In cooperation with the ThreatFabric research team.
In cooperation with the ThreatFabric research team.
Executive Summary
With more countries providing COVID-19 contact tracing applications [1], threat actors will almost certainly continue to distribute malicious Android packages that pose as legitimate contact tracing applications serving banking trojans, spyware, and ransomware. As the current COVID-19 pandemic has caused public-health and economic issues to countries around the globe [2], nations have launched contact tracing applications to monitor, identify, alert and reduce the spread of infections. A joint analysis by ThreatFabric and EclecticIQ highlight that threat actors:
- Disguised Android packages as legitimate contact tracing applications for financial gain.
- Used repackaged commodity and opensource malware to lower the investment needed.
- Used third party port forwarding and secure tunnelling services to provide anonymization to command and control (C2) infrastructure.
- Delivered malicious Android packages through links pointing to phishing pages.
Walk-through of the investigation results in EclecticIQ Platform
Commodity and opensource malware used to lower barrier to entry
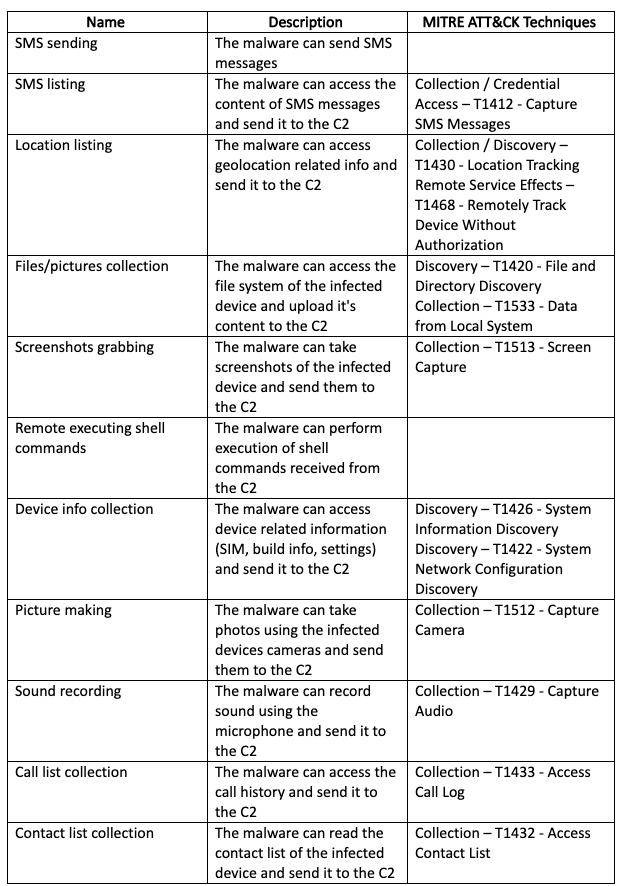
Malicious actors took advantage of the low barrier to entry to push malicious android applications under the guise of contact tracing applications to lower the investment cost needed and to steal user information. EclecticIQ and ThreatFabric researchers identified samples that were disguised as the official contact tracing applications for Colombia, Indian, and Indonesia. The samples used the commodity and opensource malware SpyMax [3], SpyNote [4], Aymyth [5], and repackaged applications with Metasploit [6] injected. One sample disguised as the official Indian contact tracing app had a thirteen-day period between the official release on the Google Play Store [7] and the estimated build time of the malicious sample.
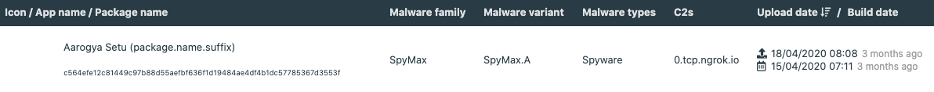
Figure 1 – Image of the ThreatFabric sandbox identifying the estimated build time for a malicious sample disguised as the official Indian contact tracing application
Third party tooling used to provide C2 anonymization
Malicious actors used third party tooling to provide anonymization to their command and control (C2) infrastructure. India was targeted with eight malicious applications that used Portmap.io and Ngrok. Portmap.io[8] is a commercially available port forwarding service, and Ngrok[9] is a secure tunnelling service.
