Synopsis
This research provides an assessment about the technical capabilities of pro-Russian hacktivist group Killnet. Through analysis of open-source intelligence and instant messaging service data this paper also demonstrates how Killnet´s messaging aligns with Russian information narratives.
Killnet Lacks Capabilities to Execute DDoS Attacks With Lasting Impact on Network Infrastructure
EclecticIQ analysts assess the cybercriminal group Killnet possesses the resources to successfully conduct short-lived Distributed Denial of Service (DDoS) attacks but lacks the capabilities to execute attacks that impair network infrastructure for a longer period. Analysts believe that Killnet supporters are novice users with zero or limited experience with DDoS attacks, based on an analysis of Telegram messaging data and open-source reporting. Killnet is a pro-Russian hacktivist group that was likely formed in February 2022. Since then, members have targeted public and private organizations in several countries and industries they perceive as hostile to the Russian Federation.
As seen with recent DDoS attacks against organizations in Estonia, Lithuania, or Japan (see list below), the group can swiftly bundle its resources and execute attacks in alignment with Russian state objectives. OSINT shows that the attacks had minimum to no lasting impact to affected organizations.
- Between September 6th and 8th, Killnet claimed responsibility for DDoS attacks against Japanese business and public institutions. Analysts assess with moderate confidence that the attacks are in response to increasing tensions between Russian and Japan regarding the Kuril Islands dispute. [1] The Kuril Islands are a chain of islands extending from the Japanese island of Hokkaido to the southern tip of Russia’s Kamchatka Peninsula. On June 6th, Russia suspended visa-free visits to the islands - an action that Japan´s Foreign Minister condemned as “totally unacceptable.”
- On August 16th, Estonia removed a Soviet-era tank monument.[2] On the same day Killnet carried out DDoS attacks against Estonian government or commercial organizations. Luukas Ilves, Under-Secretary for Digital Transformation at Estonia's Ministry of Economic Affairs and Communications confirmed the DDoS attacks. He added that attacks went “largely unnoticed” and that despite “some brief and minor exceptions, websites remained fully available throughout the day".[3]
- On June 18th Lithuania banned the import of EU-sanctioned goods coming from Russia across its territory to the Russian exclave of Kaliningrad.[4] In its Telegram channel, Killnet called on Russian hacktivists to conduct attacks on Lithuania's network infrastructure. The Lithuanian National Cyber Security Centre (NCSC) warned on June 21st of an ongoing DDoS attack against the Secure National Data Transfer Network, other governmental institutions, and private companies of Lithuania.[5] OSINT suggest that the attacks had only a minor impact on public and private internet infrastructure.[6]
Public statements by politicians, and actions taken by Western governments in support of Ukraine have been and will almost certainly continue to be triggers for future DDoS attacks.
Killnet Telegram Channel(s): An Echo Chamber for Russian Narratives and for Distributing Fear, Uncertainty, Doubt
Killnet presents itself as Russian hackers, hence many messages to subscribers in Killnet’s Telegram Channel are about calls for cyber-attacks and sharing evidence of successful attacks - overall distributing Fear, Uncertainty, Doubt (FUD). A few examples of these messages are below.
13.09.2022 06:02 Khokhols do not rejoice - nuclear ashes await you
11.09.2022 22:13 […] And let's imagine a strike on Kyiv with nuclear weapons. Not one. And 4 Sarmatians in Kyiv ...So that stone upon stone ... and radioactive ash towards England and Geyropa
23.08.2022 07:08 Let hell begin on the land of Moldova. […] The ping of the state network will stop for weeks, and then they will definitely see the light in tears-
22.07.2022 11:17 Russians are coming!
