Synopsis
Darknet marketplaces allow relatively novice users to acquire Tactics, Techniques and Procedures (TTPs) needed for a more advanced cyberattack by taking advantage of easy-to-use malware for sale by more advanced users. The effect of the exchanges provides less skilled threat actors with better developed malware without having to acquire firsthand knowledge. Exchanges also facilitate the sale of advanced malware on Darknet markets, though this type of malware continues to be gated and limited to vetted participants, creating significant roadblocks to newcomers. The exchange of knowledge and software commodities under a high degree of anonymity increases the speed of malware deployment and access to more advanced payloads for cyberattacks. Despite increased TTPs available and low barrier to entry for new users, openly advertised malware offerings remain limited to commodity malware.
Background
EclecticIQ’s threat research team performed a survey of popular darknet sites to evaluate the sophistication of malware and tools currently organized in the open. Observing the state of promotion and ease of access to malware on common forums and marketplaces provide qualitative data on how malware and threat actors are evolving. For this investigation, EclecticIQ explored the following popular darknet sites: Raid Forum, Exploit.in, White House Market, Dread Forum, and Vice City Market (1).
The Darknet—Cybercrime Nexus
The darknet (darkweb) is a segregated, non-indexed volume of the internet that relies on the TOR and other protocols to provide request origin anonymity and display requested content to end users (2). The TorBrowser is an open-source application that provides access to darknet sites, but many other applications are available. Many darknet marketplaces and forums offer free access without collecting personal details, making them popular with users throughout the globe who rely on anonymity for a variety of reasons (3). Like the clear web, the darknet includes forums where users self-organize to exchange goods or ideas with little oversight.
Cybercriminals possess a broad array of capability across the cyber threat spectrum. Threat actors operate a large volume and variety of malware that includes “commodity malware.” Commodity malware (Malware-as-a-Service (Maas), Crimeware-as-a-Service (CaaS), and off-the-shelf malware) includes malware capabilities developed by cybercriminals for cybercriminals and exchanged most commonly via the darknet. This form of malware typically represents the greatest share of malware used in attacks since it is bought and sold in volume.
Analysis
The Dynamics of Darknet Marketplaces Incentivize Novice Users to Malware Development and Cyberattacks
Forums on the darknet discussing and exchanging malware serve as easy access points for users of all skill levels. A person with minimal computer knowledge can access a large selection of Darknet forums and marketplaces where cyber tools and malware are openly exchanged. A user can easily acquire free accounts with just an email address, username, and password. A variety of malware is available to most new users regardless of skill level. Users with less computer knowledge can piggy-back on the knowledge of much more skilled developers, exchange ideas, and build more sophisticated attacks with less time, effort, and detail. Transactions use cryptocurrency providing a further layer of anonymity. The anonymity and ease of access on the Darknet make it an extremely fluid marketplace, with new buyers and sellers constantly coming and going. According to the Tor Project, the number of unique .onion addresses significantly spiked around the time many countries went into initial Covid-19 lockdowns in the first quarter of 2020 (4).
Features Included in Malware Packages Allow Less Skilled Users to Operate Malware
In general, malware-as-a-service (MaaS) families offered on darknet marketplaces are not overly sophisticated, so potential buyers with only a basic understanding of computer systems or coding knowledge can successfully acquire malware needed to execute an attack. Most malware listings across forums tend to be similar – like items sold in a tourist market. Developers advertise malware with very common built-in features that include taking screenshots, stealing passwords, logging keystrokes, and intercepting other data on a targeted machine.
