 As Europe’s leading cyber threat intelligence company, we at EclecticIQ have decided to make use of our resources and provide the community with custom reports on threats connected to the COVID-19 pandemic throughout the duration of the crisis.This is the thirteenth report in a weekly series of updates to inform of important developments to COVID-19-themed attacks.
As Europe’s leading cyber threat intelligence company, we at EclecticIQ have decided to make use of our resources and provide the community with custom reports on threats connected to the COVID-19 pandemic throughout the duration of the crisis.This is the thirteenth report in a weekly series of updates to inform of important developments to COVID-19-themed attacks.
Key Findings
- A recent attack demonstrates increased risk to COVID-19 related supply chains.
- Attack momentum is building against COVID-19 related mobile apps.
- The most significant risk to mobile will almost certainly come from Android apps masquerading as trusted apps inside legitimate marketplaces that drop Remote Access Trojans.
- The European Commission has criticized China and Russia regarding separate coordinated global disinformation efforts.
Analysis
Risk to COVID-19 Supply Chains
A task force in Germany comprised of major companies responsible for procuring COVID-19 supplies has been the focus of recent attacks targeting the email credentials of over 100 executives. The task force first convened on March 30, 2020 and preliminary threat actor activities were detected the same day. The activity detected involved domain registrations that mimicked the infrastructure of some of the companies involved in the task force.
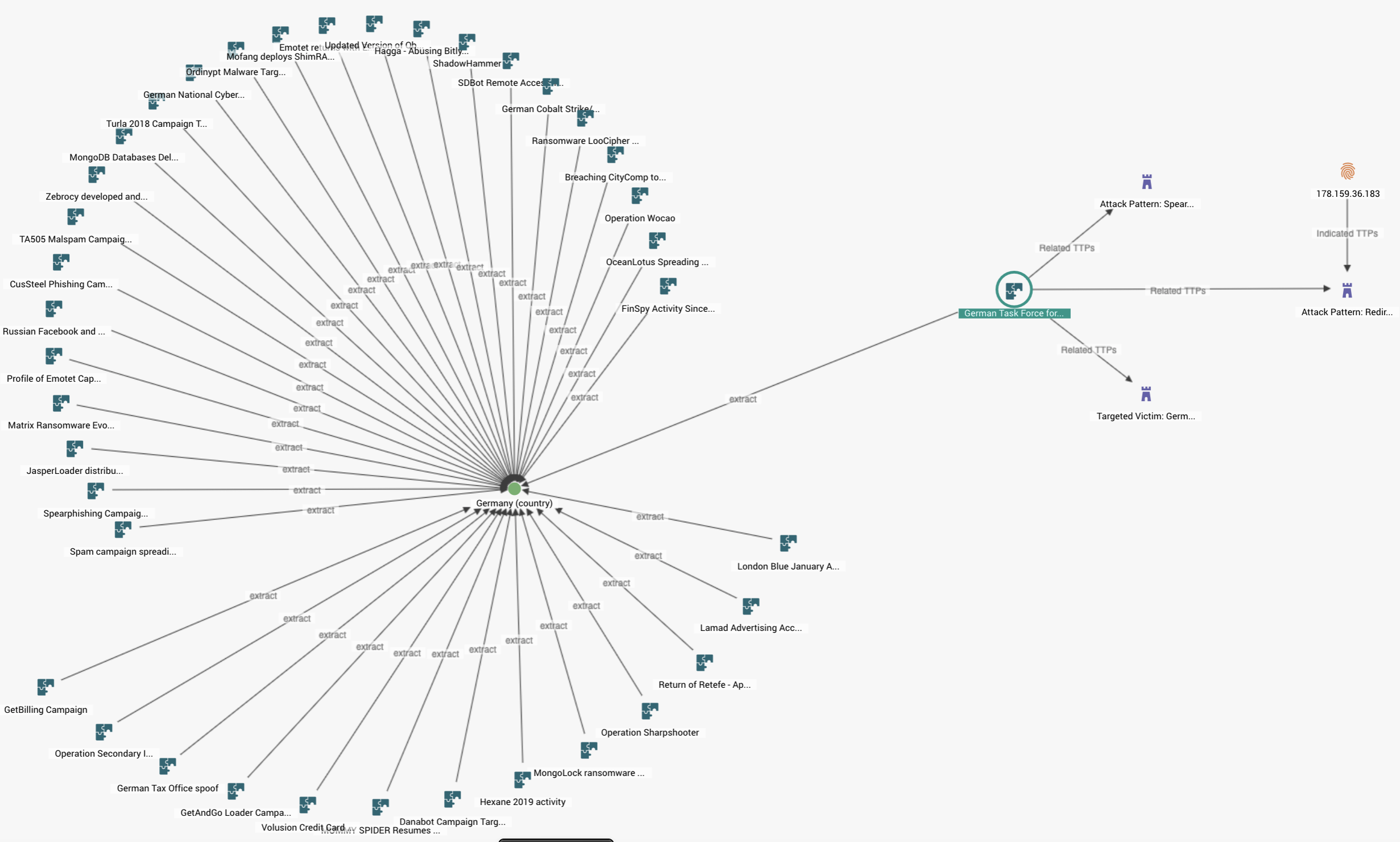 Graph in EclecticIQ Platform depicting recent attack on German-COVID task force
Graph in EclecticIQ Platform depicting recent attack on German-COVID task force
The graph above represents current threat actor actions observed against the German task force, as well as historical campaigns. Structured threat intelligence allows analysts to quickly pivot across different attacks relating to a particular target, analyzing historical attack patterns while simultaneously tracking and mapping new attack intelligence, providing valuable context for a more effective defense posture.