10.07.2022 20:22 Tomorrow is Monday, it's time to create a disaster
The U.S. Department of State [7] and EUvsDisinfo [8], a project by the European Union East StratCom Task Force [9], described common Russian disinformation narratives in detail. Analysts observed that Killnet messages echo a number of these Russian narratives - specifically the narratives of “Hahaganda”, “Elite vs. People”, and “Loss of sovereignty / Threatened National Identity”. Its objective is almost certainly to engage with Russian speaking people, and to possibly to convince (“recruit”) like-minded individuals in and outside Russia. Below is an overview of observed messages and how they relate to Russian narratives:
Hahaganda - Discrediting Perceived Russian Enemies Goes Into Extremes
The Hahaganda narrative involves the use of various derogatory words, videos, music and images to belittle the concept of democracy, democratic procedures, and candidates. In its channel, Killnet regularly shares taunting and humiliating posts of Ukrainian and Western politicians, public figures, and military personnel:
21.07.2022 17:09 - The most useful thing the coronavirus has done this year...US President Joe Biden tests positive for coronavirus..."
05.07.2022 23:06 "Vladimir Zelensky has just been found dead in his office...The preliminary cause of death is heart failure. […] When will it come true"
Analysts highlight that some of the posts reach extremes and constitute calls to violence. In one such example, Lockheed Martin chairman, president and chief executive officer, James D. Taiclet is pictured in a coffin with a caption
“this is his future - and he has no other. Condolences to him ..."
Other posts are even less subtle. As of September 13th, about 50 municipal deputies have signed a petition demanding the resignation of President Vladimir Putin.[10] In response, Killnet posted an image of a member of the Council of Deputies of the Lomonosovsky municipal next to a threatening text.
"Dear Vladimir Vladimirovich Putin. We ask you to send this bespectacled monkey of the deputy closer to Navalny! If this does not happen in the near future, then we will send [him] in a different way.”
The post below refers to NATO Secretary General Jens Stoltenberg.
26.06.2022 21:10 "I forgot to introduce you to our enemy number 1 - Jens Stoltenberg. This devil will answer for every life of a Russian soldier. And also his family, his grandchildren, and his supporters will answer!"
Elite vs. People - Portraying Killnet As Representative of the People
Killnet also deploys the “Elite vs. People” narrative in several posts, framing political leaders of Ukraine, former Soviet states, or western governments as “evil elites” who have lost connection with the needs of the “people”. In several messages, Killnet repeats this mantra arguing that their activities are not targeted against citizens, but against elites who oppose Russia.
22.08.2022 20:23 - KillNet stands 24/7 to protect its people […] Fraternal people of Moldova, you are not responsible for the actions of your Puppet corrupt government. […] We will burn out evil with a red-hot iron, by ANY means available to us. Every time OUR country is threatened by politicians, we will act and cause damage.
20.07.2022 08:51 - Refugees from Ukraine who fled to Norway are forced to stand in lines for free food. It is noted that in the city of Stavanger, more and more people are asking for food assistance in order to survive. Financial support from the Norwegian authorities is becoming insufficient. But this is only in Norway. Poor people
24.06.2022 20:19 - In general, I don’t want to cause inconvenience to the peaceful citizens of Lithuania anymore, it’s not their fault that their government has no control […].
Loss of Sovereignty / Threatened National Identity
This narrative aims to frame Ukraine and other former Soviet states as no longer sovereign, but rather controlled by Western states. Killnet messages repeat this narrative:
05.09.2022 13:40 – "Ukraine - Error 404. […]
1. There is no historical territory, actually a fictional country.
2. No sovereignty. Completely under external control.
3. No financial institution: full subsidized content from outside.
4. there are no governing bodies.
5. there is no legislation corresponding to international law.
6. invented language.
7. there is no ideology, only a cancerous informational tumor that has raised several generations of mentally ill people.
Ukraine is now not a state, but a small area, with its natives, its customs and several dialects, which the United States maintains."
24.08.2022 14:54 - Reminder from KillNet for the independence day of Khokhlostana.1 There is no such country anymore, there is no such state of Ukraine. There are only Ukrainians, without a homeland and a flag. As my Friend said: "Ukraine is one big mental hospital that has now run out of tranquilizers." Treating the majority simply does not make sense. Zelensky, will you fool and exterminate your people for a long time?