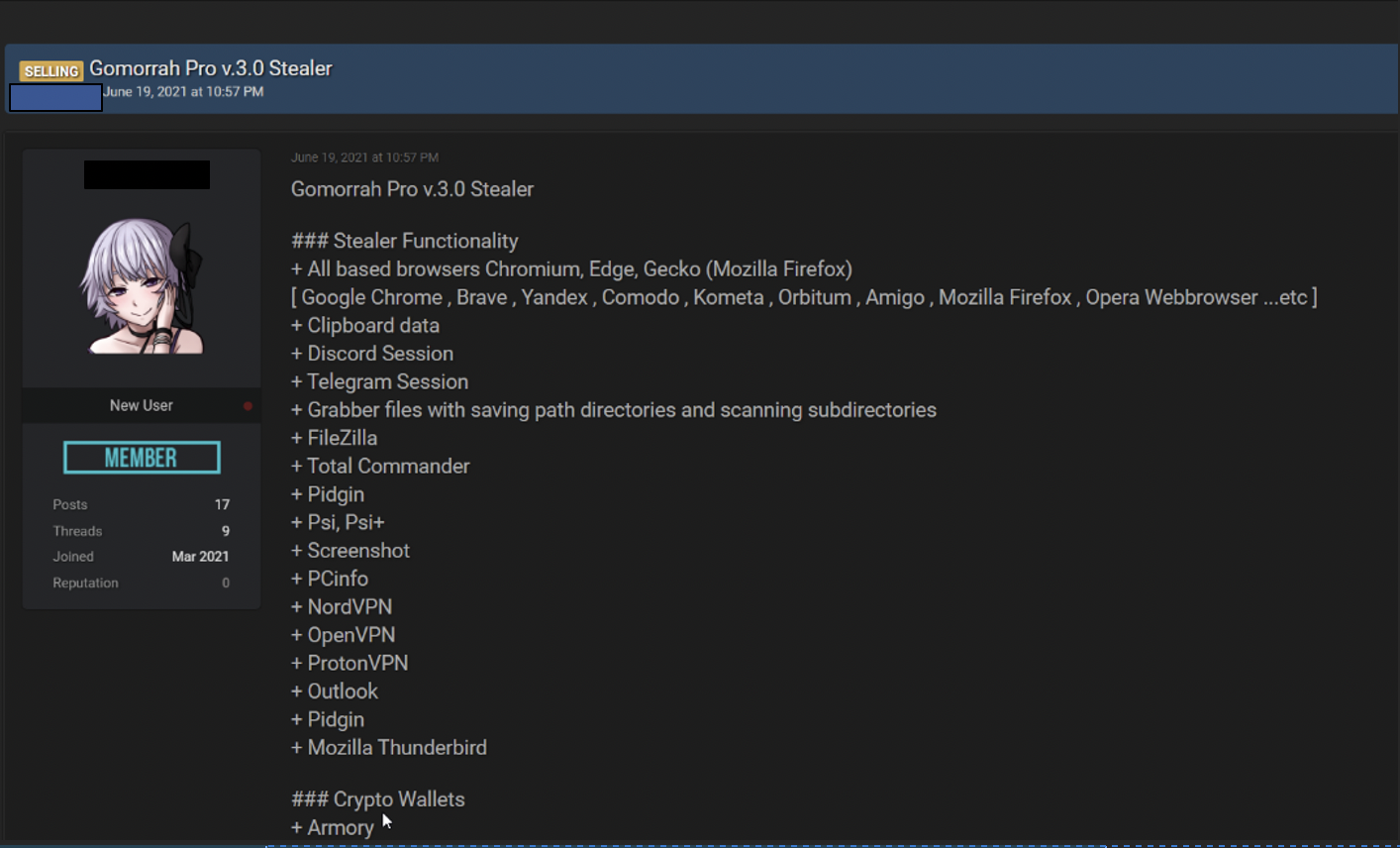 Typical commodity malware (MaaS) listing of typical TTPs.
Typical commodity malware (MaaS) listing of typical TTPs.
Many malwares come with built-out features that make operation easier for less experienced users. Packages can include elaborate point-and-click portal interfaces (command and control panels) for directing malware as well as robust support channels for troubleshooting. The many features take operation away from command lines and terminals, making the operation easier for novice users to navigate. All these factors lower the barrier to entry for malware attacks.