Malicious Android packages distributed through phishing links
Malicious contact tracing applications were distributed through phishing links designed to trick users into downloading a malicious Android package. One sample was disguised as the official contact tracing application for India. The sample, identified by MalwareHunterTeam [10] was distributed through the phishing link, ‘http://prettysavantwholesale[.]com/Aarogya-Setu-v1.5[.]apk’. Distribution of malicious Android packages disguised as legitimate contact tracing applications is consistent across regions. The official Canadian contact tracing application was targeted with ransomware, which was distributed through two phishing links designed to trick the user into downloading the CryCryptor ransomware, according to ESET [11].
Investigation findings are consistent with previous open source reporting
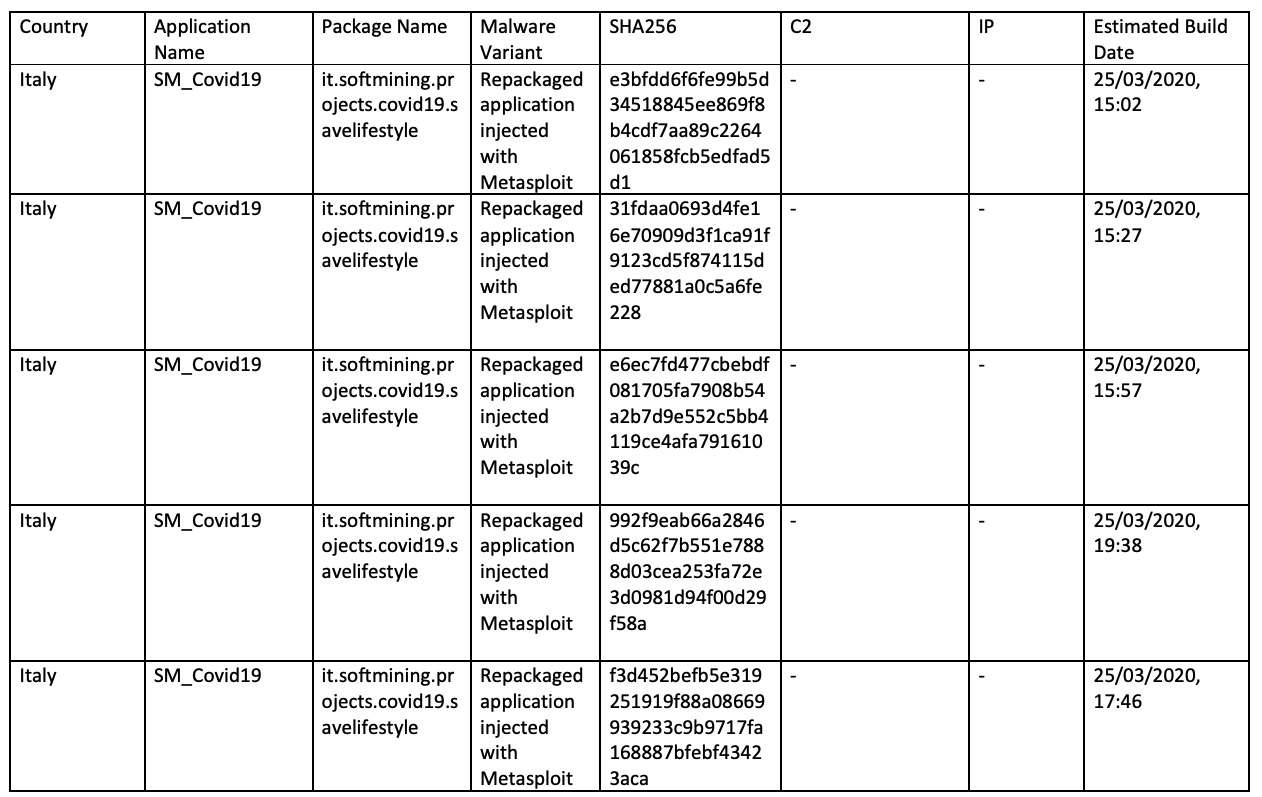
The use of commodity and open source-based malware disguised as benign contact tracing applications is consistent with previous open source reporting. Legitimate SM_Covid19 applications were repackaged and injected with Metasploit giving the identified samples remote access trojan capabilities, according to researchers at Symantec [12], and three SpyNote samples were found to be disguised as the contract tracing application for India.