24.08.2022 00:30 - Post in response to a statement by Andrzej Duda (president of Poland) that “Crimea was and is part of Ukraine like Gdańsk or Lublin to Poland […]
Fantasies of Duda.
Crimea is already Russia
Mariupol is Russia.
Kherson is Russia.
Donetsk is Russia
Lugansk is Russia.
These are facts.
More facts?
Ukraine is no longer such a country, Ukrainians remained in the territory without a name. Poland is one of the US colonies, with a puppet government."
The narrative is often mixed with a perceived threat to Russian national identity and values that would be endangered by a “progressive Western attitude attitudes about the rights of women, ethnic and religious minorities, and LGBTQ groups, among others.[8]”
25.08.2022 14:32 "Across the Republic of Moldova, we counted no more than 2,000 desktop computers, 7,500 smart gadgets for Android, and 4 iPhones through the provider. And this dirty point on the map is trying to download something against the Russian bear. She probably thinks that LGBT Europe will help her in case of a response from Russia.
02.07.2022 20:21 "In fact, none of the members of the killnet use "Alcohol"" and other substances that adversely affect human brain activity. A real man should have a healthy mind in a healthy body. So remember this, our dear subscribers. Alcohol/drugs are very bad!"
24.06.2022 21:00 A Telegram message in response to a Russian band announcing to leave Russia over the invasion of Ukraine, and releasing an anti-war video clip on June,24th. [11] How good it is when such filth leaves our Great Country. I really hope that by 2023, everything similar to the European mentality of the "Little Big" type of sexual infection will disappear from Russia
Killnet Feeding Into Russian Information Bubble But Likely Acting Independently
Analysts assess with low confidence that Killnet is operating independently, i.e., its activities and messaging are not directed by Russian intelligence and security services. The operator or operators behind Killnet likely repeat messages received from Russia’s media apparatus. In a post mid-September, the group reiterates that “[they] are not a state structure, [and their] activities are not paid by the President of the Russian Federation.” Analysts also note that the group occasionally asks for monetary support in form of donations.
Yet, it cannot be ruled out that the messaging is orchestrated by a Russian government-supported information warfare campaign.
Analysts have observed Killnet:
- Sharing and reposting messages from other pro-Russian telegram groups.
- Referencing news articles from Russian media outlets.
- Recommending journalists that write in favour of Russia´s politics.
- Distributing well-produced music videos that glorify Russian hackers and appeal to memories of the Soviet Union’s Great Patriotic War against Nazi Germany.
- Sharing links to pro-Russian radio station in Ukraine.
Eventually, the above activities feed the information strategy, meant to amplify, and justify Russia´s stance on Ukraine, NATO, Western society and other topics. The number of Telegram subscribers, messages views and replies indicates that Killnet has a solid base of followers. At the time of analysis (mid-September), about 91.000 accounts followed Killnet's Telegram channel.
Analysts saw a dip in the average number of messages posted every week in the summer months. Analysts speculate that Ukraine gaining battlefield momentum or Killnet operators taking a summer vacation have caused the decline. Yet, the average amount of message views and replies remained consistent throughout the last weeks, indicating an active follower base.