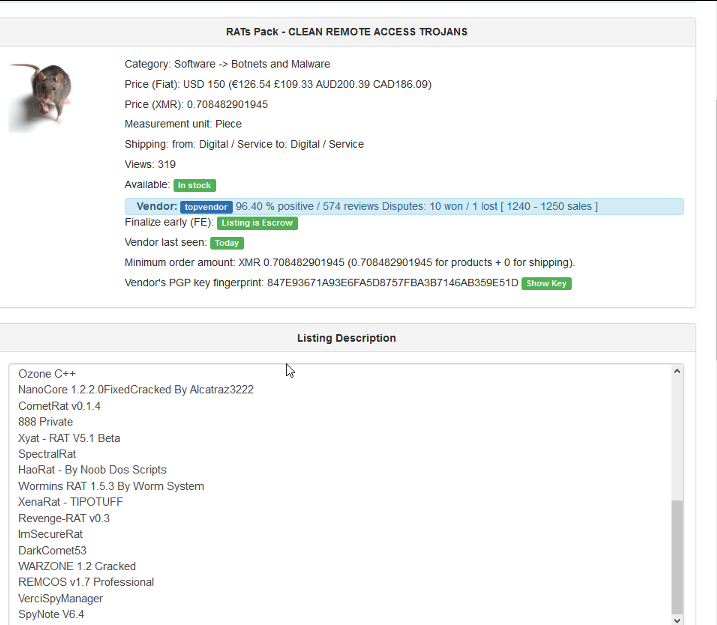 Although many malware families exist, they are largely of similar caliber.
Although many malware families exist, they are largely of similar caliber.
This screenshot depicts a common style Remote Access Trojan for sale.
Malware family types most commonly advertised on Darknet forums include bots, trojans, remote access trojans, phishing tools, and ransomware. EclecticIQ analysts observed a notable portion of posts advertising Cobalt Strike, which aligns with recent reporting detailing Cobalt Strike’s popularity among cyber threat actors (5).
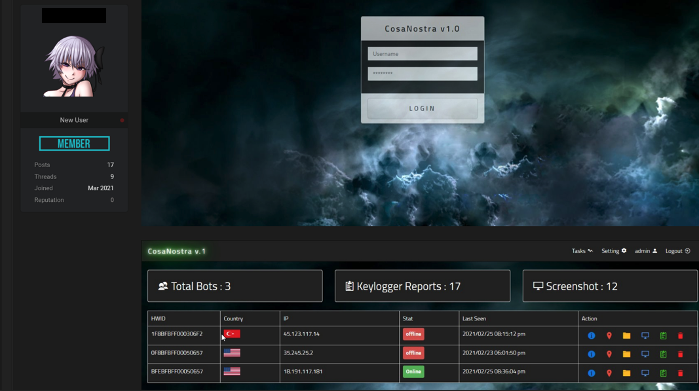 A malware listing that comes with a client portal yielding an easy-to-use graphical user interface.
A malware listing that comes with a client portal yielding an easy-to-use graphical user interface.
Users Have Access to More Complete Kill Chains
Different groups of vendors on the same darknet site specialize in different skills and types of listings. They offer a selection of malware, compromised network access, and further tooling, giving users access to more complete malware Kill-Chains. Once engaged on a particular site users can acquire malware, credentials or network access to victims, and tools to successfully infect networks and endpoints. This organization of skill-backgrounds provides aspiring cybercriminals with an easier plug-and-play approach to launch attacks and change TTPs. Users do not have to personally acquire background knowledge in code or computer science that would otherwise be requisite to operate malware.
Advanced MaaS is Not Observed Openly
MaaS listings of higher sophistication with more built-in capabilities are available, but vendors offering improved capabilities guard the listings from brand new users and novices. For certain listings, potential buyers are required to validate themselves through forum reputation scores.
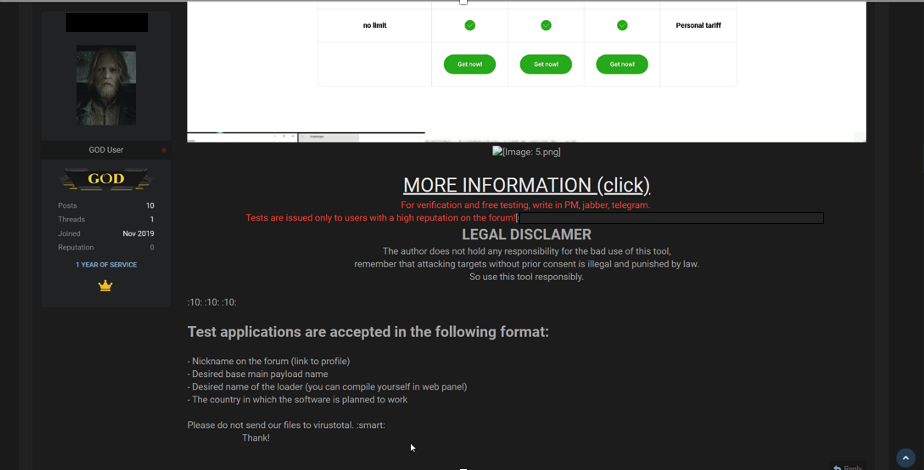 A listing where the seller takes extra care to validate certain potential clients.
