Synopsis
Cybersecurity stole more of the spotlight in 2021 than even in years past as part of a global dialogue spanning from national government headquarters to individual households. This deeper level of penetration arrived with good reason. A series of successful attacks proved highly disruptive for the public and governments unprepared to respond to far-reaching cyber threats. EclecticIQ examined the year in cybersecurity and found this tumultuous year followed the path of existing attack trends yet proved disruptive enough to warrant more and stronger responses than in years prior. Here we discuss three of the most impactful issues to emerge from 2021: highly disruptive attacks, supply chain attacks, and increased public attention to combatting cybercrime and regulating cryptocurrency as a de facto tool of the cybercrime trade.
Cyberattacks Cause Disruptions That Hit Home
For many, 2021 marked the first year in which a cyberattack disrupted daily life. High impact attacks reduced the availability of essential goods or services in countries around the world. Ransomware attacks against Brazil-based meat processing company JBS and Dutch transport company Bakker Logistiek caused shortages in meat and cheese (8, 9), hitting home for millions as signs at supermarkets explained they had run out of supplies due to a cyber incident. An attack against Colonial Pipeline in May (1), the largest refined oil products provider in the U.S., caused a gasoline shortage in the Eastern United States. Miami-based managed service provider (MSP) Kaseya was victim of an attack in July, impacting nearly 1,500 organizations around the world and highlighting the impact of cyber incidents against MSPs tasked with securing client infrastructure (2). These attacks were followed by novel political and diplomatic actions as national governments struggled to respond to increasingly disruptive attacks to industry and public life. U.S. President Biden’s meeting with Russian President Putin in June (3), and the multi-national effort to take down cybercriminal group REvil’s online infrastructure (4) and seize its assets in late September were unprecedented, and clearly demonstrated that cyber is now a top priority for government.
Supply Chain Attacks Extend the Reach of Cyber Attackers and Complicate Response