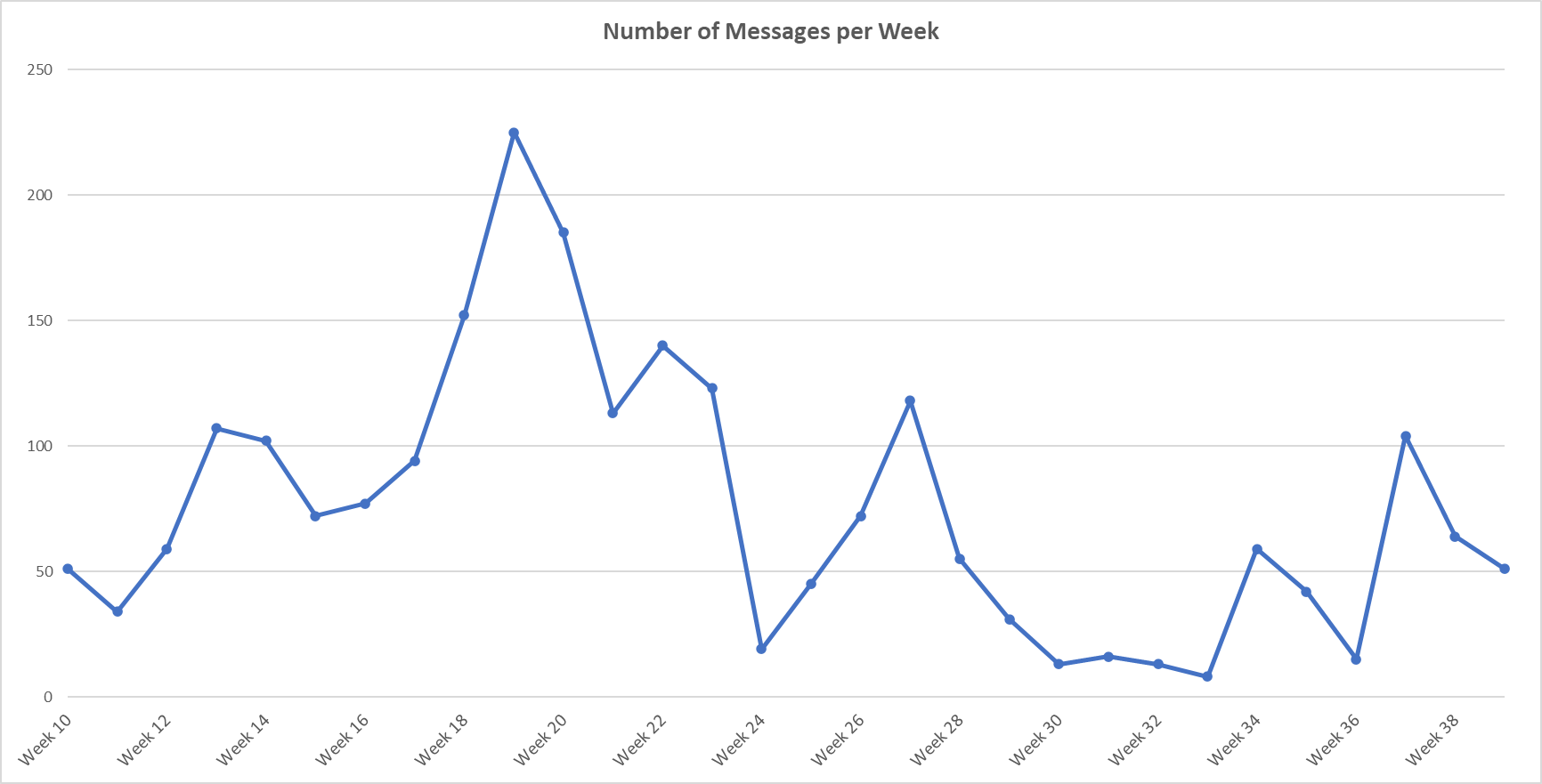
Figure 1 - Average Number of Telegram Posts per Week
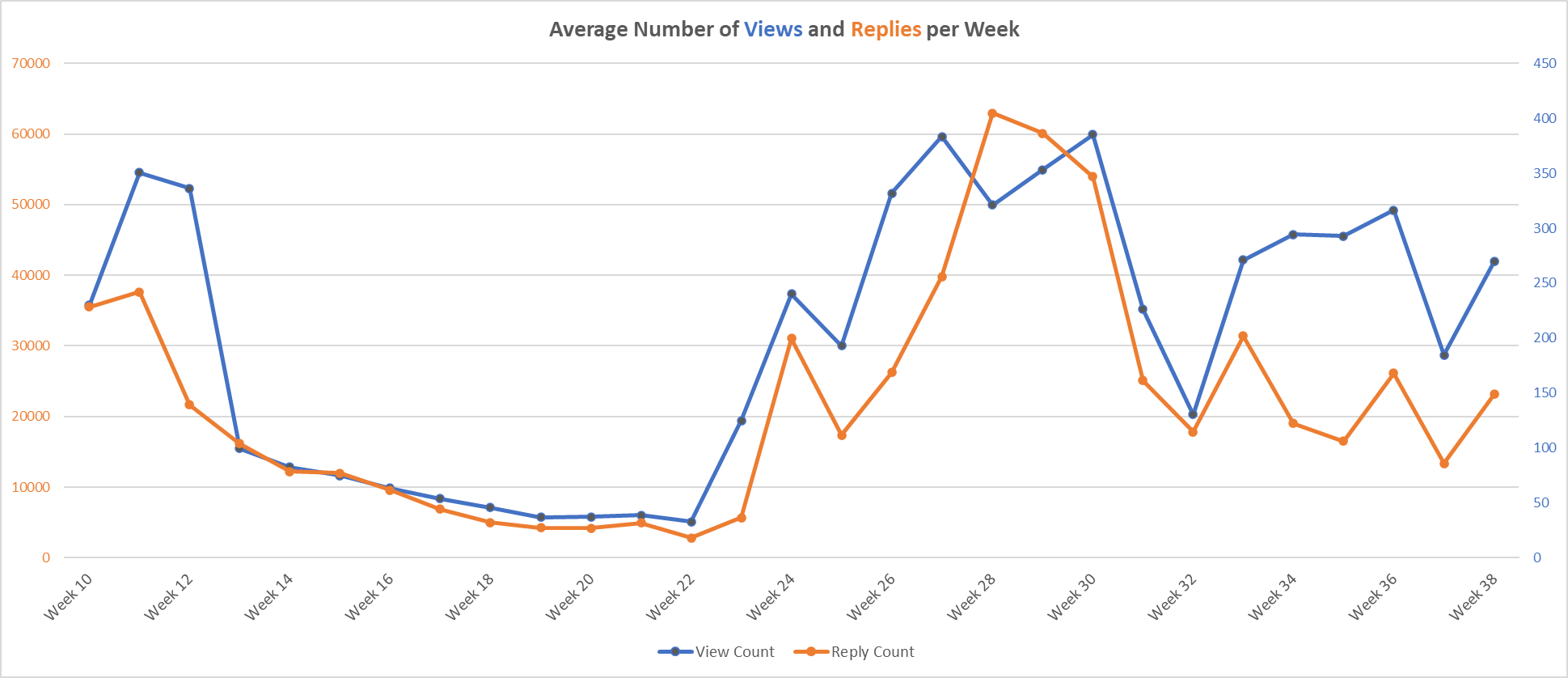
Figure 2 - Average Number of Message Views and Message Replies per Week
Looking Ahead: Extension of TTPs Would Signal Escalated Threat
Analysis shows that Killnet is clearly aligned with Russian narratives and its long and short-term goals. The group views itself as an independent cyber army that is willing to fight “the enemy” or “the evil”. The definition of evil is fluid/adjustable and includes anybody having opposing views to the Kremlin - specifically Ukraine, NATO or European member states, or the United States.
Analysts do not believe that the group currently possesses the technical capabilities to significantly harm organizations with a lasting impact on network infrastructure. OSINT shows that past attacks had limited or no noticeable impact on business operations. It is plausible that small or medium-sized businesses without DDoS protection capabilities suffer from attacks.
Successful DDoS attacks on government entities, private organizations or critical infrastructure assets in the future would signal a change in technical capabilities. Similarly, expansion to other TTPs like website defacements or theft of data would mark a change in the group’s sophistication. On September 15th, Killnet announced to recruit “encoders, network engineers, pentesters, DDoS´er, admins of UNIX and Windows systems, journalists with media connections, designers, and social engineers” - a potential first step in increasing the groups' capabilities and visibility.