A listing where the seller takes extra care to validate certain potential clients.
The requirements presents a clear barrier to the novice. Another barrier to obtaining more sophisticated malware is minimum forum-based reputation scores. Reputation score is acquired in the form of feedback from other users who have claimed to interact with one another. Feedback authenticity is nearly impossible to verify for observers. There is strong evidence that sellers can carry over reputations from other forums, allowing them to build cumulative years of experience and maintain in large groups despite the temporal nature of darknet markets (6).
Experienced Users Almost Certainly Exchange More Advanced Malware Outside Public Channels
Advanced developers are present on all forums to facilitate initial contact but may not conduct business on the forum itself. These vendors provide a simplified and somewhat non-descript initial post or listing on a forum regarding a particular malware and then immediately divert further conversation to a private channel such as Telegram, WhatsApp, and other encrypted chat or email applications.
 A listing with more vague and terse language. The developers are likely more advanced in terms of knowledge and capability than those behind other similar listings.
A listing with more vague and terse language. The developers are likely more advanced in terms of knowledge and capability than those behind other similar listings.
The behavior provides improved operational security while communicating with individuals outside of more exclusive circles. This and other measures such as the use of indirect language, allow malware developers and buyers to continue operating while evading law enforcement operations, which historically are drawn to highly publicized malware and attacks (7).
Outlook
Listings in Common Malware Markets Remain Consistent, But with Limited Capability
EclecticIQ analysts have not observed particularly advanced forms of malware openly broadcast, but Darknet forums provide an abundance of malware options for users at any skill level. The sophistication and variety of commodity malware in popular darknet markets remains relatively flat and the risk from high-volume malware (Commodity malware and MaaS) remains unchanged compared to recent years. Advancements in malware on the darknet are expected to continue at a steady pace as general knowledge, participation, and technology advancement equip more users with access to a plug-and-play approach to malware TTPs, which contribute to a more complete kill-chain and make it easier to launch cyberattacks.
Increased Government Regulation Will be The Greatest Factor in Curbing Commodity Malware Growth
Government policy to cybercriminal justice stands to be the single greatest influencer of the growth of Darknet markets. Prioritization of cybercriminal law enforcement could potentially limit open interactions on the Darknet by making cybercriminal activity more vulnerable to law enforcement action. This could reduce the amount of criminal activity by making cybercrime riskier, or it could drive malicious activities away from open public channels that have a larger audience. Regardless, the recent spate of government attention toward cybercrime will help threat hunters and security experts understand how threat actors use darknet forms as a tool to commit cybercrime.
Appendix
- https://dnstats.net/list-of-darknet-markets/
- https://www.bsi.bund.de/DE/Themen/Verbraucherinnen-und-Verbraucher/Informationen-und-Empfehlungen/Darknet-und-Deep-Web/darknet-und-deep-web_node.html
- http://geography.oii.ox.ac.uk/the-anonymous-internet/
- https://metrics.torproject.org/hidserv-dir-onions-seen.html?start=2019-04-24&end=2021-07-23
- https://www.proofpoint.com/us/blog/threat-insight/cobalt-strike-favorite-tool-apt-crimeware
- https://www.digitalshadows.com/blog-and-research/dark-web-monitoring-the-good-the-bad-and-the-ugly/, https://www.nature.com/articles/s41598-020-74416-y
- https://www.europol.europa.eu/newsroom/news/world%E2%80%99s-most-dangerous-malware-emotet-disrupted-through-global-action,
https://blogs.microsoft.com/on-the-issues/2020/10/20/trickbot-ransomware-disruption-update/
About EclecticIQ Threat Research
EclecticIQ is a global provider of threat intelligence, hunting and response technology and services. Headquartered in Amsterdam, the EclecticIQ Threat Research team is made up of experts from Europe and the U.S. with decades of experience in cyber security and intelligence in industry and government. EclecticIQ’s Threat Research team strives to apply the analytic rigor principles of U.S. Intelligence Community Directive 203 to its analysis—please click on the link for more detail.
We would love to hear from you. Please send us your feedback by emailing us at research@eclecticiq.com