A publicly reported sample disguised as the contact tracing application for Singapore was identified by EclecticIQ and ThreatFabric as the commodity Android banking trojan Alien.
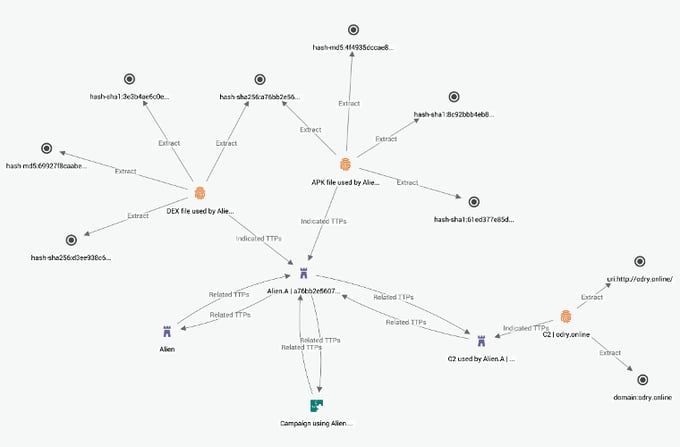
Figure 2 – Image of ThreatFabric enriched Alien.A sample disguised as the official contact tracing application for Singapore on the EclecticIQ Threat Intelligence Platform
Malicious Android packages distributed for financial gain
Cybercriminals used openly available malware and tools to repackage malicious contact tracing applications for financial gain. The Canadian contract tracing application was targeted with an open source-based ransomware named CryCryptor, according to researchers at ESET [13]. A SpyNote [14] variant disguised as the official Indian contact tracing application shared command and control infrastructure with an Aymyth [15] sample posing as a legitimate process manager application. The shared command and control infrastructure showed related repackaged spyware being distributed as unrelated applications that appear to have no overlap in target demographic. EclecticIQ and ThreatFabric assess with high confidence that the majority of contact tracing attacks are financially motivated.
Threat actors will continue to push malicious Android packages as benign contract tracing applications for financial gain
Threat actors will almost certainly continue to use commodity and open source-based malware disguised as legitimate contact tracing applications for financial gain. Malicious actors have shown their willingness to target contact tracing applications consistently for over two months. The 12th April 2020 is the earliest estimated build time identified by EclecticIQ and ThreatFabric researchers, with June 23rd, 2020 the latest identified sample targeting a contact tracing application. Countries need and plan to implement contact tracing applications due to the continued increase in COVID-19 infections [16]. Threat actors are aware of this and will continue to use low barrier to entry tools to target contact tracing applications into the near future.
Users should download contract tracing applications from official stores
Users should only download contact tracing applications from the official Google Play Store or the official website stated by their government. Users should avoid clicking links distributed through messaging services or social media sites to avoid websites hosting malicious contact tracing applications.
