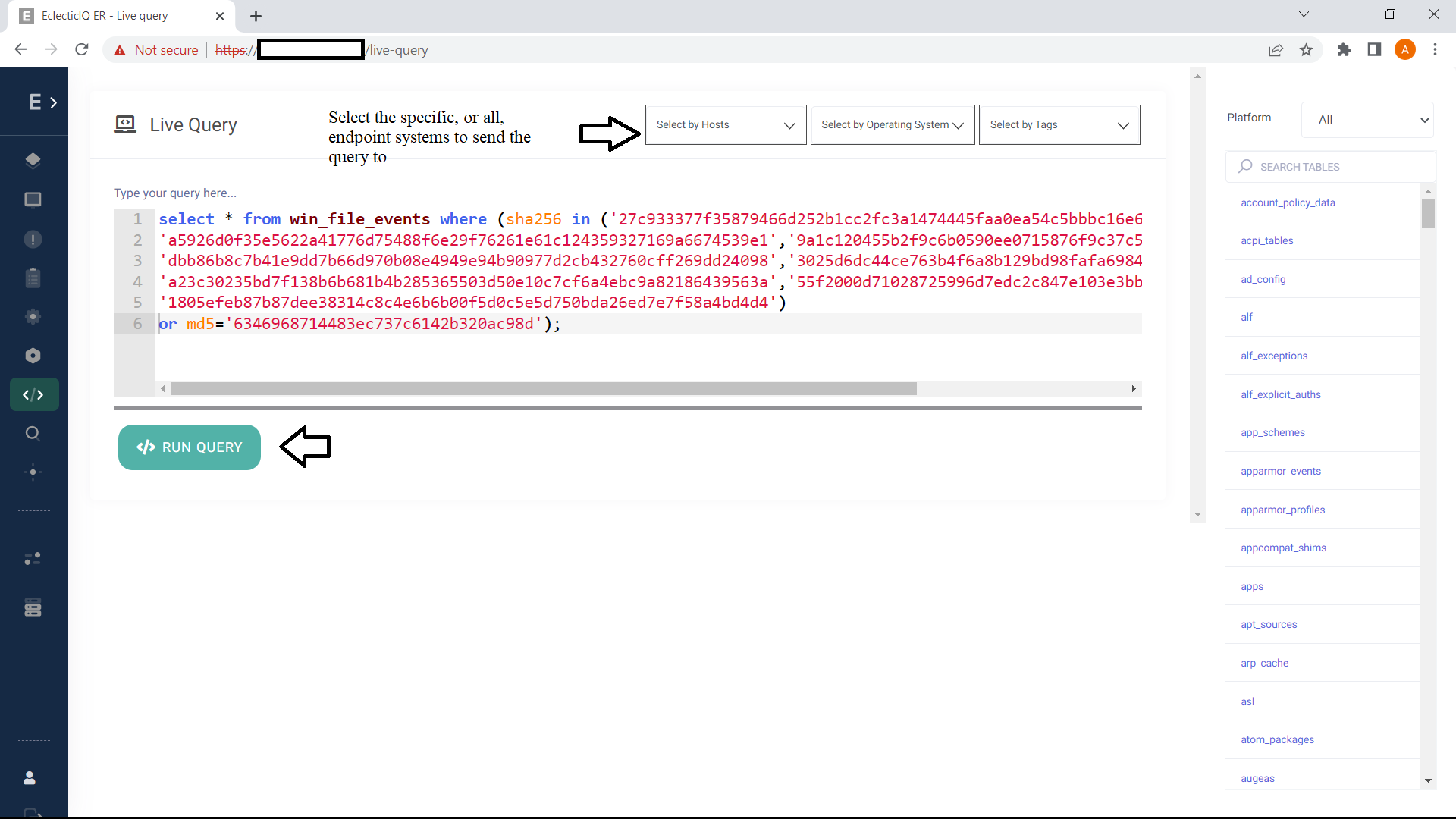 Pic 9: Importing a threat hunting Query in EclecticIQ ER
Pic 9: Importing a threat hunting Query in EclecticIQ ER
The results of the query will show the list of endpoint hosts where the malicious files might have been present or the absence of any such evidence.
