 As Europe’s leading cyber threat intelligence company, we at EclecticIQ have decided to make use of our resources and provide the community with custom reports on threats connected to the COVID-19 pandemic throughout the duration of the crisis.
As Europe’s leading cyber threat intelligence company, we at EclecticIQ have decided to make use of our resources and provide the community with custom reports on threats connected to the COVID-19 pandemic throughout the duration of the crisis.
This is the ninth report in a weekly series of updates to inform of important developments to COVID-19-themed attacks.
Key Findings
- APT attacks against COVID-19 research is currently well-established.
- Ransomware remains the highest risk to healthcare.
- High-volume attacks from cybercriminals weaponize new lure material to remain effective but rely heavily on repeat TTPs for malware delivery.
Analysis
APT Groups Establish Attacks Against Organizations Participating in COVID-19 Research.
The United States (US) issued an escalated alert to COVID-19 vaccine research participants . The alert singles out China as the primary aggressor. The alert aligns to past public reporting that covers rising tensions between the US and China regarding the pandemic. Companies participating in COVID-19 vaccine research and technologies should be on high alert for APT activity. Initial breach and intrusion are most likely to be delivered via spearphishing.
Reuters reported an APT group purportedly tied to Iran targeted Gilead Sciences Inc, a US company working on COVID-19 treatment. There is no confirmation of breach. The attack was delivered via spearphishing to “compromise email accounts of staff at the company using messages that impersonated journalists.” Spoofing of media makes the lure enticing, but less alarming to recipients. It likely blends in with similar legitimate press requests that would be expected soliciting hospitals.
A report by Check Point provides a good example of what further Exploitation and Installation Kill-Chain phases might look like if an APT group attacked a vaccine company. Check Point detailed a sophisticated backdoor, “Aria-Body” that is purportedly used by China to attack State-level organizations.
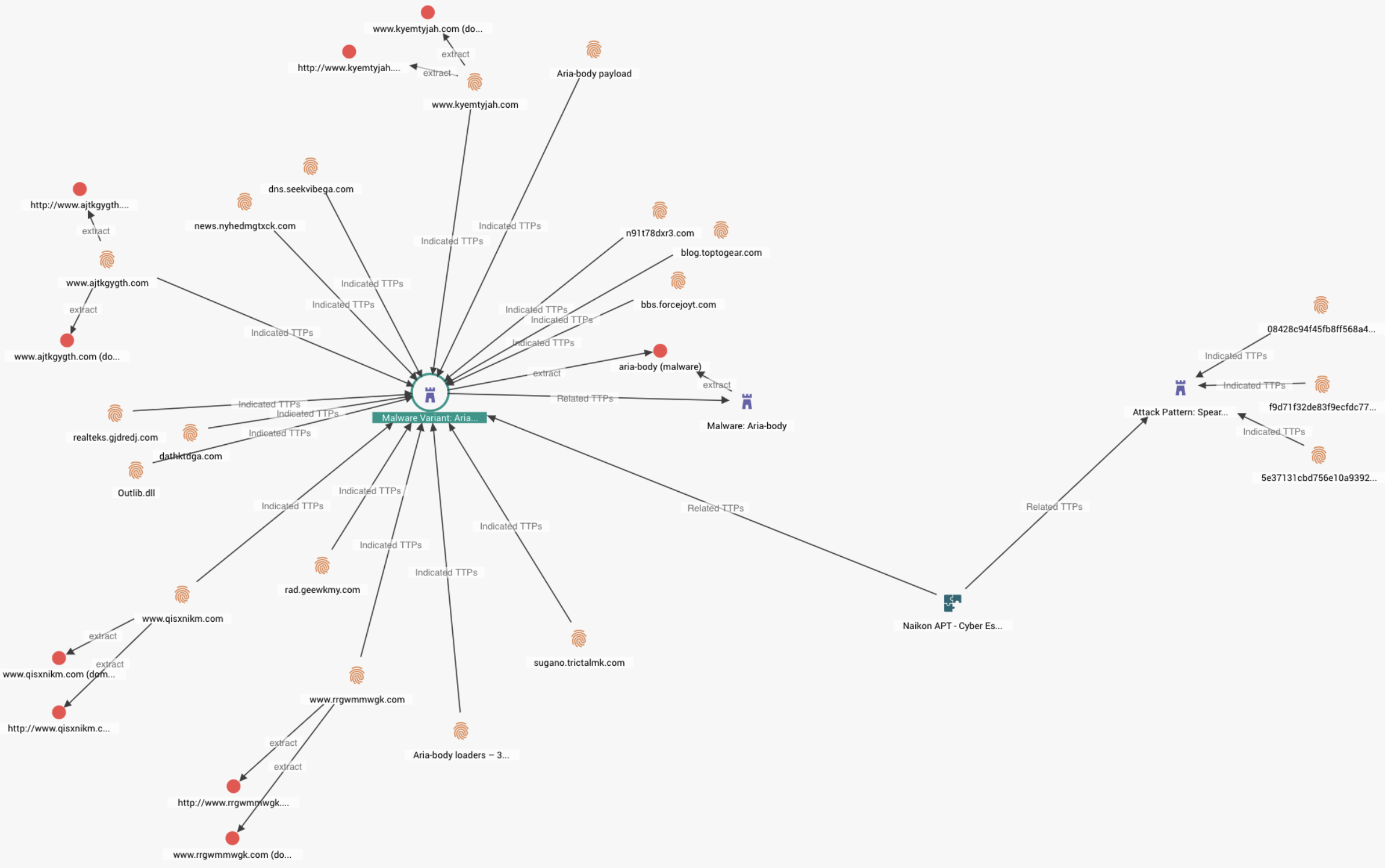 Screenshot from EclecticIQ Platform, displaying the "Aria-Body" APT malware attacking Govs in South-East Asia
Screenshot from EclecticIQ Platform, displaying the "Aria-Body" APT malware attacking Govs in South-East Asia
The malware is delivered via spearphishing, includes multiple modular capabilities for data harvesting, and uses X-OR obfuscation for C2 (Command and Control infrastructure) communications. The C2 is highly dynamic and changes frequently. This type of malware is much more difficult to detect and track than malware described in early mass-spam operations by cybercriminals. The Check Point report did not detail COVID-19-themed attacks.