References
[1] https://www.nytimes.com/2020/06/16/world/europe/contact-tracing-apps-europe-coronavirus.html[3] https://cracked.to/Thread-Supreme-SpyMax-v2-0-Android-RAT-Updated
[4] https://unit42.paloaltonetworks.com/unit42-spynote-android-trojan-builder-leaked/
[5] https://github.com/AhMyth/AhMyth-Android-RAT
[7] https://www.appbrain.com/app/aarogya-setu/nic.goi.aarogyasetu
[10] https://twitter.com/malwrhunterteam/status/1260892816307367937
[16] https://www.ecdc.europa.eu/en/geographical-distribution-2019-ncov-cases
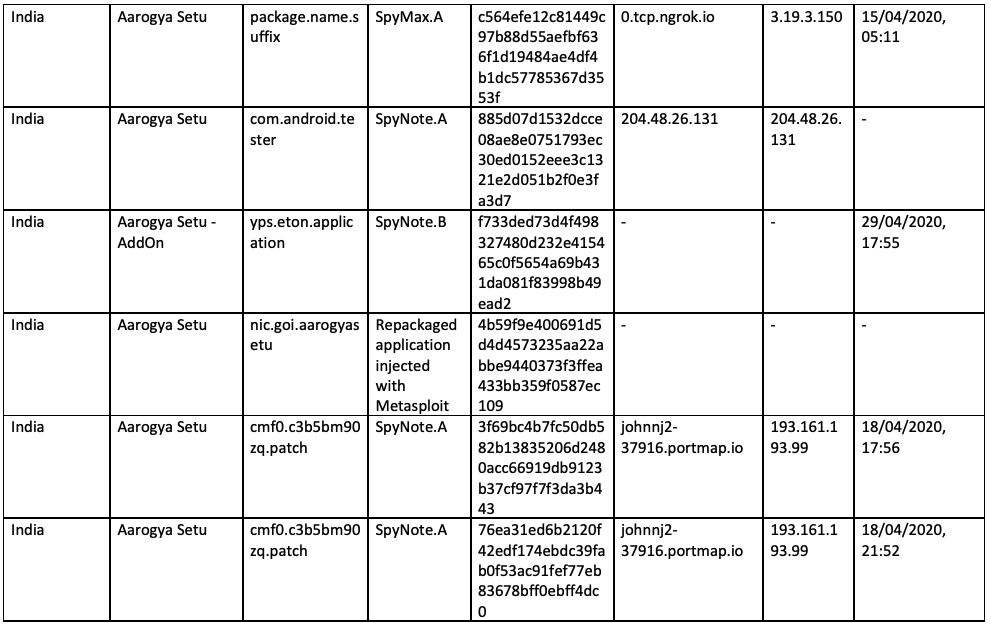
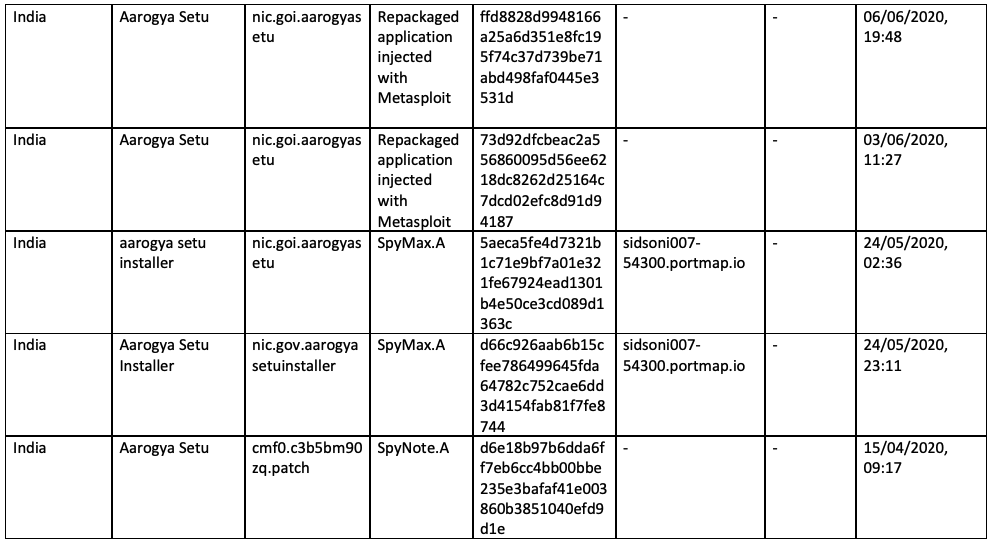
Appendix A - Samples
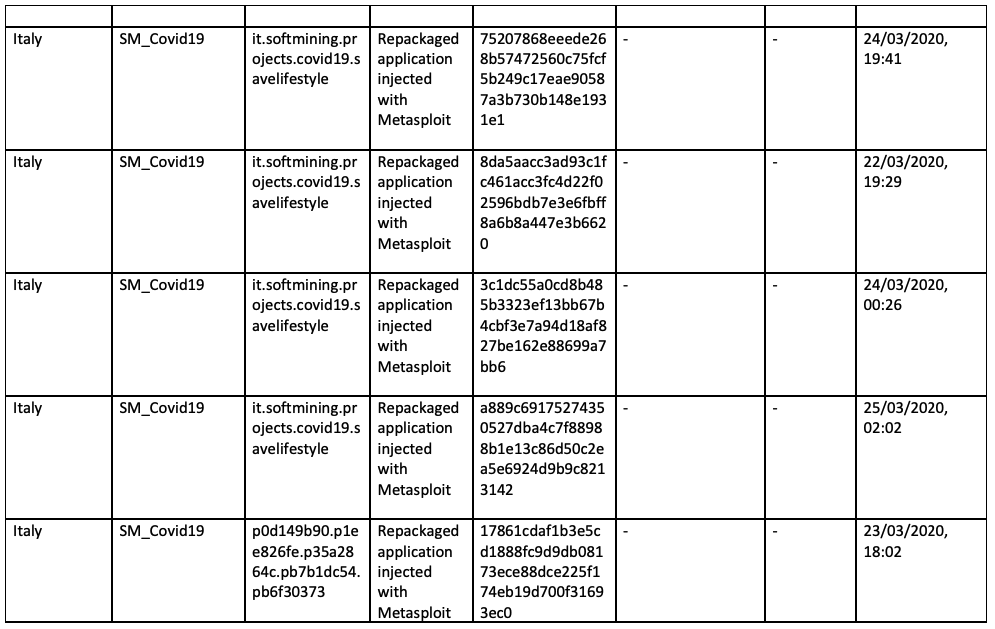
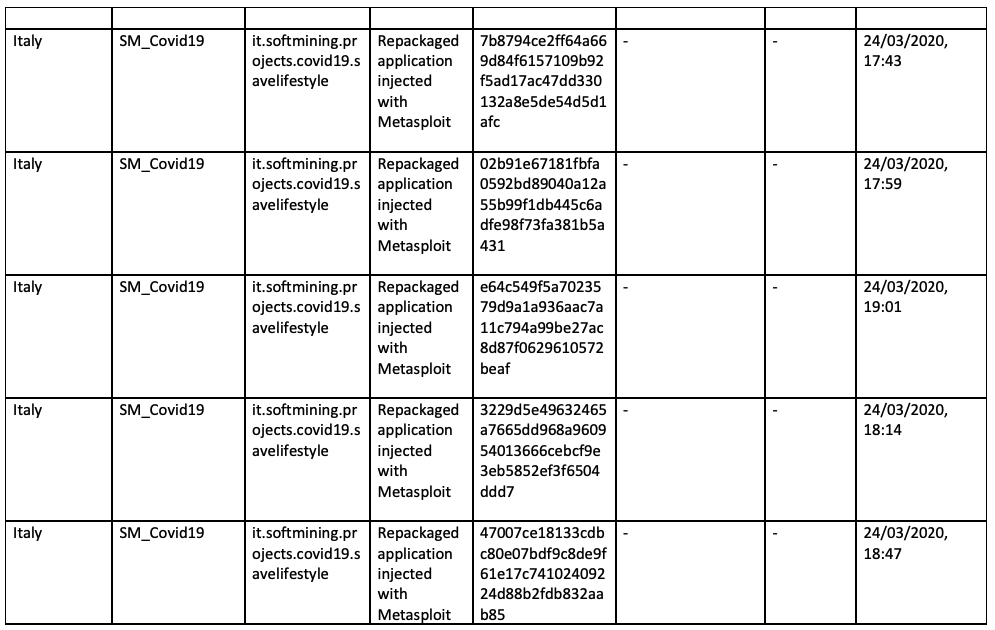
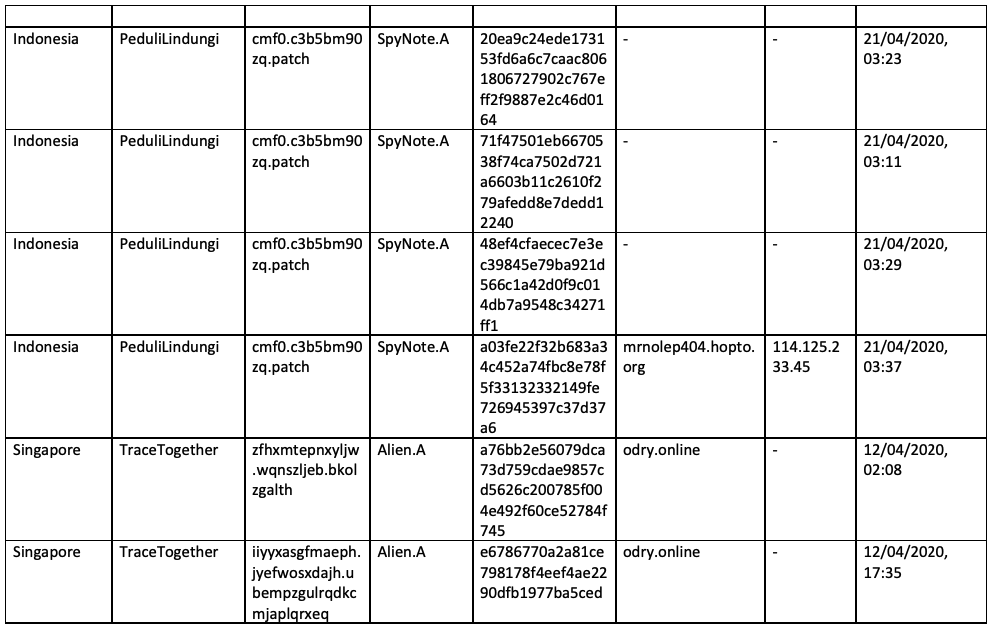
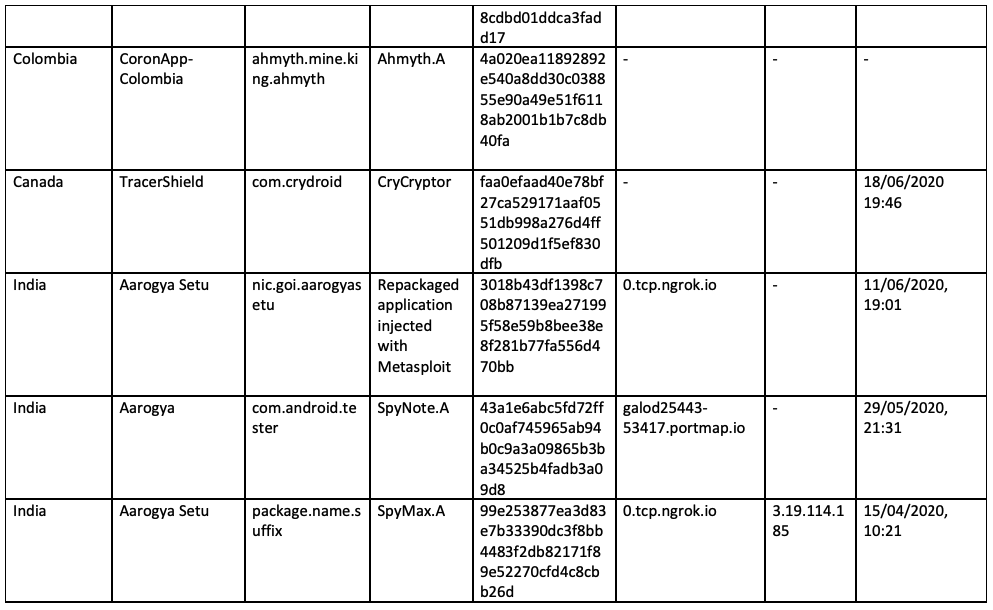