The credential targeting activity very likely represents an initial effort to gain persistence into the organization for the purpose of gaining a competitive advantage. Economic espionage could be used to out-bid competition. The TTPs (Tactics, Techniques, and Procedures) described could also serve as pretext for a BEC (Business Email Compromise). Germany is largest economy in Europe and the multinational companies involved represent potentially some of the highest-value targets. COVID-19 related supply chains will likely experience increased risk from cyberattacks as nations look to secure medical supplies ahead of a possible ‘next wave’ of infections.
In our preliminary investigation into COVID-19 themed attacks, EclecticIQ analysts discovered phishing lures with strong COVID-19 themes tailored to shipping and manufacturing companies in the form of updated invoices or notifications of infrastructure impact from the pandemic. The newer activity is highly targeted and represents a marked escalation from this earlier activity, which was more generalized and distributed.
Risk from COVID-19 Apps Continue Increasing Significantly.
In our weekly update provided the final week of April 2020 EclecticIQ threat intelligence analysts predicted rising risk to mobile apps as various COVID-19 related apps were being developed. The most significant risk to mobile will come from Android apps masquerading as trusted apps inside legitimate marketplaces that drop Remote Access Trojans (RATs). If threat actors can upload malicious software to app marketplaces, then large amounts of people are more likely to be exploited by these TTPs. RATs enable significant penetration of mobile devices, providing threat actors with privileged access to sensitive personal information, such as location, that could, in turn, expose victims to physical risk. Android is a major mobile operating system that is attractive to threat actors because of the larger pool of victims. The attacks are being supported by an increasing attack surface, partly driven by expanded app functionality. The South Korean app uses special QR codes. The increased functionality provides threat actors with more avenues to exploit, resulting in new TTPs and attack patterns that could possibly affect large swaths of State populations. So far, the TPPs described in reports such as the one above, are being carried out by cybercriminals with the goal of fraud for financial gain.
Another factor driving mobile attack risk is the volume of apps that are being published. More apps imply more potential victims that could be exploited with a single malicious app. This type of environment is more attractive to threat actors because it increases the likelihood of successful compromise. Check Point discovered 16 different apps employing a variety of payloads that included premium dialers, adware, and mobile RATs.
MIT has committed a comprehensive program that aims to track privacy risk indicators and the full report can be accessed here. Top ranking countries include mostly those adopting open and transparent frameworks. The worst ranking countries all include those adopting an in-house, centralized model, and orbiting less democratic spheres of government. Two notable inclusions on the worst ranking list are France -using its own centralized app ,and Ireland -ranking poorly despite adopting the Apple/Google tracking framework.
The privacy score is correlated to risk from the user perspective. High privacy scores represent more known risks; The software architecture and data policies account for more of the data more of the time. Known risks can be better modelled and therefore better anticipated. A low privacy score represents more unknown risk; The software architecture and data policies are not always clear with respect to data stewardship and therefore, less is known about potential risks from attack. Unknown risks cannot be anticipated or guarded against as well. A mostly up to date list of all countries with tracing apps can be found here. Individuals should orient themselves to data policies (or lack thereof) in their country so they can make the best decisions to mitigate potential personal risk that may arise when they generate data using the apps.
Outside of the countries described in the MIT initiative, open source projects are another good option for preserving privacy and data integrity. States opting for an open-source COVID-19 app-model that better preserves privacy, includes the Czech Republic, Israel, Morocco, and one app (of many) offered in India. The Apple/Google model also holds up well and is portable to many platforms. States opting for the Apple/Google framework currently, are largely aligned with the Western geopolitical sphere; comprising most of Europe, Canada, and the US. Malaysia is included as well.
BIAS Exploits Affect Tracing Apps and Remain Unpatched
BIAS exploits still remain a significant risk to any app using Bluetooth to generate COVID-19 tracking data. Currently there is still no patch since publication of the discovery near the end of May 2020. The Bluetooth SIG has released an official statement earlier in June regarding a future update to the core specification that specifically guards against BIAS exploitation by increasing authentication requirements and hardening the standard against downgrade attacks. There is currently no specified or forecast date for any patch or update. A comprehensive summary of the BIAS vulnerabilities are described in this updated release.
Misinformation Warning by the European Commission
China and Russia were highlighted recently by the European Commission for running “targeted influence operations and disinformation campaigns in the EU, its neighborhood, and globally. The Guardian reports this announcement as likely tied to Geopolitical signalling against Beijing. They also note that the TikTok software platform has signed onto a voluntary agreement along with other social media giants to combat disinformation. TikTok has a strategic partnership with Chinese supported organizations. The full publication from the EU highlights more than State efforts. Its focus includes, but is not limited to, hate-speech, cybercrime, cyberfraud, and the spread of inaccurate information.
Reporting of influence operations and disinformation in Europe were first highlighted in our update from the 3rd week of April 2020. The newer reproach very likely indicates that TTPs have evolved and intensified further from what was initially described in our earlier update.