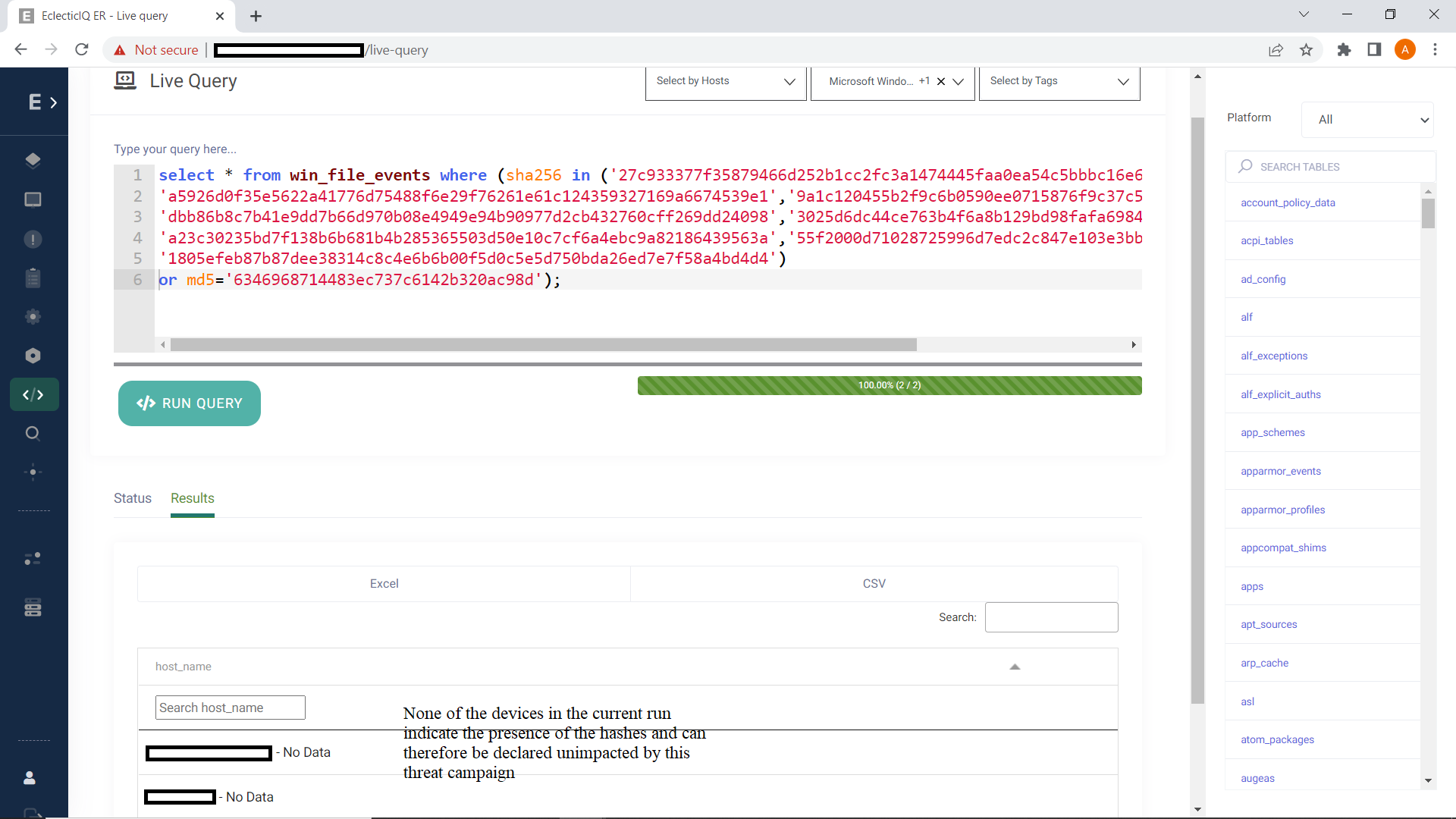 Pic 10: Results of ‘Live query’ in EclecticIQ ER
Pic 10: Results of ‘Live query’ in EclecticIQ ER
Conclusion: EclecticIQ Intelligence Center and ER Solutions Aid Investigations and Enable Quick Action
With the right tools – such as Intelligence Center and Endpoint Response solutions – analysts can accomplish more when it comes to threat hunting as it brings together the best-of-class intelligence with best-of-class telemetry. In the case of provocative NATO-themed phishing lures, analysts were able to use the Intelligence Center and Endpoint Response tools to quickly and efficiently investigate threats, identify malicious indicators, and take action to ensure no host network endpoints had been compromised. The ability to take steps like these quickly and seamlessly will be even more important as cyber threats proliferate. Ultimately, effective and efficient tools enable analysts to get to the essence of cybersecurity: providing value and defending their organization by providing timely, and actionable insights to prevent malicious intrusions.
About EclecticIQ Intelligence & Research Team
EclecticIQ is a global provider of threat intelligence, hunting, and response technology and services. Headquartered in Amsterdam, the EclecticIQ Threat Research team is made up of experts from Europe and the U.S. with decades of experience in cyber security and intelligence in industry and government.
We would love to hear from you. Please send us your feedback by emailing us at research@eclecticiq.com or fill in the EclecticIQ Audience Interest Survey to drive our research towards your priority area.
Structured Data
Find the Analyst Prompt and earlier editions in our public TAXII collection for easy use in your security stack.
TAXII v1 Discovery services: https://cti.eclecticiq.com/taxii/discovery
Please refer to our support page for guidance on how to access the feeds.
You might also be interested in:
Emotet Downloader Document Uses Regsvr32 for Execution
U.S. Seeks to Incentivize Semiconductor Manufacturing Domestically
References
-
https://www.brusselstimes.com/86197/reports-of-cyberattack-against-belgium-nearly-tripled-in-2019
-
https://therecord.media/city-of-liege-belgium-hit-by-ransomware/
-
https://nltimes.nl/2021/10/07/vdl-manufacturing-severely-affected-cyber-attack
-
https://nltimes.nl/2021/02/27/secondary-school-pays-ransom-hit-cyber-attack
-
https://nltimes.nl/2020/01/24/maastricht-univ-paid-eu250k-ransomware-hackers-report
Appendix
Below are the nine hashes which were identified via a query on the windowsupdatebg.s.llnwi[.]net URI.
- 27c933377f35879466d252b1cc2fc3a1474445faa0ea54c5bbbc16e62884abdc
- a5926d0f35e5622a41776d75488f6e29f76261e61c124359327169a6674539e1
- 9a1c120455b2f9c6b0590ee0715876f9c37c52bd519c6b57594240c91ba2a40b
- dbb86b8c7b41e9dd7b66d970b08e4949e94b90977d2cb432760cff269dd24098
- 3025d6dc44ce763b4f6a8b129bd98fafa69841477ad584eee7b74fc5e6cda83c
- a23c30235bd7f138b6b681b4b285365503d50e10c7cf6a4ebc9a82186439563a
- 55f2000d71028725996d7edc2c847e103e3bbb8eea3da9220e396e2199d2d2c4
- 6346968714483ec737c6142b320ac98d
- 1805efeb87b87dee38314c8c4e6b6b00f5d0c5e5d750bda26ed7e7f58a4bd4d4