Another point that stood out this year was the high impact of attacks exploiting high-trust systems (2). While the number of supply chain attacks fell from 2020 to 2021 according to Github (see the graph below), they have an outsized impact due to the nature of hyper-connected business networks and remain a growing critical threat to information assets. Supply chain attacks are often more potent than other attacks and difficult to mitigate for first parties because the originating compromise is outside the organization. They blend in by clandestinely penetrating a strategic point in the chain and deploying malicious code in a way that is propagated downstream automatically, due to the inherent architecture of the specific supply chain. The trust inherent in existing supply chain networks only exacerbates the problem by allowing malicious code to spread undetected.
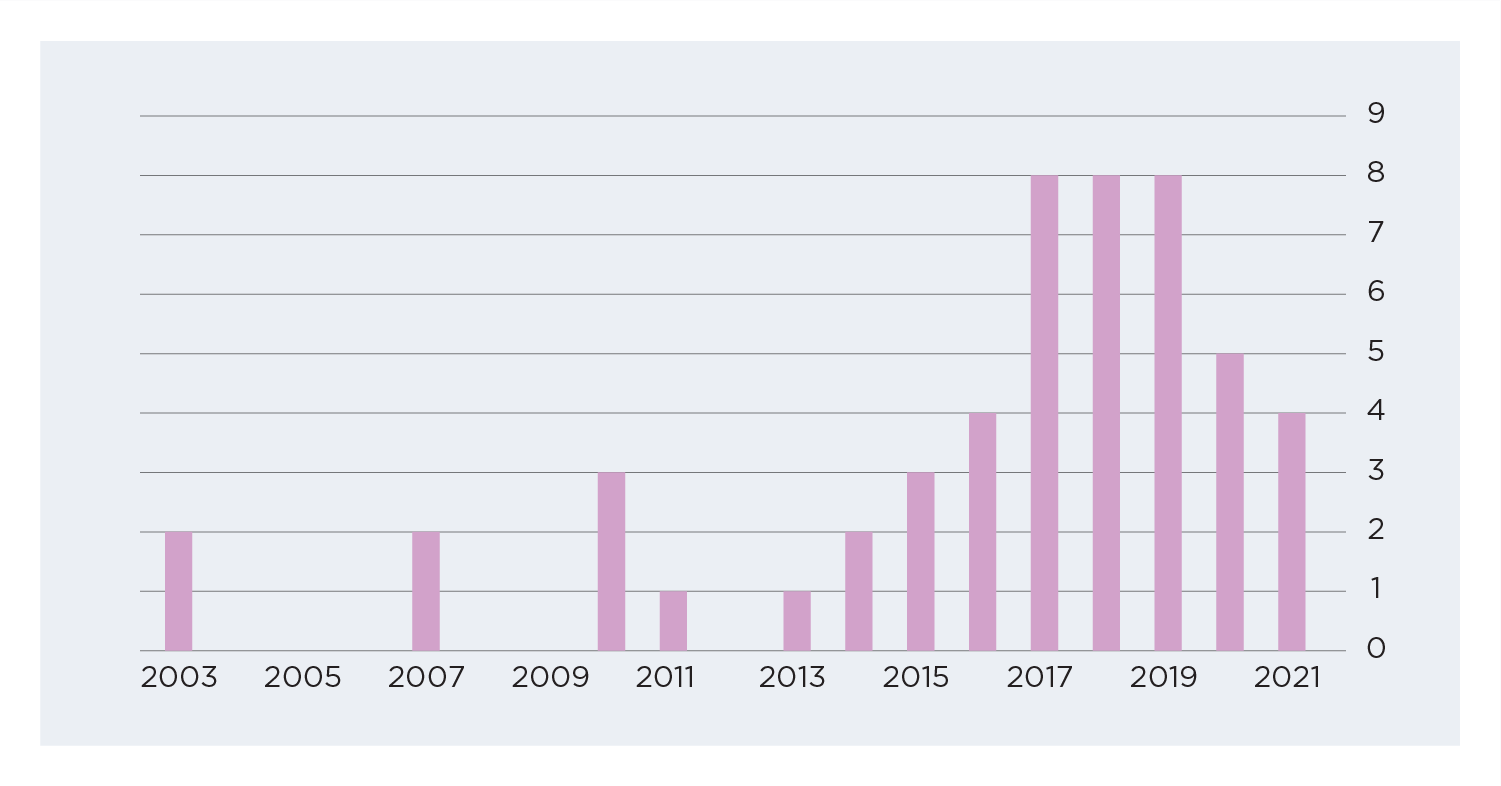
The frequency of supply chain attacks has increased in recent years (Find source).
In this way, adversaries can focus maximum effort carefully crafting individual campaigns against single targets that allow advanced persistent threats (APTs) to move laterally undetected to a greater pool of victims with a higher level of privilege that is most often unquestioned and overlooked by network defenders. The SolarWinds and Kaseya attacks provided important threat intelligence regarding current APT capabilities against cyber supply chains. (Check out our July report on the Kaseya attack here.) In a first, vulnerabilities in the SolarWinds software provided opportunity for multiple APT groups to access to sensitive victim networks across the globe for more than a year.
Governments Take Action, and Cybercriminals Take Notice
With such high impact attacks and an increasingly dynamic threat environment, governments around the world took action to better understand the nature of cyber threats, and how to combat them. Government collaboration successfully took down ransomware infrastructure (12). In response, ransomware-focused cybercriminal groups demonstrated a previously unobserved level of solidarity with each other by encouraging fellow ransomware groups, in online messages, to attack the West (7). Cryptocurrency’s key role in facilitating cybercrime became clear and attracted attention from regulators around the world, prompting examination of how to best regulate crypto (5). China took it one step further and outlawed cryptocurrency activities altogether, claiming they “seriously endanger the safety of people’s assets.” (10) Allegations of privacy and rights violations stemming from covert deployment of NSO Group’s Pegasus spyware will continue in coming months, but so far included the U.S. implementing import/export controls on sensitive technology, lest it fall into the wrong hands, and Apple suing NSO Group (11, 15). (For further details on a few of these issues, check out The Analyst Prompt here and here.)