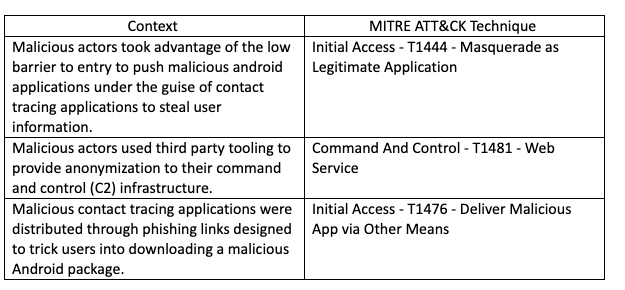
Appendix B - MITRE Techniques
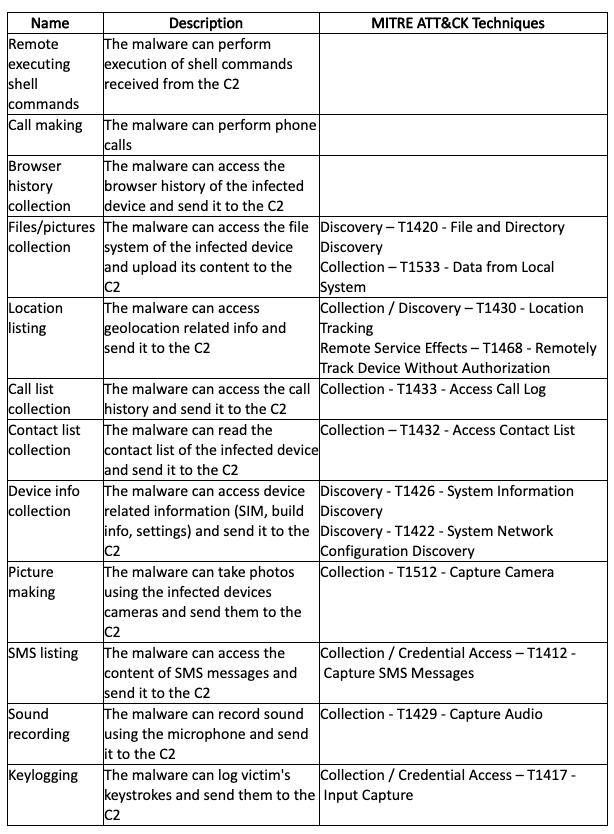
Appendix C - SpyNote.A Capabilities
Appendix D - SpyMax.A Capabilities
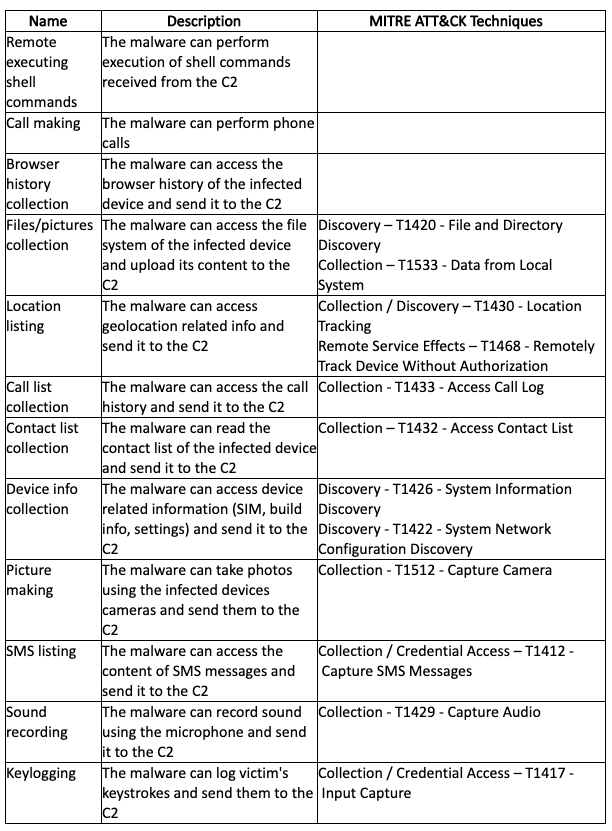
