 As Europe’s leading cyber threat intelligence company, we at EclecticIQ have decided to make use of our resources and provide the community with custom reports on threats connected to the COVID-19 pandemic throughout the duration of the crisis.
As Europe’s leading cyber threat intelligence company, we at EclecticIQ have decided to make use of our resources and provide the community with custom reports on threats connected to the COVID-19 pandemic throughout the duration of the crisis.
This is the twelfth report in a weekly series of updates to inform of important developments to COVID-19-themed attacks.
Key Findings
- Multiple reports indicate attack volume is decreasing from peak activity since the start of the pandemic.
- Threats to the workforce are changing as lockdowns ends.
- Pre-pandemic risks are likely to retake center-stage.
Analysis
Data Indicates Threat Actors Are Launching Attacks in Less Volume
Pandemic related lockdown, in many places, is starting to deescalate. Threats are very likely to shift back to similar patterns prior to the pandemic. Checkpoint data suggests that attacks from high-volume attacks are currently increasing in the short term, as employees return to more normal working conditions. The data from Checkpoint and other data trends indicate that overall attack volume is still decreasing in a larger downward trend, relative to peak activity since the start of the pandemic.
Peak attack volume featuring commodity malware occurred approximately across mid-March to early May. Threat Coalition data also supports this peak-range. Checkpoint’s data shows that in the last week, 2.5% of newly registered domains expressing COVID-19 themes were malicious and an additional 16% of the total were “suspicious”. The ratio of malicious COVID-19 themed domains appears to be sliding below rates observed earlier that were closer to 12%. Domain measurement provides a limited window into the most common and highest volume attacks.
New TTPs (Tactics, Techniques, and Procedures)
The same Checkpoint report highlights that threat actors are keying into further opportunities presented by the transition of employees back to more normal working environments. Threat actors are using medical-leave and job opportunity lures in campaigns. The lures do not employ special TTPs (Techniques, Tactics, and Procedures), but are designed to cast a wide net and take advantage of people who are newly looking for work. Unemployment is higher in many countries now. Other people are looking for a method to continue their remote work opportunity.
A vulnerability, CVE-2020-6110, was recently disclosed publicly regarding Zoom clients. Since at least the middle of April the vulnerability allowed threat actors to inject arbitrary executable files via Zoom clients to achieve remote code execution. The vulnerability is relatively easy to exploit and requires minimal tooling. The vulnerability was patched in Zoom version 4.6.12 and is not reproducible in 5.0.1, released on April, 30th.
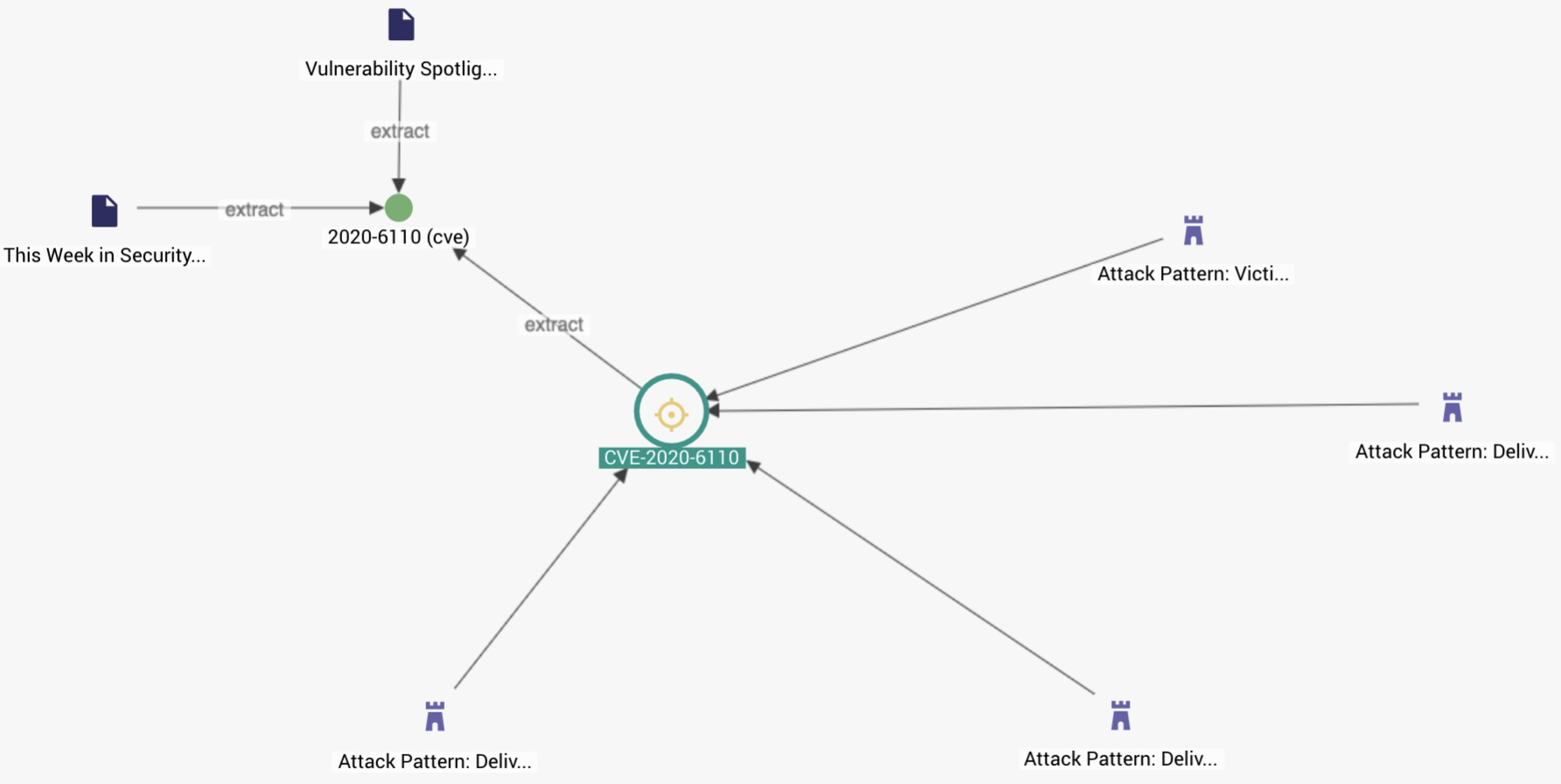 The graph above demonstrates the attack patterns described so far for this vulnerability. Threat intelligence enables organizations to track how attack patterns (TTPs) may change with time across a vulnerability.
The graph above demonstrates the attack patterns described so far for this vulnerability. Threat intelligence enables organizations to track how attack patterns (TTPs) may change with time across a vulnerability.
Another new attack reported to be effective involves the use of attaching voicemails to enterprise emails. Threat actors spoof the sender and file names to deceive security controls and end-users. The attacks are only effective against companies with existing PBX deployments that automatically incorporate voicemails into emails. They are aimed at compromising credentials using different command and control landing pages that victims are directed to. The attacks can be easily adapted to many companies and victims.
Long-term Risks Are Unlikely to Change From the Pandemic
After the transition away from the working environment induced by the pandemic the Information Security Forum (ISF) expects threats to remain unchanged from what was highlighted in their 2020 report - published before the pandemic began. The pandemic has failed to produce enduring TTPs and EclecticIQ analysts have not observed TTPs that have a lasting impact on threat actor operations. The full risk report from the ISF can be downloaded here. The Information Security Forum is a widely respected independent global community established in 1989 and focused on knowledge exchange.