Conclusion
EclecticIQ assesses the frequency of ransomware attacks shows no sign of slowing for the simple reason that successful attacks are incredibly lucrative and relatively easy for criminals to carry out without repercussions. The government initiatives to make serious cybercrime riskier and less lucrative for criminals are only beginning to coalesce; in the interim the threat of ransomware will accelerate. EclecticIQ expects to see this theme of digital dependence and vulnerabilities due to interconnected networks carry over into the next year. Increasing connectivity creates increasing reliance on technology for production—a trend which has grown over 2021’s remote work phenomenon due to ongoing Covid-19 concerns.
Against this backdrop, supply chain attack TTPs have proven extremely effective and lucrative, and most organizations are not prepared to confront this threat without more comprehensive security programs accounting for third and fourth-party risk. Finding just the right place to insert malicious code will continue to be extremely effective for advanced threat groups, and EclecticIQ expects more threat actors will look to conduct supply chain attacks in the future. Cyber security experts, under the assumption of breach model, must anticipate how APT groups may leverage trusted gateways within their networks. Threat hunting efforts must focus on high-trust systems where vulnerabilities are not expected, systems with high reputation providing trusted access, and those which could be used to access crown-jewels. A posture that assumes compromise and is unbiased will allow threat hunters to detect, respond, and mitigate similar threats in the future.
Outlook
A Secure Future Requires Strong and Collaborative Cyber Defense Today
Progress against cybercrime by governments will likely come in fits and starts. In the short term, cyber insurance may become a more commonplace manner of hedging risk for potential victims, but the tradeoff is the uptick in ransom payouts since 2019 has made cyber insurance more costly to purchase. (13) Cooperative efforts between governments and non-governmental organizations to combat ransomware will demonstrate limited or temporary success as governments work to establish the relationships and procedures needed to swiftly respond to cybercrime both domestically and internationally. Nonetheless, these efforts should be resourced and prioritized to encourage their growth. (14) Successful law enforcement operations targeting cybercrime will help prevent exponential growth, and garner a deeper understanding of threat actors’ attack patterns and how they can be thwarted.
In this ever-evolving threat environment, a solid, intelligence-based cyber defense is as important as ever. Comprehensive cyber defense programs will incorporate up-to-the moment data, streamlined processes, and the expertise of those with the skills to address individual threats at a granular level and drive collaboration across the cyber community.
Appendix:
- https://www.bloomberg.com/news/articles/2021-06-04/hackers-breached-colonial-pipeline-using-compromised-password
- https://www.zdnet.com/article/revil-websites-down-after-governments-pressured-to-take-action-following-kaseya-attack/
- https://www.defenseone.com/technology/2021/07/biden-urges-putin-give-russian-ransomware-gangsters-threatens-unspecified-consequences/183652/
- https://www.washingtonpost.com/national-security/cyber-command-revil-ransomware/2021/11/03/528e03e6-3517-11ec-9bc4-86107e7b0ab1_story.html
- https://www.reuters.com/world/us/us-justice-dept-launches-new-initiatives-cryptocurrencies-contractor-hacks-2021-10-06/
- https://www.commerce.gov/news/press-releases/2021/10/commerce-tightens-export-controls-items-used-surveillance-private
- https://www.bleepingcomputer.com/news/security/groove-ransomware-calls-on-all-extortion-gangs-to-attack-us-interests/
- https://www.bbc.com/news/business-57423008
- https://www.bleepingcomputer.com/news/security/dutch-supermarkets-run-out-of-cheese-after-ransomware-attack/
- https://www.bbc.com/news/technology-58678907
- https://www.amnesty.org/en/latest/research/2021/07/forensic-methodology-report-how-to-catch-nso-groups-pegasus/
- https://www.europol.europa.eu/newsroom/news/five-affiliates-to-sodinokibi/revil-unplugged
- https://www.reuters.com/article/us-ransomware-insurance-idUSKBN1ZL1J2
- https://blog.talosintelligence.com/2021/11/emotet-back-from-the-dead.html
- https://www.apple.com/newsroom/2021/11/apple-sues-nso-group-to-curb-the-abuse-of-state-sponsored-spyware/
- https://github.com/cncf/tag-security/blob/main/supply-chain-security/compromises/README.md