Appendix E - Ahymyth.A Capabilities
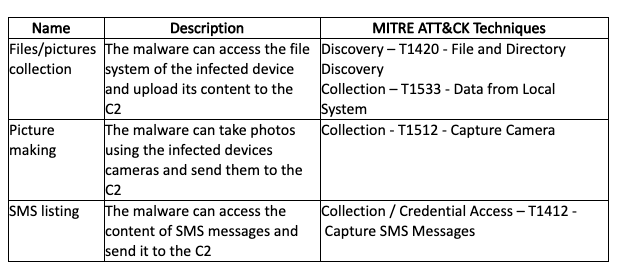
Appendix F - Alien.ACapabilities
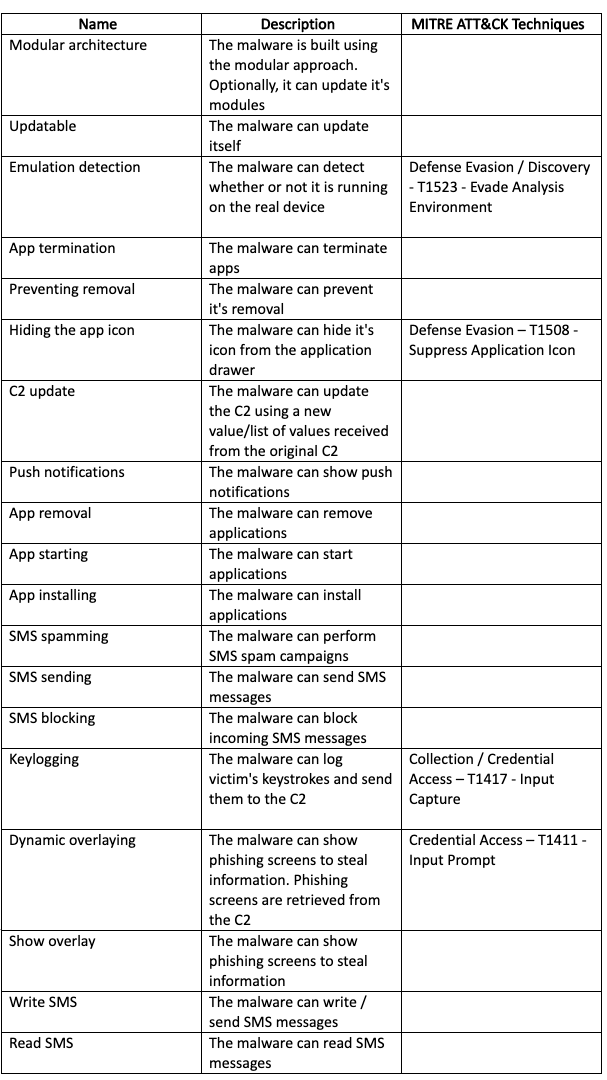
Appendix G - CryCryptor Capabilities
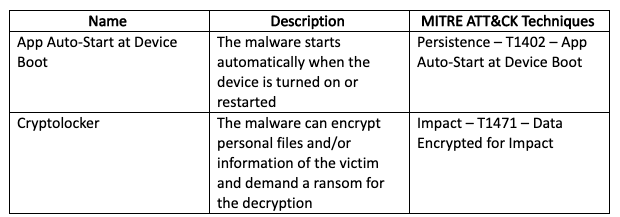
Appendix H - Metasploit Injection Capabilities