 As Europe’s leading cyber threat intelligence company, we at EclecticIQ have decided to make use of our resources and provide the community with custom reports on threats connected to the COVID-19 pandemic throughout the duration of the crisis. This is the 21st report in a weekly series of updates to inform of important developments to COVID-19-themed attacks.
As Europe’s leading cyber threat intelligence company, we at EclecticIQ have decided to make use of our resources and provide the community with custom reports on threats connected to the COVID-19 pandemic throughout the duration of the crisis. This is the 21st report in a weekly series of updates to inform of important developments to COVID-19-themed attacks.
Key Findings
- It is possible the recent Twitter hack was abetted by remote work environments tied to the Pandemic.
- Ecommerce fraud expands to a wider variety of items.
- Google and Amazon represent the largest portion of brand-spoofing in Q2 phishing attacks.
- The pandemic is stimulating increased participation in hacking forums boosting cyberattack volume.
Analysis
Risk From Attacks Against Remote Work Environments Remains High During The Pandemic.
The recent Twitter attack was likely aided, in part by, remote work environments induced by COVID-19 workplace changes. A possible component of the attack, as reported by Disruptive Labs, may have included threat actors’ ability to target Twitter employees with privileged access via their mobile phones. The unverified report from Disruptive Labs details the threat actors, “recognizing the nature of remote working, were able to, through reconnaissance, learn the cell phone numbers of the employees they were targeting. This, coupled with the other personal information they were able to obtain, allowed them to take advantage of lowered situational awareness due to remote work”. The threat actors may have also exploited remote work environments by directing Twitter employees to spoofed VPN (Virtual Private Network) portals where they could capture high-privilege credentials, including 2FA, to the administrator network. The report fails to address how the threat actors were able to pivot from VPN access to the Twitter Administrator panel.
Risk to Ecommerce Fraud Now Involves A Greater Range of Goods.
It is very likely that extended isolation of individuals drives increased e-commerce demand, since physical locations are restricted and economic conditions are causing people to look for cheaper goods online. A new FBI alert warns that social media as well as popular search engines are being used to advertise goods that, once paid for, never arrive. Most of the related attack patterns leverage recently registered (< 6 months), top-level domains (TLD) “.club” and “.top”, selling cheaper than typical goods of wide variety. Victims consistently report never receiving what they attempted to order. The TTPs described in the alert are of low-sophistication and only target money, not credentials or other personally identifying information (PII).
This represents an expansion in fraud activity to encompass general goods that are not necessarily pandemic specific. This escalation in fraud comes on the heels of earlier alerts to medical equipment fraud which used pandemic-specific TTPs. It is likely that this expanding fraud activity, away from strict COVID-19 themes, signals threat actor activity settling into a more normalized cadence relative to high-volume, short-term attack trends observed earlier in the pandemic.
Malicious Redirects Most Often Impersonate Google and Amazon Web Services.
Google and Amazon web infrastructure services are the most spoofed in cybercriminal attacks according to data research from Checkpoint. This does not represent a significant change in Exploitation and Delivery TTPs from earlier in the pandemic; technology companies were targeted the most via spoofing using similar TTPs (Tactics, Techniques, and Procedures). The changes reported by Checkpoint likely represent cybercriminals adapting TTPs to wider audiences. It is highly likely that some of the fraud activity described in the FBI alert (above) is linked to the shifting TTPs now involving brand-spoofing.
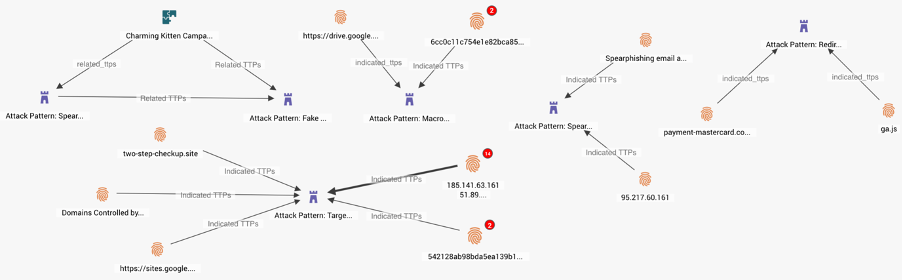
Examples of STIX TTPs and related Indicators representing recent brand spoofing attacks.
The Pandemic Is Stimulating An Increase In Participation Of Hacking Forums, Increasing The Risk From Cyberattacks.
A study of marketplaces on Hack Forums by Cambridge University has concluded that the pandemic has stimulated “a rapid climb in the number and value of contracts completed”. Contracts can involve a number of illicit hacking services to exploit systems and people or expose data. Threat actors involved are typically and relatively unskilled cybercriminals looking for easy opportunity. However, the rising sophistication of Malware-as-a-Service (MaaS) greatly increases their attack capability. The types of activities discussed on these forums has not changed as a result of the pandemic environment.


