 As Europe’s leading cyber threat intelligence company, we at EclecticIQ have decided to make use of our resources and provide the community with custom reports on threats connected to the COVID-19 pandemic throughout the duration of the crisis. This is the 20th report in a weekly series of updates to inform of important developments to COVID-19-themed attacks.
As Europe’s leading cyber threat intelligence company, we at EclecticIQ have decided to make use of our resources and provide the community with custom reports on threats connected to the COVID-19 pandemic throughout the duration of the crisis. This is the 20th report in a weekly series of updates to inform of important developments to COVID-19-themed attacks.
Key Findings:
- Netwalker ransomware operations engage organizations globally bringing increased risk to many verticals.
- Evidence from high-volume attacks demonstrate COVID-19 lures are well established in a growing number of malware families.
- Government assistance programs for business face high risk of business ID-theft.
Netwalker Ransomware Spreads Globally Indicating A High Volume Of Operations And Large Risk To Many Industries
Ransomware is of special concern to business operations that are already struggling with resources due to the pandemic - Ransomware further reduces business resources. The FBI released an alert this week to distributed Netwalker ransomware attacks covering many industries. Healthcare, Education, and Government entities are among the list of potential targets. The attacks are highly likely to use spearphishing with COVID-19 lures, or exploit unpatched Virtual Private Network appliances (CVE-2019-11510 or CVE-2019-18935).
Well-Established Malware Families Use COVID-19 Themed Lures Affecting Almost Every Vertical
Risk to COVID-19 themed phishing is proliferating and diversifying. Malware designed to establish initial access are increasingly weaponizing pandemic current events in phishing lures with success. Families including Asteroth, Emotet, Lokibot, NANOCoreRAT, PoeRAT, and Trickbot have utilized COVID-19 themed phishing lures to gain entry to networks in widespread attacks across the globe. A report from Cisco highlights how widespread this type of spearphishing has become. The malware families are all under active development, creating new modules and adapting new TTPs to their victims and lures. Many different threat actor groups are operating COVID-19 themed phishing attacks around changing current events.
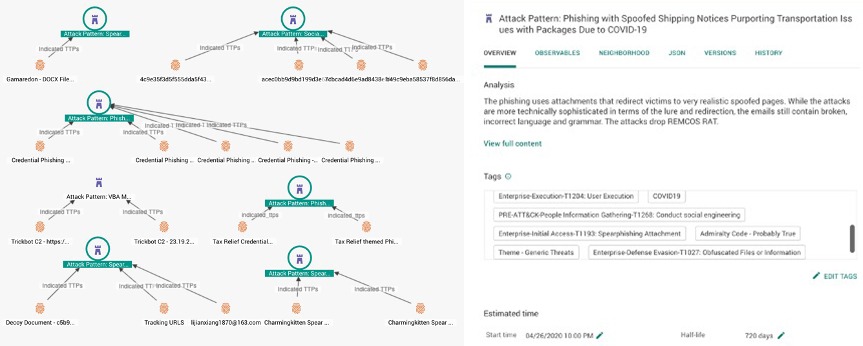
COVID-19-themed lure samples, represented by IOCs and their associated Attack Patterns mapped to MITRE ATT&CK.
Businesses and Government Assistance Face High Risk Of Fraud From ID-Theft During The Pandemic.
Cybercriminals collect information on active and dormant businesses to then impersonate the organization and claim credit. At least one credit bureau in the US estimates business ID fraud will increase in 2020 by over 250%. The increase is largely driven by pandemic effects on small to medium businesses. Business ID theft provides threat actors with more credit lines than that associated with personal ID theft. Risk increases further to entities that have part of their business infrastructure compromised by attackers as this makes impersonation easier.
It is probable that the increased incentive for medical record compromise, highlighted in the last weekly update, will further impact business ID theft. Medical records often provide for a central location containing a plethora of personally identifiable information (PII), making it easier for threat actors to find the information they need on business owners, managers, etc. using far fewer documents.