Based on a pattern of similar alerts, along with proprietary research by EclecticIQ analysts, APT attacks on companies participating in COVID-19 research are now well-established. Our earlier weekly update at the end of March first alerted to this APT activity. Attacks against vaccines and treatment research remain persistent in search of strategic proprietary healthcare information related to COVID19. This information may provide States with medical technology that gives them a competitive global edge in recovering from the effects of the pandemic as well as economic advantages.
Three possible areas to begin hunting for APT activities and intrusions could include:
- Email logs. Audit the email server and look for incoming email with attachments and email addresses with typosquatting domains that may spoof primary domains or third-party domains. Attachments may result in unauthorized modification to host environment configurations, such as unusual system calls, unusual traffic from system accounts, or registry modifications.
- Network traffic logs. Look for connections to unknown IP addresses. This can be combined with timelines from email logs to gain further insight into possible spearphishing links. Network traffic logs can also be combined with specific host logs to gain a bigger picture of the attack pattern. Monitor for unusual amounts of traffic leaving the network and look for unusual spikes in activity outside of expected times. Correlate network traffic logs with account authorization and look for sign-ins from unexpected locations.
- Audit search histories on hosts with access to sensitive, proprietary information related to COVID-19 medicine development. APTs, once inside the network, will likely search for the information they need, possibly leaving traces in host and application search histories. High-value data is likely restricted to certain systems. Hunting for evidence of search queries related to high-value data can be an effective early alert to possible APT activity inside the network. A good quick reference that further details some of these search artefacts on Windows machines is provided by SANS.
Ransomware Alert to Healthcare Remains High.
Magellan Health Inc., is a large American for-profit managed health care company that recently reported a ransomware attack, where threat actors “gained access to Magellan’s systems after sending a phishing email on April 6 that impersonated a Magellan client.” The variant used has not been reported, pending further investigation. The threat actors are confirmed to have exfiltrated “sensitive personal information” from the company and its personnel. The parent company suffered another ransomware attack on a separate healthcare-related subsidiary in late 2019.
A US-based media organization specializing in Healthcare data security points out that in addition to the big names making ransomware news, there is an abundance of smaller healthcare victims that are also falling to ransomware and go largely unreported. Larger data analysis by Emisoft indicates overall ransomware attacks on the healthcare industry are comparatively and relatively lower now during the pandemic, than compared to similar time ranges outside of the pandemic. The statistics offered in the report indicate that many ransomware operators have intentionally chosen to avoid targeting healthcare in lieu of the pandemic. They measure 25 attacks on Healthcare organizations from January to March 2020. Early media reports from early in the pandemic support this conclusion and statistics.
New Phishing Lures Hide More Recycled Techniques, Tactics, and Procedures (TTPs).
Threat actors continue to demonstrate a high level of TTP recycling in their attacks. These attacks use new lures with heavily reused phishing TTPs to exploit individuals during the pandemic. The reused attacks continue to be successful because they effectively exploit current events that take advantage of information seeking behaviour in victims. Lures exploit curiosity and good lures are able to do this without raising red flags to the user. A scholarly paper published in 2012 highlights these trends in information seeking and phishing that still hold in the pandemic today. It is relatively low-effort for threat actors to build new phishing lures. The technical back-end of these attacks remains almost the same in each case. There are many people attuned to the pandemic that there will always be new victims. It is therefore easy to adapt these attacks to new situations. Security awareness training is key at mitigating phishing TTPs. To date, security appliances have been unable to keep pace with phishing attacks.