About EclecticIQ Intelligence & Research Team
EclecticIQ is a global provider of threat intelligence, hunting, and response technology and services. Headquartered in Amsterdam, the EclecticIQ Intelligence & Research Team is made up of experts from Europe and the U.S. with decades of experience in cyber security and intelligence in industry and government.
We would love to hear from you. Please send us your feedback by emailing us at research@eclecticiq.com or fill in the EclecticIQ Audience Interest Survey to drive our research towards your priority area.
Structured Data
Find the Analyst Prompt and earlier editions in our public TAXII collection for easy use in your security stack.
TAXII v1 Discovery services: https://cti.eclecticiq.com/taxii/discovery
Please refer to our support page for guidance on how to access the feeds.
You might also be interested in:
Ukraine-Russia Conflict: Ukraine Alerts Energy Enterprises to Possible Cyberattack Escalation
AI Facial Recognition Used in Ukraine/Russia War Prone to Vulnerabilities
Appendix
-
“Russia scraps visa-free visits for former Japanese residents of four islands | NHK WORLD-JAPAN News,” NHK WORLD. https://www3.nhk.or.jp/nhkworld/en/news/20220906_07/ (accessed Sep. 12, 2022)
-
J. Henley, “Estonia removes Soviet-era tank monument amid Russia tensions,” The Guardian, Aug. 16, 2022. Accessed: Sep. 13, 2022. [Online]. Available: https://www.theguardian.com/world/2022/aug/16/estonia-removes-soviet-era-tank-monument-amid-russia-tensions-narva
-
P. Davies, “Estonia hit by massive cyberattack amid tensions with Russia,” euronews, Aug. 18, 2022. https://www.euronews.com/next/2022/08/18/estonia-hit-by-most-extensive-cyberattack-since-2007-amid-tensions-with-russia-over-ukrain (accessed Sep. 12, 2022)
-
A. Sytas, “Kaliningrad sanctions to take effect, Lithuania says,” Reuters, Jun. 18, 2022. Accessed: Jun. 28, 2022. [Online]. Available: https://www.reuters.com/world/europe/lithuania-says-sanctions-goods-kaliningrad-take-effect-saturday-2022-06-18/
-
“Intense DDoS attacks targeted several companies and institutions in Lithuania.” https://lrv.lt/en/news/intense-ddos-attacks-targeted-several-companies-and-institutions-in-lithuania (accessed Jun. 28, 2022).
-
NetBlocks [@netblocks], “ Confirmed: Metrics show a disruption to government networks in #Lithuania as the National Cyber Security Centre reports a denial-of-service cyberattack affecting secure networks used by state institutions, also affecting public and private internet infrastructure https://t.co/dgsDrJDyxq,” Twitter, Jun. 27, 2022. https://twitter.com/netblocks/status/1541430568457572352 (accessed Sep. 12, 2022).
-
“Russia’s Top Five Persistent Disinformation Narratives,” United States Department of State. https://www.state.gov/russias-top-five-persistent-disinformation-narratives/ (accessed Sep. 13, 2022).
-
PE, “5 Common Pro-Kremlin Disinformation Narratives,” EU vs DISINFORMATION, Apr. 02, 2019. https://euvsdisinfo.eu/5-common-pro-kremlin-disinformation-narratives/ (accessed Sep. 13, 2022).
-
“EEAS | EEAS Website.” https://www.eeas.europa.eu/_en (accessed Sep. 20, 2022).
-
T. S. K. CNN Eliza Mackintosh, Adrienne Vogt, Aditi Sangal, “September 13, 2022 Russia-Ukraine news,” CNN. https://www.cnn.com/europe/live-news/russia-ukraine-war-news-09-13-22/index.html (accessed Sep. 16, 2022).
-
G. Argyriou, “Little Big Leaves Russia Over War In Ukraine,” Eurovision News | Music | Fun, Jun. 26, 2022. https://eurovisionfun.com/en/2022/06/little-big-leaves-russia-over-war-in-ukraine/ (accessed Sep. 12, 2022).



